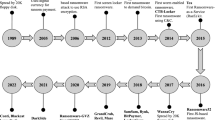
Abstract
Network security faces an escalating threat from hacker attacks due to the proliferation and extensive adoption of computer and internet technology. Ransomware, a prevalent form of malicious software, is frequently employed in cyberattacks to deceive victims into revealing their confidential and sensitive data. Consequently, victims may find themselves unable to retrieve their data unless they yield to ransom demands for stolen files or information. To tackle these challenges, a range of countermeasures and strategies have been devised. In this experiment, A Ransomware Detection Service first exposes all current and upcoming ransomware in Windows file shares. This system helps to detect when/where ransomware has shot Windows file shares or local drives. This system doesn't avoid ransomware viruses, instead it trains or informs operators to not remove the files that are duplicated from the “SourcePath”. The “Find Ransomware Files” tab facilitates determining harm affected by a prior uncaught virus. “Audit Files” tab will navigate a directory, parallel file signatures for required file extensions, and build an authenticated files list, unauthenticated files list (likely corrupted/encrypted files), undetermined files list, and forbidden files list. These lists are compiled to form a dataset with 50 feature columns and a Classifier to train a Machine Learning model to predict future Phishing and Ransomware attacks. A Logistic Regression and Random Forest Classifier achieve an accuracy of 98% in predicting unseen file shares, which makes this method a popular one to consider in the realm of Ransomware Detection. Our aim is to highlight vital defense upgrade in machine learning-centered methods for ransomware detection before utilization in the wild. Our outcomes and findings should put appropriate inquiries for supporters such as how machine learning prototypes can be made more flexible for strong implementation of security goals.











Similar content being viewed by others
Data Availability
The datasets analyzed during the current study are available from the corresponding author on reasonable request.
References
Kharaz, A., Arshad S. (2016). Unveil: A large-scale, automated approach to detecting ransomware. In USENIX security symposium.
Kiraz, M. S., et al. (2017). Detecting large integer arithmetic for defense against crypto ransomware. Cryptology ePrint Archive.
Daku, H., Zavarsky, P., Malik, Y. (2018). Behavioral based classification and identification of ransomware variants using machine learning. In 17th IEEE international conference on trust, security and privacy in computing and communications/12th IEEE international conference on big data science and engineering (TrustCom/BigDataSE) (pp. 1560–1564). IEEE.
Sgandurra, D., Muoz-Gonzlez, L., Mohsen, R., & Lupu, E. C. (2016). Automated dynamic analysis of ransomware: Benefits, limitations and use for detection. arXiv preprint arXiv:1609.03020
Alhawi, O. M. K., Baldwin, J., & Dehghantanha, A. (2018). Leveraging machine learning techniques for windows ransomware network traffic detection (pp. 93-106N). Springer.
Ravi, N., Dandekar, N., Mysore, P., Littman, M. L. (2005). Activity recognition from accelerometer data. In AAAI (vol. 5, pp. 1541–1546).
Azmoodeh, A., Dehghantanha, M. C., & Choo, K.-K.R. (2018). Detecting crypto-ransomware in IoT networks based on energy consumption footprint. Journal of Ambient Intelligence and Humanized Computing, 9(4), 1141–1152.
You, K., & Yim, I. (2016). Malware obfuscation techniques: A brief survey. In International conference on broadband, wireless computing communication and application.
Robert, L. (2014). We live security. [Online].
Shaukat, S. K., Ribeiro, V. J. (2018). Ransom wall: A Layered défense system against cryptographic ransomware At-tacks using machine learning. In IEEE–2018 10th international conference on communication systems & networks (COMSNETS).
Honda, T., Mukaiyama, K., Shirai, T., Ohki, T., Nishigaki, M. (2018). Ransomware detection considering user’s document editing. In IEEE–2018 IEEE 32nd international conference on advanced information networking and applications.
Zhang, H., et al. (2019). Classification of ransomware families with machine learning based on N-gram of opcodes. Future Generation Computer Systems, 90, 211–221.
Baldwin, J., & Dehghantanha, A. (2018). Leveraging support vector machine for opcode density based detection of crypto-ransomware. Cyber Threat Intelligence, 70, 107–136.
Subedi, K. P., et al. (2018). Forensic analysis of ransomware families using static and dynamic analysis. In 2018 IEEE security and privacy workshops (SPW) (pp. 180–185).
Shaukat, S. K., Ribeiro, V. J. (2018). Ransomwall: A layered defense system against cryptographic ransomware attacks using machine learning. In 10th international conference on communications systems & networks (COMSNETS) (pp. 356–363).
Ferrante, A., et al. (2017). Extinguishing ransomware—a hybrid approach to android ransomware detection. In International symposium on foundations and practice of security (pp. 242–259).
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no relevant financial or non-financial interests to disclose.
Ethical Approval
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Badrinath, S., Dodhi, R. & Muthalagu, R. Ransomware Detection Service: Execution and Analysis Using Machine Learning Techniques. Wireless Pers Commun 133, 995–1009 (2023). https://doi.org/10.1007/s11277-023-10801-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10801-w