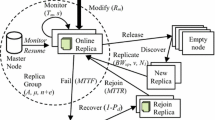
Abstract
Virtual world has the potential to become a future global electronic marketplace, integrating many isolated markets in many areas. To achieve this goal, future virtual world is required to be persistent, implying that a virtual world together with its accumulated content shall exist forever regardless of dynamic changes of its users and owners. Unfortunately, existing virtual worlds, owning by some entities, are not immune from death due to business entity failure. To provide a persistent virtual world, a decentralized architecture is explored, which is constructed on user contributed devices. However, there are many challenges to realize a decentralized virtual world. One important issue is user cooperation in reliable content storage. The devices contributed by users may not be reliable for maintaining all user contents, but users do not have the incentive to provide reliable devices for others. This paper addresses the issue by two steps. First, an indicator, called replica group reliability, is provided to users, which is based on the proposed replicability index. Based on the indicator, users can learn the reliability of their content storage. Then, a new user incentive mechanism, called equity-based node allocation strategy, is proposed to promote user cooperation to collectively maintain reliable content storage. A decentralized algorithm implementing the strategy is designed and the evaluation results show its effectiveness and efficiency.









Similar content being viewed by others
Notes
The inactive virtual world list in http://opensimulator.org/wiki/Grid_List.
References
Dionisio JDN, Gilbert R (2013) 3D virtual worlds and the metaverse: current status and future possibilities. ACM Comput Surv (CSUR) 45(3):34
Tredinnick L (2018) Virtual realities in the business world. Bus Inf Rev 35(1):39–42
Zhou M, Leenders MA, Cong LM (2018) Ownership in the virtual world and the implications for long-term user innovation success. Technovation. https://doi.org/10.1016/j.technovation.2018.06.002
Shen B, Guo J, Li LX (2018) Cost optimization in persistent virtual world design. Inf Technol Manag 19(3):108–114
Lua EK, Crowcroft J, Pias M, Sharma R, Lim S (2005) A survey and comparison of peer-to-peer overlay network schemes. IEEE Commun Surv Tutor 7:72–93
Adams JS (1965) Inequity in social exchange. Adv Exp Soc Psychol 2:267–299
Adams JS (1963) Towards an understanding of inequity. J Abnorm Soc Psychol 67:422
Krishnan R, Smith MD, Telang R (2003) The economics of peer-to-peer networks. Available at SSRN: https://ssrn.com/abstract=504062 or http://dx.doi.org/10.2139/ssrn.504062. Accessed 8 May 2017
Shen B, Wang B, Guo J (n.d.) Full list of sample virtual worlds. http://www.cis.umac.mo/~jzguo/pages/virtualworlds/list.html. Accessed 22 Oct 2016
Gilmore JS, Engelbrecht HA (2012) A survey of state persistency in peer-to-peer massively multiplayer online games. IEEE Trans Parallel Distrib Syst 23:818–834
Frécon E, Stenius M (1998) DIVE: a scaleable network architecture for distributed virtual environments. Distrib Syst Eng 5:91
Singh G, Serra L, Png W, Ng H (1994) BrickNet: a software toolkit for network-based virtual worlds. Presence Teleoper Virtual Environ 3:19–34
Kazman R (1993) Making WAVES: on the design of architectures for low-end distributed virtual environments. In: Virtual reality annual international symposium, IEEE, pp 443–449
Greenhalgh C, Purbrick J, Snowdon D (2000) Inside MASSIVE-3: flexible support for data consistency and world structuring. In: Proceedings of the third international conference on collaborative virtual environments, pp 119–127
Engelbrecht HA, Gilmore JS (2017) Pithos: distributed storage for massive multi-user virtual environments. ACM Trans Multimed Comput Commun Appl 13:31
Holzapfel S, Schuster S, Weis T (2011) VoroStore—a secure and reliable data storage for peer-to-peer-based MMVEs. In: 2011 IEEE 11th international conference on computer and information technology (CIT) pp 35–40
Varvello M, Diot C, Biersack EW (2009) P2P second life: experimental validation using Kad. In: INFOCOM 2009, IEEE, pp 1161–1169
Carlini E, Ricci L, Coppola M (2013) Flexible load distribution for hybrid distributed virtual environments. Future Gener Comput Syst 29:1561–1572
Shen B, Guo J (2018) Virtual net: a decentralized architecture for interaction in mobile virtual worlds. Wirel Commun Mobile Comput 2018:24
Bhagwan R, Tati K, Cheng Y, Savage S, Voelker GM (2004) Total recall: system support for automated availability management. In: Proceedings of the 1st conference on networked systems design and implementation (NSDI)
Adar E, Huberman BA (2000) Free riding on Gnutella, First Monday. 5 (2000). http://firstmonday.org/ojs/index.php/fm/article/view/792/701<%3B/Hu96. Accessed 8 May 2017
Oualha N, Roudier Y (2010) Peer-to-peer storage: security and protocols. Nova Science Publishers Inc., Hauppauge
Liu W, Peng D, Lin C, Chen Z, Song J (2010) Enhancing tit-for-tat for incentive in BitTorrent networks. Peer-to-Peer Netw Appl 3:27–35
Lillibridge M, Elnikety S, Birrell A, Burrows M, Isard M (2003) A cooperative internet backup scheme. In: Proceedings of the annual conference on USENIX annual technical
Shen H, Lin Y, Li Z (2013) Refining reputation to truly select high-QoS servers in peer-to-peer networks. IEEE Trans Parallel Distrib Syst 24:2439–2450
Oualha N, Roudier Y (2011) Securing P2P storage with a self-organizing payment scheme. In: Data privacy management, autonomous spontaneous security, and security assurance. Springer, Berlin, pp 155–169
Vishnumurthy V, Chandrakumar S, Sirer EG (2003) Karma: a secure economic framework for peer-to-peer resource sharing. In: Workshop on economics of peer-to-peer systems
Guo J, Gong Z (2011) Measuring virtual wealth in virtual worlds. Inf Technol Manag 12(2):121–135
Austin W, Walster E (1974) Reactions to confirmations and disconfirmations of expectancies of equity and inequity. J Pers Soc Psychol 30:208–216
Messe LA, Dawson JE, Lane IM (1973) Equity as a mediator of the effect of reward level on behavior in the Prisoner’s Dilemma game. J Pers Soc Psychol 26:60
Radinsky TL (1969) Equity and inequity as a source of reward and punishment. Psychon Sci 15:293–295
Wicker AW, Bushweiler G (1970) Perceived fairness and pleasantness of social exchange situations: two factorial studies of inequity. J Pers Soc Psychol 15:63
Patchen M (1961) The choice of wage comparisons. Prentice-Hall, Englewood Cliffs
Walster E, Traupmann J, Walster GW (1978) Equity and extramarital sexuality. Arch Sex Behav 7:127–142
Leventhal GS, Allen J, Kemelgor B (1969) Reducing inequity by reallocating rewards. Psychon Sci 14:295–296
Telly CS, French WL, Scott WG (1971) The relationship of inequity to turnover among hourly workers. Adm Sci Q 17:164–172. https://doi.org/10.2307/2391826
Schmitt DR, Marwell G (1972) Withdrawal and reward reallocation as responses to inequity. J Exp Soc Psychol 8:207–221. https://doi.org/10.1016/S0022-1031(72)80002-7
Xu C, Gamage S, Rao PN, Kangarlou A, Kompella RR, Xu D (2012) vSlicer: latency-aware virtual machine scheduling via differentiated-frequency CPU slicing. In: Proceedings of the 21st international symposium on high-performance parallel and distributed computing, June 2012, pp 3–14
Donald EK et al (1999) The art of computer programming. Sort Search 3:426–458
Massoulié L, Le Merrer E, Kermarrec A-M, Ganesh A (2006) Peer counting and sampling in overlay networks: random walk methods. In: Proceedings of the twenty-first annual ACM-SIAM symposium principles of distributed computing, pp 123–132
Jelasity M, Montresor A (2004) Epidemic-style proactive aggregation in large overlay networks. In: Proceedings of the 24th international conference on distributed computing systems, pp 102–109
Van De Bovenkamp R, Kuipers F, Van Mieghem P (2012) Gossip-based counting in dynamic networks. Network 2012:404–417
Knoll M, Wacker A, Schiele G, Weis T (2008) Bootstrapping in peer-to-peer systems. In: 14th IEEE international conference on parallel and distributed systems 2008. ICPADS’08, pp 271–278
Acknowledgements
This research was partially supported by the University of Macau Research Grant No. MYRG2017-00091-FST.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Derivation of replicability
Replicability (w) is measured by the maximal amount of data that can be transferred in a replication. In a logical computer, let N1 be the expected number of live replica when a replication is triggered, tr be the average time of all N2 replica fails, and τr be the expected residual life of one live replica. During tr, the average residual life (τr) of a replica can be simply estimated by τr = tr/2 (since the residual life of a replica can be any time between 0 and tr). Given the minimal upload bandwidth assigned for replication (BWup), the total amount of data that can be uploaded is bounded to:
The average time of all N1 replica fails can be estimated by tr= N1/Rf, where Rf is the replica failure rate (i.e., the average number of replica failure within a time unit). Its reciprocal is the period of replica failure, denoted by Tf, indicating the expected length of two replica failure. For N replicas, suppose their time-to-failure (TTF) is uniformly distributed with the mean value equal to the global node mean time-to-failure (MTTF). Let t1 be the TTF of replica 1, t2 be the TTF of 2, …, and tN be the TTF of replica N. On average, t1 = Tf, t2 = 2Tf, …, tN= N·Tf, and
Therefore, Tf and Rf can be estimated by
By bringing tr= N1/Rf and (7) into (6), w can be converted to:
In the LCR model, two replication thresholds, the minimal number of replica (n) and the maximal number of replica (n + e), are maintained in a logical computer for replication cost minimization [4]. Specifically, a replication procedure will be triggered once (e +1) replicas are failed. Thus, N1 can be estimated by (n −1) and (9) can be converted to:
In (10), the number of extra replicas (e) is related to node stability and content size [4], complicating the estimation of w. To simplify the estimation, e can be restricted to its maximum (E). When e reaches its maximum, w will reach its minimum. So logically, as long as the minimum w can meet replication requirement, the actual one from a smaller e is definitely sufficient, and (10) can be converted to
Since BWup, n, and E are constants and selected in configuration, w is only related to MTTF, that is,
Appendix B: Proof of Theorem 1
Theorem 1
(Weak equity achievement) For any time ti and tj, if a device chain is maintained and sorted both at ti and tj, then weak equity can be achieved.
Proof
The theorem can be proved by three steps. Step 1 proves that minimizing the difference user return and user contribution is the only way to minimize the difference of return/contribution ratio among all users. Step 2 proves that a sorted device chain can provide the minimal difference between user return and user contribution. Lastly, Step 3 proves that the equity can be maintained along with time.
-
Step 1 Let D1, D2, …, Dn be n devices belonging to User 1, User 2, …, User n, MTTFi be the MTTF of Di, MTTFi,c (MTTFi,r) be the MTTF corresponding to User i’s contributed (received) replicability, and MTTFi,r be the set of MTTFs of the devices providing User i’s received replicability. Moreover, let avg(·) be the function calculating the average value of a given set.
To minimize \( \left| {\frac{{w_{\rm{r}}^{i} }}{{w_{\rm{c}}^{i} }} - \frac{{w_{\rm{r}}^{j} }}{{w_{\rm{c}}^{j} }}} \right| \), |wir − p·wic |, |wjr − q·wjc |, and |p − q| also have to be minimized. In another word, both wir and wjr are approximately the p times of wic and wjc . If p = q > 1, it means all users receive more replicability than their contributed replicability, which is impossible for Dn without out-of-band resource contribution. On the other hand, if p = q <1, it means all users receive less replicability than their contributed replicability, which is impossible for D1 without out-of-band resource depletion. An exception for p = q ≠1 without the above restriction is the condition that wir = wjr , wic = wjc , and wir ≠ wic . A proof by contradiction can falsify this condition. Specifically, wir ≠ wic means MTTFr≠MTTFc. However, as w = A·MTTF, if wir = wjr , then MTTFi = MTTFj for any device Di and Dj. As avg(MTTFi,r) = MTTFi,r, then MTTFi,r = MTTFi,c leading to a contradiction. Thus, the only way to minimize \( \left| {\frac{{w_{\rm{r}}^{i} }}{{w_{\rm{c}}^{i} }} - \frac{{w_{\rm{r}}^{j} }}{{w_{\rm{c}}^{j} }}} \right| \), is to minimize |wir −·wic | and |wjr −·wjc |, that is, to make user return approach to user contribution.
-
Step 2 Let Di be a device in a device chain L sorted in devices’ observed MTTF, DN be the set of the k neighboring devices of Di, and Df be a device in DN such that \( \left| {{\text{MTTF}}_{i} {-}{\text{MTTF}}_{f} } \right|{\text{ }} \ge {\text{ }}\left| {{\text{MTTF}}_{i} {-}{\text{MTTF}}_{m} } \right| \) for any device Dm in DN.
DN provides the least difference of user return and user contribution to Di, which can be proved by contradiction. If there is another device Da (Da ∉ DN) which can provide a smaller difference of user return and user contribution to Di, then \( \left| {{\text{MTTF}}_{i} {-}{\text{MTTF}}_{f} } \right| > \left| {{\text{MTTF}}_{i} {-}{\text{MTTF}}_{a} } \right| \), which means that L is not sorted in devices’ observed MTTF and a contradiction is found. Therefore, a sorted device chain can provide the minimal difference between user return and user contribution.
-
Step 3 The periodical execution of the position change routine ensures that the equity can be maintained along with time.
Rights and permissions
About this article
Cite this article
Shen, B., Tan, W., Guo, J. et al. An equity-based incentive mechanism for persistent virtual world content service. SOCA 14, 227–241 (2020). https://doi.org/10.1007/s11761-020-00297-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11761-020-00297-8