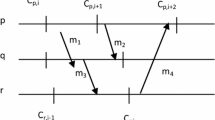
Abstract
Mobile ad hoc networks (MANETs) are increasingly being employed for expanding the computing capabilities of existing cellular mobile systems and in the implementation of mobile computing grids. However, MANETs are susceptible to various transient as well as permanent failures and a fault tolerance technique is crucial in order to effectively utilize the constituent nodes as viable compute resources. Checkpointing and message logging based rollback recovery is a well established approach to provide fault tolerance in static and cellular mobile distributed systems; yet its use for achieving fault tolerance in MANETs is comparatively less explored. The existing recovery algorithms cannot be applied directly to MANETs due to their insufficiency in handling challenges like absence of static infrastructure, frequent node movement, constrained wireless bandwidth and limited stable storage. In this paper, we propose a checkpointing based rollback recovery protocol for clustered MANETs that determines the checkpointing frequency of a mobile node based on its mobility; thereby avoiding unnecessary checkpoints. The protocol uses a popular graph theoretic construct called connected dominating set to lower the communication overhead due to the recovery procedure. The findings of our scheme have been substantiated by the complexity analysis and simulation under varying network conditions.











Similar content being viewed by others
References
Randell, B. (1975). System structure for software fault tolerance. IEEE Transactions on Software Engineering, 1(2), 220–232.
Elnozahy, E. N., Alvisi, L., Wang, Y., & Johnson, D. B. (2002). A survey of rollback-recovery protocols in message-passing systems. ACM Computing Surveys, 34(3), 375–408.
Darby, P. J, I. I. I., & Tzeng, N. (2010). Decentralized QoS-aware checkpointing arrangement in mobile grid computing. IEEE Transactions on Mobile Computing, 9(8), 1173–1186.
Wang, Z., Chen, Q., & Gao, C. (2006). Implementing grid computing over mobile ad-hoc networks based on mobile agent. In Proceedings of the fifth international conference on grid and cooperative computing workshops (pp. 321–326).
Rao, I., Imran, N., Woo Lee, P., Huh, E., & Chung, T. (2006). A proxy based efficient checkpointing scheme for fault recovery in mobile grid system. In Proceedings of the 13th international conference on high performance computing, Lecture notes in computer science (Vol. 4297, pp 448–459).
Alvisi, L., & Marzullo, K. (1998). Message logging: pessimistic, optimistic, causal, and optimal. IEEE Transactions on Software Engineering, 24(2), 149–159.
Acharya, A., & Badrinath, B. R. (1994). Checkpointing distributed applications on mobile computers. In Proceedings of the third international conference on parallel and distributed information systems (pp. 73–80). September 1994.
Prakash, R., & Singhal, M. (1996). Low-cost checkpointing and failure recovery in mobile computing systems. IEEE Transactions on Parallel and Distributed Systems, 7(10), 1035–1048.
Higaki, H., & Takizawa, M. (1998). Checkpoint-recovery protocol for reliable mobile systems. In Proceedings of the seventeenth IEEE symposium on reliable distributed systems (pp. 93–99). October 1998.
Tantikul, T. & Manivannan, D. (2005). A communication-induced checkpointing and asynchronous recovery protocol for mobile computing systems. In Sixth international conference on parallel and distributed computing, applications and technologies (pp. 70–74), December 2005.
Strom, R., & Yemini, S. (1985). Optimistic recovery in distributed systems. ACM Transactions on Computer Systems, 3(3), 204–226.
Park, T., Woo, N., & Yeom, H. Y. (2002). An efficient optimistic message logging scheme for the recoverable mobile computing systems. IEEE Transactions on Mobile Computing, 1(4), 265–277.
George, S. E., Chen, I., & Jin, Y. (2006). Movement based checkpointing and logging for recovery in mobile computing systems. In Proceedings of the 5th ACM international workshop on data engineering for wireless and mobile access (MobiDE ‘06) (pp. 51–58).
Men, C., Xu, Z., & Li, X. (2008). An efficient checkpointing and rollback recovery scheme for cluster-based multi-channel ad hoc wireless networks. In International symposium on parallel and distributed processing with applications (pp. 371–378).
Ono, M., & Higaki., H, (2007). Consistent checkpoint protocol for wireless ad hoc networks. In The 2007 international conference on parallel and distributed processing techniques and applications, USA, (pp. 1041–1046).
Juang, T. T., & Liu, M. C. (2002). An efficient asynchronous recovery algorithm in wireless mobile ad hoc networks. Journal of Internet Technology Special Issue on Wireless Internet: Applications and Systems, 3(2), 147–155.
Haynes, T. W., Hedetniemi, S. T., & Slater, P. J. (1998). Fundamentals of domination in graphs. New York: Marcel Dekker.
Wu, J. & Li, H. (1999). On calculating connected dominating set for efficient routing in ad hoc wireless networks. In Proceedings of the 3rd international workshop on discrete algorithms and methods for mobile computing and communications (pp. 7–14).
Blum, J., Ding, M., Thaeler, A. & Cheng, X. (2005). Connected dominating set in sensor networks and MANETs. In D.-Z. Du. & P. Pardalos (Eds.), Handbook of combinatorial optimization (pp. 329–369). Springer: US.
Yu, J., Wang, N., Wang, G., & Yu, D. (2013). Review: Connected dominating sets in wireless ad hoc and sensor networks—A comprehensive survey. Computer Communications, 36(2), 121–134.
Guha, S., & Khuller, S. (1998). Approximation algorithms for connected dominating sets. Algorithmica, 20(4), 374–387.
Bharghavan, V. & Das, B. (1997). Routing in ad hoc networks using minimum connected dominating sets. In Proceedings of the international conference on communications (pp. 376–380), June 1997.
Yin, B., Shi, H., & Shang, Y. (2011). An efficient algorithm for constructing a connected dominating set in mobile ad hoc networks. Journal of Parallel and Distributed Computing, 71(1), 27–39.
Alzoubi, K. M., Wan, P.-J., & Frieder, O. (2002). Distributed heuristics for connected dominating sets in wireless ad hoc networks. Journal of Communications and Networks, 4(1), 22–29.
Chen, B., Jamieson, K., Balakrishnan, H., & Morris, R. (2002). Span: an energy-efficient coordination algorithm for topology maintenance in ad hoc wireless networks. Wireless Networks, 8(5), 481–494.
Jaggi, P. K. & Singh, A. K. (2012). Preventing useless checkpoints in MANETs. In 2012 2nd IEEE international conference on parallel distributed and grid computing (PDGC) (pp. 533–538).
Plank, J. S., Li, K., & Puening, M. A. (1998). Diskless checkpointing. IEEE Transactions on Parallel and Distributed Systems, 9(10), 972–986.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Jaggi, P.K., Singh, A.K. Movement-Based Checkpointing and Message Logging for Recovery in MANETs. Wireless Pers Commun 83, 1971–1993 (2015). https://doi.org/10.1007/s11277-015-2498-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2498-8