Abstract
A combinatorial method of encryption with a similarity to the classical scheme of linear coding has been suggested by the author. The general idea is to treat vertices of a graph as messages and arcs of a certain length as encryption tools. We will study the quality of such an encryption in the case of graphs of high girth by comparing the probability to guess the message, (vertex) at random with the probability of breaking the key, i.e. guessing the encoding arc. In fact, the quality is good for graphs which are close to the Erdös bound, defined by the Even Cycle Theorem.
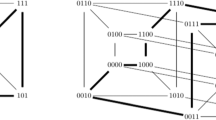
In the case of parallelotopic graphs, there is a uniform way to match arcs with strings in a certain alphabet. Among parallelotopic graphs we distinguish linguistic graphs of affine type whose vertices (messages) and arcs (encoding tools) both could be naturally identified with vectors over the GF(q), and neighbors of the vertex defined by a system of linear equations. We will discuss families of linguistic and parallelotopic graphs of increasing girth as the source for assymmetric cryptographic functions and related open key algorithms.
Several constructions of families of linguistic graphs of high girth with good quality, complexity and expansion coefficients will be considered. Some of those constructions have been obtained via group-theoretical and geometrical techniques.
Similar content being viewed by others
References
Ahiezer, N. I. and Krein, M.: Some Questions in the Theory of Moments, Amer.Math.Soc., Providence, 1962.
Alkire, B. and Vandenberghe, L.: Convex optimization problems involving finite autocorrela-tion sequences, Technical Report, 2000. Submitted to Math. Progr.B.
Davidson, T. N., Zhi-Quan Luo and Sturm, J. F.: Linear matrix inequality formulation of spectral mask constraints, Preprint, 2000.
Faybusovich, L.: Self-concordant barriers for cones generated by Chebyshev systems, SIOPT 13(3) (2002), 770-781.
Genin, Y., Hachez, Y., Nesterov, Y. and Van Dooren, P.: Optimization problems over positive pseudo-polynomial matrices, SIAM J. Matrix Anal. Appl.2001, Submitted.
Genin, Y., Hachez, Y., Nesterov, Y. and Van Dooren, P.: Convex optimization over positive polynomials and filter design, Proc. UKACC Int. Cont. Conf., 2000.
Gohberg, I., Lancaster, P. and Rodman, L.: Matrix Polynomials, Academic Press, New York, 1982, pp. 409.
Krein, M. G. and Nudelman, A. A.: The Markov Moment Problem and Extremal Problems, Amer. Math. Soc., Providence, 1977.
Lang, S.: Algebra, Addison-Wesley, Reading, Mass., 1993.
Nesterov, Yu.: Squared functional systems and optimization problems, In: High Performance Optimization, Kluwer Acad. Publ., Dordrecht, 2000, pp. 405-440.
Nesterov, Yu. and Nemirovskii, A.: Interior-point Polynomial Algorithms in Convex Programming, SIAM Stud. Appl. Math. 13, SIAM, Phil., 1994.
Rockafellar, R. T.: Convex Analysis, Princeton Univ. Press, Princeton, NJ, 1970.
Author information
Authors and Affiliations
Rights and permissions
About this article
Cite this article
Ustimenko, V.A. Graphs with Special Arcs and Cryptography. Acta Applicandae Mathematicae 74, 117–153 (2002). https://doi.org/10.1023/A:1020686216463
Issue Date:
DOI: https://doi.org/10.1023/A:1020686216463