Abstract
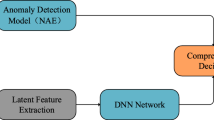
Intrusion detection is an essential security issue in the present digital climate. Spiteful cyber attacks can frequently hide/sneak in abundant volumes of regular data in lopsided network traffic. In cyberspace, it has a great level of stealth and opacity, making it crucial for network-based intrusion detection systems (NIDS) to assure the accuracy in detection and the given timelines. The false-positive issue is one of the inherent drawbacks of NIDS, which are widely employed to identify threats and safeguard networks. Imbalance classes and unreasonable network datasets are the main reasons behind these false positives. This paper proposes an autoencoder-based anomaly detection methodology, which uses a reconstruction error approach to generate attack samples, which are less in number in the training dataset. Feature rngineering is also performed in this paper using the recursive feature elimination method. We utilized the NSL-KDD dataset for this experiment. The result shows that our approach is better than various modern approaches in terms of various metrics such as accuracy, precision, recall, and F1 score.


Similar content being viewed by others
References
Siddiqi MA, Pak W. An agile approach to identify single and hybrid normalization for enhancing machine learning-based network intrusion detection. IEEE Access. 2021;9:137494–513. https://doi.org/10.1109/ACCESS.2021.3118361.
Diro AA, Chilamkurti N. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener Comput Syst. 2018;82:761–8. https://doi.org/10.1016/j.future.2017.08.043.
Ghasemi J, Esmaily J, Moradinezhad R. Intrusion detection system using an optimized kernel extreme learning machine and efficient features. Sadhana Acad Proc Eng Sci. 2020. https://doi.org/10.1007/s12046-019-1230-x.
Halbouni A, Gunawan TS, Habaebi MH, Halbouni M, Kartiwi M, Ahmad R. Machine learning and deep learning approaches for CyberSecurity: a review. IEEE Access. 2022;10:19572–85. https://doi.org/10.1109/ACCESS.2022.3151248.
Al-Daweri MS, Ariffin KAZ, Abdullah S, Senan MFEM. An analysis of the KDD99 and UNSW-NB15 datasets for the intrusion detection system. Symmetry (Basel). 2020;12(10):1–32. https://doi.org/10.3390/sym12101666.
Liu L, Wang P, Lin J, Liu L. Intrusion detection of imbalanced network traffic based on machine learning and deep learning. IEEE Access. 2021;9:7550–63. https://doi.org/10.1109/ACCESS.2020.3048198.
Chkirbene Z, Erbad A, Hamila R, Mohamed A, Guizani M, Hamdi M. TIDCS: a dynamic intrusion detection and classification system based feature selection. IEEE Access. 2020;8:95864–77. https://doi.org/10.1109/ACCESS.2020.2994931.
Le Jeune L, Goedeme T, Mentens N. Machine learning for misuse-based network intrusion detection: overview, unified evaluation and feature choice comparison framework. IEEE Access. 2021;9:63995–4015. https://doi.org/10.1109/ACCESS.2021.3075066.
Akashdeep IM, Kumar N. A feature reduced intrusion detection system using ANN classifier. Expert Syst Appl. 2017;88:249–57. https://doi.org/10.1016/j.eswa.2017.07.005.
Jiang K, Wang W, Wang A, Wu H. Network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access. 2020;8:32464–76. https://doi.org/10.1109/ACCESS.2020.2973730.
Wisanwanichthan T, Thammawichai M. A double-layered hybrid approach for network intrusion detection system using combined Naive Bayes and SVM. IEEE Access. 2021;9:138432–50. https://doi.org/10.1109/ACCESS.2021.3118573.
Liu C, Gu Z, Wang J. A hybrid intrusion detection system based on scalable K-Means+ random forest and deep learning. IEEE Access. 2021;9:75729–40. https://doi.org/10.1109/ACCESS.2021.3082147.
Elhefnawy R, Abounaser H, Badr A. A hybrid nested genetic-fuzzy algorithm framework for intrusion detection and attacks. IEEE Access. 2020;8:98218–33. https://doi.org/10.1109/ACCESS.2020.2996226.
Tang Y, Li C. An online network intrusion detection model based on improved regularized extreme learning machine. IEEE Access. 2021;9:94826–44. https://doi.org/10.1109/ACCESS.2021.3093313.
Wang W, et al. Anomaly detection of industrial control systems based on transfer learning. Tsinghua Sci Technol. 2021;26:821–32.
Fatani A, Elaziz MA, Dahou A, Al-Qaness MAA, Lu S. IoT intrusion detection system using deep learning and enhanced transient search optimization. IEEE Access. 2021;9:123448–64. https://doi.org/10.1109/ACCESS.2021.3109081.
Jiang H, He Z, Ye G, Zhang H. Network Intrusion detection based on PSO-Xgboost model. IEEE Access. 2020;8:58392–401. https://doi.org/10.1109/ACCESS.2020.2982418.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Industrial IoT and Cyber-Physical Systems” guest edited by Arun K Somani, Seeram Ramakrishnan, Anil Chaudhary, and Mehul Mahrishi.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Giri, K., Gupta, M. & Dadheech, P. An Efficient Hybrid Approach for Intrusion Detection in Cyber Traffic Using Autoencoders. SN COMPUT. SCI. 4, 498 (2023). https://doi.org/10.1007/s42979-023-01865-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-023-01865-3