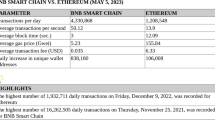
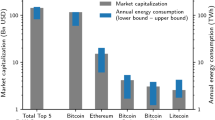
Abstract
Blockchain technology has emerged in the last decade and has been increasingly adopted in real-world applications. It relies on several cryptographic techniques, namely cryptographic hashing and digital signatures, which are threatened by the development of quantum computers. Quantum computing can potentially implement algorithms which can invalidate assumptions underlying these systems, namely pre-image resistance, and the intractability of certain hidden subgroup problems. Several research works have investigated the nature of the threats posed by quantum computing to blockchain, and have proposed potential countermeasures to secure the systems. In this paper we will analyse the timeline along which such threats are likely to become real for blockchain implementations, and assess the level of threat posed given the proposed countermeasures. After providing a reasoned summary of the quantum computing threats to blockchain and possible solutions, we discuss the time frame within which, by integrating the insights provided by recent research on their evolution, quantum computers may become mature enough to support the implementation of algorithms that could actually break the current public blockchain implementations, like Bitcoin.

Similar content being viewed by others
Availability of data and materials
The submission has no data or other materials to be made available.
References
Aaronson S, Arkhipov A (2011) The computational complexity of linear optics. In: Proceedings of the forty-third annual ACM symposium on Theory of computing. pp 333–342
Aggarwal D, Brennen G, Lee T, et al (2018) Quantum attacks on bitcoin, and how to protect against them. Ledger 3
Aono Y, Liu S, Tanaka T, et al (2022) The present and future of discrete logarithm problems on noisy quantum computers. IEEE Trans Quantum Eng
Arikan E (2003) An information-theoretic analysis of grover’s algorithm. In: Quantum Communication and Information Technologies. Springer, p 339–347
Arute F, Arya K, Babbush R et al (2019) Quantum supremacy using a programmable superconducting processor. Nature 574(7779):505–510
Barabasi S, Barrera J, Bhalani P, et al (2019) Student user experience with the ibm qiskit quantum computing interface. In: Future of Information and Communication Conference. Springer, pp 547–563
Bernstein DJ, Lange T (2017) Post-quantum cryptography. Nature 549(7671):188–194
Cacciapuoti AS, Caleffi M, Tafuri F et al (2019) Quantum internet: networking challenges in distributed quantum computing. IEEE Netw 34(1):137–143
Chow J, Dial O, Gambetta J (2021) Ibm quantum breaks the 100-qubit processor barrier. IBM Research Blog
Dennis R, Disso JP (2019) An analysis into the scalability of bitcoin and ethereum. In: Third International Congress on Information and Communication Technology. Springer, pp 619–627
Deutsch D, Jozsa R (1992) Rapid solution of problems by quantum computation. Proc R Soc Lond Ser A Math Phys Sci 439(1907):553–558
Devoret MH, Schoelkopf RJ (2013) Superconducting circuits for quantum information: an outlook. Science 339(6124):1169–1174
Edwards M, Mashatan A, Ghose S (2020) A review of quantum and hybrid quantum/classical blockchain protocols. Quantum Inf Process 19(6):1–22
Ekert A, Jozsa R (1996) Quantum computation and shor’s factoring algorithm. Rev Mod Phys 68(3):733
Fedorov AK, Kiktenko EO, Lvovsky AI (2018) Quantum computers put blockchain security at risk. Nature 563(7729):465–468
Fernandez-Carames TM, Fraga-Lamas P (2020) Towards post-quantum blockchain: A review on blockchain cryptography resistant to quantum computing attacks. IEEE Access 8:21091–21116
Friedman JR, Patel V, Chen W et al (2000) Quantum superposition of distinct macroscopic states. Nature 406(6791):43–46
Grimes RA (2019) Cryptography apocalypse: preparing for the day when quantum computing breaks today’s crypto. Wiley
Grover LK (1996) A fast quantum mechanical algorithm for database search. In: Proceedings of the twenty-eighth annual ACM symposium on Theory of computing. pp 212–219
Horan K, Kahrobaei D (2018) The hidden subgroup problem and post-quantum group-based cryptography. In: International Congress on Mathematical Software. Springer, pp 218–226
Ikeda K (2018) Security and privacy of blockchain and quantum computation. In: Advances in Computers, vol 111. Elsevier, p 199–228
Johnson D, Menezes A, Vanstone S (2001) The elliptic curve digital signature algorithm (ecdsa). Int J Inf Secur 1(1):36–63
Kappert N, Karger E, Kureljusic M (2021) Quantum computing-the impending end for the blockchain? In: Pacific Asia Conference on Information Systems (PACIS). Dubai
Koshy P, Koshy D, McDaniel P (2014) An analysis of anonymity in bitcoin using p2p network traffic. In: International Conference on Financial Cryptography and Data Security. Springer, pp 469–485
Madsen LS, Laudenbach F, Askarani MF et al (2022) Quantum computational advantage with a programmable photonic processor. Nature 606(7912):75–81
Mosca M (2018) Cybersecurity in an era with quantum computers: will we be ready? IEEE Secur Priv 16(5):38–41
Nakamoto S (2008) A peer-to-peer electronic cash system. Bitcoin. 4:2. https://bitcoin.org/bitcoin.pdf
Rodenburg B, Pappas SP (2017) Blockchain and quantum computing. Tech. rep., The MITRE Corporation
Sevilla J, Riedel CJ (2020) Forecasting timelines of quantum computing. arXiv preprint arXiv:2009.05045
Shor PW (1999) Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev 41(2):303–332
Skosana U, Tame M (2021) Demonstration of Shor’s factoring algorithm for N=21 on IBM quantum processors. Sci Rep 11(1):1–12
Stewart I, Ilie D, Zamyatin A et al (2018) Committing to quantum resistance: a slow defence for bitcoin against a fast quantum computing attack. R Soc Open Sci 5(6):180410
Zhong HS, Wang H, Deng YH et al (2020) Quantum computational advantage using photons. Science 370(6523):1460–1463
Zhu H (2001) Survey of computational assumptions used in cryptography broken or not by shor’s algorithm
Author information
Authors and Affiliations
Contributions
K.S. analysed the literature, developed the framework and wrote the main draft of the manuscript. M.C. supervised the project, provided background knowledge on blockchain technology, and revised the paper. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Human and animal ethics
Not applicable
Consent for publication
All authors have checked the manuscript and agree with the submission.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Schärer, K., Comuzzi, M. The quantum threat to blockchain: summary and timeline analysis. Quantum Mach. Intell. 5, 19 (2023). https://doi.org/10.1007/s42484-023-00105-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42484-023-00105-4