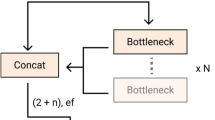
Abstract
Hole detection is a crucial task for monitoring the status of wireless sensor networks (WSN) which often consist of low-capability sensors. Holes can form in WSNs due to the problems during placement of the sensors or power/hardware failure. In these situations, sensing or transmitting data could be affected and can interrupt the normal operation of the WSNs. It may also decrease the lifetime of the network and sensing coverage of the sensors. The problem of hole detection is especially challenging in WSNs since the exact location of the sensors is often unknown. In this paper, we propose a novel hole detection approach called FD-CNN which is based on Force-directed (FD) Algorithm and Convolutional Neural Network (CNN). In contrast to existing approaches, FD-CNN is a centralized approach and is able to detect holes from WSNs without relying on the information related to the location of the sensors. The proposed approach also alleviates the problem of high computational complexity in distributed approaches. The proposed approach accepts the network topology of a WSN as an input and generates the identity of the nodes surrounding each detected hole in the network as the final output. In the proposed approach, an FD algorithm is used to generate the layout of the wireless sensor networks followed by the identification of the holes in the layouts using a trained CNN model. In order to prepare labeled datasets for training the CNN model, an unsupervised pre-processing method is also proposed in this paper. After the holes are detected by the CNN model, two algorithms are proposed to identify the regions of the holes and corresponding nodes surrounding the regions. Extensive experiments are conducted to evaluate the proposed approach based on different datasets. Experimental results show that FD-CNN can achieve 80% sensitivity and 93% specificity in less than 2 minutes.
























Similar content being viewed by others
Notes
FD algorithms can generate both textual and graphical outputs from a given input topology. Textual output contains the coordinates of the nodes in the projected layouts.
References
Abbasi AZ, Islam N, Shaikh ZA et al (2014) A review of wireless sensors and networks’ applications in agriculture. Comput Stand Interfaces 36(2):263–270
Ahmed N, Kanhere SS, Jha S (2005) The holes problem in wireless sensor networks: a survey. ACM SIGMOBILE Mobile Comput Commun Rev 9(2):4–18
Ahn J, Park J, Park D, Paek J, Ko J (2018) Convolutional neural network-based classification system design with compressed wireless sensor network images. PloS one 13(5)
Al Qundus J, Dabbour K, Gupta S, Meissonier R, Paschke A (2020) Wireless sensor network for ai-based flood disaster detection. Annals of Operations Research 1–23
Antil P, Malik A, Kumar S (2016) Neighbor adjacency based hole detection protocol for wireless sensor networks. Procedia Comput Sci 79:866–874
Bayrakdar ME (2020) Enhancing sensor network sustainability with fuzzy logic based node placement approach for agricultural monitoring. Comput Electron Agric 174:105461
Bi K, Tu K, Gu N, Dong WL, Liu X (2006) Topological hole detection in sensor networks with cooperative neighbors. In: 2006 International Conference on Systems and Networks Communications (ICSNC’06), pp. 31–31. IEEE
Cheong SH, Si YW (2016) Accelerating the kamada-kawai algorithm for boundary detection in a mobile ad hoc network. ACM Trans Sensor Netw (TOSN) 13(1):1–29
Cheong SH, Si YW (2017) Boundary node detection and unfolding of complex non-convex ad hoc networks. ACM Trans Sensor Netw (TOSN) 14(1):1–34
Cheong SH, Si YW (2020) Force-directed algorithms for schematic drawings and placement: a survey. Inf Vis 19(1):65–91
Das S, DebBarma MK (2018) Hole detection in wireless sensor network: A review. In: Recent Findings in Intelligent Computing Techniques, pp. 87–96. Springer
Das S, Debbarma MK (2021) A comparative study on coverage-hole detection improvement with inner empty circle over delaunay triangulation method in wireless sensor networks. In: Communication Software and Networks, pp. 553–561. Springer
Davidson R, Harel D (1996) Drawing graphs nicely using simulated annealing. ACM Trans Gr (TOG) 15(4):301–331
Dekkers A, Aarts E (1991) Global optimization and simulated annealing. Math Progr 50(1):367–393
Deng J, Dong W, Socher R, Li LJ, Li K, Fei-Fei L (2009) Imagenet: A large-scale hierarchical image database. In: 2009 IEEE conference on computer vision and pattern recognition, pp. 248–255. Ieee
Fang Q, Gao J, Guibas LJ (2006) Locating and bypassing holes in sensor networks. Mobile Netw Appli 11(2):187–200
Fruchterman TM, Reingold EM (1991) Graph drawing by force-directed placement. Softw: Pract Exp 21(11):1129–1164
Funke S (2005) Topological hole detection in wireless sensor networks and its applications. In: Proceedings of the 2005 joint workshop on Foundations of mobile computing, pp. 44–53
Hajjej F, Hamdi M, Ejbali R, Zaied M (2020) A distributed coverage hole recovery approach based on reinforcement learning for wireless sensor networks. Ad Hoc Netw 101:102082
Jacomy M, Venturini T, Heymann S, Bastian M (2014) Forceatlas2, a continuous graph layout algorithm for handy network visualization designed for the gephi software. PloS one 9(6)
Khalifa B, Al Aghbari Z, Khedr AM (2021) A distributed self-healing coverage hole detection and repair scheme for mobile wireless sensor networks. Sustain Comput: Infor Syst 30:100428
Kirkpatrick S, Gelatt CD, Vecchi MP (1983) Optimization by simulated annealing. Science 220(4598):671–680
Krizhevsky A, Sutskever I, Hinton GE (2012) Imagenet classification with deep convolutional neural networks. Adv Neural Inf Process Syst 25:1097–1105
Lai YH, Cheong SH, Zhang H, Si YW (2021) Coverage hole detection in wsn with force-directed algorithm and transfer learning. Appl Intell pp. 1–22
Long Y, Gong Y, Xiao Z, Liu Q (2017) Accurate object localization in remote sensing images based on convolutional neural networks. IEEE Trans Geosci Remote Sens 55(5):2486–2498
Lu J, Feng L, Yang J, Hassan MM, Alelaiwi A, Humar I (2019) Artificial agent: the fusion of artificial intelligence and a mobile agent for energy-efficient traffic control in wireless sensor networks. Futur Gener Comput Syst 95:45–51
Luo C, Wang B, Cao Y, Xin G, He C, Ma L (2021) A hybrid coverage control for enhancing uwsn localizability using ibso-vfa. Ad Hoc Netw 123:102694
Maturana D, Scherer S (2015) Voxnet: A 3d convolutional neural network for real-time object recognition. In: 2015 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), pp 922–928. IEEE
Meena N, Singh B (2020) Analysis of coverage hole problem in wireless sensor networks. In: Smart Systems and IoT: Innovations in Computing, pp. 187–196. Springer
Naghibi M, Barati H (2020) Egrpm: energy efficient geographic routing protocol based on mobile sink in wireless sensor networks. Sustain Comput: Infor Syst 25:100377
Noack A (2007) Energy models for graph clustering. J Graph Algorithms Appl 11(2):453–480
Oracevic A, Akbas S, Ozdemir S (2017) Secure and reliable object tracking in wireless sensor networks. Comput Secur 70:307–318
Patterson J, Gibson A (2017) Deep learning: A practitioner’s approach. O’Reilly Media, Inc
Prasanth A, Jayachitra S (2020) A novel multi-objective optimization strategy for enhancing quality of service in iot-enabled wsn applications. Peer-to-Peer Netw Appl 13(6):1905–1920
Priyadarshi R, Gupta B, Anurag A (2020) Deployment techniques in wireless sensor networks: a survey, classification, challenges, and future research issues. The Journal of Supercomputing pp 1–41
Ramazani S, Kanno J, Selmic RR, Brust MR (2016) Topological and combinatorial coverage hole detection in coordinate-free wireless sensor networks. Int J Sens Netw 21(1):40–52
Redmon J, Farhadi A (2018) Yolov3: An incremental improvement. arXiv
Rehman Au, Rehman SU, Raheem H (2019) Sinkhole attacks in wireless sensor networks: a survey. Wirel Pers Commun 106(4):2291–2313
Sangwan A, Singh RP (2015) Survey on coverage problems in wireless sensor networks. Wirel Pers Commun 80(4):1475–1500
Senouci MR, Mellouk A, Assnoune K (2013) Localized movement-assisted sensordeployment algorithm for holedetection and healing. IEEE Trans Parallel Distrib Syst 25(5):1267–1277
Tong C, Li J, Zhu F (2017) A convolutional neural network based method for event classification in event-driven multi-sensor network. Comput Electr Eng 60:90–99
Tossa F, Abdou W, Ezin EC, Gouton P (2020) Improving coverage area in sensor deployment using genetic algorithm. In: International Conference on Computational Science, pp 398–408. Springer
Yan F, Ma W, Shen F, Xia W, Shen L (2020) Connectivity based k-coverage hole detection in wireless sensor networks. Mobile Netw Appl 25(2):783–793
Yang J (2021) An ellipse-guided routing algorithm in wireless sensor networks. Digital Commun Netw
Yi L, Deng X, Wang M, Ding D, Wang Y (2017) Localized confident information coverage hole detection in internet of things for radioactive pollution monitoring. IEEE Access 5:18665–18674
Funding
This research was funded by University of Macau (File no. MYRG2019-00136-FST and MYRG2018-00246-FST).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A - Force-directed algorithms
Davidson-Harel algorithm The energy value E used in the simulated annealing defined in the DH algorithm is the sum of attractive force (\(f_a\)) and repulsive force (\(f_r\)), which can be calculated as follows:
During initialization, a node u is randomly selected from the network. Next, the DH algorithm creates a temporary node v. The DH algorithm then assigns the location to the node v based on the location of the node u. The position of the node v and other nodes in the network can be used to calculate the new energy value \(E^{'}\), which is defined as follows:
In addition, when the liquid cools slowly, the DH algorithm obeys the Boltzmann distribution rule [14]. If \(E^{'} - E \le 0\), then use \( E^{\prime } \) as the energy of the next iteration, because \( E^{\prime } \) has a lower energy value. If \(E^{'} - E > 0\), the probability equation is used to determine whether to use the new energy \( E^{\prime } \) in the next iteration. The probability equation is defined as follows:
where T is the temperature variable and k is the Boltzmann constant. If the probability p is less than the threshold \(\varepsilon \), the new energy \( E^{\prime } \) is accepted; otherwise, the old energy E will be used in the next iteration. The time complexity of DH algorithm is \(O(V^2 \times E)\), where V is the number of nodes in the network topology, E is the number of edges in the network topology.
ForceAtlas2 algorithm Jacomy et al. [20] proposed a revised attractiveness based on the LinLog model, which is defined as follows:
where d is the distance between nodes u and v. In addition, a degree-dependent repulsion model is proposed in the FA2 algorithm to reduce the repulsive force. This repulsion model increases the chance that nodes with lower than average degrees are connected to nodes with higher than average degrees. The repulsion model of FA2 algorithm is defined as follows:
where k is the ideal pairwise distance constant, as used in FR algorithm. d is the distance between nodes u and v, and deg(n) is the number of associated edges Node n, including the edge of in-out degree. The time complexity of FA2 algorithm is \(O(V^2+E)\) where V is the number of nodes in the network topology, E is the number of edges in the network topology.
KK-MS-DS algorithm The goal of the KK-MS-DS algorithm [8] is to push the nodes in the outer boundary away from the inner nodes. Nodes tag with a decaying stiffness (m). The higher the decaying stiffness value of the node (m), the farther the distance of the node can be moved. The value of m of the node decreases with the execution time, which is defined as follows:
where t is the number of times that the selected node is updated. p is the decay rate, and z is the remaining energy possessed by the node. The KK-MS-DS algorithm terminates, when the stable state (r) remains unchanged until a predefined iteration or r is less than the threshold \(\varepsilon \). The stable state (r) means that a coarse visualization of the graph has been constructed, but the final stage of the entire graph has not yet been reached. The ratio of the stable state r is defined as follows:
where d is the total number of edges in the graph, \(L^{'}_{i}\) is the edge length from the graph generated by the KK-MS-DS algorithm, and \(L_i\) is the edge length of the input graph. The time complexity of KK-MS-DS algorithm is \(O(n \times (V + v^2))\), where n is the number of iteration, V is the number of nodes in the given graph, and v is the number of nodes in the ordered queue.
Appendix B - Pseudocode of force-directed algorithms
The pseudocode for DH algorithm, FA2 algorithm and KK-MS-DS algorithm are given in Algorithm 4, Algorithm 5 and Algorithm 6 respectively.



Rights and permissions
About this article
Cite this article
Cheong, SH., Ng, KH. & Si, YW. An image classification approach for hole detection in wireless sensor networks. J Supercomput 78, 8774–8809 (2022). https://doi.org/10.1007/s11227-021-04276-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-04276-4