Abstract
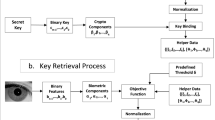
Cryptography and biometry are important components of contemporary access control systems. Cryptographic systems themselves are highly reliable but they require the exact reproduction of access keys; this cannot be done by humans, while the corresponding devices might be lost or stolen. Biometric data are always with the person; however, they vary: it is impossible to obtain the same feature values. In this paper, a way is proposed to link the cryptographic key and the biometric features of the iris. This yields a two-component key such that no original component can be extracted until the biometric features close to the original ones, i.e., the data of the same person, are presented. The connecting method (coder) and the extracting method (decoder) consist of several separate steps executed successively. To select the parameters, we solve the following discrete optimization problem: under the given threshold of the false accept rate, we minimize the value of the false reject rate. The restrictions of this optimization problem are the minimal size of the coded key and the maximal size of the final key. Numerical experiments are conducted on open-access databases (DBs).





Similar content being viewed by others
REFERENCES
A. P. Alferov, A. Yu. Zubov, A. S. Kuz’min, and A. V. Cheremushkin, Principles of Cryptography (Gelios ARV, Moscow, 2005) [in Russian].
A. L. Chmora, “Key masking using biometry,” Probl. Peredachi Inform. 47 (2), 28–143 (2011).
J. G. Daugman, “Information theory and the IrisCode,” IEEE Trans. Inform. Forensics Secur. 11, 400–409 (2016).
S. Gong, V. N. Boddeti, and A. K. Jain, “On the capacity of face representation,” arXiv: 1709.10433 (2017).
M. P. Yankov, M. A. Olsen, M. B. Stegmann, S. S. Christensen, and S. Forchhammer, “Fingerprint entropy and identification capacity estimation based on pixel-level generative modelling,” IEEE Trans. Inform. Forensics Secur. 15, 56–65 (2020).
A. I. Ivanov, P. S. Lozhnikov, and A. E. Sulavko, “Evaluation of singature verification reliability based on artificial neural networks, bayesian multivariate functional and quadratic forms,” Komp’yut. Opt. 41, 765–774 (2017).
A. Juels and M. Sudan, “A fuzzy vault scheme,” Designs, Codes Cryptogr. 38, 237–257 (2006).
J. Daugman, “How iris recognition works,” in Proceedings of the International Conference on Image Processing, Lake Buena Vista, Orlando, USA,2012, Vol. 1, pp. 33–36.
B. H. Shekar, R. K. Bharathi, J. Kittler, Y. V. Vizilter, and L. Mestestskiy, “Grid structured morphological pattern spectrum for off-line signature verification,” in Proceedings of the International Conference on Biometrics, Phuket, Thailand,2015, Vol. 8, pp. 430–435.
C. Rathgeb and A. Uhl, “A survey on biometric cryptosystems and cancelable biometrics,” EURASIP J. Inform. Secur. 3, 1–25 (2011).
A. V. Maiorov, “Neural network hash function,” Neirokomp’yut.: Razrab. Primen., No. 6, 45–48 (2009).
A. I. Ivanov, S. A. Somkin, D. Yu. Andreev, and E. A. Malygina, “Diversity metrics to watch actual biometric data distribution statistics 'fuzzy extractors' in their protection of a range,” Vestn. UrFO, Bezopasn. Inform. Sfere 2 (12), 16–23 (2014).
GOST (State Standard) R No. 52633.5-2011, Data protection. Information security technique. Automatic training of neural network converters biometry access code (2012).
Y. Sutcu, H. T. Sencar, and N. Memon, “A secure biometric authentication scheme based on robust hashing,” in Proceedings of the 7th Workshop on Multimedia and Security, New York,2005, pp. 111–116.
C. Rathgeb and A. Uhl, “Privacy preserving key generation for iris biometrics,” in Communications and Multimedia Security, Ed. by B. de Decker and I. Schaumueller-Bichl (Springer, Berlin, Heidelberg, 2010), pp. 191–200.
CASIA Iris Image Database, Institute of Automation, Chinese Academy of Sciences, 2010. http://biometrics.idealtest.org/findTotalDbByMode.do?mode=Iris.
G. Davida, Y. Frankel, and B. Matt, “On the relation of error correction and cryptography to an offline biometric based identification scheme,” in Proceedings of the Workshop on Coding and Cryptography, France, Paris,1999, pp. 129–138.
Y. Dodis, R. Ostrovsky, L. Reyzin, and A. Smith, “Fuzzy extractors: How to generate strong keys from biometrics and other noisy data,” SIAM J. Comput. 38, 97–139 (2008).
S. Yang and I. Verbauwhede, “Secure iris verification,” in Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, Honolulu, USA,2007, Vol. 2, pp. 133–136.
J.-P. Linnartz and P. Tuyls, “New shielding functions to enhance privacy and prevent misuse of biometric templates,” in Proceedings of the 4th International Conference on Audio- and Video-Based Biometric Person Authentication, Guildford, UK,2003, pp. 393–402.
A. Shamir, “How to share a secret,” Commun. ACM 22, 612–613 (1979).
Y. J. Lee, K. Bae, S. J. Lee, K. R. Park, and J. Kim, “Biometric key binding: Fuzzy vault based on iris images,” in Proceedings of the 2nd International Conference on Biometrics, Seoul, Korea,2007, pp. 800–808.
X. Wu, N. Qi, K. Wang, and D. Zhang, “An iris cryptosystem for information security,” in Proceedings of the International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Harbin, China,2008, pp. 1533–1536.
A. Juels and M. Wattenberg, “A fauzzy commitment scheme,” in Proceedings of the 6th ACM Conference on Computer and Communications Security, Singapore,1999, pp. 28–36.
F. Hao, R. Anderson, and J. Daugman, “Combining crypto with biometrics effectively,” IEEE Trans. Comput. 55, 1081–1088 (2006).
R. H. Morelos-Zaragosa, The Art of Error Correcting Coding (Wiley, New York, 2006).
A. Yu. Rubis, M. A. Lebedev, Yu. V. Vizil’ter, O. V. Vygolov, and S. Yu. Zheltov, “Comparative image filtering using monotonic morphological operators,” Komp’yut. Opt. 42, 306–311 (2018).
M. A. Lebedev, A. Yu. Rubis, Yu. V. Vizil’ter, O. V. Vygolov, and S. Yu. Zheltov, “Detecting image differences based on reference EMD-filters,” Mat. Metody Raspozn. Obrazov. 18, 116–117 (2017).
I. S. Reed and G. Solomon, “Polynomial codes over certain finite fields,” J. SIAM 8, 300–304 (1960).
S. Kanade, D. Camara, E. Krichen, D. Petrovska-Delacretaz, and B. Dorizzi, “Three factor scheme for biometric-based cryptographic key regeneration using iris,” in Proceedings of the Biometrics Symposium, Tampa, FL, USA,2008, pp. 59–64.
A. I. Ivanov, “The problem of using fuzzy extractors in statistical biology and cryptography,” Perv. Milya, No. 1, 40 (2015).
K. A. Gankin, A. N. Gneushev, and I. A. Matveev, “Iris image segmentation based on approximate methods with subsequent refinements,” J. Comput. Syst. Sci. Int. 53, 224 (2014).
V. Novik, I. Matveev, and I. Litvinchev, “Enhancing iris template matching with the optimal path method,” Wireless Networks, 1–8 (2018).
D. L. Woodard and K. Ricanek, “Iris databases,” in Encyclopedia of Biometrics, Ed. by S. Z. Li and A. Jain (Springer, Boston, MA, 2009).
P. Phillips, W. Scruggs, A. O’Toole, et al., “Frvt 2006 and Ice 2006 large-scale experimental results,” IEEE PAMI 5, 831–846 (2010).
H. Proenca and L. Alexandre, “UBIRIS: A noisy iris image database,” in Proceedings of the 13th International Conference on Image Analysis and Processing, Cagliari, Italy,2005, pp. 970–977.
www.sovereigncctv.com/panasonic-bm-et300-iris-reader.html. Accessed April 13, 2020.
www.sourcesecurity.com/lg-iris-irisaccess-3000-technical-details.html. Accessed April 13, 2020.
www.iritech.com/products/hardware/. Accessed April 13, 2020.
I. S. Reed, “A class of multiple-error-correcting codes and the decoding scheme,” Trans. IRE Profess. Group Inform. Theory 4, 38–49 (1954).
Funding
This study was partially supported by the Russian Foundation for Basic Research (grant no. 19-07-01231).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Translated by A. Muravnik
Rights and permissions
About this article
Cite this article
Zainulina, E.T., Matveev, I.A. Binding Cryptographic Keys into Biometric Data: Optimization. J. Comput. Syst. Sci. Int. 59, 699–711 (2020). https://doi.org/10.1134/S1064230720050135
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1134/S1064230720050135