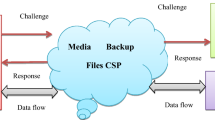
Abstract
With the emergence of cloud eco-system and technologies like Internet of Things (IoT), bit data analytics became essential to reap benefits of maintaining large volumes of data. As there is amalgamation of different devices, protocols, standard and use cases linked to IoT, there is increasing risk of security. IoT applications are vulnerable due to lack of security standards at global level. There is need for continuous efforts to provide end-to-end security in IoT applications. Sensor networks associated with IoT are resource constrained but produce large volumes of data or big data. In such environment, more light weight security primitives. Elliptic Curve Diffie Hellman (ECDH) is one such lightweight scheme for secure key exchange among connected devices. Nevertheless, ECDH is found vulnerable to attacks. To address this problem, we proposed a scheme known as E-ECDH (ECDH+SIGH) which is an enhanced version of ECDH. Our scheme is designed to enhance security level in IoT use cases. To evaluate our scheme, we used an IoT use case meant for anomaly detection in healthcare context. This application is in distributed environment where cloud infrastructure, IoT platform and Message Queue Telemetry Transport (MQTT) protocol are involved. Our experimental study showed that E-ECDH improves level of security in given IoT application and found to be better than existing security schemes.









Similar content being viewed by others
Data availability
There is no third party of data is consider for this research work. Hence it doesn’t required any permissions from third party.
References
Ahamed J, Rajan AV (2016) Internet of Things (IoT): Application systems and security vulnerabilities. 2016 5th International Conference on Electronic Devices, Systems and Applications (ICEDSA), Ras Al Khaimah, United Arab Emirates, pp. 1-5
Alferidah DK, Jhanjhi NZ (2020) “A review on security and privacy issues and challenges in internet of things”, IJCSNS International Journal of Computer Science and Network. Security 20(4)
Al-Garadi MA, Mohamed A, Al-Ali AK, Du X, Ali I, Guizani M (2020) A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. In: IEEE Commun SurvTutor 22(3):1646–1685
AL-mawee W (2012) Privacy and Security Issues in IoT Healthcare Applications for the Disabled Users a Survey. Master's Theses. 651
Ammar M, Russello G, Crispo B (2018) Internet of Things: A survey on the security of IoT frameworks. J Inform Sec Appli 38:8–27
Ande R, Adebisi B, Hammoudeh M, Saleem J (2020) Internet of Things: Evolution and technologies from a security perspective. Sustain Cities Soc 54:101728
Azmoodeh A, Dehghantanha A, Raymond Choo KK (2019) Big data and internet of things security and forensics: Challenges and opportunities. Handbook Big Data IoT Sec:1–4
T. Baranwal, Nitika R, Pateriya PK (2016) Development of IoT based smart security and monitoring devices for agriculture. 2016 6th International Conference - Cloud System and Big Data Engineering (Confluence), Noida, India, pp. 597-602
Berkay Celik Z (2018) Program analysis of commodity iot applications for security and privacy: Challenges and opportunities. ACM Comput Surv 52(4):1–30
Bernstein DJ (2006) “Curve25519: New Di_e-Hellman speed records”, In M. Yung, Y. Dodis, A. Kiayias, and T. Malkin, editors, Public Key Cryptography - PKC 2006, 9th International Conference on Theory and Practice of Public-Key Cryptography, New York, NY, USA, April 24-26, 2006, Proceedings, volume 3958 of Lecture Notes in Computer Science, pages 207-228. Springer
D. J. Bernstein The post-quantum internet. Invited talk at PQCrypto 2016: https://cr.yp.to/talks/2016.02.24/slides-djb-20160224-a4.pdf, Feb, 2016
Bos JW, Friedberger SJ (2019) Arithmetic considerations for isogeny-based cryptography. IEEE Trans Comput 68(7):979–990
Craig C, Longa P, Naehrig M (2016) Efficient algorithms for supersingular isogeny Diffie-Hellman. In” Advances in Cryptology–CRYPTO 2016: 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 14-18, 2016, Proceedings, Part I 36, pp. 572-601
S. K. Datta and C. Bonnet (2016) Easing IoT application development through DataTweet framework. 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, pp. 430-435
Datta SK, Gyrard A, Bonnet C, Boudaoud K (2015) oneM2M architecture based user centric IoT application development. 3rd International Conference on Future Internet of Things and Cloud, pp.1-8
David J, De Feo L (2011) Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies. In: Post-Quantum Cryptography: 4th International Workshop, PQCrypto 2011, Taipei, Taiwan, November 29–December 2, Proceedings 2011, 4, pp. 19-34
Diffie W, Hellman M (1976) New directions in cryptography. IEEE Trans Inf Theory 22(6):644–654
Ejaz W, Anpalagan A (2019) Internet of things for smart cities: technologies, big data and security. Springer International Publishing, Berlin/Heidelberg, Germany
Giuseppe A, Persico V, Pescapé A (2020) Industry 4.0 and health: Internet of things, big data, and cloud computing for healthcare 4.0. J Ind Inf Integr 18:100129
Hasan MK, Ahmed MM, Musa SS, Islam S, Abdullah SNHS, Hossain E, Nafi NS, Vo N. (2021b). An Improved Dynamic Thermal Current Rating Model for PMU-Based Wide Area Measurement Framework for Reliability Analysis Utilizing Sensor Cloud System . IEEE Access, pp.1–13. https://doi.org/10.1109/access.2021.3052368
Hasan MK, Ghazal TM, Alkhalifah A, Ab KA. (2021a). Fischer Linear Discrimination and Quadratic Discrimination Analysis–Based Data Mining Technique for Internet of Things. Front Public Health 9, pp.1-18.
Imran M, Ahmed SR, Kamrul HM, Rosilah H, Ul HA, Akram ZK, Sajjad S (2020) Protect Mobile Travelers Information in Sensitive Region Based on Fuzzy Logic in IoT Technology. Security and Communication. Networks:1–12. https://doi.org/10.1155/2020/8897098
Jeffrey H, Pipher J, Silverman JH (1998) NTRU: A ring-based public key cryptosystem. In: International algorithmic number theory symposium, pp. 267-288. Berlin, Heidelberg: Springer Berlin Heidelberg
F. Jonsson and M. Tornkvist (2017) RSA authentication in internet of things. Degree Project In Technology, First Cycle, 15 Credits Stockholm, Sweden
Kang Y-M, Han M-R, Han K-S, Kim J-B (2015) A study on the internet of things (IoT) applications. Int J Software Eng Appli 9(9):117–126
Li C (2020) Information processing in Internet of Things using big data analytics. Comput Commun 160:718–729
Liu Z, Yan T (2013) Study on multi-view video based on IOT and its application in intelligent security system," Proceedings 2013 International Conference on Mechatronic Sciences, Electric Engineering and Computer (MEC), Shenyang, China, pp. 1437-1440
López D, Daniel MBU, Cely CS, Murgueitio DT et al (2018) Developing secure IoT services: A security-oriented review of IoT platforms. Symmetry 10(12):669
McEliece RJ (1978) A public-key cryptosystem based on algebraic coding theory. Coding Thv 4244:114–116
Merkle RC (1979) Secrecy, authentication, and public key systems. PhD thesis, Stanford University
Mike H (2015) Ed448-Goldilocks, a new elliptic curve." Cryptology ePrint Archive
Milne JS (1986) Arithmetic Geometry, chapter Abelian Varieties, pp.103-150. Springer New York, New York, NY
Montgomery PL (1987) Speeding the Pollard and elliptic curve methods of factorization. Math Comput 48(177):243–264
Nguyen Duc A, Ronald J, Pangkaj P, Abrahamsson P (2017) Security challenges in IoT development: a software engineering perspective. pp.1-5
Nguyen XT, Tran HT, Baraki H, Geihs K (2015) FRASAD: A framework for model-driven IoT Application Development. In: 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, pp 387–392
Patarin J (1996) Hidden _elds equations (HFE) and isomorphisms of polynomials (IP): two new families of asymmetric algorithms. In: U. M. Maurer, editor, EUROCRYPT '96, volume 1070 of LNCS, pp. 33-48
Pustišek M, Kos A (2018) “Approaches to front-end IoT application development for the ethereum blockchain”, Science Direct. Procedia Comput Sci 129:410–419
Riahi A, Challal Y, Natalizio E, Chtourou Z, Bouabdallah A (2013) A aystemic approach for IoT security. DCOSS, Boston, United States. pp.351-355
Savola RM, Savolainen P, Evesti A, Abie H, Sihvonen M (2015) Risk-driven security metrics development for an e-health IoT application. 2015 Information Security for South Africa (ISSA), Johannesburg, South Africa, pp. 1-6
Shami TM, Grace D, Burr A (2018) Load balancing and control using particle swarm optimisation in 5G heterogeneous networks. IEEE:1–6
Shayla I, Khalifa OO, Abdalla HAH, Kamrul HM, Razzaque MA, Biswajeet P. (2020). Design and Evaluation of a Multihoming-Based Mobility Management Scheme to Support Inter Technology Handoff in PNEMO. Wireless Personal Communications, pp.1-21. https://doi.org/10.1007/s11277-020-07412-0
Sreeja R, Paul V, Menon VG, Khosravi MR (2019) A secure and efficient lightweight symmetric encryption scheme for transfer of text files between embedded iot devices. Symmetry 11(2):293
Suma DV (2019) Towards sustainable industrialization using big data and internet of things. J IoT in Social, Mobile, Analytics, Cloud 1(1):24–37
Sutjiatmo BP, Erwinsyah A, Lydia EL, Shankar K et al (2019) Empowering internet of things (IoT) through big data. Int J Eng Adv Technol 8, no. 6S2:938–942
Tellez M, El-Tawab S, Heydari MH (2016) IoT security attacks using reverse engineering methods on WSN applications. 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, pp. 182-187
Tweneboah-Koduah S, Skouby KE, Tadayoni R (2017) Cyber security threats to IoT applications and service domains. Wirel Pers Commun 95:169–185
Ukil A, Bandyopadhyay S, Bhattacharyya A, Pal A, Bose T (2014) Lightweight security scheme for IoT applications using CoAP. Int J Pervasive Comput Commun 10(4):372–392
Weiqiang L, Jian N, Zhe L, Chunyang L, O'Neill M (2019) Optimized modular multiplication for supersingular isogeny diffie-hellman. IEEE Trans Comput:1–1
Yashwant D, Joshi V (2018) “Some issues on architecture for secure services for IoT”, Department of Electronics and Telecommunication. Engineering:1–13
Acknowledgements
The authors would like to express their gratitude to the Ministry of Higher Education Malaysia for funding this research project through Fundamental Research Grant Scheme (FRGS) with Project Code: FRGS/1/2022/TK02/UCSI/02/1 and also to UCSI University, Malaysia.
Funding
Not Applicable
Author information
Authors and Affiliations
Contributions
N.Madhusudhan Reddy-Literature review, methodology
Budati Anil Kumar-Results development
Shayla Islam-Rough & Main draft preparation
Gajula Ramesh-Results validation
Corresponding author
Ethics declarations
Ethical Approval
Not Applicable
Competing interests
Personal Nature
Additional information
Communicated by: Dr S B Goyal
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Reddy, N.M., Budati, A.K., Islam, S. et al. Enhanced Elliptic Curve- Diffie Hellman Technique with Bigdata Analytics for Satellite Image Security Enhancement in Internet of Things Systems. Earth Sci Inform 17, 711–723 (2024). https://doi.org/10.1007/s12145-023-01194-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12145-023-01194-2