Abstract—
This article considers ensuring protection of Vehicular Ad-Hoc Networks (VANET) against malicious nodes. Characteristic performance features of VANETs and threats are analyzed, and current attacks identified. The proposed approach to security provision relies on radial basis neural networks and makes it possible to identify malicious nodes by indicators of behavior.
Similar content being viewed by others
INTRODUCTION
A subclass of mobile ad-hoc networks, Vehicular Ad hoc Networks (VANETs) are currently being actively developed and gaining popularity.
The nodes in VANETs are vehicles able to exchange information needed for motion. Such information includes motion speed, traffic conditions, road pavement condition, road accidents, etc. The main goal of VANETs is to make road traffic safer and more efficient.
Some of the VANET’s objectives include:
—helping the driver to control the motor vehicle by adjusting the car course and speed on the road, deploying navigation, and preventing collisions;
—reporting such road events as repair works, accidents, and obstacles; and
—and providing access to additional services, e.g., service payment, road conditions, and reporting the availability of parking lots.
VANETs can be potentially expanded and used all over the world. However, these networks suffer from a number of problems one of which is security. The role of information security in VANETs is critical because it directly affects public security. It becomes, therefore, necessary to develop efficient techniques of security provision in vehicular networks.
THREATS AND CURRENT ATTACKS IN VANETs
To identify the threats to which VANETs are exposed, one needs to analyze their features. As a subclass of mobile ad hoc networks, VANETs inherit their features as well. One can distinguish such features as the unavailability of a fixed topology and centralized infrastructure for exchanging messages from node to node and unstable internode connection due to wireless information transfer lines.
However, in addition to the inherited features, VANETs have such specific and VANET-typical features as [1]:
—high node movement speed, which means the dominance of one-off and short-time internode contacts;
—high probability of instantaneous load upsurge, e.g., in emergencies and other incidents, which may cause overload;
—a large number of simultaneously cooperating nodes and possibility for new participants to intrude into the network;
—a need to instantaneously react to occurring incidents and minimal time the nodes have to respond to messages; and
—constant changes in topology due to ad hoc motion of nodes.
Proceeding from the considered features, one may conclude that the most dangerous threats come from internal intruders and are intended to violate the network’s accessibility and integrity of transmitted messages. Confidentiality is a major property of security; in the context of VANETs, however, its violation is uncritical.
The attacks the intruder can make to affect the network’s integrity and accessibility are as follows:
—Packet modification attacks: a compromised node modifies packets of data that flow through the node. In the case of success, this attack may lead to communicating false information to the nodes. The attack seriously affects the integrity of data.
—Packet rejection attacks: the network’s normal run is violated when the intruder rejects completely or partially the packets passing through its node. The properties affected by these attacks are the accessibility and, to a greater extent, integrity of transferred data.
—Black or gray hole attacks: an intruding device disguises itself as a network node through which the best path to the destination node runs. There may be no connection between the intruder and the target node within the network at all. In the case of success, this attack impairs accessibility because, after the attack is over, other than optimal routes are used, which allows violation of the integrity of transferred information. The only difference between the black and the gray hole attack consists in the extent of their destructive effects. Whereas a black hole attack affects all received packets, whether by rejecting or modifying them, a gray hole attack affects only some of them.
—Sibylla’s attack: in this case, the intruder emulates the work of many identical nodes each of which appears in the network as a trusted node. Other nodes in the network perceive them as different. The packets transferred to the emulated nodes pass through only the attacker’s node. As a result, the network becomes less productive and, therefore, less accessible.
The intruder can make the above enumerated attacks by unauthorized access to a network node (automobile) and changing its behavior or introducing its proper malicious node into the network.
USING NEURAL NETWORKS IN VANETs
Today, many techniques have been elaborated to protect VANETs from various attacks. It is not always expedient to jointly use the available techniques of protection from specific attacks because of a large number of mobile nodes and decentralized network topology. Moreover, many techniques contradict each other, e.g., in required routing protocols, which makes their simultaneous work in one network impossible. In this regard, the preferable approaches for use in distributed networks are all-purpose techniques that allow protecting against the overwhelming majority of attacks.
In particular, good results for distributed networks are shown by the technique based on behavior analysis of nodes [2]. Relying on this approach, the nodes control the behavior of their neighbors in specific aspects. For example, to assess the reliability of its neighbor in retranslation of packets, a node can track whether the neighbor resends inbound traffic. The indicator elaborated during the behavior analysis is used by the node in deciding whether to cooperate with the neighbor or not.
However, since VANETs are characterized by increasingly mobile nodes and rapid replacement of cooperating neighbors, the number of internode contacts may be insufficient for unambiguously revealing a malicious node. The means proposed to solve this problem is the set of tools of neural networks. Using the indicators of behavior obtained in a certain period, one can predict a node’s intentions and thus reduce the time necessary to reveal a malicious node.
The set of tools of neural networks makes it possible to solve several tasks one of which is forecasting. The neural network’s forecasting ability stems directly from the ability to distinguish hidden dependences between input and output data and make their classification. After the learning phase, the network can forecast the future value of some sequence. The forecasting task is defined as follows: assume that there are n discrete readings {y(t1), y(t2) …, y(tk)} in successive time instants t1, t2, …, tk. The task is to predict the value of y(tk + 1) at some time instant tk + 1 in the future.
The kind of neural network that is used to solve predictive problems is a radial- basis neural network [3]. They are constructed using radial neurons the activation function of which carries nonzero values only in the vicinity of its center.
The input parameters to be supplied to the neural network are N current indicators of a certain aspect of behavior. The forecast indicator will come at the network’s exit.
The most important aspects of behavior that allow protecting against the overwhelming majority of attacks are
—packet transmission when the packet retranslation process is checked for detecting nodes that do not resend packets or resend only certain ones;
—packet integrity when packets are checked upon retranslation for integrity to ensure protection against packet modification attacks; and
—intensity of queries that shows the frequency of queries generated by a node and allows protecting against attacks related to line clogging and depletion of computational resources.
Packet transmission and integrity are defined as the number of successfully processed packets related to the overall number of packets transferred to the node. Successful processing is understood as the correct retranslation of a packet without modifying its contents. The intensity of queries can be defined as the number of queries generated per fixed interval of time.
The number of aspects of behavior can be increased depending on the task for solution. Each aspect is predicted using a respective neural network. For the architecture of the used neural network, see Fig. 1.
The input network layer receives N indicators on the basis of a particular aspect of behavior. The hidden layer contains the radial basis activation function. The output layer derives the forecast indicator of behavior by weighted summation of values generated by hidden neurons.
The number of neurons in the input layer corresponds to the number of input indicators. The number of neurons in the hidden layer depends on many factors and is defined during the tests upon reaching the required precision.
The neurons in the hidden layer are activated using the Gaussian function
where x is the input vector and \(\sigma \) and с are the activation function’s controlling parameters, referred to as the “function window width” and “center,” respectively.
Coefficients \(\sigma \) and с are defined in the network adjustment phase. Vector c takes individual random examples from the learning sample. Width \(\sigma \) is defined explicitly by heuristic selection [4].
The vector difference norm is found as the Euclidean distance according to the following equation:
The hidden layer neurons are linked in a fully connected scheme with the output layer neuron responsible for the weighted summation according to the following equation:
where ω is the weight vector that is the center of the radial basis function that corresponds to the neuron with number i.
The weights from the neurons of the hidden to the output layer are found using linear regression [5].
NEURAL NETWORK PROTECTION FOR VANET ARCHITECTURE
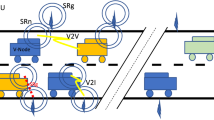
The main feature of VANETs is the need for a distributed self-organizing topology to maintain a rapid transfer of data among mobile nodes. However, this does not rule out the possibility for automobiles to communicate not only with each other but with the roadside network as well [6]. This way, the user can obtain access to various services such as payment for services, information about free parking lots, etc.
Safety will also be ensured using urban infrastructure. For the proposed network architecture see Fig. 2. The nodes in this architecture exchange necessary information that maintains traffic safety. In addition, the nodes cooperate with base stations (BSs) spread across the network’s entire service domain.
In the context of security provision, these stations are meant to cooperate with the nodes, obtain necessary indicators of behavior, and transfer these data to the processing server. The server performs the required computations using the set of neural network tools and forecasts node behavior indicators. If the indicator of some aspect is below the set threshold value, this information will be sent to all the nodes in the network via base stations. The threshold indicator at which a node will be defined as malicious is found statically during the tests.
Each node in the network decides for itself how to use the information about the malicious node received from the server. Some nodes can stop all cooperation with this node altogether; others can continue this cooperation but in restricted mode, e.g., ignoring only certain packets.
There are several strong points of using the given architecture for security provision. First of all, the complicated access to elements of urban infrastructure will prevent the intruder from negatively affecting the base stations. Second, the server responsible for security has more computational resources than do mobile nodes, which will allow complex computations.
CONCLUSIONS
This study has resulted in proposing an approach to providing protection for vehicular ad-hoc networks against internal intruder threats. The characteristic features of VANETs have been identified, and their influence on the network’s security has been determined. Protection techniques delivering good results in ad hoc networks have many features that make these methods insufficiently effective. The solution proposed to solve the problems that have emerged is the use of a radial basis neural network for forecasting node behavior indicators. The architecture has been determined in which the elaborated security provision technique will be used.
The future work plan involves modeling the work of a VANET using the proposed protection technique in the emulator for efficiency assessment. In addition, the network’s emulation will allow elaborating a more precise approach to selecting neural network parameters.
REFERENCES
Sabahi, F., Impact of threats on vehicular adhoc network security, Int. J. Comput. Theory Eng., 2012, vol. 4, no. 5, p. 840.
Zahariadis, T., et al., Energy-aware secure routing for large wireless sensor networks, WSEAS Trans. Commun., 2009, vol. 8, no. 9, pp. 981–991.
Awad, M., et al., Prediction of time series using RBF neural networks: A new approach of clustering, Int. Arab J. Inf. Technol., 2009, vol. 6, no. 2, pp. 138–143.
Haykin, S., et al., Neural Networks and Learning Machines, Upper Saddle River, NJ: Pearson, 2009, vol. 3.
Jirina, M., Radial Basis Function Neural Network with Example Weights and LMS Linear Regression Weight Setting, 2001.
Kalinin, M., Krundyshev, V., Zegzhda, P., and Belenko, V., Network security architectures for VANET, Proceedings of the 10th International Conference on Security of Information and Networks, ACM, 2017, pp. 73–79.
ACKNOWLEDGMENTS
The project results are achieved using the resources of supercomputer center of Peter the Great St.Petersburg Polytechnic University – SCC “Polytechnichesky” (www.spbstu.ru).
The project is financially supported by Ministry of Science and Higher Education of the Russian Federation, Federal Program “Researching and Development in Priority Directions of Scientific and Technological Sphere in Russia within 2014–2020” (Contract no. 14.575.21.0131, September 26, 2017, unique identifier RFMEFI57517X0131).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Translated by S. Kuznetsov
About this article
Cite this article
Ovasapyan, T.D., Moskvin, D.A. & Kalinin, M.O. Using Neural Networks to Detect Internal Intruders in VANETs. Aut. Control Comp. Sci. 52, 954–958 (2018). https://doi.org/10.3103/S0146411618080199
Received:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411618080199