Abstract
Academics are both owners and users of copyrighted material. Complex, vague, and ever-changing copyright law creates problems related to copyright for academicians and students who want to access works and digital products. It is important to increase the awareness of these individuals in order to prevent these problems. In this study, it is aimed to classify academicians and graduate students according to their awareness of the copyright of digital products. Chi-Squared Automatic Interaction Detector (CHAID), one of the Decision Tree (DT) algorithms, was applied to data obtained by questionnaire from academicians and graduate students working in different universities in Turkey. According to the findings of the DT models obtained, the most important variables that affect whether academicians and graduate students obtain digital products legally are found to be age, gender and level of computer use. 60.6% of academicians and graduate students and all those who are in the young age group and who can use computers at an advanced level use pirated software. Age-related concepts are Free Software and Copyleft, and the level of knowledge about these concepts is low. Most academicians and graduate students do not download cracking programs from the internet; do not use the work of others without attribution, and do not share their own licensed software with their friends. When it comes to copyright violations, younger people think that downloading content should be free, while most middle-aged and older people disagree. Although all academicians and graduate students think that the person who violates copyright does not care about social responsibility, academicians agree with this idea more than students. The reasons for copyright violations were determined as insufficient law/legislation, financial reasons and the belief that they would not be caught.









Similar content being viewed by others
Data availability
The datasets used and/or analysed during the current study are available from the corresponding author on reasonable request.
Change history
05 July 2022
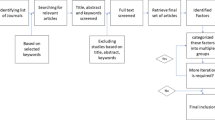
Springer Nature’s version of this paper was updated: In the pdf version, Section numbers and placement of Figures 7-9 were revised.
References
Adebayo, A. O., & Chaubey, M. S. (2019). Data mining classification techniques on the analysis of student’s performance. Global Scientific Journal GSJ, 7(4), 79–95
Agarwal, S., Pandey, G. N., & Tiwari, M. D. (2012). Data mining in education: data classification and decision tree approach. International Journal of e-Education, e-Business, E-Management and e-Learning, 2(2), 140–144
Aggarwal, C. C. (2015). An introduction to data classification. (Edited by Aggarwal, C. C.) Data Classification Algorithms and Applications. IBM T. J. Watson Research Center Yorktown Heights, New York, USA Taylor & Francis Group
Albayrak, A. S., & Koltan Yılmaz, S. (2009). Data mining: Decision tree algorithms and an application on ise data. Suleyman Demirel University The Journal of Faculty of Economics and Administrative Sciences, 14(1), 31–52
Al-Rafee, S., & Cronan, T. P. (2006). Digital piracy: Factors that influence attitude toward behavior. Journal Of Business Ethics, 63, 237–259. https://doi.org/10.1007/s10551-005-1902-9
Al-Rafee, S., & Rouibah, K. (2010). The fight against digital piracy: An experiment. Telematics and Informatics, 27(3), 283–292. https://doi.org/10.1016/j.tele.2009.12.002
American University Library (2010). What faculty need to know about copyright for teaching. https://www.american.edu/library/documents/upload/copyright_for_teaching.pdf, 18.04.2022.
Annasaheb, A. B., & Verma, V. K. (2016). Data mining classification techniques: A recent survey. International Journal of Emerging Technologies in Engineering Research (IJETER), 4(8), 51–54
Atanasova, I. (2019). Copyright infringement in digital environment. Economics & Law, 1(1), 13–22
Begum, I., & Sharma, H. K. (2018). Piracy: A threat to academicians and publishers. Journal of Intellectual Property Rights, 23, 261–269
Besimoğlu, C. (2007). The differences between disciplines in the academisians usage of electronic journals. Unpublished master thesis. Hacettepe University, Social Science Institute, Ankara
Butland, N. C., & Sullivan, J. J. (2018). Pirate tales from the deep [Web]: An exploration of online copyright infringement in the digital age.University of Massachusetts Law Review, 13 (1), Article 2.
Byrne, B. M. (1998). Structural equation modeling with lisrel, prelis and simlis: Basic concepts, aplications and programming. Mahwah, NJ: Lawrence Erlbaum Associates
Çelik, A. (2018). Investigation levels about of faculty of education students’ awareness copyright issues in relation to digital products. Unpublished master thesis. Hacettepe University, Institute of Education Science, Ankara
Çetinkaya, Z., & Horasan, F. (2021). Decision trees in large data sets. UMAGD, 13(1), 140–151
Chaouch, K. (2018). Digital copyright issues in Moroccan scientific research and higher education: The need for up-to-date legislation. (Editors: Taubman, A. et. al.) Research papers from the 2018 regional wipo-wto colloquium for ip teachers and scholars in Africa, 168–183. WIPO Academy and the WTO Intellectual Property, Government Procurement and Competition Division
Chiang, E., & Assane, D. (2002). Software copyright infringement among college students. Applied Economics, 34(2), 157–166. DOI: https://doi.org/10.1080/000368400110034253
Copyleft.org (2021). What is copyleft? https://copyleft.org/ access date: 17.6.2021
Dawson, P. H., & Yang, S. Q. (2016). Institutional repositories, open access and copyright: What are the practices and implications? Science & Technology Libraries, 35(4), 279–294. DOI:https://doi.org/10.1080/0194262X.2016.1224994
Dela Cruz, A. P. (2018). Predicting the relapse category in patients with tuberculosis: A Chi-Square Automatic Interaction Detector (CHAID) decision tree analysis. Open Journal of Social Sciences, 6, 29–36. https://doi.org/10.4236/jss.2018.612003
Demirtel, H., & Sağıroğlu, Ş. (2011). Copylefted software: What and how secure are they? TÜBAV Journal of Science, 4(1), 52–63. Retrieved from https://dergipark.org.tr/en/pub/tubav/issue/21522/230954
Di Valentino, L. (2015). Awareness and perception of copyright among teaching faculty at Canadian universities. Partnership: The Canadian Journal of Library and Information Practice and Research, 10(2), 1–16. https://doi.org/10.21083/partnership.v10i2.3556
Díaz-Perez, F. M., & Bethencourt-Cejas, B. (2016). CHAID algorithm as an appropriate analytical method for tourism market segmentation. Journal of Destination Marketing & Management, 5, 275–282
Dryden, J. (2014). Just let it go? Controlling reuse of online holdings. Archivaria, 77, 43–71
Durica, M., Frnda, J., & Svabova, L. (2019). Decision tree based model of business failure prediction for Polish companies. Oeconomia Copernicana, 10(3), 453–469. 10.24136/ oc.2019.022
Elsayad, A. M., Al-Dhaifallah, M., & Nassef, A. M. (2018). Analysis and Diagnosis of Erythemato-Squamous Diseases using CHAID Decision Trees. 15th International Multi-Conference on Systems, Signals & Devices (SSD), 252–262
Federal Ministry of Education and Research (2020). Copyright in Academic Work - An Overview for Research, Teaching and Libraries. https://ctnr.med.uni-rostock.de/fileadmin/Zentren/ctnr/Download/Handreichung_UrhWissG_eng.pdf, 01.04.2022
Fitriasih, R., Hati, S. R. H., & Achyar, A. (2019). Piracy behavior among university students. In: Education excellence and innovation management through vision 2020, 6930–6941. 33rd International-Business-Information-Management-Association (IBIMA), Conference, Granada, SPAIN
Free Software Foundation (2021). What is free software? https://www.fsf.org/about/what-is-free-software access date:17.6.2021
Gan, L. L., & Koh, H. C. (2006). An empirical study of software piracy among tertiary institutions in Singapore. Information & Management, 43(5), 640–649. https://doi.org/10.1016/j.im.2006.03.005
Geçer, A. K., & Topal, A. D. (2021). Academic and postgraduate student awareness of digital product copyright issues. Information Development, 37(1), 90–104
Go, & Globe (2021). Online Piracy in Numbers – Facts and Statistics [Infographic]. https://www.go-globe.com/online-piracy/
Hafeez, M. A., Rashid, M., Tariq, H., Abideen, Z. U., Alotaibi, S. S., & Sinky, M. H. (2021). Performance improvement of decision tree: A Robust classifier using Tabu Search algorithm. Appl Sci, 11, 6728
Han, J., Kamber, M., & Pei, J. (2012). Data mining concepts and techniques. Waltham, USA: Morgan Kaufmann Publishers is an imprint of Elsevier, Third Edition
He, C., & Lu, K. (2018). Risk management in SMEs with financial and nonfinancial indicators using business intelligence methods. Integrated Economy and Society: Diversity, Creativity and Technology MakeLearn and TIIM International Conference, 16–18 May, Naples, Italy
Horava, T. (2011). Copyright discourse in the academy: Values, policies, and technology. Academic Matters Journal. https://academicmatters.ca/copyright-discourse-in-the-academy-values-policies-and-technology/
Hsu, H. C., & Kang, S. K. (2007). CHAID- based segmentation: International visitors׳ trip characteristics and perceptions. Journal of Travel Research, 46, 207–216. DOI: https://doi.org/10.1177/0047287507299571
Isı, A., Özaydin, Ö., & Cemrek, F. (2014). Determination of factors affecting individuals’ investment behaviour using CHAID analysis. Journal of Economics Finance and Accounting, 1(4), 273–284
Jamali, H. R. (2017). Copyright compliance and infringement in ResearchGate full-text journal articles. Scientometrics, 112, 241–254. https://doi.org/10.1007/s11192-017-2291-4
Jing, L. (2021). Why is piracy such a problem in Europe? Red points. https://www.redpoints.com/blog/piracy-in-europe/
Kass, G. V. (1980). An exploratory technique for investigating large quantities of categorical data. Journal of the Royal Statistical Society Series C (Applied Statistics), 29(2), 119–127
Kavcar, G. Türkiye’de Telif Hakları Hukuku Bağlamında İnternet Ortamında Telif Haklarının Korunması (Protection of Copyrights on the Internet in the Context of Copyright Law in Turkey). Kılınç Law, & Consulting (2020). https://kilinclaw.com.tr/telif-haklari-hukukunda-internet-ortaminda-telif-haklarinin-korunmasi/
Kesavaraj, G., & Sukumaran, S. (2013). A Study on Classification Techniques in Data Mining. 4th ICCCNT, July 4–6, Tiruchengode, India
Kline, R. B. (1998). Principles and practice of structural equation modeling. NY: Guilford Press; 1998
Konstantakis, N. I., Palaigeorgiou, G. E., Siozos, P. D., & Tsoukalas, I. A. (2010). What do computer science students think about software piracy? Behaviour & Information Technology, 29(3), 277–285. Doi: https://doi.org/10.1080/01449290902765076
KuklaGryz, A., Tyrowicz, J., & Krawczyk, M. (2021). Digital piracy and the perception of price fairness: evidence from a field experiment. Journal of Cultural Economics, 45, 105–131
Kwak, W. I., & Choi, W. I. (2008). An exploratory study on the antecedent factors to the piracy of the digital copyrights. International Commerce and Information Review, 10(4), 47–62
Lagola, K. (2021). A Teacher’s Guide to Copyright and Fair Use. George Lucas Educational Foundation, https://www.edutopia.org/article/teachers-guide-copyright-and-fair-use
Legohérel, P., Hsu, C. H. C., & Daucé, B. (2015). Variety-seeking: Using the CHAID segmentation approach in analyzing the international traveler market. Tourism Management, 46, 359–366
MacCallum, B., Sugawara, MacCallum, R. C., Browne, M. W., & Sugawara, H. M. (1996). Power analysis and determination of sample size for covariance structure modeling.Psychological Methods, 1(2):130–149. doi: https://doi.org/10.1037/1082-989X.1.2.130.
Micunovic, M., & Balković, L. (2016). Author’s rights in the digital age: How Internet and peer-to-peer file sharing technology shape the perception of copyrights and copywrongs. Libellarium: journal for the research of writing, books, and cultural heritage institutions, [S.l.], 8(2), 27–64. doi:https://doi.org/10.15291/libellarium.v0i0.232
Milanović, M., & Stamenković, M. (2016). CHAID Decision Tree: Methodological frame and application. Economic Themes, 54(4), 563–586
Mishra, A., Gupta, B. B., Peraković, D., & Peñalvo, F. J. G. (2021). A Survey on Data mining classification approaches. International Conference on Smart Systems and Advanced Computing (Syscom-2021), December 25–26, 2021
Oganyan, V. A., Vinogradova, M. V., & Volkov, D. V. (2018). Internet piracy and vulnerability of digital content. European Research Studies Journal, 21(4), 735–743
Önder, E., & Uyar, Ş. (2017). CHAID Analysis to determine socioeconomic variables that explain students’ academic success. Universal Journal of Educational Research, 5(4), 608–619. DOI: https://doi.org/10.13189/ujer.2017.050410. http://www.hrpub.org
Opensource.com (2021). What is open source? https://opensource.com/resources/what-open-source access date:17.6.2021
Padil, H. M., Azmi, F., Ahmad, N. L., Shariffuddin, N., Nudin, N. A., & Razak, F. A. (2020). Awareness on Copyright Among Students. International Invention, Innovative & Creative (InIIC) Conference, Series 1/2020, eISBN: 978-967-17324-8-9, MNNF Publisher
Palus, P., & Haryanto, J. O. (2016). Consumer behavior prediction analysis based on rationalism and understanding about consequences towards pirated digital products. Jurnal Manajemen, 20(2), 325–337. https://doi.org/10.24912/jm.v20i2.51
Pham, Q. T., Dang, N. M., & Nguyen, D. T. (2020). Factors affecting on the digital piracy behavior: An empirical study in Vietnam. Journal of Theoretical and Applied Electronic Commerce Research, 15(2), 122–135
Ramsey, C., & McCaughey, M. (2012). Copyright for Academics in the Digital Age. Academe 98(5), 10–17.
Rana, S. U. (2018). Copyrights infringement control awareness and practices in advertising agencies in Pakistan. Master degree project. University of Skövde. Pakistan
Rao, A. S., Ramana, A. V., & Ramakrishna, S. (2019). Implementing the data mining approaches to classify the images with visual words. International Journal of Recent Technology and Engineering (IJRTE), 7(6S2), 901–909
Ritschard, G. (2013). CHAID and Earlier Supervised Tree. In J. J. Methods, McArdle, & G. Ritschard (Eds.), Contemporary Issues in Exploratory Data Mining in Behavioral Sciences (pp. 48–74). New York: Routeledge
Rokach, L., & Maimon, O. (2005). Decision Trees. In O. Maimon, & L. Rokach (Eds.), Data Mining and Knowledge Discovery Handbook. Boston, MA: Springer. https://doi.org/10.1007/0-387-25465-X_9
Sadiku, M. N. O., Ashaolu, T. J., Ajayi-Majebi, A., & Musa, S. M. (2021). Digital piracy. International Journal of Scientific Advances, 2(5), 797–800
Shelke, R. R., Archana, B., & Deshpande, S. A. (2020). Classification technique for super market dataset using mobile devices. Journal of Critical Reviews, 7(19), 2589–2592
Singh, D., Choudhary, N., & Samota, J. (2013). Analysis of data mining classification with decision tree technique. Global Journal of Computer Science and Technology Software & Data Engineering, 13(13), 1–5
Song, Y., & Lu, Y. (2005). Decision tree methods: applications for classification and prediction. Shanghai Arch Psychiatry, 27(2), 130–135. doi: https://doi.org/10.11919/j.issn.1002-0829.215044]
Stim, R. (2019). Copyright and Fair Use Overview (in Getting Permission 7th Edition) https://www.nolo.com/
Tam, K. Y., Feng, K. Y., & Kwan, S. (2019). The role of morality in digital piracy: Understanding the deterrent and motivational effects of moral reasoning in different piracy contexts. Journal of the Association for Information Systems, 20(5), 604–628. DOI: https://doi.org/10.17705/1jais.00545
Thongmak, M. (2014). Youth’s intention to pirate digital products: Antecedents and consequences. UK Academy for Information Systems Conference Proceedings, 6. http://aisel.aisnet.org/ukais2014/
Tijo, B. T., & Abdulazeez, A. M. (2021). Classification based on decision tree algorithm for machine learning. Journal of Applied Science and Technology Trends, 02, 01, 20–28
Tomczyk, Ł. (2021). Evaluation of digital piracy by youths. Future Internet, 13, 11, 1–26
US, & Copyright Office, What is Copyright? https://www.copyright.gov/what-is-copyright/ access date: 17.6.2021
Uzgören, N., Kara, H., & Uzgören, E. (2015). Review of submissive acts tendencies of managers by CHAID analysis: A research on manager candidate student. EKEV Akademi Dergisi, 19(61), 451–462
Van Diepen, M., & Franses, P. H. (2006). Evaluating Chi-Squared Automatic Interaction Detection. Information Systems, 31(8), 814–831
Vida, I., Kos Koklič, M., Kukar-Kinney, M., & Penz, E. (2012). Predicting consumer digital piracy behavior: The role of rationalization and perceived consequences. Journal of Research in Interactive Marketing, 6(4), 298–313. https://doi.org/10.1108/17505931211282418
Wulandari, H. (2014). Economy and technology as influential factors for digital piracy sustainability: An Indonesian case. Procedia-Social and Behavioral Sciences, 164, 112–117
Yoon, C. (2011). Theory of planned behavior and ethics theory in digital piracy: An integrated model. Journal Of Business Ethics, 100,, 405–417. https://doi.org/10.1007/s10551-010-0687-7
Funding
There is no funding in this study.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no competing interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
KOLTAN YILMAZ, Ş., DEVECİ TOPAL, A. Analysis of awareness of academicians and graduate students about digital product copyrights with chi-squared automatic interaction detector. Educ Inf Technol 27, 12743–12771 (2022). https://doi.org/10.1007/s10639-022-11142-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10639-022-11142-0