Abstract
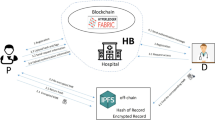
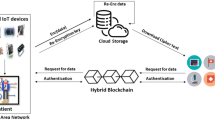
E-healthcare system has been introduced to provide real-time patient health monitoring using IoT sensors and efficiently share patient data with multiple users. Patients need to outsource their health data over the cloud due to the resource-constrained nature of IoT devices and patient devices. While accessing the data from a trusted cloud or distributed users makes health data susceptible and leads to leakage and manipulation. Therefore, we need secure data sharing with fine-grained access control and authentication schemes. The existing proxy re-encryption data sharing schemes use the same key to re-encrypt the patient’s health data more than once, leading to a collusion attack with users. This paper proposes an efficient and collusion-resistant re-encryption scheme (CRRE) with mutual authentication to address the collusion attack that provides privacy-preserving secure data sharing with fine-grained access control. Integrating the CRRE scheme with blockchain provides data integrity, verifiability, accountability, and interoperability between all entities in the e-healthcare system. The random oracle model and AVISPA tool are used to validate the formal and informal security of the CRRE scheme. The proposed scheme is implemented and compared with existing PRE-based schemes on various parameters. The results prove that the proposed CRRE scheme is more efficient and suitable for resource-constrained devices in the e-healthcare system.












Similar content being viewed by others
Data Availability
Data sharing not applicable to this article as no datasets were generated during the current study.
References
AVISPA (2019) Automated validation of internet security protocols and applications. http://www.avispa-project.org/. Accessed: Oct 2019
Agyekum O, Opuni-Boachie K, Qi X, Sifah EB, Gao J, Xia H, Xiaojiang D, Guizani M (2019) A secured proxy-based data sharing module in IoT environments using blockchain. Sensors 19(5):1235
Akpakwu GA, Silva BJ, Hancke GP, Abu-Mahfouz AM (2018) A survey on 5G networks for the internet of things: communication technologies and challenges. IEEE Access 6:3619–3647
Ali M, Abbas A, Khan U, Khan SU (2018) SeSPHR: a methodology for secure sharing of personal health records in the cloud. IEEE Trans Cloud Comput
Ali M, Sadeghi M-R, Liu X (2020) Lightweight revocable hierarchical attribute-based encryption for internet of things. IEEE Access 8:23951–23964
Ara A, Al-Rodhaan M, Tian Y, Al-Dhelaan A (2017) A secure privacy-preserving data aggregation scheme based on bilinear ElGamal cryptosystem for remote health monitoring systems. IEEE Access 5:12601–12617
Ateniese G, Fu K, Green M, Hohenberger S (2005) Improved proxy re-encryption schemes with applications to secure distributed storage. In: Proc. of the 12th Annual network and distributed system security symposium, pp 29–44
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: 2007 IEEE Symposium on security and privacy (SP’07), IEEE, pp 321–334
Blaze M, Bleumer G, Strauss M (1998) Divertible protocols and atomic proxy cryptography. In: Proceedings of Eurocrypt ’98. vol 1403, pp 127–144
Bleichenbacher D (1998) Chosen cipher-text attacks against protocols based on the RSA encryption standard PKCS 1. In: Annual international cryptology conference. Springer, Berlin, pp 1–12
Boneh D, Franklin M (2001) Identity-based encryption from the Weil pairing. In: Annual international cryptology conference. Springer, Berlin, pp 213–229
Cao H, Leung V, Chow C, Chan H (2009) Enabling technologies for wireless body area networks a survey and outlook. IEEE Commun Mag 47(12):84–93
Chu C, Tzeng W (2007) Identity-based proxy re-encryption without random oracles. In: Garay JA, Lenstra AK, Mambo M, Peralta R (eds) ISC 2007. LNCS, vol. 4779. Springer, Berlin, pp 189–202
Deng H, Qin Z, Qianhong W, Guan Z, Zhou Y (2020) Flexible attribute-based proxy re-encryption for efficient data sharing. Inf Sci 511:94–113
Fang L, Susilo W, Ge C, Wang J (2012) Chosen-ciphertext secure anonymous conditional proxy re-encryption with keyword search. Theor Comput Sci 462(20):39–58
Ghazvini A, Shukur Z (2013) Security challenges and success factors of electronic healthcare system. Procedia Technol 11:212–219
Gupta A, Chaurasiya VK (2019) Reinforcement learning based energy management in wireless body area network: a survey. In: 2019 IEEE Conference on information and communication technology, IEEE, pp 1–6
Hidalgo A, Pérez N, Lemus-Aguilar I (2022) Factors Determining the Success of eHealth Innovation Projects. Int J Softw Sci Comput Intell (IJSSCI) 14 (1):1–22
Hong H, Liu X, Sun Z (2018) A fine-grained attribute based data retrieval with proxy re-encryption scheme for data outsourcing systems. Mob Netw Appl 1–6
Huang Q, Yang Y, Jingyi F (2018) PRECISE Identity-based private data sharing with conditional proxy re-encryption in online social networks. Futur Gener Comput Syst 86:1523–1533
Kaur M, Singh D, Kumar V, Gupta BB, Abd El-Latif AA (2021) Secure and energy efficient-based E-health care framework for green internet of things. IEEE Trans Green Commun Netw 5(3):1223–1231
Kocher P, Jaffe J, Jun B (1999) Differential Power Analysis. In: Proceedings of 19th Annual international cryptology conference (CRYPTO’99), Lecture Notes in Computer Science, vol 1666, Santa Barbara, California, USA, pp 388–397
Lai J, Deng RH, Li Y (2012) Expressive, CP-ABE with partially hidden access structures. Computerand Communications Security, Seoul
Li J, Zhang Y, Chen X, Xiang Y (2018) Secure attribute-based data sharing for resource-limited users in cloud computing. Comput Secur 72:1–12
Li H, Zhu L, Shen M, Gao F, Tao X, Liu S (2018) Blockchain-based data preservation system for medical data. J Med Syst 42(8):141
Liang K, Liu JK, Wong DS, Susilo W (2014) An efficient cloud-based revocable identity-based proxy re-encryption scheme for public clouds data sharing. In: Computer security ESORICS 2014, Springer, pp 257–272
Liang K, Man Ho A, Liu JK, Susilo W, Wong DS, Yang G, Yong Y, Yang A (2015) A secure and efficient ciphertext-policy attribute-based proxy re-encryption for cloud data sharing. Futur Gener Comput Syst 52:95–108
Liu Y, Ren Y, Ge C, Xia J, Wang Q (2019) A CCA-secure multi-conditional proxy broadcast re-encryption scheme for cloud storage system. J Inf Secur Appl 47:125–131
Luo W, Ma, W (2018) A secure revocable identity-based proxy re-encryption scheme for cloud storage. In: International conference on cloud computing and security. Springer, Cham, pp 519–530
Nakamoto S (2019) Bitcoin: a peer-to-peer electronic cash system. Manubot
Plageras AP, Stergiou C, Kokkonis G, Psannis KE, Ishibashi Y, Kim BG, Gupta BB (2017) Efficient large-scale medical data (ehealth big data) analytics in internet of things. In: 2017 IEEE 19th Conference on business informatics (CBI), vol 2, IEEE, pp 21–27
Raghav AN, Venkatesan S, Verma S (2020) poEWAL: a lightweight consensus mechanism for blockchain in IoT. Pervasive Mob Comput 69:101291
Rasmusen SC, Penz M, Widauer S, Nako P, Kurteva A, Roa-Valverde A, Fensel A (2022) Raising consent awareness with gamification and knowledge graphs: an automotive use case. Int J Semant Web Inf Syst (IJSWIS) 18(1):1–21
Salhi DE, Tari A, Kechadi MT (2021) Using clustering for forensics analysis on internet of things. Int J Softw Sci Comput Intell (IJSSCI) 13(1):56–71
Sangaiah AK, Medhane DV, Bian G-B, Ghoneim A, Alrashoud M, Hossain MS (2020) Energy-aware green adversary model for cyber physical security in industrial system. IEEE Trans Ind Inform 16(5):3322–3329
Sangaiah AK, Medhane DV, Han T, Hossain MS, Muhammad G (2019) Enforcing position-based confidentiality with machine learning paradigm through mobile edge computing in real-time industrial informatics. IEEE Trans Ind Inform 15(7):4189–4196
Shao J, Cao Z (2009) CCA-Secure proxy re-encryption without pairings. In: Jarecki S, Tsudik G (eds) PKC 2009. LNCS, vol. 5443. Springer, Berlin, pp 357–376
Su M, Bo Z, Anmin F, Yan Y, Gongxuan Z (2020) PRTA a proxy re-encryption based trusted authorization scheme for nodes on CloudIoT. Inf Sci 527:533–547
Sultan N (2014) Making use of cloud computing for healthcare provision: opportunities and challenges. Int J Inf Manag 34(2):177–184
Tewari A, Gupta BB (2020) Secure timestamp-based mutual authentication protocol for iot devices using rfid tags. Int J Semant Web Inf Syst (IJSWIS) 16(3):20–34
Wang C, Fang J, Li Y (2015) An improved cloud-based revocable identity-based proxy re-encryption scheme. In: International conference on applications and techniques in information security. Springer, Berlin, pp 14–26
Wang XA, Huang X, Yang X, Liu L, Wu X (2012) Further observation on proxy re-encryption with keyword search. J Syst Softw 85:643–654
Wang C, Li Y, Fang J, Xie J (2017) Cloud-aided scalable revocable identity-based encryption scheme with cipher-text update. Concurr Comput Pract Exp 29(20):e4035
Wang Q, Li W, Qin Z (2019) Proxy re-encryption in access control framework of information-centric networks. IEEE Access 7:48417–48429
Wang XA, Yang Xiaoyuan, Li Cong, Liu Yudong, Ding Yong (2018) Improved functional proxy re-encryption schemes for secure cloud data sharing. Comput Sci Inf Syst 15(3):585–614
Wood G (2014) Ethereum a secure decentralized generalized transaction ledger. Ethereum Proj Yellow Pap 151(2014):1–32
Wu R, Ahn G-J, Hu H (2012) Secure sharing of electronic health records in clouds. In: Proc. 8th Int. Conf. Collaborative Comput., Netw., Appl Worksharing (CollaborateCom), pp 711–718
Xhafa F, Feng J, Zhang Y, Chen X, Li J (2015) Privacy-aware attributebased PHR sharing with user accountability in cloud computing. J Supercomput 71(5):1607–1619
Xia QI, Sifah EB, Asamoah KO, Gao J, Xiaojiang D, MeDShare MG (2017) Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 5:14757–14767
Xu P, Jiao T, Qianhong W, Wang W, Jin H (2015) Conditional identity-based broadcast proxy re-encryption and its application to cloud email. IEEE Trans Comput 65(1):66–79
Yaacoub J-PA, Noura M, Noura HN, Salman O, Yaacoub E, Couturier R, Chehab A (2020) Securing internet of medical things systems: limitations, issues and recommendations. Futur Gener Comput Syst 105:581–606
Yang Y, Lu H, Weng J, et al. (2014) Fine-grained conditional proxy re-encryption and application. In: Proceedings of the 8th International conference on provable security, pp 206–222
Ying MEI (2017) The utilizing Blockchain-Based method of the secure storage of medical records [J]. J Jiangxi Norm Univ (Nat Sci Ed) 41(5):484–490
Ying Z, Wei L, Li Q, Liu X, Cui J (2018) A lightweight policy preserving EHR sharing scheme in the cloud. IEEE Access 6:53698–53708
Zhang Y, Chen X, Li J, W ong DS, Li H (2013) Anonymous attribute-based encryption supporting efficient decryption test. In: Proceedings o f the 8th ACMSIGSAC symposium on information, computer and communications security. Hangzhou, China
Zhang A, Lin X (2018) Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. J Med Syst 42(8):140
Zhang Y, Zheng D, Deng RH (2018) Security and privacy in smart health: efficient policy-hiding attribute-based access control. IEEE Internet Things J 5(3):2130–2145
Zhang C, Zhu L, Xu C, Lu R (2018) PPDP: an efficient and privacy preserving disease prediction scheme in cloud-based e-Healthcare system. Futur Gener Comput Syst 79:16–25
Zhang C, Zhu L, Xu C, Sharif K, Du X, Guizani M (2019) LPTD: achieving lightweight and privacy-preserving truth discovery in CIot. Futur Gener Comput Syst 90:175–184
Zheng X, Zhou Y, Ye Y, Li F (2020) A cloud data deduplication scheme based on certificateless proxy re-encryption. J Syst Archit 102:101666
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Financial disclosure
The ministry of education under the government of India has sponsored this work.
Conflict of Interests
The authors declare no potential conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Maurya, C., Chaurasiya, V.K. Collusion-resistant and privacy-preserving data sharing scheme on outsourced data in e-healthcare system. Multimed Tools Appl 82, 40443–40472 (2023). https://doi.org/10.1007/s11042-023-15006-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15006-8