Abstract
The dynamic of the secret key rate of the discrete-variable quantum key distribution (QKD) protocol over the non-Markovian quantum channel is investigated. In particular, we calculate the secret key rate for the six-state protocol over non-Markovian depolarizing channels with coloured noise and Markovian depolarizing channels with Gaussian white noise, respectively. We find that the secure secret key rate for the non-Markovian depolarizing channel will be larger than the Markovian one under the same conditions even when their upper bounds of tolerable quantum bit error rate are equal. This indicates that this coloured noise in the non-Markovian depolarizing channel can enhance the security of communication. Moreover, we show that the secret key rate fluctuates near the secure point when the coupling strength of the system with the environment is high. The results demonstrate that the non-Markovian effects of the transmission channel can have a positive impact on the security of discrete-variable QKD.
Export citation and abstract BibTeX RIS
1. Introduction
Quantum key distribution (QKD) [1–7] provides a novel way to allow two distant authorized parties, the sender Alice and the receiver Bob, to remotely establish a secret key through quantum and classical channels. Generally, the classical channel needs to be authenticated, i.e. the legitimated parties identify themselves and a third party may listen to the communication but cannot participate in it. However, the quantum channel is open so that the third party can manipulate the communication. The security of QKD originates from the fundamental principles of quantum mechanics. More precisely, the legitimated parties can estimate the security after communication, since the leakage of information in a quantum channel to eavesdropper, Eve, is quantitatively related to the degradation of communication [3].
The unconditional security of QKD schemes with the ideal system [8, 9] and practical system [10] has been proved for several years. However, the ignorance of imperfection of the practical QKD system still exists and limits Eve's attack strategy. So the unconditional security should be reconsidered under more powerful attacks introduced by Eve. To avoid the leakage of information from the loopholes of the imperfect practical QKD system, many potential attacks [11–20] have been proposed recently. The known considerations of the imperfection of the practical QKD system are focused on the practical system devices, and the quantum channels are usually approximately considered to be Markovian, i.e. the correlation time between the system and environment is infinitely short so that the memory effects can be neglected. In practice, the correlations between the system and environment exist for a small finite period of time, which leads to the quantum channel with memory [21]. In recent years, non-Markovian effects have been investigated in the dynamics of entanglement [22–24], quantum correlation [25], quantum channel capacity [26] and the security of continuous-variable QKD [27]. Moreover, the optical non-Markovian signatures in semiconductor quantum wires have been achieved in an experiment [28]. Interestingly, it is shown in [27] that the non-Markovian effects may be exploited to enhance the security of continuous-variable QKD and detect eavesdropping along the transmission line. However, the security analysis is addressed in Gaussian individual attacks, whereas Eve's collective attacks are not being considered.
In this paper, we explore the security of discrete-variable QKD schemes over non-Markovian quantum channels. In particular, we investigate the dynamics of the secret key rates for the six-state protocol [29, 30] by restricting consideration to collective attacks, where the transmission quantum channels are specified as non-Markovian depolarizing channels with coloured noise and the Markovian one with Gaussian white noise [21]. In contrast, we show that the secure secret key rate for the non-Markovian channels may always be larger than the Markovian ones. Moreover, we find that the nosier the channels are, the more effectively the non-Markovian effects will enhance the security of transmission. When the coupling strength of the system with the environment is high enough, the secret key rate fluctuates near the secure point.
This paper is organized as follows. In section 2, we introduce the physical model we will investigate and construct the non-Markovian depolarizing quantum channel with coloured noise. We then briefly introduce the six-state protocol, and calculate and analyse contrastively the dynamics of the secret key rates and quantum bit error rate (QBER) of the six-state protocol under collective attack for the non-Markovian and Markovian depolarizing channels in section 3. Finally, the conclusions are drawn in section 4.
2. The non-Markovian depolarizing channel with coloured noise
In this section, we introduce the physical model under study, i.e. the non-Markovian depolarizing channel with coloured noise. As known, the evolution of the quantum system can be described as a completely positive map (CPM) [31]. A known depolarizing quantum channel can be expressed as the CPM 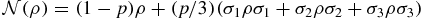 , where 0 ⩽ p ⩽ 1, and σi for i = 1, 2, 3 are Pauli operators. This CPM defines a depolarizing channel with white noise, which comes from the Markovian master equation. However, the Markovian master equation that describes the time evolution of the quantum system is an approximation, since the correlation time between the quantum system and environment is seen to be infinitely short so that the memory effects can be neglected. In practice, the correlation time is a small finite period of time, which leads to the non-Markovian master equation. In the following, we review the derivation of the depolarizing channel with coloured noise [21].
, where 0 ⩽ p ⩽ 1, and σi for i = 1, 2, 3 are Pauli operators. This CPM defines a depolarizing channel with white noise, which comes from the Markovian master equation. However, the Markovian master equation that describes the time evolution of the quantum system is an approximation, since the correlation time between the quantum system and environment is seen to be infinitely short so that the memory effects can be neglected. In practice, the correlation time is a small finite period of time, which leads to the non-Markovian master equation. In the following, we review the derivation of the depolarizing channel with coloured noise [21].
A prevailing memory kernel master equation can be described by

where K is an integral operator that depends on time acting as the form  ,
, 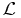 is a Lindblad superoperator describing the dynamics due to the interaction of the system and environment and ρ is the density operator of the small system of interest. The solution to the master equation (1) defines a completely positive and trace-preserving linear map
is a Lindblad superoperator describing the dynamics due to the interaction of the system and environment and ρ is the density operator of the small system of interest. The solution to the master equation (1) defines a completely positive and trace-preserving linear map  that describes the evolution of a system coupled to an environment.
that describes the evolution of a system coupled to an environment.
A master equation of the form of equation (1) arises when considering any two-level quantum system that interacts with an environment possessing random telegraph signal noise. It is possible to write a time-dependent Hamiltonian for this kind of system,
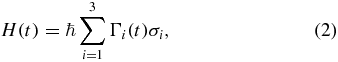
where Γi(t) are independent random variables. Each random variable can be defined as Γi(t) = aini(t). The random variable ni(t) has a Poisson distribution with a mean equal to t/2τi, while ai is an independent coin-flip random variable assuming the values ± ai. A model like this describes, for instance, a spin-1/2 particle in the presence of three orthogonal magnetic fields, each of which has a constant magnitude ai and inverts randomly in time with a distribution given by ni.
By using the von Neumann equation ![$\dot{\rho }=-({\rm i}/\hbar )[H,\rho ]=-{\rm i}\sum _{k}(t)[\sigma _{k},\rho ]$](https://content.cld.iop.org/journals/0953-4075/45/13/135501/revision1/jpb422885ieqn5.gif) , one can obtain the solution for the density operator of the form
, one can obtain the solution for the density operator of the form
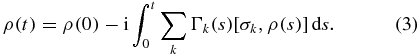
Applying the correlation functions of the random telegraph signal  , and substituting equation (3) back into the von Neumann equation and performing a stochastic average, one obtains the memory kernel master equation
, and substituting equation (3) back into the von Neumann equation and performing a stochastic average, one obtains the memory kernel master equation
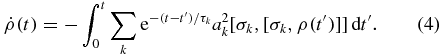
It can be seen from equation (4) that the state of the system at time t depends on its past history. It is known that the Fourier transform of the correlation function gives the power spectrum of the environment. For white noise, the delta-function correlation in time leads to a flat power spectrum for the environment, and the system is equally coupled to all frequencies of environment, while for the coloured noise, the system prefers certain frequencies and a gives the coupling strength of the system with environment while τ determines the most preferred frequencies.
By assuming that the fluctuations τi are equal, one can obtain the solution to equation (4) as a linear map  on
on  [21]. This map is a generalization of the depolarizing channel to the case of coloured noise, which can be written in the form of Kraus decomposition
[21]. This map is a generalization of the depolarizing channel to the case of coloured noise, which can be written in the form of Kraus decomposition  with Kraus operators given by
with Kraus operators given by 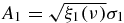 ,
, 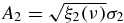 ,
,  and
and  , provided that the following conditions are all satisfied:
, provided that the following conditions are all satisfied:
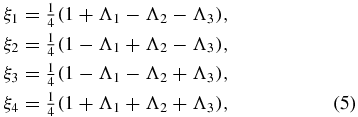
where ν = t/2τ is the dimensionless time and Λi(ν) = e−ν[cos (μiν) + sin (μiν))/μi] are damped harmonic oscillators having frequencies 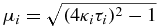 with κ2i = aj2 + a2k for i ≠ j ≠ k. The restrictions in equation (5) assure that the linear map
with κ2i = aj2 + a2k for i ≠ j ≠ k. The restrictions in equation (5) assure that the linear map  is completely positive. By assuming τ → 0 and a → ∞, the random telegraph signal reduces to a Gaussian white noise and equation (4) becomes
is completely positive. By assuming τ → 0 and a → ∞, the random telegraph signal reduces to a Gaussian white noise and equation (4) becomes ![$\dot{\rho }(t)=-\int ^{t}_{0}\delta (t-t^{\prime })\sum _{k}2a^{2}_{k}\tau [\sigma _{k},[\sigma _{k},\rho (t^{\prime })]]\,{\rm d}t^{\prime }$](https://content.cld.iop.org/journals/0953-4075/45/13/135501/revision1/jpb422885ieqn16.gif) . This leads to
. This leads to  in equation (5) with inverse lifetimes γi = 4κ2iτ. It should be pointed out that, whether in the case of coloured noise or white noise, there are examples of maps that are positive but not completely [32–34]. The map is completely positive if and only if the linear combinations in equation (5) are non-negative.
in equation (5) with inverse lifetimes γi = 4κ2iτ. It should be pointed out that, whether in the case of coloured noise or white noise, there are examples of maps that are positive but not completely [32–34]. The map is completely positive if and only if the linear combinations in equation (5) are non-negative.
3. Unconditional security of the six-state protocol over a non-Markovian depolarizing channel
The six-state protocol is similar to the well-known BB84 four-state protocol, but with an additional basis [29, 30]. In the six-state protocol, Alice first generates a random bit k = −1, 1 and chooses one basis Θ randomly out of the three bases X, Y and Z. Then Alice prepares and sends over a quantum channel a qubit with the |Θk〉 state, which is the eigenstate of the Θ basis with the eigenvalue of k/2. Bob randomly chooses one basis out of the three bases and measures the states along the chosen direction. Alice and Bob compare the bases they used via a public channel, and keep the bit value if the bases match; otherwise they discard it. Lastly, Alice and Bob repeat the above steps and apply bit error correction and privacy amplification to obtain a shared key string.
The unconditional security bounds for the six-state protocol [30] have been found in [35, 36] for the case where the quantum signals are single qubits. As usual, the proof for this prepare-and-measure (P&M) six-state scheme can be performed by an entanglement-based (EB) scheme: Alice produces the state  ; then she keeps the first qubit and sends the other one to Bob. This state shows perfectly correlated outcomes in the X and Z bases and perfectly anti-correlated outcomes in the Y basis. Bob may flip his results when he measures with Y basis. Without loss of generality, the symmetry of the six-state protocol implies that one can compute the unconditional security bound by restricting the consideration to collective attacks, and even further, to those cases such that the final state of Alice and Bob is Bell diagonal [3, 35, 36],
; then she keeps the first qubit and sends the other one to Bob. This state shows perfectly correlated outcomes in the X and Z bases and perfectly anti-correlated outcomes in the Y basis. Bob may flip his results when he measures with Y basis. Without loss of generality, the symmetry of the six-state protocol implies that one can compute the unconditional security bound by restricting the consideration to collective attacks, and even further, to those cases such that the final state of Alice and Bob is Bell diagonal [3, 35, 36],
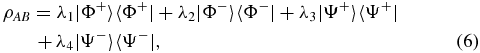
where ∑iλi = 1 and  ,
,  . It should be emphasized that the restriction for calculating the unconditional security bound does not depend on the type of the quantum channel, i.e. whether the quantum channel is with or without quantum memory, the restriction is feasible. In particular, λi acts as a function of time for the quantum channel with memory. It can be seen that |Φ±〉 give perfect correlation in the Z basis, |Φ+〉, |Ψ+〉 give perfect correlation in the X basis, and |Φ+〉, |Ψ−〉 show perfect correlation in the Y basis. Thus, the QBER for the three bases are given by
. It should be emphasized that the restriction for calculating the unconditional security bound does not depend on the type of the quantum channel, i.e. whether the quantum channel is with or without quantum memory, the restriction is feasible. In particular, λi acts as a function of time for the quantum channel with memory. It can be seen that |Φ±〉 give perfect correlation in the Z basis, |Φ+〉, |Ψ+〉 give perfect correlation in the X basis, and |Φ+〉, |Ψ−〉 show perfect correlation in the Y basis. Thus, the QBER for the three bases are given by

Eve's information IE is given by the Holevo bound
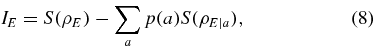
where S is von Neumann entropy, a is a symbol of Alice's classical alphabet distributed with probability p(a), ρE = ∑ap(a)ρE|a is Eve's partial state, with ρE|a being the corresponding state of Eve's ancilla state. Eve can purify the state of ρAB such that S(ρE) = S(ρAB) = H({λ1, λ2, λ3, λ4}), and the bit a values 0 or 1 equiprobably in this attack. So we obtain
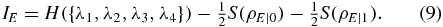
The detailed computation of ρE|b [2] shows that S(ρE|0) = S(ρE|1) = h(εz), where h is binary entropy. For the six-state protocol, all the error rates are measured, and equation (9) can be rewritten as
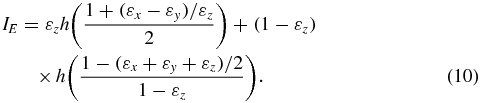
Now we calculate the evolution of the transmission state over the non-Markovian depolarizing channel with coloured noise. Having derived the Kraus operators of the depolarizing channel with coloured noise, the evolution of the state ρAB with the second qubit interacting with environment can be written as
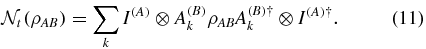
For the case of the non-Markovian depolarizing channel with coloured noise, the error rates can be calculated as
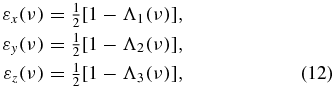
where Λi(ν) = e−ν[cos (μiν) + sin (μiν))/μi]. Now we consider the dynamics of the secret key rates for the non-Markovian case of state evolution. Under the assumption of depolarizing channels, i.e. εx(ν) = εy(ν) = εz(ν) = Q(ν); hence a1 = a2 = a3, the secret key rates for the non-Markovian case can be derived as
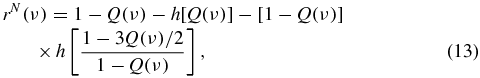
while for the case of the Markovian depolarizing channel with Gaussian white noise, Λi(ν) in error rates should be valued as  , and hence,
, and hence, ![$Q(t)=\frac{1}{2}[1-{\rm e}^{-\gamma _{{\rm i}}t}]$](https://content.cld.iop.org/journals/0953-4075/45/13/135501/revision1/jpb422885ieqn22.gif) . The secret key rate for the case of the Markovian channel is denoted as rM(t). It should be pointed out that the secret key rate here is derived under the assumption of one-way post-processing, no pre-processing and perfect error correction.
. The secret key rate for the case of the Markovian channel is denoted as rM(t). It should be pointed out that the secret key rate here is derived under the assumption of one-way post-processing, no pre-processing and perfect error correction.
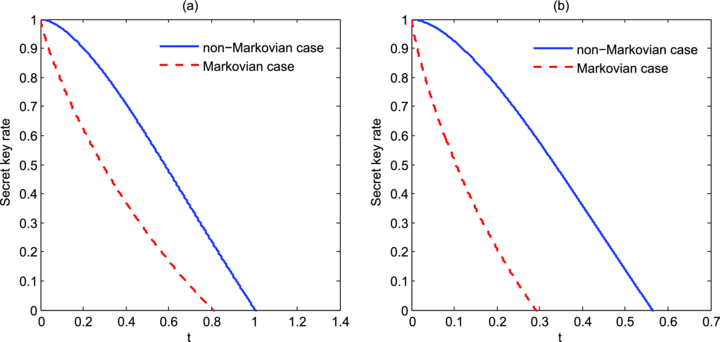
In what follows, we check whether the non-Markovian quantum channel can exhibit higher security of transmission of classical information under the same conditions. In figure 1, we plot the dynamics of the secret key rates for the cases of non-Markovian and Markovian depolarizing quantum channels under the same conditions for some different parameters |ai|. It can be seen that the secure secret key rate for the non-Markovian case is larger than the Markovian case. Also, the difference between the two cases is much clearer for the more noisy channel, since the secure secret key rate for the Markovian channel is more sensitive to the increase in noise. However, when the coupling strength of the system with the external system, which can be measured by the parameters |ai|, becomes small, the secure secret key rate for the non-Markovian case will not always be larger than the Markovian case. By setting τ = 1, we find rN(ν) ⩾ rM(t) always exists for secure communication in the regime of 0.2282 ⩽ |ai| ⩽ |a*|, where ![$|a^{*}|=\sqrt{[(\pi /\ln 3)^{2}+1]/32}$](https://content.cld.iop.org/journals/0953-4075/45/13/135501/revision1/jpb422885ieqn23.gif) , is the upper bound to keep the linear map
, is the upper bound to keep the linear map  completely positive for all times. Figure 2 presents the case that the secure secret key rate for the Markovian depolarizing channel may be larger than the non-Markovian one for some time when |ai| ⩽ |a*|.
completely positive for all times. Figure 2 presents the case that the secure secret key rate for the Markovian depolarizing channel may be larger than the non-Markovian one for some time when |ai| ⩽ |a*|.
Figure 1. The comparison of the dynamics of secret key rates of the six-state protocol over the non-Markovian and Markovian depolarizing quantum channels under the conditions (a) τ = 1, |a1| = |a2| = |a3| = 0.3 and (b) τ = 1, |a1| = |a2| = |a3| = 0.5. The blue solid and red dashed curves correspond, respectively, to the secure secret key rate in the case of non-Markovian and Markovian depolarizing channels.
Download figure:
Standard imageFigure 2. The comparison of the dynamics of secret key rates of the six-state protocol over the non-Markovian and Markovian depolarizing quantum channels under the conditions (a) τ = 1, |a1| = |a2| = |a3| = 0.2 and (b) τ = 1, |a1| = |a2| = |a3| = |a*|. The blue solid and red dashed curves correspond, respectively, to the secure secret key rate in the case of the non-Markovian and Markovian depolarizing channels.
Download figure:
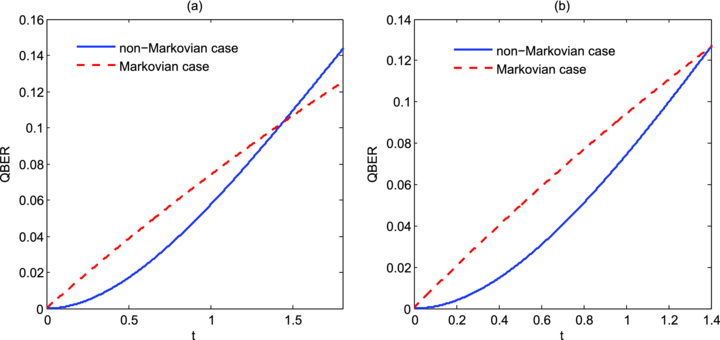
Standard imageIt should be mentioned that the time parameter t denotes the duration of the processing of the quantum channel. Thus, to guarantee the absolutely secure communication, one should limit the processing time of the quantum channel. Actually, the control of the processing time corresponds to the restriction of the QBER, and the unconditional security bounds of the QBER for the non-Markovian and Markovian depolarizing channels are equal to 12.61%. However, the dynamics of the QBER for the non-Markovian and Markovian depolarizing channels are different. Correspondingly, we find that the QBER for the Markovian case is always larger than the non-Markovian case under the same conditions in the regime 0.2282 ⩽ |ai| ⩽ |a*| when setting τ = 1. Figure 3 shows the dynamics of the QBER for two different parameters |ai|.
Figure 3. The comparison of the dynamics of QBER for the six-state protocol over the non-Markovian and Markovian depolarizing quantum channels under the conditions (a) τ = 1, |a1| = |a2| = |a3| = 0.2 and (b) τ = 1, |a1| = |a2| = |a3| = |a*|. The blue solid and red dashed curves correspond, respectively, to the QBER in the case of the non-Markovian and Markovian depolarizing channels.
Download figure:
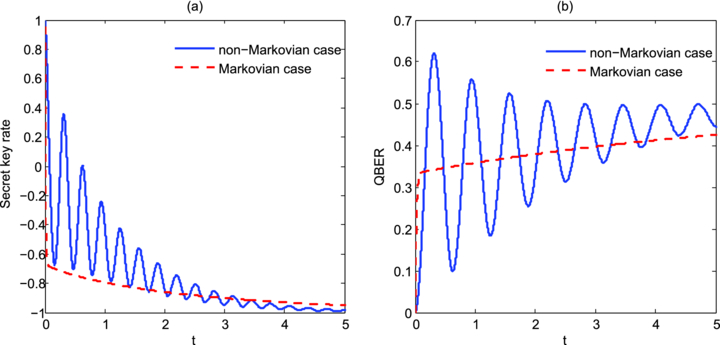
Standard imageNow we extend to the generalized depolarizing channel. Assuming the coupling strengths of the system with the external system in three directions are different, i.e. ai for i = 1, 2, 3 are not equal, the restriction |ai| ⩽ |a*| to keep  completely positive for all times can be broken. We find that the secret key rate will fluctuate near the secure point along time when the coupling strength of the system with the environment is high enough. This effect originates from the convergent oscillation of the QBER in the case of the non-Markovian depolarizing channel, which has not been found in the case of the Markovian channel. Figure 4 shows this effect when setting a high coupling strength in one direction. Since the secret key rate is positive in only some ranges of time, one application is that the legitimate parties can guarantee security communication by controlling the processing time of the non-Markovian quantum channel. It should be noted that the non-Markovian effects of the constructed quantum channel act along the quantum signals passing through the quantum channel. Moreover, it can be seen from the physical model that the former transmission of the quantum state will not affect the next transmission, i.e. the correlations between the subsequent quantum signals do not exist in this model.
completely positive for all times can be broken. We find that the secret key rate will fluctuate near the secure point along time when the coupling strength of the system with the environment is high enough. This effect originates from the convergent oscillation of the QBER in the case of the non-Markovian depolarizing channel, which has not been found in the case of the Markovian channel. Figure 4 shows this effect when setting a high coupling strength in one direction. Since the secret key rate is positive in only some ranges of time, one application is that the legitimate parties can guarantee security communication by controlling the processing time of the non-Markovian quantum channel. It should be noted that the non-Markovian effects of the constructed quantum channel act along the quantum signals passing through the quantum channel. Moreover, it can be seen from the physical model that the former transmission of the quantum state will not affect the next transmission, i.e. the correlations between the subsequent quantum signals do not exist in this model.
Figure 4. The comparison of the dynamics of (a) secret key rate, (b) QBER, for the six-state protocol over the non-Markovian and Markovian depolarizing quantum channels under the conditions τ = 1, |a1| = |a2| = 0.2, |a3| = 5. The blue solid and red dashed curves correspond, respectively, to the QBER in the case of the non-Markovian and Markovian depolarizing channels.
Download figure:
Standard imageOur results for the non-Markovian channel have shown something very different from the Markovian case. The non-Markovian channel has a better performance than the Markovian one to resist the leakage of information with the increasing of noise. Actually, the non-Markovian effects can be useful to enhance the security of quantum communication. This advantage originates from the small period of correlation time between the system and environment of the non-Markovian channel, which leads to a smaller QBER in transmission than the Markovian channel. Therefore, we can combine the application of the non-Markovian and Markovian quantum channel to achieve optimally secure QKD.
4. Summary and conclusions
We have investigated the dynamics of the secret key rate of the discrete-variable QKD protocol over the quantum channel with non-Markovian effects. In particular, we have introduced the physical model of the non-Markovian depolarizing channel with coloured noise, and calculated the secret key rate for the six-state protocol over non-Markovian and Markovian quantum channels under the same conditions. Moreover, we numerically compare the performances of the information transmissions over these two types of quantum channels. We find that the secure secret key rate will always be larger for non-Markovian channels than Markovian ones when the coupling strength of the system with the environment is strong enough. In particular, we obtain the lower bound of the coupling strength ai when the parameter τ is specified as τ = 1. It should be mentioned that we focus on the study of the value of the secure secret key rate as the function of processing time of the quantum channel. In practice, the transmission distance for secure QKD is also an important parameter, which is directly related to the transmission speeds of the quantum states over the Markovian and non-Markovian channels. However, the secure transmission distances over the Markovian and non-Markovian channels are out of our discussions.
Since the upper bounds of tolerable QBER for secure QKD are equal over the non-Markovian and Markovian depolarizing channels, we demonstrate that the better performance of the non-Markovian depolarizing quantum channel for the six-state protocol originates from the different dynamics of QBER. Furthermore, we consider the generalized non-Markovian depolarizing channel and show that the secret key rate will fluctuate near the secure point when the coupling strength of the system with the environment is high. This indicates that the coloured noise in the non-Markovian quantum channels can enhance the security of communication. The results demonstrate that the non-Markovian effects of the transmission channel can have a positive impact on the security of discrete-variable QKD.
Acknowledgment
This work was supported by the National Natural Science Foundation of China (grant nos 61 102 053, 61 170 228, 60 970 109 and 60 801 051).