Abstract
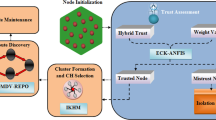
Recently Mobile adhoc networks (MANETs) have received the great attention of researchers as these models provide a wide range of applications. But MANET nodes are prone to various security threats. To overcome this issue, many trust management frameworks have been implemented in the literature. It has been found that the use of machine learning can predict trust values more efficiently. However, machine learning performance suffers from the hyper-parameters tuning and over-fitting issues. Therefore, in this paper, novel trust management is proposed. initially, the Adaptive neuro-fuzzy inference system (ANFIS) is used to train the trust prediction model. Thereafter, a non-dominated sorting genetic algorithm-III (NSGA-III) is used to tune the hyper-parameters of the ANFIS model. Precision, recall, and root mean squared error metrics are used to design a multi-objective fitness function. Optimized link state routing (OLSR) protocol is used for comparative analyses purpose. Three different attacks are applied on the designed network i.e., link spoofing, jellyfish, and gray hole attacks to obtain the dataset. Comparative analysis reveals that the proposed trust evaluation model outperforms the competitive trust evaluation models in terms of various performance metrics such as routing overheads, average end to end latency, packet delivery ratio, and throughput. Thus, the proposed protocol is more secure against various security threats.










Similar content being viewed by others
References
Bhuvaneswari, R., Ramachandran, R.: Denial of service attack solution in OLSR based manet by varying number of fictitious nodes. Clust. Comput. 22(5), 12689–12699 (2019)
Vanitha, K., Rahaman, A.Z.: Preventing malicious packet dropping nodes in manet using IFHM based SAODV routing protocol. Clust. Comput. 22(6), 13453–13461 (2019)
Serhani, A., Naja, N., Jamali, A.: Aq-routing: mobility-, stability-aware adaptive routing protocol for data routing in manet-IoT systems. Clust. Comput. 23(1), 13–27 (2020)
Kandan, J.M., Sabari, A.: Fuzzy hierarchical ant colony optimization routing for weighted cluster in MANET. Clust. Comput. 22(4), 9637–9649 (2019)
Sangeetha, S., Dhaya, R., Kanthavel, R.: Improving performance of cooperative communication in heterogeneous manet environment. Clust. Comput. 22(5), 12389–12395 (2019)
Basavegowda, H.S., Dagnew, G.: Deep learning approach for microarray cancer data classification. CAAI Trans. Intell. Technol. 5(1), 22–33 (2020)
Kumaravel, A., Chandrasekaran, M.: Performance analysis of malicious node detection in manet using ANFIS classification approach. Clust. Comput. 22(6), 13445–13452 (2019)
Ghosh, S., Shivakumara, P., Roy, P., Pal, U., Lu, T.: Graphology based handwritten character analysis for human behaviour identification. CAAI Trans. Intell. Technol. 5(1), 55–65 (2020)
Anand, M., Sasikala, T.: Efficient energy optimization in mobile ad hoc network (MANET) using better-quality AODV protocol. Clust. Comput. 22(5), 12681–12687 (2019)
Wang, R., Yu, H., Wang, G., Zhang, G., Wang, W.: Study on the dynamic and static characteristics of gas static thrust bearing with micro-hole restrictors. Int. J. Hydromechatronics 2(3), 189–202 (2019)
Wiens, T.: Engine speed reduction for hydraulic machinery using predictive algorithms. Int. J. Hydromechatronics 2(1), 16–31 (2019)
Osterland, S., Weber, J.: Analytical analysis of single-stage pressure relief valves. Int. J. Hydromechatronics 2(1), 32–53 (2019)
Gupta, B., Tiwari, M., Lamba, S.S.: Visibility improvement and mass segmentation of mammogram images using quantile separated histogram equalisation with local contrast enhancement. CAAI Trans. Intell. Technol. 4(2), 73–79 (2019)
Xia, H., Jia, Z., Li, X., Ju, L., Sha, E.H.-M.: Trust prediction and trust-based source routing in mobile ad hoc networks. Ad Hoc Netw. 11(7), 2096–2114 (2013)
Tan, S., Li, X., Dong, Q.: Trust based routing mechanism for securing OSLR-based manet. Ad Hoc Netw. 30, 84–98 (2015)
Djedjig, N., Tandjaoui, D., Medjek, F., Romdhani, I.: Trust-aware and cooperative routing protocol for IoT security. J. Inf. Secur. Appl. 52, 102467 (2020)
Gong, W., You, Z., Chen, D., Zhao, X., Gu, M., Lam, K.-Y.: Trust based routing for misbehavior detection in ad hoc networks. J. Netw. 5(5), 551 (2010)
Islabudeen, M., Devi, M.K.: A smart approach for intrusion detection and prevention system in mobile ad hoc networks against security attacks. Wirel. Pers. Commun. 1–32 (2020)
Khanna, N., Sachdeva, M.: Study of trust-based mechanism and its component model in manet: current research state, issues, and future recommendation. Int. J. Commun. Syst. 32(12), e4012 (2019)
Gunasekaran, M., Premalatha, K.: Teap: trust-enhanced anonymous on-demand routing protocol for mobile ad hoc networks. IET Inf. Secur. 7(3), 203–211 (2013)
Xia, H., Jia, Z., Ju, L., Zhu, Y.: Trust management model for mobile ad hoc network based on analytic hierarchy process and fuzzy theory. IET Wirel. Sens. Syst. 1(4), 248–266 (2011)
Fatima, S.K., Fatima, S.G., Sattar, S.A., Srinivasa Rao, D.D.: An independent trust model for manet based on fuzzy logic rules. Int. J. Adv. Res. Eng. Technol. 10(2), 278–289 (2019)
Xu, J., Feng, S., Liang, W., Ke, J., Meng, X., Zhang, R., Shou, D.: An algorithm for determining data forwarding strategy based on recommended trust value in manet. Int. J. Embed. Syst. 12(4), 544–553 (2020)
Manoranjini, J., Chandrasekar, A., Jothi, S.: Improved QoS and avoidance of black hole attacks in manet using trust detection framework. Automatika 60(3), 274–284 (2019)
Sadayan, G., Ramaiah, K.: Enhanced data security in manet using trust-based bayesian statistical model with RSSI by AOMDV. Concurr. Comput. e5397 (2019)
Nguyen, D.Q., Toulgoat, M., Lamont, L.: Impact of trust-based security association and mobility on the delay metric in manet. J. Commun. Netw. 18(1), 105–111 (2016)
Wadhwani, G.K., Khatri, S.K., Mutto, S.: Trust framework for attack resilience in manet using AODV. J. Discret. Math. Sci. Cryptogr. 23(1), 209–220 (2020)
Josephine, J.A., Senthilkumar, S.: Tanimoto support vector regressive linear program boost based node trust evaluation for secure communication in manet. Wirel. Pers. Commun. 1–21 (2020)
Marathe, N., Shinde, S.K.: ITCA, an IDS and trust solution collaborated with ack based approach to mitigate network layer attack on manet routing. Wirel. Pers. Commun. 107(1), 393–416 (2019)
Merlin, R.T., Ravi, R.: Novel trust based energy aware routing mechanism for mitigation of black hole attacks in manet. Wirel. Pers. Commun. 104(4), 1599–1636 (2019)
Kaur, M., Singh, D., Uppal, R.S.: Parallel strength pareto evolutionary algorithm-II based image encryption. IET Image Process. 14(6), 1015–1026 (2019)
Gupta, A., Singh, D., Kaur, M.: An efficient image encryption using non-dominated sorting genetic algorithm-III based 4-d chaotic maps. J. Ambient Intell. Hum. Comput. 11(3), 1309–1324 (2020)
Kaur, M., Singh, D., Kumar, V., Sun, K.: Color image dehazing using gradient channel prior and guided l0 filter. Inf. Sci. 521, 326–342 (2020)
Kaur, M., Singh, D., Sun, K., Rawat, U.: Color image encryption using non-dominated sorting genetic algorithm with local chaotic search based 5d chaotic map. Future Gener. Comput. Syst. 107, 333–350 (2020)
Pragathi, Y.S., Shetty, S.P.: Design and implementation of ANFIS to enhance the performance of secure lar routing protocol in manets
Budyal, V., Manvi, S.S.: ANFIS and agent based bandwidth and delay aware anycast routing in mobile ad hoc networks. J. Netw. Comput. Appl. 39, 140–151 (2014)
Shabut, A.M., Dahal, K.P., Bista, S.K., Awan, I.U.: Recommendation based trust model with an effective defence scheme for manets. IEEE Trans. Mob. Comput. 14(10), 2101–2115 (2014)
Marimuthu, M., Krishnamurthi, I.: Enhanced OLSR for defense against DOS attack in ad hoc networks. J. Commun. Netw. 15(1), 31–37 (2013)
Venkataraman, R., Pushpalatha, M., Rao, T.R.: Regression-based trust model for mobile ad hoc networks. IET Inf. Secur. 6(3), 131–140 (2012)
Li, X., Jia, Z., Zhang, P., Zhang, R., Wang, H.: Trust-based on-demand multipath routing in mobile ad hoc networks. IET Inf. Secur. 4(4), 212–232 (2010)
Zhang, H., Wang, X., Memarmoshrefi, P., Hogrefe, D.: A survey of ant colony optimization based routing protocols for mobile ad hoc networks. IEEE Access 5, 24139–24161 (2017)
Cheng, H., Yang, S.: Genetic algorithms with immigrants schemes for dynamic multicast problems in mobile ad hoc networks. Eng. Appl. Artif. Intell. 23(5), 806–819 (2010)
Yang, S., Cheng, H., Wang, F.: Genetic algorithms with immigrants and memory schemes for dynamic shortest path routing problems in mobile ad hoc networks. IEEE Trans. Syst. Man Cybern. Part C 40(1), 52–63 (2009)
Surendran, S., Prakash, S.: An ACO look-ahead approach to QOS enabled fault-tolerant routing in manets. China Commun. 12(8), 93–110 (2015)
Nandi, B., Barman, S., Paul, S.: Genetic algorithm based optimization of clustering in ad hoc networks, arXiv preprint arXiv:1002.2194
Ali, H., Shahzad, W., Khan, F.A.: Energy-efficient clustering in mobile ad-hoc networks using multi-objective particle swarm optimization. Appl. Soft Comput. 12(7), 1913–1928 (2012)
Kaliappan, M., Augustine, S., Paramasivan, B.: Enhancing energy efficiency and load balancing in mobile ad hoc network using dynamic genetic algorithms. J. Netw. Comput. Appl. 73, 35–43 (2016)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kaur, J., Kaur, S. Novel trust evaluation using NSGA-III based adaptive neuro-fuzzy inference system. Cluster Comput 24, 1781–1792 (2021). https://doi.org/10.1007/s10586-020-03218-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-020-03218-8