Abstract
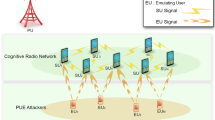
Primary User Emulation Attack (PUEA) is the most serious concern in Cognitive Radio (CR). The PUEA are malevolent users attempt to imitate primary signals and confuse CR users to prevent them from accessing vacant frequency bands. The proposed technique detects energy and assigns an appropriate threshold value for identifying attackers in the network using unique Smart Threshold detection (STD). The free space propagation model and two ray ground models are considered for finding the attacks. The authentication confirmation process (ACP) is carried out for detecting multiple PUEAs; ACP uses DNA sequencing using Binary to Excess One (BEO). The objective of this paper is to identify the PUEAs from the network and not providing the vacant frequency bands to the PUEAs and the frequent bands should be used by the primary and the secondary user efficiently. Here the secondary user will find out whether the PUEA or primary user is accessing the vacant bands using the STD-ACP technique. The simulation process is executed in the MATLAB platform. The Proposed STD-ACP finds out the attack strength, probability of detection, probability of error, probability of false alarms, and identifies the number of PUEAs. By simulating the performance of the primary user will be increased while the PUEAs can be detached from the network. The proposed STD-ACP approach is compared with attack-aware threshold selection (AATS), optimal voting rule, and K-out-of-N rule methods respectively.













Similar content being viewed by others
References
Hong, X., Chen, Z., Wang, C. X., Vorobyov, S. A., & Thompson, J. S. (2009). Cognitive radio networks. IEEE vehicular technology magazine, 4(4), 76–84.
Haghighat, M., & Sadough, S. M. S. (2015). Smart primary user emulation in cognitive radio networks: Defence strategies against radio-aware attacks and robust spectrum sensing. Transactions on Emerging Telecommunications Technologies, 26(9), 1154–1164.
Borle, K. M., Chen, B., & Du, W. K. (2015). Physical layer spectrum usage authentication in cognitive radio: Analysis and implementation. IEEE Transactions on Information Forensics and Security, 10(10), 2225–2235.
Nguyen, V. T., Villain, F., & Le Guillou, Y. (2012). Cognitive radio RF: overview and challenges. VLSI Design, 2012, 1–13. https://doi.org/10.1155/2012/716476
Rathee, G., Jaglan, N., Garg, S., Choi, B. J., & Choo, K. K. R. (2020). A secure spectrum handoff mechanism in cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 6(3), 959–969.
Ghanem, W. R., Shokair, M., & Dessouky, M. I. (2015). Investigation of PUEA in cognitive radio networks using energy detection in different channel model. Circuits and Systems: An International Journal (CSIJ), 2, 1–13.
Lee, J., & Ekici, E. (2017). Sensor selection under correlated shadowing in cognitive radio networks. IEEE Communications Letters, 21(7), 1633–1636.
Sureka, N. & Gunaseelan, K., (2019). Detection& defense against primary user emulation attack in dynamic cognitive radio networks. In 2019 Fifth International Conference on Science Technology Engineering and Mathematics (ICONSTEM) (Vol. 1, pp. 505–510). IEEE.
Neinavaie, M., Khalife, J. & Kassas, Z.M., (2020). Blind opportunistic navigation: Cognitive deciphering of partially known signals of opportunity. In Proceedings of the 33rd International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2020) (pp. 2748–2757).
Sharifi, A. A., Sharifi, M., & Niya, M. J. M. (2016). Secure cooperative spectrum sensing under primary user emulation attack in cognitive radio networks: Attack-aware threshold selection approach. AEU-International Journal of Electronics and Communications, 70(1), 95–104.
Sharifi, A. A., & Mofarreh-Bonab, M. (2018). Dynamic threshold selection approach in voting rule for detection of primary user emulation attack. Electrica, 18(2), 227–233.
Saber, M. J., & Sajad Sadough, S. M. (2017). Optimisation of cooperative spectrum sensing for cognitive radio networks in the presence of smart primary user emulation attack. Transactions on Emerging Telecommunications Technologies, 28(1), e2885.
Reyes, H., Subramaniam, S., Kaabouch, N., & Hu, W. C. (2016). A spectrum sensing technique based on autocorrelation and Euclidean distance and its comparison with energy detection for cognitive radio networks. Computers & Electrical Engineering, 52, 319–327.
Liu, X., Sun, C., Yu, W., & Zhou, M. (2021). Reinforcement-learning-based dynamic spectrum access for software-defined cognitive industrial internet of things. IEEE Transactions on Industrial Informatics, 18(6), 4244–4253.
Liu, X., Sun, C., Yau, K. L. A., & Wu, C. (2022). Joint collaborative big spectrum data sensing and reinforcement learning based dynamic spectrum access for cognitive internet of vehicles. IEEE Transactions on Intelligent Transportation Systems. https://doi.org/10.1109/TITS.2022.3175570
Hu, L., Shi, R., Mao, M., Chen, Z., Zhou, H., & Li, W. (2019). Optimal energy-efficient transmission for hybrid spectrum sharing in cooperative cognitive radio networks. China Communications, 16(6), 150–161.
Liu, X., Sun, Q., Lu, W., Wu, C., & Ding, H. (2020). Big-data-based intelligent spectrum sensing for heterogeneous spectrum communications in 5G. IEEE Wireless Communications, 27(5), 67–73.
Liu, X., Sun, C., Zhou, M., Wu, C., Peng, B., & Li, P. (2020). Reinforcement learning-based multislot double-threshold spectrum sensing with Bayesian fusion for industrial big spectrum data. IEEE Transactions on Industrial Informatics, 17(5), 3391–3400.
Sharifi, M., Sharifi, A. A., & Niya, M. J. M. (2018). Cooperative spectrum sensing in the presence of primary user emulation attack in cognitive radio network: Multi-level hypotheses test approach. Wireless Networks, 24(1), 61–68.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Anandh, O.S., Mathew, T.E., Pradeep, K.V. et al. Novel STD-ACP for detecting energy and threshold value in the network. Wireless Netw 29, 3151–3161 (2023). https://doi.org/10.1007/s11276-023-03368-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-023-03368-8