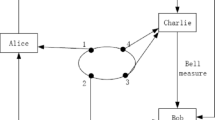
Abstract
Recently, Qiu et al. proposed a semi-quantum voting scheme based on the ring signature (International Journal of Theoretical Physics, 60: 1550–1555(2021)), in which the signer and verifier only need to measure the received particles with Z-basis and perform some classical simple encryption/decryption operations on the classical message. Although their scheme is very efficient, it cannot resist the eavesdropping attacks and forgery attack. In this paper, first, the eavesdropping attacks on Qiu et al.’s scheme are proposed. Second, we show the forgery attack on their scheme. Then, based on the GHZ state, an improved semi-quantum electronic voting protocol is proposed. In the new protocol, the eavesdropping check technology not only can be used to detect the eavesdropping, but also can be used to share a random number. By using the random number and the shared key, the signed vote is encrypted so that it is infeasible for the adversary to trace the signer’s identity and forge a valid signed vote. The new protocol overcomes all the security drawbacks of the old protocol. What is more, it has better practicability and efficiency than the similar semi-quantum voting protocols.
Similar content being viewed by others
Data Availability
No datasets were generated or analysed during the current study.
References
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
Huang, Y., Su, Z., Zhang, F., et al.: Quantum algorithm for solving hyper elliptic curve discrete logarithm problem. Quantum Inf. Process. 19, 62 (2020)
Sutradhar, K., Om, H.: Efficient quantum secret sharing without a trusted player. Quantum Inf. Process. 19(2), 73 (2020)
Sutradhar, K., Om, H.: Secret sharing based multiparty quantum computation for multiplication. Int. J. Theor. Phys. 60(9), 3417–3425 (2021)
Sutradhar, K., Om, H.: Enhanced (t, n) threshold d-level quantum secret sharing. Sci. Rep. 11(1), 17083 (2021)
Sutradhar, K., Om, H.: A generalized quantum protocol for secure multiparty summation. IEEE Trans. Circ. Syst. II Express Briefs. 67(12), 2978–2982 (2020)
Sutradhar, K., Om, H.: Hybrid quantum protocols for secure multiparty summation and multiplication. Sci. Rep. 10(1), 9097 (2020)
Sutradhar, K., Om, H.: An efficient simulation for quantum secure multiparty computation. Sci. Rep. 11(1), 2206 (2021)
Sutradhar, K., Om, H.: A cost-effective quantum protocol for secure multi-party multiplication. Quantum Inf. Process. 20(11), 380 (2021)
Sutradhar, K.: Secure multiparty quantum aggregating protocol. Quantum Inf. Comput. 23(3&4), 245–256 (2023)
Venkatesh, R., Savadatti Hanumantha, B.: Electronic medical records protection framework based on quantum blockchain for multiple hospitals. Multimed Tools Appl. 1–14 (2023). https://doi.org/10.1007/s11042-023-16848-y
Venkatesh, R., Hanumantha, B.S.: A privacy-preserving quantum blockchain technique for electronic medical records. IEEE Eng. Manag. 51(4), 137–144 (2023)
Sutradhar, K.: A quantum cryptographic protocol for secure vehicular communication. IEEE Trans. Intell. Transp. Syst. 1–10 (2023). https://doi.org/10.1109/TITS.2023.3322728
Christandl, M., Wehner, S.: Quantum anonymous transmissions. Roy B. (eds) Advances in Cryptology-ASIACRYPT 2005 3788, 217–235 (2005)
Vaccaro, J.A., Spring, J., Chefles, A.: Quantum protocols for anonymous voting and surveying. Phys. Rev. A 75(1), 012333 (2005)
Hillery, M., et al.: Towards quantum-based privacy and voting. Phys. Lett. A 349(1–4), 75–81 (2006)
Hillery, M.: Quantum voting and privacy protection: first steps. Int. Soc. Opt Eng. (2006). https://doi.org/10.1117/2.1200610.0419
Li, Y., Zeng, G.H.: Quantum anonymous voting systems based on entangled state. Opt. Rev. 15(5), 219–223 (2008)
Horoshko, D., Kilin, S.: Quantum anonymous voting with anonymity check. Phys. Lett. A 375(8), 1172–1175 (2011)
Jiang, L., He, G.Q., Nie, D., Xiong, J., Zeng, G.H.: Quantum anonymous voting for continuous variables. Phys. Rev. A 85(4), 042309 (2012)
Wang, Y.W., Wei, X.H., Zhu, Z.H.: Quantum voting protocols based on the non-symmetric quantum channel with controlled quantum operation teleportation (in Chinese). Acta Phys. Sin. 62(16), 160302 (2013)
Tian, J.H., Zhang, J.Z., Li, Y.P.: A voting protocol based on the controlled quantum operation teleportation. Int. J. Theor. Phys. 55(5), 2303–2310 (2016)
Thapliyal, K., Sharma, R.D., Pathak, A.: Analysis and improvement of Tian-Zhang-Li voting protocol based on controlled quantum teleportation. arXiv:1602.00791 [quant-ph] (2016)
Wang, Q.L., et al.: Self-tallying quantum anonymous voting. Phys. Rev. A 94(2), 022333 (2016)
Qin, J.Q., Shi, R.H., Zhang, R.: Quantum voting protocol based on controlled quantum secure direct communication(in Chinese). Chinese J. Quantum Electron. 35(5), 558–566 (2018)
Li, Y.P., Zhou, F., Wang, T., et al.: Novel quantum voting protocol with eight-qubit cluster entangled state. Int. J. Theor. Phys. 59, 2671–2680 (2020)
Jiang, D.H., Wang, J., Liang, X.Q., et al.: Quantum voting scheme based on locally indistinguishable orthogonal product states. Int. J. Theor. Phys. 59(2), 436–444 (2020)
Liu, B.X., Jiang, D.H., Liang, X.Q., et al.: A novel quantum voting scheme based on BB84-state. Int. J. Theor. Phys. 60(4), 1339–1349 (2021)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7–11 (2014)
Li, Y.R., Jiang, D.H., Zhang, Y.H., et al.: A quantum voting protocol using single-particle states. Quantum Inf. Process. 20, 110 (2021)
Xiong, Z.H., Yin, A.H.: Single particle electronic voting scheme based on quantum ring signature. Mod. Phys. Lett. A 37(26), 2250174 (2022)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical Bob. Phys. Rev. Lett. 99(14), 140501 (2007)
Xu, Y.P., Gao, D.Z., Liang, X.Q., et al.: Semi-quantum voting protocol. Int. J. Theor. Phys. 61(3), 78 (2022)
Qiu, C., Zhang, S.B., Chang, Y., et al.: Electronic voting scheme based on a quantum ring signature. Int. J. Theor. Phys. 60(4), 1550–1555 (2021)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351(1–2), 23–25 (2006)
Gisin, N., Ribordy, G.G., Tittel, W., et al.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–195 (2002)
Deng, F.G., Li, X.H., Zhou, H.Y., Zhang, Z.J.: Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72(4), 044302 (2005)
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74(5), 054302 (2006)
Yang, C.W., Hwang, T., Luo, Y.P.: Enhancement on “Quantum blind signature based on two-state vector formalism.” Quantum Inf. Process. 12(1), 109–117 (2012)
Hwang, T., Lee, K.C.: EPR quantum key distribution protocols with 100% qubit efficiency. IET Inf. Secur. 1(1), 43–45 (2007)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant No.62272090) and the Key Scientific Research Project of Colleges and Universities in Henan Province (Grant No.22A413010).
Funding
This work was funded by Key Scientific Research Project of Colleges and Universities in Henan Province, 22A413010, National Natural Science Foundation of China, 62272090.
Author information
Authors and Affiliations
Contributions
The correctness and security analyzed were presented by Xin Xiangjun and Qiu Shujing, and the manuscript was written by Xin Xiangjun and Qiu Shujing as well. The manuscript was reviewed by Zheng qian, Li Chaoyang and Li Fagen. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing Interest
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Shujing, Q., Xiangjun, X., qian, Z. et al. Security Analysis and Improvements on a Semi-Quantum Electronic Voting Protocol. Int J Theor Phys 63, 79 (2024). https://doi.org/10.1007/s10773-024-05618-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-024-05618-7