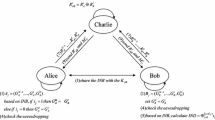
Abstract
Nowadays, there are a lot of quantum private comparison (QPC) protocols put forward with various quantum technologies. These protocols are found to perform QPC generally deploying user-shared keys or entanglement. However, either the establishment of secret keys or the preparation of entangled states is time consuming, and also their relative devices are usually costly. In order to overcome the shortcomings, this work designs a fast QPC protocol only using single particles without keys and entanglement, allowing two users to compare the equality of their secrets under the help of two semi-honest third parties. It would be ideal for cases needing a fast and low-cost QPC, easy to implement with common quantum technologies. These traits make it an alternative way to operate QPC.

Similar content being viewed by others
References
Yang, Y.G., Gao, W.F., Wen, Q.Y.: Secure quantum private comparison. Phys. Scr. 80(6), 065002 (2009)
Liu, B., Gao, F., Jia, H.Y., Huang, W., Zhang, W.W., Wen, Q.Y.: Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process. 12(2), 887–897 (2013)
Chen, X.B., Su, Y., Niu, X.X., Yang, Y.X.: Efficient and feasible quantum private comparison of equality against the collective amplitude damping noise. Quantum Inf. Process. 13(1), 101–112 (2014)
Sun, Z.W., Yu, J.P., Wang, P., Xu, L.L., Wu, C.H.: Quantum private comparison with a malicious third party. Quantum Inf. Process. 14(6), 2125–2133 (2015)
Lang, Y.-F.: Semi-quantum private comparison using single photons. Int. J. Theor. Phys. 57(10), 3048–3055 (2018)
Ye, T.-Y., Ye, C.-Q.: Measure-resend semi-quantum private comparison without entanglement. Int. J. Theor. Phys. 57(12), 3819–3834 (2018)
Yang, Y.G., Xia, J., Jia, X., Shi, L., Zhang, H.: New quantum private comparison protocol without entanglement. Int. J. Quant. Inform. 10(6), 1250065 (2012)
Ye, T.Y.: Quantum private comparison via cavity QED. Commun. Theor. Phys. 67(2), 147–156 (2017)
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A: Math. Theor. 42(5), 055305 (2009)
Liu, W., Wang, Y.B., Cui, W.: Quantum private comparison protocol based on Bell entangled states. Commun. Theor. Phys. 57(4), 583–588 (2012)
Zi, W., Guo, F.Z., Luo, Y., Cao, S.H., Wen, Q.Y.: Quantum private comparison protocol with the random rotation. Int. J. Theor. Phys. 52(9), 3212–3219 (2013)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11(2), 373–384 (2012)
Wang, C., Xu, G., Yang, Y.X.: Cryptanalysis and improvements for the quantum private comparison protocol using EPR pairs. Int. J. Quant. Inform. 11(4), 1350039 (2013)
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Comment on quantum private comparison protocols with a semihonest third party. Quantum Inf. Process. 12(2), 877–885 (2013)
Zhang, W.W., Zhang, K.J.: Cryptanalysis and improvement of the quantum private comparison protocol with semi-honest third party. Quantum Inf. Process. 12(5), 1981–1990 (2013)
Lin, J., Yang, C.W., Hwang, T.: Quantum private comparison of equality protocol without a third party. Quantum Inf. Process. 13(2), 239–247 (2014)
Zhang, B., Liu, X.T., Wang, J., Tang, C.J.: Cryptanalysis and improvement of quantum private comparison of equality protocol without a third party. Quantum Inf. Process. 14(12), 4593–4600 (2015)
Lang, Y.-F.: Quantum gate-based quantum private comparison. Int. J. Theor. Phys. 59(3), 833–840 (2020)
Li, J., Zhou, H.F., Jia, L., Zhang, T.T.: An efficient protocol for the private comparison of equal information based on four-particle entangled W state and Bell entangled states swapping. Int. J. Theor. Phys. 53(7), 2167–2176 (2014)
Liu, W., Wang, Y.B., Jiang, Z.T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun. 284(12), 3160–3163 (2011)
Zhang, W.W., Li, D., Li, Y.B.: Quantum private comparison protocol with W states. Int. J. Theor. Phys. 53(5), 1723–1729 (2014)
Lang, Y.-F.: Quantum Private Comparison without Classical Computation. Int. J. Theor. Phys. 59(9), 2984–2992 (2020)
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283(7), 1561–1565 (2010)
Lin, J., Tseng, H.Y., Hwang, T.: Intercept-resend attacks on Chen et al.’s quantum private comparison protocol and the improvements. Opt. Commun. 284(9), 2412–2414 (2011)
Li, Y.B., Wang, T.Y., Chen, H.Y., et al.: Fault-tolerate quantum private comparison based on GHZ states and ECC. Int. J. Theor. Phys. 52(8), 2818–2825 (2013)
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12(2), 1077–1088 (2013)
Xu, G.A., Chen, X.B., Wei, Z.H., Li, M.J., Yang, Y.X.: An efficient protocol for the quantum private comparison of equality with a four-qubit cluster state. Int. J. Quant. Inform. 10(4), 1250045 (2012)
Sun, Z.W., Long, D.Y.: Quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 52(1), 212–218 (2013)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z.: A protocol for the quantum private comparison of equality with χ-type state. Int. J. Theor. Phys. 51(1), 69–77 (2012)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z., Cui, W.: New quantum private comparison protocol usingχ-type state. Int. J. Theor. Phys. 51(6), 1953–1960 (2012)
Lin, S., Guo, G.D., Liu, X.F.: Quantum private comparison of equality with χ-type entangled states. Int. J. Theor. Phys. 52(11), 4185–4194 (2013)
Ye, T.Y., Ji, Z.X.: Two-party quantum private comparison with five-qubit entangled states. Int. J. Theor. Phys. 56(5), 1517–1529 (2017)
Ji, Z.X., Ye, T.Y.: Quantum private comparison of equal information based on highly entangled six-qubit genuine state. Commun. Theor. Phys. 65(6), 711–715 (2016)
Ji, Z.X., Zhang, H.G., Fan, P.R.: Two-party quantum private comparison protocol with maximally entangled seven-qubit state. Mod. Phys. Lett. A 34(28), 1–179 (2019)
Liu, W., Wang, Y.B., Wang, X.M.: Multi-party quantum private comparison protocol using d-dimensional basis states without entanglement swapping. Int. J. Theor. Phys. 53(4), 1085–1091 (2014)
Luo, Q.B., Yang, G.W., She, K., Niu, W.N., Wang, Y.Q.: Multi-party quantum private comparison protocol based on d-dimensional entangled states. Quantum Inf. Process. 13(10), 2343–2352 (2014)
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with n-level entangled states. Quantum Inf. Process. 13(11), 2375–2389 (2014)
Ji, Z.X., Ye, T.Y.: Multi-party quantum private comparison based on the entanglement swapping of d-level Cat states and d-level Bell states. Quantum Inf. Process. 16(7), 177 (2017)
Ye, C.Q., Ye, T.Y.: Multi-party quantum private comparison of size relation with d-level single-particle states. Quantum Inf. Process. 17(10), 252 (2018)
Lang, Y.-F.: Improvement of multi-party quantum private comparison protocol using d-dimensional basis states without entanglement swapping. Int. J. Theor. Phys. 59(9), 2773–2780 (2020)
Chou, W.H., Hwang, T., Gu, J.: Semi-quantum private comparison protocol under an almost-dishonest third party. http://arxiv.org/pdf/quant-ph/160707961.pdf
Lo, H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154–1162 (1997)
Long, G.L., Liu, X.S.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65, 032302 (2002)
Li, C.Y., Zhou, H.Y., Wang, Y., Deng, F.G.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22(5), 1049–1052 (2005)
Li, C.Y., Li, X.H., Deng, F.G., Zhou, P., Liang, Y.J., Zhou, H.Y.: Efficient quantum cryptography network without entanglement and quantum memory. Chin. Phys. Lett. 23(11), 2896–2899 (2006)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Acknowledgements
The author Lang Yan-Feng thanks Daughter Lang Duo-Zi for her support on this work.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lang, YF. Fast Quantum Private Comparison Without Keys and Entanglement. Int J Theor Phys 61, 45 (2022). https://doi.org/10.1007/s10773-022-05033-w
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-05033-w