CARVER+Shock and Business Process Management in Improving Food Safety of Primary Production
Abstract
:1. Introduction
2. Literature Review
- Environmental factors include animal reservoirs—animal husbandry, access to fruit and vegetable growing areas, and contact with pets, pests, or wildlife fauna and flora.
- Fertilizers and plant protection products—use of untreated or insufficiently cleaned organic soil improvers, manure or compost.
- Agricultural water—use of contaminated water for irrigation, or pesticides and fungicides.
- Hygiene and health status of workers—contamination by workers.
- unapproved enhancements (adding substances to improve properties)
- substitution (replacing ingredients with cheaper substitutes)
- dilution (enrichment of more expensive raw materials with cheaper substitutes)
- Primary farming and harvesting—these systems cover both small family farms and large agricultural businesses. It is necessary to ensure the safety of raw materials used in agricultural production, from the soil condition, seeds, and fertilizers in plant production to animal feed in livestock production. In particular, WHO experts have suggested the need to take samples of finished products, test them, and, if necessary, inform the relevant state authorities.
- Food processing.
- Food logistics, including storage and transportation.
- Wholesale and retail distribution.
- Gastronomy.
- Monitoring and recalling products on the market.
- Reduce the likelihood of a deliberate attack
- Reduce the impact of an attack on a food business
- Provide stakeholders safe production and supply chain [10].
3. Materials and Methods
- Criticality is a measure of an attack’s impact on public health and the economy. Question: Do I hurt the victims’ economy, health, and ability to fight?
- Accessibility is the ability to physically access and exit an attack location. Questions: How close? How easy to reach the victims? What physical access is available?
- Recovery is the ability to recover from a given system or infrastructure attack. Question: How quickly can victims rebuild?
- Vulnerability is the ease of performing an attack. Questions: Can I damage the target? Is it reinforced or guarded?
- Effect is the amount of loss caused by direct attack, measured by production loss. Question: Do victims have backups or alternatives?
- Recognizability is ease of target identification. Question: Can the attacker recognize and find the target?
- Setting the scenarios and assumptions for the whole analysis. This should include identification of what is supposed to be protected from what type of threats.
- Gathering experts. The team could consist of experts from various specializations: food production, food science, microbiology, epidemiology, radiology, toxicology, medicine, and risk assessment.
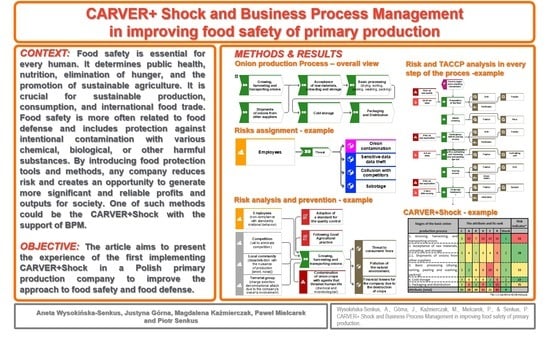
- Describing and documenting the food supply chain that is under assessment. Business process management and modeling methodology enriched with TACCP analysis would be beneficial [47].
- Assigning results. Each factor can be ranked against CARVER+Shock attributes to calculate a final score for that node. The scoring tables used for analysis are often calculated based on catastrophic accidents at a national level. The scoring can be modified in order to meet a specificity of a given facility. A key factor is that the analysis helps to distinguish one operation of the entity from another
- Applying the lessons learned. After critical factors have been identified, the final step is to develop a plan to implement countermeasures that minimize the attractiveness of targets. Remedies may include improvements to physical assets, personnel, and operational safety that help minimize aggressor accessibility to a process or product.
4. Empirical Results and Discussion
4.1. Business Process Management and Modeling Methodology
4.2. The Studied Enterprise
4.3. Results and Discussion
- Criticality (3): the attribute ‘critical’ as a measure of public health in the attack relates to health problems or loss of life among workers and residents adjacent to the onion cultivation.
- Accessibility (10): access by unauthorized people is highly probable, e.g., temporary workers are hired for harvesting and transport.
- Recoverability (7): Growing onions is associated with a certain length of growing season, and in the case of chemical contamination, soil remediation can be a long process.
- Vulnerability (10): The evaluation team found that the cultivation, harvesting, and transport of onions favor the accessible introduction of a contaminant, while the environment is favorable because the cultivation is not monitored.
- Effect (10): The attack’s impact could destroy more than 50% of the production system; soil remediation, re-purchase of raw material, and disposal of contaminated raw material or product must also be considered.
- Recognizability (rank 10): The goal is straightforward to recognize. It is very easy to locate the onion fields and to identify company transport because they carry a company logo.
- Shock (rank 1): in this case there is no historical, cultural, religious, or other symbolic significance.
- Packaging and distribution (R = 35)
- Basic processing (drying, sorting, peeling, washing, packing) (R = 33)
- Acceptance of raw materials, unloading, and storage (R = 28)
- Cold storage (R = 27).
- F (Follow)—follow the established plan and food defense procedures.
- I (Inspect)—control your position, work area, and adjacent positions and areas.
- R (Recognize)—recognize what is wrong.
- S (Secure)—secure all ingredients, supplies, and finished products.
- T (Tell)—inform your superiors if you notice anything unusual or suspicious.
5. Conclusions
- awareness and competence of executive employees and company managers
- standards and procedures ensuring the safety of the production system
- development and implementation of preventive measures relating to the company and entities in the supply chain
- observation and monitoring of preparations for potential attacks (monitoring of the plant, tracking information in the local press and social media).
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviated Terms and Notes
| BPM | Business process management |
| BRC | British Retail Consortium (or BRC) is a trade association for retail businesses in the United Kingdom |
| BSI Group | British Standards Institution |
| CARVER+Shock | Criticality, Accessibility, Recoverability, Vulnerability, Effect, Recognizability |
| EC | European Commission |
| Employees FIRST | Follow, Inspect, Recognize, Secure, Tell |
| FDA | Food and Drug Administration |
| FSIS | Food Safety and Inspection Service |
| GlobalG.A.P. is a farm assurance program, translating consumer requirements into Good Agricultural Practice. | |
| Food Fraud | a crime committed for financial gain |
| Food Defense | protection of food from malicious adulteration, such as acts of terrorism or extortion |
| HACCP | Hazard Analysis and Critical Control Point |
| IFS | International Food Standard is an international food safety standard developed in 2002 by representatives of German retail trade |
| ISO 22000 is a Food safety management system by the International Organization for Standardization, which is outcome-focused, providing requirements for any organization in the food industry with the objective to help to improve overall performance in food safety. | |
| SME | Small and medium-sized enterprises |
| TACCP | Threat Assessment Critical Control Point |
| USA | United States of America |
| USDA | United States Department of Agriculture |
| VACD | Value-added chain diagram |
| WHO | World Health Organization |
References
- Vågsholm, I.; Arzoomand, N.S.; Boqvist, S. Food Security, Safety, and Sustainability—Getting the Trade-Offs Right. Front. Sustain. Food Syst. 2020, 4, 16. [Google Scholar] [CrossRef]
- FAO; WHO. The Future of Food Safety—Transforming Knowledge into Action for People, Economies and the Environment. Technical Summary by FAO and WHO; FAO: Rome, Italy; WHO: Rome, Italy, 2020. [Google Scholar] [CrossRef]
- Grace, D. Food Safety and the Sustainable Development Goals; ILRI: Nairobi, Kenya, 2017. [Google Scholar]
- Stawicka, E. Corporate social responsibility and the milk market in Poland. J. Tour. Reg. Dev. 2018, 9, 71–80. [Google Scholar] [CrossRef] [Green Version]
- Lang, T.; Barling, D. Food security and food sustainability: Reformulating the debate. Geogr. J. 2012, 178, 313–326. [Google Scholar] [CrossRef]
- FAO. Sustainable Food Systems: Concept and Framework. 2018. Available online: http://www.fao.org/3/ca2079en/CA2079EN.pdf (accessed on 22 February 2022).
- Górna, J.; Kaźmierczak, M.; Zapłata, S. Praktyka Zarządzania Systemowego w Doskonaleniu Organizacji; Wydawnictwo Uniwersytetu Ekonomicznego w Poznaniu: Poznań, Poland, 2021. [Google Scholar]
- European Commission. Laying Down the General Principles and Requirements of Food Law, Establishing the European Food Safety Authority and Laying Down Procedures in Matters of Food Safety; Regulation (EC); European Commission: Brussels, Belgium, 2002; Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32002R0178 (accessed on 13 January 2022).
- European Commission. On the Hygiene of Foodstuffs; Regulation (EC); European Commission: Brussels, Belgium, 2002; Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32004R0852 (accessed on 13 January 2022).
- PAS. Guide to Protecting and Defending Food and Drink from Deliberate Attack, 3rd ed.; The British Standards Institution: London, UK, 2017. Available online: https://www.food.gov.uk/sites/default/files/media/document/pas962017_0.pdf (accessed on 22 February 2022).
- Official Journal of the European Union 2017/C 163/01. Commission Notice on Guidance Document on Addressing Microbiological Risks in Fresh Fruits and Vegetables at Primary Production Through Good Hygiene. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:52017XC0523(03) (accessed on 23 January 2022).
- Górna, J. Społeczna odpowiedzialność przedsiębiorstw w zakresie zasad higieny na etapie produkcji podstawowej. Zagadnienia Doradz. Rol. 2018, 1, 102–111. [Google Scholar]
- Adams, A.; Marsh, K. Assessing Threats & Vulnerabilities for Food Defence; Adele Adams Associates Ltd. & Techni-K Consulting Ltd.: Ilkley, UK, 2014; Available online: http://techni-kimages.s3.amazonaws.com/wpcontent/uploads/woocommerce_uploads/2015/11/04100143/Assessing-Threat-Vulnerability-for-Food-Defence1.pdf (accessed on 23 January 2022).
- Davidson, R.K.; Antunes, W.; Madslien, E.H.; Belenguer, J.; Gerevini, M.; Perez, T.T.; Prugger, R. From food defence to food supply chain integrity. Br. Food J. 2017, 119, 52–66. [Google Scholar] [CrossRef] [Green Version]
- Pietrzyck, K.; Jarzębowski, S.; Petersen, B. Exploring Sustainable Aspects Regarding the Food Supply Chain, Agri-Food Quality Standards, and Global Trade: An Empirical Study among Experts from the European Union and the United States. Energies 2021, 14, 5987. [Google Scholar] [CrossRef]
- USDA. Food Defense Risk Mitigation Tool. Available online: https://www.fsis.usda.gov/food-safety/food-defense-and-emergency-response/food-defense (accessed on 23 January 2022).
- Larson, R.B. Perceived food safety and food defense responsibility for farmers, transporters, retailers and consumers. Br. Food J. 2021, 123, 4309–4331. [Google Scholar] [CrossRef]
- Ustawa z dnia 25 Sierpnia 2006 r. o Bezpieczeństwie Żywności i Żywienia; Dz.U. z 2020 r. poz. 2021. Available online: https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20200002021/U/D20202021Lj.pdf (accessed on 23 January 2022).
- Global G.A.P. IFA V5.4-1-GFS, Control Points and Compliance Criteria—All Farm Base. Available online: https://www.globalgap.org/uk_en/documents/#q=(*V5.4-1*)%20OR%20%22*V5.4-1*%22 (accessed on 23 January 2022).
- ISO/TS 22002-1:2009 (E). Prerequisite Programmes on Food Safety—Part 1: Food Manufacturing; ISO: Geneva, Switzerland, 2009. [Google Scholar]
- British Retail Consortium. Global Standard Food; The Stationery Office: London, UK, 2018. [Google Scholar]
- IFS. Food Standard for Assessing product and process compliance in relation to food safety and quality version 7. 2020. Available online: https://www.academia.edu/37915370/IFS_Food_Standard_for_auditing_quality_and_food_safety_of_food_products_Food (accessed on 23 January 2022).
- Kinsey, J.; Stinson, T.F.; Degeneffe, D.J.; Ghosh, K.; Busta, F. Consumers Response to a New Food Safety Issue: Food Terrorism. In Proceedings of the IUFOST XIIIth Congress of Food Science and Technology, Nantes, France, 17–21 September 2006. [Google Scholar]
- World Health Organization. Global Public Health Response to Natural Occurrence, Accidental Release or Deliberate Use of Biological and Chemical Agents or Radionuclear Material that Affect Health. Fifty-Fifth World Assembly, WHA55.16. 2002. Available online: https://apps.who.int/gb/archive/pdf_files/WHA55/ewha5516.pdf (accessed on 23 January 2022).
- Peter, C. Food Terrorism: Do We Care? Int. J. Saf. Secur. Tour. Hosp. 2015, 1, 1–14. [Google Scholar]
- World Health Organization. Terrorist Threats to Food: Guidance for Establishing and Strengthening Prevention and Response Systems; World Health Organization: Geneva, Switzerland, 2003. [Google Scholar]
- Binczycka-Anholcer, M.; Imiołek, A. Bioterroryzm jako jedna z form współczesnego terroryzmu. Hygeia Public Health 2011, 46, 326–333. Available online: http://www.h-ph.pl/pdf/hyg-2011/hyg-2011-3-326.pdf (accessed on 23 January 2022).
- Wiśniewska, M. Systemic Food Defence Management Against Terrorism; Publishing House of the Gdansk University: Gdańsk, Poland, 2016. [Google Scholar]
- Sobel, J.; Khan, A.S.; Swerdlow, D.L. Threat of a biological terrorist attack on the US food supply: The CDC perspective. Lancet 2002, 359, 874–880. [Google Scholar] [CrossRef]
- Jurica, K.; Vrdoljak, J.; Brčić Karačonji, I. Food defence systems as an answer to food terrorism. Arh. Za Hig. Rada I Toksikol. 2019, 70, 232–255. [Google Scholar] [CrossRef] [Green Version]
- Ingelfinger, J.R. Melamine and the Global Implications of Food Contamination. N. Engl. J. Med. 2008, 359, 2745–2748. [Google Scholar] [CrossRef]
- Chan, E.Y.Y.; Griffiths, S.M.; Chan, C.W. Public-health risks of melamine in milk products. Lancet 2008, 372, 1444–1445. [Google Scholar] [CrossRef]
- O’shea, P. Dodgy dumplings and lethal liver: Risk, food terrorism, and Sino–Japanese relations. Pac. Rev. 2015, 28, 303–321. [Google Scholar] [CrossRef]
- Spink, J.; Moyer, D.C. Defining the Public Health Threat of Food Fraud. J. Food Sci. 2011, 76, 156–163. [Google Scholar] [CrossRef]
- Hefnawy, M. Advances in Food Protection: Focus on Food Safety and Defence; Springer Science & Business Media: Dordrecht, The Netherlands, 2011. [Google Scholar]
- Spink, J.; Ortega, D.L.; Chen, C.; Wu, F. Food fraud prevention shifts the food risk focus to vulnerability. Trends Food Sci. Technol. 2017, 62, 215–220. [Google Scholar] [CrossRef]
- Ulberth, F. Tools to combat food fraud–a gap analysis. Food Chem. 2020, 330, 127044. [Google Scholar] [CrossRef]
- Soon, J.M.; Krzyzaniak, S.C.; Shuttlewood, Z.; Smith, M.; Jack, L. Food fraud vulnerability assessment tools used in food industry. Food Control. 2019, 101, 225–232. [Google Scholar] [CrossRef]
- Tomski, P. On case study method in Entrepreneurship research, Zeszyty Naukowe Politechniki Częstochowskiej. Zarządzanie 2017, 27, 189–198. [Google Scholar]
- Zainal, Z. Case Study as a Research Method. J. Kemanus. 2007, 5, 1–6. [Google Scholar]
- Mroczko, F. Jakościowe metody badań. Obserwacja naukowa. Pr. Nauk. WWSZIP 2012, 26, 65–78. [Google Scholar]
- Zelek, A. Case study—Nieocenione narzędzie dydaktyczne. Około Pedagog. 2021, 2, 66–79. [Google Scholar]
- Mielcarek, P. Metoda case study w rozwoju teorii naukowych. Organ. I Kier. 2014, 1, 105–117. [Google Scholar]
- Georgescu, M.; Raita, S.M. Deployment of the CARVER plus SHOCK vulnerability assessment method in a food processing facility—A case study. Lucr. Ştiinţifice Med. Vet. 2019, 4, 39–52. [Google Scholar]
- Wiśniewska, M. Wykorzystanie metody CARVER+Shock do wstępnej oceny ryzyka powodziowego. Współczesne Zarządzanie 2010, 3, 62–71. [Google Scholar]
- FDA. Carver + Shock Primer. An Overview of the Carver Plus Shock Method for Food Sector Vulnerability Assessments. Available online: https://www.fda.gov/food/food-defense-programs/carver-shock-primer (accessed on 20 January 2022).
- Mitenius, N.; Kennedy, S.P.; Busta, F.F. Food Safety Management: Chapter 35. In Food Defense; Motarjemi, Y., Lelieveld, H., Eds.; Academic Press: Cambridge, MA, USA, 2013; pp. 937–958. [Google Scholar]
- Hammer, M.; Brocke, J.V.; Rosemann, M. What Is Business Process Management? Handbook on Business Process Management 1; Brocke, J.V., Rosemann, M., Eds.; Springer: Berlin, Germany, 2010. [Google Scholar]






| Event | Food/Poison | Infected | Deaths |
|---|---|---|---|
| 2017–2018 South African listeriosis outbreak | Processed meat | 1060 | 216 |
| 2017 Valley Oak Nacho Cheese Botulism outbreak | nacho cheese | 10 | 1 |
| 2015–present European listeriosis outbreak | Frozen corn suspected | 32 | 6 |
| 2013–2014 Danish listeriosis outbreak | Spiced lamb roll, pork, sausages, bacon, liver pâté etc. | 40 | 15 |
| 2011 Germany E. coli O104:H4 outbreak | fenugreek sprouts | 4000 | 53 |
| 2011 United States listeriosis outbreak in cantaloupes | cantaloupe | 146 | 303 |
| 2008 Canada listeriosis outbreak | cold cuts | 50 | 22 |
| 2008 United States salmonellosis outbreak in peanuts | peanuts | 200 | 9 |
| 2006 North American E. coli O157:H7 outbreak in spinach | spinach | 205 | 3 |
| 2005 South Wales E. coli O157 outbreak | meat | 157 | 1 |
| 2003 United States hepatitis A outbreak | green onions | 555 | 3 |
| 2002 United States listeriosis outbreak in poultry | poultry | 50 | 8 |
| 1998 United States listeriosis outbreak | cold cuts and hot dogs | 100 | 20 |
| 1996 Wishaw (Scotland) E. coli outbreak | meat | 496 | 21 |
| 1996 Odwalla E. coli outbreak | unpasteurized apple juice | 66 | 1 |
| Salmonella in ice cream | ice cream | 224 | 0 |
| 1993 Jack in the Box E. coli outbreak | undercooked hamburgers | 700 | 4 |
| 1985 California listeriosis outbreak in cheese | queso fresco | 86 | 50 |
| 1985 United States salmonellosis outbreak in milk | milk | 5295 | 9 |
| 2008 Chinese milk scandal | melamine and urea | 300,000 | 6 |
| 1981 Spain rapeseed oil toxicity | possibly aniline | 25,000 | 600 |
| 1971 Iraq poison grain disaster | methylmercury | 650 | 650 |
| Food Quality | Food Fraud | Motivation: Economic Gain |
|---|---|---|
| Food Safety | Food Defence | Harm including health, economic, terror |
| Unintentional | Intentional |
| Criticality Criteria | Scale |
|---|---|
| “Loss of over 10,000 lives OR loss of more than $100 billion” | 9–10 |
| “Loss of life is between 1000 and 10,000 OR loss of between $10 and $100 billion (note: if looking on a company level, loss of between 61 and 90% of the total economic value for which you are concerned)” | 7–8 |
| “Loss of life between 100 and 1000 OR loss of between $1 and $10 billion (note: if looking on a company level, loss of between 31 and 60% of the total economic value for which you are concerned)” | 5–6 |
| “Loss of life less than 100 OR loss of between $100 million and $1 billion (note: if looking on a company level, loss of between 10 and 30% of the total economic value for which you are concerned)” | 3–4 |
| “No loss of life OR loss of less than $100 million (note: if looking on a 1–2 company level, loss of >10% of the total economic value for which you are concerned)” | 1–2 |
| Accessibility Criteria | Scale |
| “Easily accessible (e.g., the target is outside the building, and no perimeter fence). Limited physical or human barriers or observation. The attacker has relatively unlimited access to the target. The attack can be carried out using medium or large volumes of contaminant without undue concern for detection. Multiple sources of information concerning the facility and the target are easily available.” | 9–10 |
| “Accessible (e.g., the target is inside the building but in an unsecured part of the facility). Human observation and physical barriers are limited. The attacker has access to the target for an hour or less. The attack can be carried out with moderate to large volumes of contaminant but requires the use of stealth. Only limited specific information is available on the facility and the target.” | 7–8 |
| “Partially accessible (e.g., inside building, but in a relatively unsecured, but busy, part of the facility). Under constant possible human observation. Some physical barriers may be present, contaminants must be disguised, and time limitations are significant. Only general, non-specific information is available on the facility and the target.” | 5–6 |
| “Hardly accessible (e.g., inside building in a secured part of the facility). Human observation and physical barriers with an established means of detection. Access is generally restricted to operators or authorized persons. Contaminants must be disguised, and time limitations are extreme. Limited general information available on the facility and the target.” | 3–4 |
| “Not accessible. Physical barriers, alarms, human observation, and defined intervention means are in place. The attacker can access the target for less than 5 min with all equipment carried in pockets. No useful publicly available information concerning the target.” | 1–2 |
| Vulnerability Criteria | Scale |
| “Target characteristics allow for easy introduction of sufficient agents to achieve an aim.” | 9–10 |
| “Target characteristics almost always allow for the introduction of sufficient agents to achieve an aim.” | 7–8 |
| “Target characteristics allow 30 to 60% probability that sufficient agents can be added to achieve an aim.” | 5–6 |
| “Target characteristics allow moderate probability (10 to 30%) that sufficient agents can be added to achieve an aim.” | 3–4 |
| “Target characteristics allow low probability (less than 10%) sufficient agents can be added to achieve an aim.” | 1–2 |
| Effect Criteria | Scale |
| “Greater than 50% of the system’s production impacted” | 9–10 |
| “25–50% of the system’s production impacted” | 7–8 |
| “10–25% of the system’s production impacted” | 5–6 |
| “1–10% of the system’s production impacted” | 3–4 |
| “Less than 1% of system’s production impacted” | 1–2 |
| Recognizability Criteria | Scale |
| “The target is recognizable and requires little or no training for recognition.” | 9–10 |
| “The target is easily recognizable and requires only a small amount of training for recognition.” | 7–8 |
| “The target is difficult to recognize or might be confused with other targets or target components and requires some training for recognition.” | 5–6 |
| “The target is difficult to recognize, and it is easily confused with other targets or components and requires extensive training for recognition.” | 3–4 |
| “The target cannot be recognized under any conditions, except by experts.” | 1–2 |
| Shock Criteria | Scale |
| “Target has primary historical, cultural, religious, or other symbolic importance. Losing over 10,000 lives. Significant impact on sensitive subpopulations, e.g., children or elderly. National economic impact more than $100 billion.” | 9–10 |
| “Target has high historical, cultural, religious or other symbolic importance. Loss of between 1000 and 10,000 lives. Significant impact on sensitive subpopulations, e.g., children or elderly. The national economic impact is between $10 and $100 billion.” | 7–8 |
| “Target has moderate historical, cultural, religious, or other symbolic importance. Loss of life between 100 and 1000. Moderate impact on sensitive subpopulations, e.g., children or elderly. The national economic impact between $1 and $10 billion.” | 5–6 |
| “Target has little historical, cultural, religious, or other symbolic importance, loss of life less than 100. Minor impact on sensitive subpopulations, e.g., children or elderly. The national economic impact is between $100 million and $1 billion.” | 3–4 |
| “Target has no historical, cultural, religious, or other symbolic importance. Loss of life less than 10. No impact on sensitive subpopulations, e.g., children or elderly. National economic impact less than $100 million.” | 1–2 |
 | Process/Function/Stage |  | Product/Output |
 | Good practice/Policy |  | Consequence for enterprise |
 | Risk |  | Consequence for product |
 | Stakeholder (outsider) |
| No | Attackers | A Possible Method of Attack Depends on the Target of the Attack |
|---|---|---|
| 1 |  | |
| 2 |  | |
| 3 |  | |
| 4 |  | |
| Stages of the Basic OnionProduction Process | The Attribute and its Rank | Risk Indicator * | ||||||
|---|---|---|---|---|---|---|---|---|
| C | A | R | V | E | R | Shock | ||
| 1. Growing, harvesting, and transporting onions | 3 | 10 | 7 | 10 | 10 | 10 | 1 | 51 |
| 2. Acceptance of raw materials, unloading, and storage | 3 | 4 | 3 | 4 | 4 | 8 | 2 | 28 |
| 2.1. Shipments of onions from other suppliers | ||||||||
| 3. Basic processing (drying, sorting, peeling and washing, packing) | 3 | 2 | 4 | 6 | 10 | 6 | 2 | 33 |
| 4. Cold storage | 3 | 4 | 4 | 4 | 2 | 8 | 2 | 27 |
| 5. Packaging and distribution | 3 | 8 | 2 | 9 | 1 | 10 | 2 | 35 |
| Attribute (total) | 15 | 28 | 20 | 33 | 21 | 42 | 9 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wysokińska-Senkus, A.; Górna, J.; Kaźmierczak, M.; Mielcarek, P.; Senkus, P. CARVER+Shock and Business Process Management in Improving Food Safety of Primary Production. Agriculture 2022, 12, 1018. https://doi.org/10.3390/agriculture12071018
Wysokińska-Senkus A, Górna J, Kaźmierczak M, Mielcarek P, Senkus P. CARVER+Shock and Business Process Management in Improving Food Safety of Primary Production. Agriculture. 2022; 12(7):1018. https://doi.org/10.3390/agriculture12071018
Chicago/Turabian StyleWysokińska-Senkus, Aneta, Justyna Górna, Magdalena Kaźmierczak, Paweł Mielcarek, and Piotr Senkus. 2022. "CARVER+Shock and Business Process Management in Improving Food Safety of Primary Production" Agriculture 12, no. 7: 1018. https://doi.org/10.3390/agriculture12071018