Abstract
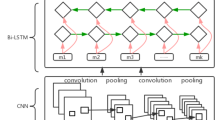
Domain Generation Algorithm(DGA) serve as variety detection of domain utilized with malicious into develop random domain as a specific algorithm that accept assignation parts on that malicious botnet communication. In recent days, DGA has presented in addition to communicated extensively harder identifying through these classical feature based DGA. By this chapter, they utilize these character-based to these DGA domain together with present a framework of Deep Neural Network to classifying DGA and existing methods by DGA identification utilized machine learning approach predicated on characteristics sampling in addition to deep learning approach on identify botnet domain. At the same time, these techniques achieve weakly performance against the word-list based botnet. In this chapter, the proposed deep learning approach of Multi-Head Self-Attention-Recurrent Convolution Neural Network-Self Attention Bidirectional Long Short Term Memory model toward identifying together with classifies DGA domain threat. Initially, this Recurrent Convolution Neural Network along with Self Attention Bidirectional Long Short Term Memory layer has utilized that context this highlights over this domain consequences information; and next that multi head self-attention layer has utilized on measures comparable position over these contexts domain information. Lastly, the DGA domain features that miscellaneous weights are set within this output layer through improve detection in addition to classification tasks. Toward realistic, the captured of F1 measure 98.95% to the extent of detection together with macro-average F1 measure 83.97% to the extent of classification domain of DGA tasks.





Similar content being viewed by others
References
Alex (2020) Keyword Research, Competitive Analysis, & Website Ranking, Alexa. 2020. Available online: https://www.alexa.com/ (accessed on 10 July 2020)
Anderson HS, Woodbridge J, Filar B, (2016) Deepdga: Adversarially-tuned domain generation and detection. In: Proceedings of the 2016 ACM workshop on artificial intelligence and security. ACM, Vienna. pp 13–21
Bahdanau D, Cho K, Bengio Y, (2014) Neural machine translation by jointly learning to align and translate. arXiv e-prints:arXiv:1409.0473. https://ui.adsabs.harvard.edu/abs/2014arXiv1409.0473B
Bambenek, J. OSINT Feeds from Bambenek Consulting. 2020. Available online: http://osint.bambenekconsulting.com/feeds/ (accessed on 10 June 2020)
Grill M, Nikolaev I, Valeros V, Rehak M, (2015) Detecting DGA malware using NetFlow. In Proceedings of the IFIP/IEEE international symposium on integrated network management (IM), Ottawa, ON, Canada, 11–15, pp 1304–1309, https://doi.org/10.1109/INM.2015.7140486
He K, Zhang X, Ren S, Sun J, (2016) Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 770–778
Hochreiter S, Schmidhuber J (1997) Long short-term memory. Neural Comput 9(12):1735–1780
India M, Safari P, and Hernando J, (2019) Self multi-head attention for speaker recognition, 2019, arXiv:1906.09890. [Online]. Available: http://arxiv.org/abs/1906.09890
Lai S, Xu L, Liu K, Zhao J, (2015) Recurrent convolutional neural networks for text classification. In: Proceedings of the 29th AAAI conference on artificial intelligence and the 27th innovative applications of artificial intelligence conference, Austin, TX, USA, 25–30, pp. 2267–2273
Li Y, Xiong K, Chin T, Hu C (2019) A machine learning framework for domain generation algorithm-based malware detection. IEEE Access 7:32765–32782
Liao C F, Tsao Y, Lu X, and Kawai H, (2019) Incorporating symbolic sequential modeling for speech enhancement. In: Proceedings conference international speech commun assoc. (INTERSPEECH), Sep. 2019, pp 2733-2737
Luong M-T, Pham H, Manning CD, (2015) Effective approaches to attention-based neural machine translation. In: Proceedings of the 2015 conference on empirical methods in natural language processing. ACL, Lisboa. pp 1412–1421
Mac H, Tran D, Tong V, Nguyen LG, Tran HA, (2017) Dga botnet detection using supervised learning methods. In: Proceedings of the Eighth international symposium on information and communication technology. ACM, Nha Trang. pp 211–218
360netlab, “DGA,” 2020, accessed 10 June, 2020.https://data.netlab.360.com/dga/.
Patil JB, Dharmaraj R (2018) Feature-based malicious url and attack type detection using multi-class classification. ISeCure 10(2):141–162
Plohmann D, Yakdan K, Klatt M, Bader J, Gerhards-Padilla E, (2016) A comprehensive measurement study of domain generating malware. In: 25th [USENIX] security symposium ([USENIX] Security 16). USENIX, Austin. pp 263–278
Qiao Y, Zhang B, Zhang W, Kumar A, Wu H (2019) Dga domain name classification method based on long short-term memory with attention mechanism. Appl Sci 9(20):4205
Ren P, Chen Z, Ren Z, Wei F, Ma J, de Rijke M, (2017) Leveraging contextual sentence relations for extractive summarization using a neural attention model. In: Proceedings of the 40th international ACM SIGIR conference on research and development in information retrieval. ACM, Tokyo.pp 95–104
Rumelhart D, Hinton G, Williams R (1986) Learning representations by back propagating errors. Nature 323(10):533–536
Saxe J, Berlin K, (2017) expose: A character-level convolutional neural network with embeddings for detecting malicious urls, file paths and registry keys. arXiv e-prints:arXiv:1702.08568. https://ui.adsabs.harvard.edu/abs/2017arXiv170208568S
Shibahara T, Yagi T, Akiyama M, Chiba D, Yada T, (2016) Efficient dynamic malware analysis based on network behavior using deep learning. In: 2016 IEEE global communications conference (GLOBECOM). IEEE, Washington, DC. pp 1–7
Socher R, Huang EH, Pennington J, Ng AY, Manning CD (2011) Dynamic pooling and unfolding recursive autoencoders for paraphrase detection. Adv Neural Inf Process Syst 2011(24):801–809
Tran D, Mac H, Tong V, Tran HA, Nguyen G (2017) A lstm based framework for handling multiclass imbalance in dga botnet detection. Neuro Computing 275(11):2017
Vaswani A, Shazeer N, Parmar N, Uszkoreit J, Jones L, Gomez A, Kaiser L, Polosukhin I, (2017) Attention is all you need
Wang W, Shirley K, (2015) Breaking bad: detecting malicious domains using word segmentation. arXiv e-prints:arXiv:1506.04111. https://ui.adsabs.harvard.edu/abs/2015arXiv150604111W
Woodbridge J, Anderson HS, Ahuja A, Grant D, (2016) predicting domain generation algorithms with long short-term memory networks. arXiv 2016, arXiv:1611.00791. [Online]. Available: http://arxiv.org/abs/1611.00791
Xu C, Shen J, Du X (2019) Detection method of domain names generated by dgas based on semantic representation and deep neural network. Comput Security 85(04):77–88
Yang Z, Yang D, Dyer C, He X, Smola A, Hovy E, (2016) Hierarchical attention networks for document classification. In: Proceedings of the 2016 conference of the North American chapter of the association for computational linguistics: Human Language Technologies. ACL, San Diego. pp 1480–1489
Yang L, Liu G, Zhai J, Dai Y, Yan Z, Zou Y, Huang W, (2018) A novel detection method for word-based dga. In: International conference on cloud computing and security. Springer, Haikou. pp 472–483
Yu B, Gray D.L, Pan J, Cock M.D, Nascimento ACA, (2017) Inline DGA detection with deep networks. In Proceedings of the 2017 IEEE international conference on data mining workshops (ICDMW), New Orleans, LA, USA, 18–21, pp. 683–692. doi:https://doi.org/10.1109/ICDMW.2017.96
Yu B, Pan J, Hu J, Nascimento A, De Cock M, (2018) Character level based detection of DGA domain names. In: 2018 International joint conference on neural networks (IJCNN), IEEE, 07 2018, pp. 1–8
Zang X, Gong J, Hu X (2018) Detecting malicious domain name based on AGD. J Commun 39(7):15–25
Zhou P, Shi W, Tian J, Qi Z, Li B, Hao H, Xu B 2016a Attention-based bidirectional long short-term memory networks for relation classification In: Proceedings of the 54th annual meeting of the association for computational linguistics 08(2016a): 207–212
Zhou X, Wan X, Xiao J, 2016b. Attention-based lstm network for cross-lingual sentiment classification. In: Proceedings of the 2016b conference on empirical methods in natural language processing. ACL, Texas. pp 247–256
Acknowledgements
This research has supported acknowledge over the NVIDIA corporation of Capital One on the part of incredible opportunity on deploy the deep neural network developed to the extent of research within the live environment in order to evaluation.
Funding
None.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sarojini, S., Asha, S. Detection for domain generation algorithm (DGA) domain botnet based on neural network with multi-head self-attention mechanisms. Int J Syst Assur Eng Manag (2022). https://doi.org/10.1007/s13198-022-01713-2
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13198-022-01713-2