Devising a method for detecting “evil twin” attacks on IEEE 802.11 networks (Wi-Fi) with KNN classification model
DOI:
https://doi.org/10.15587/1729-4061.2023.282131Keywords:
IEEE 802.11, Wi-Fi, evil twin, machine learning, classification, triangulation, cyber securityAbstract
The object of research is IEEE 802.11 (Wi-Fi) networks, which are often the targets of a group of attacks called "evil twin". Research into this area is extremely important because Wi-Fi technology is a very common method of connecting to a network and is usually the first target of cybercriminals when they attack businesses. With the help of a systematic analysis of the literature focused on countering attacks of the "evil twin" type, this work identifies the main advantages of using artificial intelligence systems in the analysis of network data and identification of intrusions in Wi-Fi networks. To evaluate the effectiveness of intrusion detection and cybercrime analysis, a number of experiments as close as possible to real attacks on Wi-Fi networks were conducted.
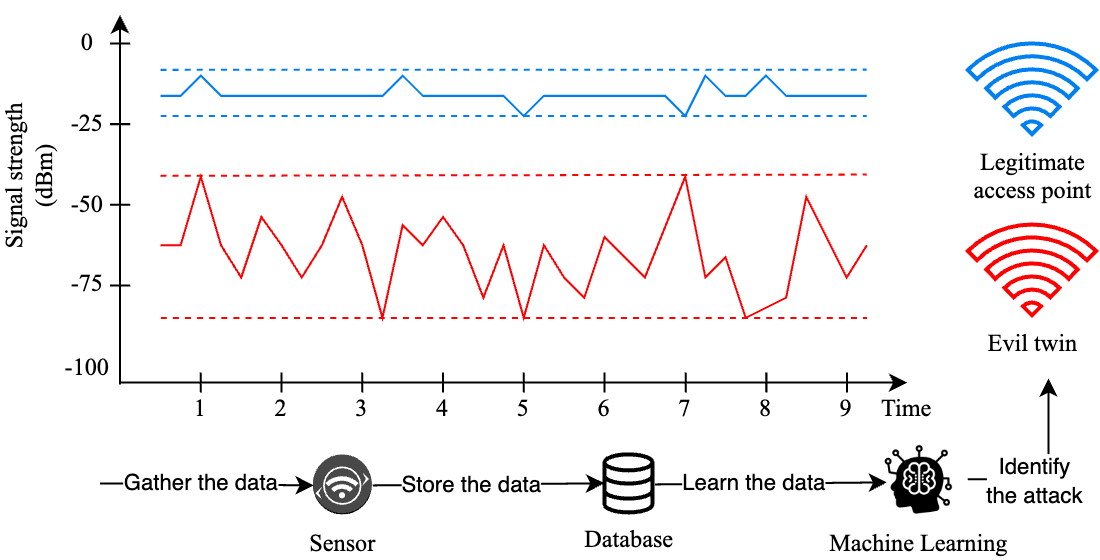
As part of the research reported in this paper, a method is proposed for detecting cybercrimes in IEEE 802.11 (Wi-Fi) wireless networks using artificial intelligence, namely a model built on the basis of the k-nearest neighbors method. This method is based on the classification of previously collected data, namely the signal strength from the access point, and then continuous comparison of the newly collected data with the trained model.
A compact and energy-efficient prototype of a hardware and software system has been designed for the implementation of monitoring, analysis of ethernet network packets and data storage based on time series. In order to reduce the load on the computer network and taking into account the limited computing power of the system, a method of data aggregation was proposed, which ensures fast transfer of information.
The results, namely 100 % of test cases (more than 7 thousand), were classified correctly, which indicates that the chosen method of data analysis will significantly increase the security of information and communication systems at the state and private levels
References
- Nagpal, J., Patil, R., Jain, V., Pokhriyal, R., Rajawat, R. (2018). Evil Twin Attack and Its Detection. International Journal of Emerging Technologies and Innovative Research, 5 (12), 169–171. doi: https://www.jetir.org/view?paper=JETIR1812326
- Bednarczyk, M., Piotrowski, Z. (2019). Will WPA3 really provide Wi-Fi security at a higher level? XII Conference on Reconnaissance and Electronic Warfare Systems. doi: https://doi.org/10.1117/12.2525020
- Vanhoef, M., Ronen, E. (2020). Dragonblood: Analyzing the Dragonfly Handshake of WPA3 and EAP-pwd. 2020 IEEE Symposium on Security and Privacy (SP). doi: https://doi.org/10.1109/sp40000.2020.00031
- Value of Wi-Fi. Wi-Fi Alliance. Available at: https://www.wi-fi.org/discover-wi-fi/value-of-wi-fi
- Forbes, G., Massie, S., Craw, S. (2020). WiFi-based Human Activity Recognition using Raspberry Pi. 2020 IEEE 32nd International Conference on Tools with Artificial Intelligence (ICTAI). doi: https://doi.org/10.1109/ictai50040.2020.00115
- Banakh, R., Piskozub, A. (2018). Attackers' Wi-Fi Devices Metadata Interception for their Location Identification. 2018 IEEE 4th International Symposium on Wireless Systems within the International Conferences on Intelligent Data Acquisition and Advanced Computing Systems (IDAACS-SWS). doi: https://doi.org/10.1109/idaacs-sws.2018.8525538
- Lu, Q., Qu, H., Zhuang, Y., Lin, X.-J., Ouyang, Y. (2018). Client-Side Evil Twin Attacks Detection Using Statistical Characteristics of 802.11 Data Frames. IEICE Transactions on Information and Systems, E101.D (10), 2465–2473. doi: https://doi.org/10.1587/transinf.2018edp7030
- Modi, V., Parekh, C. (2017). Detection of Rogue Access Point to Prevent Evil Twin Attack in Wireless Network. International Journal of Engineering Research And, V6 (04). doi: https://doi.org/10.17577/ijertv6is040102
- Kuo, E.-C., Chang, M.-S., Kao, D.-Y. (2018). User-side evil twin attack detection using time-delay statistics of TCP connection termination. 2018 20th International Conference on Advanced Communication Technology (ICACT). doi: https://doi.org/10.23919/icact.2018.8323699
- Agarwal, M., Biswas, S., Nandi, S. (2018). An Efficient Scheme to Detect Evil Twin Rogue Access Point Attack in 802.11 Wi-Fi Networks. International Journal of Wireless Information Networks, 25 (2), 130–145. doi: https://doi.org/10.1007/s10776-018-0396-1
- Banakh, R., Piskozub, A., Opirskyy, I. (2018). Detection of MAC Spoofing Attacks in IEEE 802.11 Networks Using Signal Strength from Attackers’ Devices. Advances in Computer Science for Engineering and Education, 468–477. doi: https://doi.org/10.1007/978-3-319-91008-6_47
- Harsha, S. et al. (2019). Improving Wi-Fi security against evil twin attack using light weight machine learning application. COMPUSOFT, 8 (3). Available at: https://www.researchgate.net/publication/332344245_Improving_Wi-Fi_security_against_evil_twin_attack_using_light_weight_machine_learning_application
- Dong, Y., Zampella, F., Alsehly, F. (2023). Beyond KNN: Deep Neighborhood Learning for WiFi-based Indoor Positioning Systems. 2023 IEEE Wireless Communications and Networking Conference (WCNC). doi: https://doi.org/10.1109/wcnc55385.2023.10118752
- Yang, C., Song, Y., Gu, G. (2012). Active User-Side Evil Twin Access Point Detection Using Statistical Techniques. IEEE Transactions on Information Forensics and Security, 7 (5), 1638–1651. doi: https://doi.org/10.1109/tifs.2012.2207383
- Scapy. Available at: https://scapy.net/
- InfluxDB. Available at: https://www.influxdata.com/
- NumPy. Available at: https://numpy.org/
- Pandas. Available at: https://pandas.pydata.org/
- Matplotlib. Available at: https://matplotlib.org/
- Seaborn. Available at: https://seaborn.pydata.org/
- Salkind, N. J., Frey, B. B. (2019). Statistics for people who (think they) hate statistics. SAGE Publications, 76–102.
- Scikit-Learn. Available at: https://scikit-learn.org/stable/
- Mladenova, T., Valova, I. (2021). Analysis of the KNN Classifier Distance Metrics for Bulgarian Fake News Detection. 2021 3rd International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA). doi: https://doi.org/10.1109/hora52670.2021.9461333
- Taunk, K., De, S., Verma, S., Swetapadma, A. (2019). A Brief Review of Nearest Neighbor Algorithm for Learning and Classification. 2019 International Conference on Intelligent Computing and Control Systems (ICCS). doi: https://doi.org/10.1109/iccs45141.2019.9065747
- sklearn.metrics.classification_report. Available at: https://scikit-learn.org/stable/modules/generated/sklearn.metrics.classification_report.html
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Roman Banakh, Andrian Piskozub, Ivan Opirskyy

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.