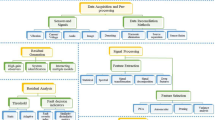
Abstract
Load redistribution (LR) attacks in power systems can cause significant damage to the power grids, which leads to blackouts and other disastrous consequences. The paper aims to detect LR attacks using entropy-based features, even with limited information, to provide a practical solution. The paper presents an entropy-based method for LR attack detection, which is superior to traditional methods in identifying abnormal system behavior. The proposed method uses entropy to extract features that can differentiate normal and abnormal system behavior. The probability density function (PDF) of LR attacks is used to calculate the entropy of the system, which can then be used as a feature for detection. The paper concludes that the entropy-based approach offers a practical and effective solution for detecting LR attacks, even with limited information. The proposed method is a model-based free approach, making it highly desirable for practical applications. The results obtained on the IEEE 14-bus system show that the suggested method is accurate and can be used to protect power grids from LR attacks.






Similar content being viewed by others
References
A. Khaleghi, M.S. Ghazizadeh, M.R. Aghamohammadi, A deep learning-based attack detection mechanism against potential cascading failure induced by load redistribution attacks. IEEE Trans. Smart Grid 14(6), 4772–4783 (2023). https://doi.org/10.1109/TSG.2023.3256480
X. Liu, Z. Li, False data attacks against ac state estimation with incomplete network information. IEEE Trans. Smart Grid 8(5), 2239–2248 (2017). https://doi.org/10.1109/TSG.2016.2521178
X. Liu, Z. Li, Z. Shuai, Y. Wen, Cyber attacks against the economic operation of power systems: a fast solution. IEEE Trans. Smart Grid 8(2), 2239–2248 (2016)
X. Liu, Z. Li, Local topology attacks in smart grids. IEEE Trans. Smart Grid 8(6), 2617–2626 (2016)
R. Kaviani, K.W. Hedman, An Enhanced energy management system including a real-time load-redistribution threat analysis tool and cyber-physical SCED. IEEE Trans. Power Syst. (2021). https://doi.org/10.1109/TPWRS.2021.3135357
Y. Liu, P. Ning, M.K. Reiter, False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 14(1), 1–33 (2011)
J. Zhang, L. Sankar, Physical system consequences of unobservable state-and-topology cyber-physical attacks. IEEE Trans. Smart Grid 7(4), 2016 (2016)
A. Ashok, M. Govindarasu, Cyber attacks on power system state estimation through topology errors. IEEE Power Energy Soc. General Meet. 2012, 1–8 (2012)
J. Zhao, L. Mili, M. Wang, A generalized false data injection attacks against power system nonlinear state estimator and countermeasures. IEEE Trans. Power Syst. 33(5), 4868–4877 (2018). https://doi.org/10.1109/TPWRS.2018.2794468
Y. Xiang, L. Wang, A game-theoretic study of load redistribution attack and defense in power systems. Electr. Power Syst. Res. 151, 12–25 (2017)
K. Manandhar, X. Cao, F. Hu, Y. Liu, Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control Netw. Syst. 1(4), 370–379 (2014). https://doi.org/10.1109/TCNS.2014.2357531
R. Kaviani, K.W. Hedman, A detection mechanism against load-redistribution attacks in smart grids. IEEE Trans. Smart Grid 12(1), 704–714 (2020)
Z. Liu, L. Wang, Defense strategy against load redistribution attacks on power systems considering insider threats. IEEE Trans. Smart Grid 12(2), 1529–1540 (2021). https://doi.org/10.1109/TSG.2020.3023426
A. Pinceti, L. Sankar, O. Kosut, Load redistribution attack detection using machine learning: a data-driven approach. IEEE Power Energy Soc. Gen. Meet. 1–5, 2018 (2018). https://doi.org/10.1109/PESGM.2018.8586644
A. Khaleghi, M.O. Sadegh, M. Ghazizadeh-Ahsaee, A.M. Rabori, Transient fault area location and fault classification for distribution systems based on wavelet transform and adaptive neuro-fuzzy inference system (ANFIS). Adv. Electr. Electron. Eng. 16, 155–166 (2018)
H. Wang, A. Meng, Y. Liu, X. Fu, G. Cao, Unscented Kalman Filter based interval state estimation of cyber physical energy system for detection of dynamic attack. Energy 188, 116036 (2019). https://doi.org/10.1016/j.energy.2019.116036
D. Mukherjee, S. Chakraborty, S. Ghosh, Deep learning-based multilabel classification for locational detection of false data injection attack in smart grids. Electr. Eng. 104(1), 259–282 (2022)
Z. Chu et al. A Verifiable framework for cyber-physical attacks and countermeasures in a resilient electric power grid, arXiv Prepr. arXiv2104.13908, (2021).
A. Khaleghi, M. Oukati Sadegh, Single-phase fault location in four-circuit transmission lines based on wavelet analysis using ANFIS. J. Electr. Eng. Technol. 14, 1577–1584 (2019). https://doi.org/10.1007/s42835-019-00209-7
Funding
State Grid Shandong Electric Power Company Science and Technology Project Funding “Research and Application of Information System Vulnerability Control Technology Based on Running Time Self protection Technology” (ERP Code: 520609230004).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing of interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Liu, X., Zhang, Y., Wang, Z. et al. Detecting False Data Injection Attacks (FDIAs) in Power Systems Based on Entropy Criteria. J. Inst. Eng. India Ser. B 105, 121–129 (2024). https://doi.org/10.1007/s40031-023-00960-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40031-023-00960-6