Abstract
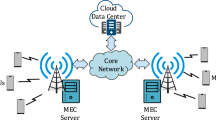
Mobile Edge Computing (MEC), which is a product of 5G technology development, is actually a kind of edge computing form. It takes the base station as the edge server and sinks the cloud computing services to the network edge. To better protect the users and the base stations, a lightweight authentication and key agreement scheme, which is applicable to the MEC field, is proposed in this paper. It achieves secure and efficient key agreement under the premise that the users and the edge servers are completely anonymous and untraceable. For this scheme, instead of the complicated elliptic curve computation and the bilinear pairing computation, it flexibly adopts a number of temporarily generated symmetric keys to realize the identity authentication of the three parties while guaranteeing both the security and efficiency. Compared with other schemes, it is featured in low performance requirements and can better adapt to MEC environment.

Similar content being viewed by others
References
Shi W, Cao J, Zhang Q, Li Y, Xu L (2016) Edge computing: Vision and challenges. IEEE Internet of Things J 3(5):637–646. https://doi.org/10.1109/JIOT.2016.2579198
Hassan N, Yau KLA, Wu C (2019) Edge computing in 5g: a review. IEEE Access 7:127276–127289. https://doi.org/10.1109/ACCESS.2019.2938534
Hu YC, Patel M, Sabella D, Sprecher N, Young V (2015) Mobile edge computing–a key technology towards 5g. ETSI White Paper 11(11):1–16
Mijumbi R, Serrat J, Gorricho JL, Latre S, Charalambides M, Lopez D (2016) Management and orchestration challenges in network functions virtualization. IEEE Commun Mag 54(1):98–105. https://doi.org/10.1109/MCOM.2016.7378433
Ghaznavi M, Khan A, Shahriar N, Alsubhi K, Ahmed R, Boutaba R (2015) Elastic virtual network function placement. In: 2015 IEEE 4th International Conference on Cloud Networking (CloudNet), IEEE, pp 255–260. https://doi.org/10.1109/CloudNet.2015.7335318
Varghese B, Wang N, Barbhuiya S, Kilpatrick P, Nikolopoulos DS (2016) Challenges and opportunities in edge computing. In: 2016 IEEE International Conference on Smart Cloud (SmartCloud), IEEE, pp 20–26. https://doi.org/10.1109/SmartCloud.2016.18
Fettweis GP (2014) The tactile internet: Applications and challenges. IEEE Vehic Technol Mag 9(1):64–70. https://doi.org/10.1109/MVT.2013.2295069
Al-Fuqaha A, Guizani M, Mohammadi M, Aledhari M, Ayyash M (2015) Internet of things: a survey on enabling technologies, protocols, and applications. IEEE Commun Surv Tutor 17(4):2347–2376. https://doi.org/10.1109/COMST.2015.2444095
Moores V (2017) The internet of me: technology can improve the passenger experience, but you still need good service. Air Transport World
Chang KC, Seow YM (2019) Protective measures and security policy non-compliance intention: it vision conflict as a moderator. J Organization End User Comput (JOEUC) 31(1):1–21. https://doi.org/10.4018/JOEUC.2019010101
Rana S, Mishra D, Arora R (2021) Privacy-preserving key agreement protocol for fog computing supported internet of things environment. Wirel Personal Commun 1–21. https://doi.org/10.1007/s11277-021-08234-4
Shen J, Yang H, Wang A, Zhou T, Wang C (2019) Lightweight authentication and matrix-based key agreement scheme for healthcare in fog computing. Peer-to-Peer Netw App 12(4):924–933. https://doi.org/10.1007/s12083-018-0696-3
Wazid M, Das AK, Kumar N, Vasilakos AV (2019) Design of secure key management and user authentication scheme for fog computing services. Futur Gen Comput Syst 91:475–492. https://doi.org/10.1016/j.future.2018.09.017
Mo J, Hu Z, Chen H, Shen W (2019) An efficient and provably secure anonymous user authentication and key agreement for mobile cloud computing. Wirel Commun Mobil Comput 2019. https://doi.org/10.1155/2019/4520685
Odelu V, Das AK, Kumari S, Huang X, Wazid M (2017) Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Futur Gen Comput Syst 68:74–88. https://doi.org/10.1016/j.future.2016.09.009
Azees M, Vijayakumar P, Deboarh LJ (2017) EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans Intell Transport Syst 18(9):2467–2476. https://doi.org/10.1109/TITS.2016.2634623
Maria A, Pandi V, Lazarus JD, Karuppiah M, Christo MS (2021) BBAAS: Blockchain-based anonymous authentication scheme for providing secure communication in vanets. Secur Commun Netw 2021. https://doi.org/10.1155/2021/6679882
Wang C, Huang R, Shen J, Liu J, Vijayakumar P, Kumar N (2021) A novel lightweight authentication protocol for emergency vehicle avoidance in vanets. IEEE Internet of Things J. https://doi.org/10.1109/JIOT.2021.3068268
Chen CM, Huang Y, Wang KH, Kumari S, Wu ME (2020) A secure authenticated and key exchange scheme for fog computing. Enterprise Information Systems, pp 1–16. https://doi.org/10.1080/17517575.2020.1712746
Tsai JL, Lo NW (2015) A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst J 9(3):805–815. https://doi.org/10.1109/JSYST.2014.2322973
Mishra D, Dharminder D, Yadav P, Rao YS, Vijayakumar P, Kumar N (2020) A provably secure dynamic id-based authenticated key agreement framework for mobile edge computing without a trusted party. J Info Secur App 55:102648. https://doi.org/10.1016/j.jisa.2020.102648
Jia X, He D, Kumar N, Choo KKR (2019) Authenticated key agreement scheme for fog-driven iot healthcare system. Wirel Netw 25(8):4737–4750. https://doi.org/10.1007/s11276-018-1759-3
Xue J, Bai Z (2021) Security and efficient authentication scheme for mobile edge computing. J Beijing Univ Posts Telecommun 44:110–116. https://doi.org/10.13190/j.jbupt.2020-005
Li X, Zhang Y, Liu X, Cao J, Zhao Q (2012) A lightweight roaming authentication protocol for anonymous wireless communication. In: 2012 IEEE Global Communications Conference (GLOBECOM), IEEE, pp 1029–1034. https://doi.org/10.1109/GLOCOM.2012.6503248
Mahmood K, Chaudhry SA, Naqvi H, Kumari S, Li X, Sangaiah AK (2018) An elliptic curve cryptography based lightweight authentication scheme for smart grid communication. Futur Gen Comput Syst 81:557–565. https://doi.org/10.1016/j.future.2017.05.002
Canetti R, Krawczyk H (2001) Analysis of key-exchange protocols and their use for building secure channels. In: International conference on the theory and applications of cryptographic techniques, Springer, pp 453–474. https://doi.org/10.1007/3-540-44987-6_28
Zhao R, Wang X, Xia J, Fan L (2020) Deep reinforcement learning based mobile edge computing for intelligent internet of things. Phys Commun 43:101184. https://doi.org/10.1016/j.phycom.2020.101184
Syverson P, Cervesato I (2000) The logic of authentication protocols. In: International School on Foundations of Security Analysis and Design, Springer, pp 63–137. https://doi.org/10.1007/3-540-45608-2_2
Syverson PF, Van Oorschot PC (1994) On unifying some cryptographic protocol logics. In: Proceedings of 1994 IEEE Computer Society Symposium on Research in Security and Privacy, IEEE, pp 14–28. https://doi.org/10.1109/RISP.1994.296595
Syverson, Paul F and Van Oorschot, Paul C (1996) A unified cryptographic protocol logic. Technical Report, Naval Research Lab Washington DC. https://doi.org/10.21236/ada464967
Burrows M, Abadi M, Needham RM (1989) A logic of authentication. Proc Royal Soc London A Math Phys Sci 426(1871):233–271. https://doi.org/10.1098/rspa.1989.0125
Gong L, Needham RM, Yahalom R (1990) Reasoning about belief in cryptographic protocols. In: IEEE Symposium on Security and Privacy, Citeseer, pp 234–248. https://doi.org/10.1109/risp.1990.63854
Abadi M, Tuttle MR (1991) A semantics for a logic of authentication. In: Proceedings of the tenth annual ACM symposium on Principles of distributed computing, pp 201–216. https://doi.org/10.1145/112600.112618
Mao W, Boyd C (1993) Towards formal analysis of security protocols. In: 1993 Proceedings Computer Security Foundations Workshop VI, IEEE, pp 147–158. https://doi.org/10.1109/CSFW.1993.246631
Hou J, Huang L (2004) Research on formal verification and design of security protocols. Tsinghua University
Ma M, He D, Wang H, Kumar N, Choo KKR (2019) An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet of Things J 6(5):8065–8075. https://doi.org/10.1109/JIOT.2019.2902840
Gupta DS, Islam SH, Obaidat MS, Vijayakumar P, Kumar N, Park Y (2020) A provably secure and lightweight identity-based two-party authenticated key agreement protocol for iiot environments. IEEE Syst J 15(2):1732–1741. https://doi.org/10.1109/JSYST.2020.3004551
Liu J, Li Q, Sun R, Du X, Guizani M (2018) An efficient anonymous authentication scheme for internet of vehicles. In: 2018 IEEE International Conference on Communications (ICC), IEEE, pp 1–6. https://doi.org/10.1109/ICC.2018.8422447
Jia X, He D, Kumar N, Choo KKR (2019) A provably secure and efficient identity-based anonymous authentication scheme for mobile edge computing. IEEE Syst J 14(1):560–571. https://doi.org/10.1109/JSYST.2019.2896064
Eftekhari SA, Nikooghadam M, Rafighi M (2021) Security-enhanced three-party pairwise secret key agreement protocol for fog-based vehicular ad-hoc communications. Vehic Commun 28:100306. https://doi.org/10.1016/j.vehcom.2020.100306
Yao M, Wang X, Gan Q, Lin Y, Yang Y (2022) A key-insulated secure multi-server authenticated key agreement protocol for edge computing-based vanets. Available at SSRN 4048732. https://doi.org/10.2139/ssrn.4048732
Deebak BD, Al-Turjman F, Mostarda L (2020) Seamless secure anonymous authentication for cloud-based mobile edge computing. Comput Electric Eng 87:106782. https://doi.org/10.1016/j.compeleceng.2020.106782
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yukun, Z., Wenxue, W. Lightweight anonymous authentication and key agreement protocols for mobile edge computing. Peer-to-Peer Netw. Appl. 15, 1994–2006 (2022). https://doi.org/10.1007/s12083-022-01333-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-022-01333-4