Abstract
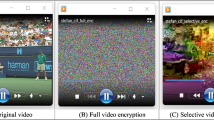
Image encryption plays a crucial role in safeguarding sensitive visual data from unauthorized access. In this research, we propose a novel hybrid approach for image encryption that combines the strength of chaotic maps and the optimization power of Genetic Algorithm (GA). The proposed method aims to enhance encryption security, complexity, and robustness to various attacks. The encryption process begins with the application of a chaotic map, specifically the Sine fusion chaos, to scramble the positions of image pixels. This chaotic map introduces chaos and non-linearity, rendering the image data indiscernible. In the subsequent step, AES and Genetic Algorithm is introduced to encrypt the image. The GA dynamically evolves the encryption process, aiming to find an optimal cipher image that maximizes encryption security and minimizes the possibility of unauthorized decryption. Experimental results demonstrate that the proposed hybrid approach outperforms traditional image encryption methods in terms of resistance to attacks, robustness, and visual obfuscation. This suggested work demonstrated the algorithm’s resilience to statistical attacks by achieving a maximum entropy of 7.99 and almost zero correlation, despite numerous analyses being conducted on the algorithm. The security analysis reveals the strength of our scheme against various cryptographic attacks. The hybrid encryption technique is suitable for applications requiring heightened image security, such as medical imaging, confidential document transfer, and satellite imagery.












Similar content being viewed by others
Data availibility
Authors confirm that this manuscript has no associated data.
References
Abdullah, A.H., Enayatifar, R., Lee, M.: A hybrid genetic algorithm and chaotic function model for image encryption. AEU-Int. J. Electron. Commun. 66, 806–816 (2012). https://doi.org/10.1016/j.aeue.2012.01.015
Attaullah, Shah, T., Jamal, S.S.: An improved chaotic cryptosystem for image encryption and digital watermarking. Wirel. Pers. Commun. 110, 1429–1442 (2020). https://doi.org/10.1007/s11277-019-06793-1
Belazi, A., Abd El-Latif, A.A., Belghith, S.: A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process. 128, 155–170 (2016). https://doi.org/10.1016/j.sigpro.2016.03.021
Benaissi, S., Chikouche, N., Hamza, R.: A novel image encryption algorithm based on hybrid chaotic maps using a key image. Optik 272, 170316 (2023). https://doi.org/10.1016/j.ijleo.2022.170316
Bhowmik, S., Acharyya, S.: Image encryption approach using improved chaotic system incorporated with differential evolution and genetic algorithm. J. Inf. Secur. Appl. 72, 103391 (2023). https://doi.org/10.1016/j.jisa.2022.103391
Cavusoglu, Ü., Kaçar, S.: A novel parallel image encryption algorithm based on chaos. Cluster Comput. 22, 1211–1223 (2019). https://doi.org/10.1007/s10586-018-02895-w
Chai, X.: An image encryption algorithm based on bit level Brownian motion and new chaotic systems. Multimed. Tools Appl. 76, 1159–1175 (2017). https://doi.org/10.1007/s11042-015-3088-1
Chai, X., Gan, Z., Zhang, M.: A fast chaos-based image encryption scheme with a novel plain image-related swapping block permutation and block diffusion. Multimed. Tools Appl. 76, 15561–15585 (2017). https://doi.org/10.1007/s11042-016-3858-4
Chai, X., Gan, Z., Yuan, K., Chen, Y., Liu, X.: A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput. Appl. 31, 219–237 (2019). https://doi.org/10.1007/s00521-017-2993-9
Robert, L.D.: Introduction to Chaotic Dynamical Systems. Chapman Hall CRC, Boca Raton (2021)
Enayatifar, R., Abdullah, A.H., Isnin, I.F., Altameem, A., Lee, M.: Image encryption using a synchronous permutation-diffusion technique. Opt. Lasers Eng. 90, 146–154 (2017). https://doi.org/10.1016/j.optlaseng.2016.10.006
Farah, M.B., Guesmi, R., Kachouri, A., Samet, M.: A novel chaos based optical image encryption using fractional Fourier transform and DNA sequence operation. Opt. Laser Technol. 121, 105777 (2020). https://doi.org/10.1016/j.optlastec.2019.105777
Feldman, D.P.: Chaos and Fractals: An Elementary Introduction. Oxford University Press, Oxford (2012)
Fridrich, J.: Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 8, 1259–1284 (1998). https://doi.org/10.1142/S021812749800098X
Gayathri, J., Subashini, S.: A survey on security and efficiency issues in chaotic image encryption. Int. J. Inf. Comput. Secur. 8, 347–381 (2016). https://doi.org/10.1504/IJICS.2016.080427
Ghazvini, M., Mirzadi, M., Parvar, N.: A modified method for image encryption based on chaotic map and genetic algorithm. Multimed. Tools Appl. 79, 26927–26950 (2020). https://doi.org/10.1007/s11042-020-09058-3
Hu, T., Liu, Y., Gong, L.H., Ouyang, C.J.: An image encryption scheme combining chaos with cycle operation for DNA sequences. Nonlinear Dyn. 87, 51–66 (2017). https://doi.org/10.1007/s11071-016-3024-6
Hua, Z., Zhou, Y.: Image encryption using 2D Logistic-adjusted-Sine map. Inf. Sci. 339, 237–253 (2016). https://doi.org/10.1016/j.ins.2016.01.017
Hussain, S., Asif, M., Shah, T., Mahboob, A., Eldin, S.M.: Redesigning the serpent algorithm by PA-Loop and its image encryption application. IEEE Access 11, 29698–29710 (2023). https://doi.org/10.1109/ACCESS.2023.3261568
Kaur, M., Kumar, V.: A comprehensive review on image encryption techniques. Arch. Comput. Methods Eng. 27, 15–43 (2020). https://doi.org/10.1007/s11831-018-9298-8
Khalid, I., Shah, T., Eldin, S.M., Shah, D., Asif, M., Saddique, I.: An integrated image encryption scheme based on elliptic curve. IEEE Access 11, 5483–5501 (2022). https://doi.org/10.1109/ACCESS.2022.3230096
Khan, M.: A novel image encryption scheme based on multiple chaotic S-boxes. Nonlinear Dyn. 82, 527–533 (2015). https://doi.org/10.1007/s11071-015-2173-3
Khan, M., Jamal, S.S., Hazzazi, M.M., Ali, K.M., Hussain, I., Asif, M.: An efficient image encryption scheme based on double affine substitution box and chaotic system. Integration 81, 108–122 (2021). https://doi.org/10.1016/j.vlsi.2021.05.007
Khan, M., Shah, T.: A novel statistical analysis of chaotic S-box in image encryption. 3D Res. 5, 1–8 (2014). https://doi.org/10.1007/s13319-014-0016-5
Lambora, A., Gupta, K., Chopra, K.: Genetic algorithm: a literature review. In: 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon). IEEE, pp. 380–384 (2019). https://doi.org/10.1109/COMITCon.2019.8862255
Li, B., Liao, X., Jiang, Y.: A novel image encryption scheme based on improved random number generator and its implementation. Nonlinear Dyn. 95, 1781–1805 (2019). https://doi.org/10.1007/s11071-018-4659-2
Li, C., Luo, G., Qin, K., Li, C.: An image encryption scheme based on chaotic tent map. Nonlinear Dyn. 87, 127–133 (2017). https://doi.org/10.1007/s11071-016-3030-8
Li, C., Zhang, Y., Xie, E.Y.: When an attacker meets a cipher-image in 2018: a year in review. J. Inf. Secur. Appl. 48, 102361 (2019)
Li, Y., Wang, C., Chen, H.: A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt. Lasers Eng. 90, 238–246 (2017). https://doi.org/10.1016/j.optlaseng.2016.10.020
Li, Z., Peng, C., Li, L., Zhu, X.: A novel plaintext-related image encryption scheme using hyper-chaotic system. Nonlinear Dyn. 94, 1319–1333 (2018). https://doi.org/10.1007/s11071-018-4426-4
Lin, C.H., Wu, J.X., Chen, P.Y., Lai, H.Y., Li, C.M., Kuo, C.L., Pai, N.S.: Intelligent symmetric cryptography with chaotic map and quantum based key generator for medical images infosecurity. IEEE Access 9, 118624–118639 (2021). https://doi.org/10.1109/ACCESS.2021.3107608
Liu, H., Wang, X.: Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Opt. Commun. 284, 3895–3903 (2011). https://doi.org/10.1016/j.optcom.2011.04.001
Liu, H., Wang, X.: Image encryption using DNA complementary rule and chaotic maps. Appl. Soft Comput. 12, 1457–1466 (2012). https://doi.org/10.1016/j.asoc.2012.01.016
Liu, W., Sun, K., Zhu, C.: A fast image encryption algorithm based on chaotic map. Opt. Lasers Eng. 84, 26–36 (2016). https://doi.org/10.1016/j.optlaseng.2016.03.019
Liu, Y., Wang, J., Fan, J., Gong, L.: Image encryption algorithm based on chaotic system and dynamic S-boxes composed of DNA sequences. Multimed. Tools Appl. 75, 4363–4382 (2016). https://doi.org/10.1007/s11042-015-2479-7
Luo, Y., Ouyang, X., Liu, J., Cao, L.: An image encryption method based on elliptic curve Elgamal encryption and chaotic systems. IEEE Access 7, 38507–38522 (2019). https://doi.org/10.1109/ACCESS.2019.2906052
Mahalingam, H., Veeramalai, T., Menon, A.R., Amirtharajan, R.: Dual-domain image encryption in unsecure medium—a secure communication perspective. Mathematics 11, 1–23 (2023). https://doi.org/10.3390/math11020457
Mahalingam, H., Velupillai Meikandan, P., Thenmozhi, K., Moria, K.M., Lakshmi, C., Chidambaram, N., Amirtharajan, R.: Neural attractor-based adaptive key generator with DNA-coded security and privacy framework for multimedia data in cloud environments. Mathematics 11, 1–23 (2023). https://doi.org/10.3390/math11081769
Mahboob, A., Asif, M., Nadeem, M., Saleem, A., Eldin, S.M., Siddique, I.: A cryptographic scheme for construction of substitution boxes using quantic fractional transformation. IEEE Access 10, 132908–132916 (2022). https://doi.org/10.1109/ACCESS.2022.3230141
Mahboob, A., Asif, M., Siddique, I., Saleem, A., Nadeem, M., Grzelczyk, D., Awrejcewicz, J.: A novel construction of substitution box based on polynomial mapped and finite field with image encryption application. IEEE Access 10, 119244–119258 (2022). https://doi.org/10.1109/ACCESS.2022.3218643
Mahboob, A., Siddique, I., Asif, M., Nadeem, M., Saleem, A.: Construction of highly non linear component of block cipher based on McLaurin series and Mellin transformation with application in image encryption. Multimed. Tools Appl. 83(3), 7159–7177 (2024). https://doi.org/10.1007/s11042-023-15965-y
Mirjalili, S.: Evolutionary Algorithms and Neural Networks. Studies in Computational Intelligence, p. 780. Springer, Berlin (2019)
Mozaffari, S.: Parallel image encryption with bitplane decomposition and genetic algorithm. Multimed. Tools Appl. 77, 25799–25819 (2018). https://doi.org/10.1007/s11042-018-5817-8
Nepomuceno, E.G., Nardo, L.G., Arias-Garcia, J., Butusov, D.N., Tutueva, A.: Image encryption based on the pseudo-orbits from 1D chaotic map. Chaos Interdiscip. J. Nonlinear Sci. (2019). https://doi.org/10.1063/1.5099261
Noshadian, S., Ebrahimzade, A., Kazemitabar, S.J.: Optimizing chaos based image encryption. Multimed. Tools Appl. 77, 25569–25590 (2018). https://doi.org/10.1007/s11042-018-5807-x
Pak, C., Huang, L.: A new color image encryption using combination of the 1D chaotic map. Signal Process. 138, 129–137 (2017). https://doi.org/10.1016/j.sigpro.2017.03.011
Panwar, K., Purwar, R.K., Jain, A.: Cryptanalysis and improvement of a color image encryption scheme based on DNA sequences and multiple 1D chaotic maps. Int. J. Bifurc. Chaos 29(08), 1950103 (2019). https://doi.org/10.1142/S0218127419501037
Pareek, N.K., Patidar, V., Sud, K.K.: Image encryption using chaotic logistic map. Image Vis. Comput. 24, 926–934 (2006). https://doi.org/10.1016/j.imavis.2006.02.021
Parida, P., Pradhan, C., Gao, X.Z., Roy, D.S., Barik, R.K.: Image encryption and authentication with elliptic curve cryptography and multidimensional chaotic maps. IEEE Access 9, 76191–76204 (2021). https://doi.org/10.1109/ACCESS.2021.3072075
Peitgen, H.O., Jürgens, H., Saupe, D., Feigenbaum, M.J.: Chaos and Fractals: New Frontiers of Science, vol. 106, pp. 560–604. Springer, New York (2004)
Sahari, M.L., Boukemara, I.: A pseudo-random numbers generator based on a novel 3D chaotic map with an application to color image encryption. Nonlinear Dyn. 94, 723–744 (2018). https://doi.org/10.1007/s11071-018-4390-z
Sivanandam, S.N., Sumathi, S., Deepa, S.N.: Introduction to Fuzzy Logic Using MATLAB. Springer, Berlin (2007)
Song, W., Zheng, Y., Fu, C., Shan, P.: A novel batch image encryption algorithm using parallel computing. Inf. Sci. 518, 211–224 (2020). https://doi.org/10.1016/j.ins.2020.01.009
Tewani, R., Garg, Y., Bagga, J.S., Singh, A., Bhalsodia, R.: Image encryption using permutation-diffusion approach. In: Advances in Data Sciences, Security and Applications: Proceedings of ICDSSA 2019, pp. 363–373. Springer, Singapore (2020)
Wang, X., Feng, L., Li, R., Zhang, F.: A fast image encryption algorithm based on non-adjacent dynamically coupled map lattice model. Nonlinear Dyn. 95, 2797–2824 (2019). https://doi.org/10.1007/s11071-018-4723-y
Wang, X., Wang, Y., Zhu, X., Luo, C.: A novel chaotic algorithm for image encryption utilizing one-time pad based on pixel level and DNA level. Opt. Lasers Eng. 125, 1–12 (2020). https://doi.org/10.1016/j.optlaseng.2019.105851
Wang, X.Y., Li, Z.M.: A color image encryption algorithm based on Hopfield chaotic neural network. Opt. Lasers Eng. 115, 107–118 (2019). https://doi.org/10.1016/j.optlaseng.2018.11.010
Wang, X.Y., Gu, S.X., Zhang, Y.Q.: Novel image encryption algorithm based on cycle shift and chaotic system. Opt. Lasers Eng. 68, 126–134 (2015). https://doi.org/10.1016/j.optlaseng.2014.12.025
Xu, L., Gou, X., Li, Z., Li, J.: A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt. Lasers Eng. 91, 41–52 (2017). https://doi.org/10.1016/j.optlaseng.2016.10.012
Yaghouti Niyat, A., Moattar, M.H.: Color image encryption based on hybrid chaotic system and DNA sequences. Multimed. Tools Appl. 79, 1497–1518 (2020). https://doi.org/10.1007/s11042-019-08247-z
Ye, G.: Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recognit. Lett. 31, 347–354 (2010). https://doi.org/10.1016/j.patrec.2009.11.008
Ye, G., Pan, C., Huang, X., Mei, Q.: An efficient pixel-level chaotic image encryption algorithm. Nonlinear Dyn. 94, 745–756 (2018). https://doi.org/10.1007/s11071-018-4391-y
Yosefnezhad Irani, B., Ayubi, P., Amani Jabalkandi, F., Yousefi Valandar, M., Jafari Barani, M.: Digital image scrambling based on a new one-dimensional coupled Sine map. Nonlinear Dyn. 97, 2693–2721 (2019). https://doi.org/10.1007/s11071-019-05157-5
Zhan, K., Wei, D., Shi, J., Yu, J.: Cross-utilizing hyperchaotic and DNA sequences for image encryption. J. Electron. Imaging 26, 013021–013021 (2017). https://doi.org/10.1117/1.JEI.26.1.013021
Zhao, L., Adhikari, A., Xiao, D., Sakurai, K.: On the security analysis of an image scrambling encryption of pixel bit and its improved scheme based on self-correlation encryption. Commun. Nonlinear Sci. Numer. Simul. 17, 3303–3327 (2012). https://doi.org/10.1016/j.cnsns.2011.12.015
Zhu, S., Deng, X., Zhang, W., Zhu, C.: Secure image encryption scheme based on a new robust chaotic map and strong S-box. Math. Comput. Simul. 207, 322–346 (2023). https://doi.org/10.1016/j.matcom.2022.12.025
Funding
The authors have not received any funding.
Author information
Authors and Affiliations
Contributions
Both authors contributed to the study conception and design. Material preparation and analysis were performed by S. K. The first draft of the manuscript was written S. K. Supervision, reviewing and editing were done by D. S.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest related to the research presented in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kumar, S., Sharma, D. Image scrambling encryption using chaotic map and genetic algorithm: a hybrid approach for enhanced security. Nonlinear Dyn (2024). https://doi.org/10.1007/s11071-024-09670-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11071-024-09670-0