Underwater Acoustic Sensor Network Data Optimization with Enhanced Void Avoidance and Routing Protocol
Main Article Content
Abstract
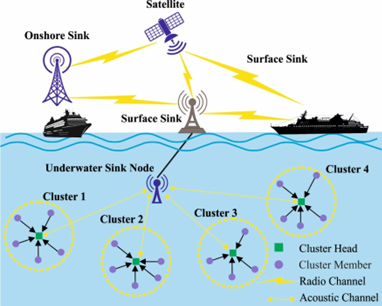
Deployment of a multi-hop underwater acoustic sensor network (UASN) in a larger region presents innovative challenges in reliable data communications and survivability of network because of the limited underwater interaction range or bandwidth and the limited energy of underwater sensor nodes. UASNs are becoming very significant in ocean exploration applications, like underwater device maintenance, ocean monitoring, ocean resource management, pollution detection, and so on. To overcome those difficulties and attains the purpose of maximizing data delivery ratio and minimizing energy consumption of underwater SNs, routing becomes necessary. In UASN, as the routing protocol will guarantee effective and reliable data communication from the source node to the destination, routing protocol model was an alluring topic for researchers. There were several routing techniques devised recently. This manuscript presents an underwater acoustic sensor network data optimization with enhanced void avoidance and routing (UASN-DAEVAR) protocol. The presented UASN-DAEVAR technique aims to present an effective data transmission process using proficient routing protocols. In the presented UASN-DAEVAR technique, a red deer algorithm (RDA) is employed in this study. In addition, the UASN-DAEVAR technique computes optimal routes in the UASN. To exhibit the effectual results of the UASN-DAEVAR technique, a wide spread experimental analysis is made. The experimental outcomes represented the enhancements of the UASN-DAEVAR model.
Article Details
How to Cite
Garg, M. ., Sharma, S. ., Balu, M. V. ., Sinha, D. K. ., Bhatt, D. P. ., & Bhagat, A. K. . (2022). Underwater Acoustic Sensor Network Data Optimization with Enhanced Void Avoidance and Routing Protocol. International Journal of Communication Networks and Information Security (IJCNIS), 14(3), 150–162. https://doi.org/10.17762/ijcnis.v14i3.5602
Issue
Section
Research Articles

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.