Abstract
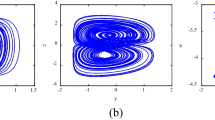
The performance of chaotic systems in generating signals is an essential factor in determining the security of cryptosystems. A new 3D chaotic system is designed based on Hénon and logistic mapping, called 3D Improve-Hénon and Logistic (3D-IHAL), to design a secure and reliable cryptosystem. The attractor phase diagram, Lyapunov exponent, and bifurcation diagram are used to evaluate the performance of 3D-IHAL. NIST tests the randomness of the sequences generated by 3D-IHAL. The results show that 3D-IHAL is suitable for cryptography because of its good dynamic characteristics. In the cryptosystem, the parameters and initial values of 3D-IHAL are generated by the Hash function, and 3D-IHAL generates the key stream required for the encryption phase. In the encryption phase, a hybrid cryptosystem is designed by two different encryption methods, mod and xor, which are used according to the position of the pixel value. Our algorithm is evaluated in public datasets. The evaluation results show that the horizontal, Queryvertical, and diagonal correlations of ciphertext are 0.00012, -0.00089, and -0.00055, respectively, and the information entropy is 7.9992. Compared with the existing algorithms, the proposed algorithm has better security.



















Similar content being viewed by others
Data Availability
All data generated or analysed during this study are included in this published article.
References
Zhou S, Wang X, Zhang Y (2023) Novel image encryption scheme based on chaotic signals with finite-precision error. Inf Sci 621:782–798
Saračević M, Sharma SK, Ahmad K (2022) A novel block encryption method based on Catalan random walks. Multimed Tools Appl 81(25):36667–36684
Saračević M, Adamović S, Maček N et al (2021) Source and channel models for secret-key agreement based on Catalan numbers and the lattice path combinatorial approach. J Inf Sci Eng 37(2):469–482
Wang X, Gao S, Ye X et al (2021) A new image encryption algorithm with cantor diagonal scrambling based on the PUMCML system. Int J Bifurc Chaos 31(01):2150003
Li Q, Wang X, Ma B et al (2021) Concealed attack for robust watermarking based on generative model and perceptual loss. IEEE Trans Circuits Syst Video Technol 32(8):5695–5706
Saračević M, Adamović S, Miškovic V et al (2019) A novel approach to steganography based on the properties of Catalan numbers and Dyck words. Futur Gener Comput Syst 100:186–197
Selimović F, Stanimirović P, Saračević M et al (2020) Authentication based on the image encryption using delaunay triangulation and catalan objects. Acta Polytech Hungarica 17(6):207–224
Liu H, Zhang Y, Kadir A et al (2019) Image encryption using complex hyper chaotic system by injecting impulse into parameters. Appl Math Comput 360:83–93
Gong J (2020) Plaintext recovery attack on 3DES algorithm with different byte keys. J Intell Fuzzy Syst 38(6):7487–7495
Shahbazi K, Ko SB (2020) Area-efficient nano-AES implementation for Internet-of-Things devices. IEEE Trans Very Large Scale Integr Syst 29(1):136–148
Gao S, Wu R, Wang X et al (2023) A 3D model encryption scheme based on a cascaded chaotic system. Signal Process 202:108745
Zheng J, Zeng Q (2022) An image encryption algorithm using a dynamic S-box and chaotic maps. Appl Intell 52(13):15703–15717
Li T, Zhao Q, Wang Y et al (2022) Image sequence encryption based on chaotic fingerprint phase mask and single-shot digital holography. J Opt. https://doi.org/10.1007/s12596-022-01064-y
Elsaid SA, Alotaibi ER, Alsaleh S (2023) A robust hybrid cryptosystem based on DNA and Hyperchaotic for images encryption. Multimed Tools Appl 82(2):1995–2019
Liu P, Wang X, Su Y et al (2023) Globally coupled private image encryption algorithm based on infinite interval spatiotemporal chaotic system. IEEE Trans Circuits Syst I Regul Pap 70(6):2511–2522
Liu P, Wang X, Su Y (2023) Image encryption via complementary embedding algorithm and new spatiotemporal chaotic system. IEEE Trans Circuits Syst Video Technol 33(5):2506–2519
Liu H, Kadir A, Xu C (2020) Cryptanalysis and constructing S-box based on chaotic map and backtracking. Appl Math Comput 376:125153
Neela KL, Kavitha V (2023) Blockchain based Chaotic Deep GAN Encryption scheme for securing medical images in a cloud environment. Appl Intell 53(4):4733–4747
Paul A, Kandar S, Dhara BC (2022) Image encryption using permutation generated by modified Regula-Falsi method. Appl Intell 52(10):10979–10998
Zhou S, Zhao Z, Wang X (2022) Novel chaotic colour image cryptosystem with deep learning. Chaos Solit Fractals 161:112380
Toktas A, Erkan U. 2D fully chaotic map for image encryption constructed through a quadruple-objective optimization via artificial bee colony algorithm. Neural Comput Appl 34 (6):4295–4319
Liu H, Kadir A, Liu J (2019) Color pathological image encryption algorithm using arithmetic over Galois field and coupled hyper chaotic system. Opt Lasers Eng 122:123–133
Erkan U, Toktas A, Toktas F et al (2022) 2D eπ-map for image encryption. Inf Sci 589:770–789
Zhou S, Wang X, Zhang Y et al (2022) A novel image encryption cryptosystem based on true random numbers and chaotic systems. Multimed Syst 28(1):95–112
Chai X, Wu H, Gan Z et al (2021) An efficient approach for encrypting double color images into a visually meaningful cipher image using 2D compressive sensing. Inf Sci 556:305–340
Kumar CM, Vidhya R, Brindha M (2022) An efficient chaos based image encryption algorithm using enhanced thorp shuffle and chaotic convolution function. Appl Intell 52(3):2556–2585
Xie EY, Li C, Yu S et al (2017) On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process 132:150–154
Li C, Lin D, Lü J et al (2018) Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multimed 25(4):46–56
Lazzús JA, Rivera M, López-Caraballo CH (2016) Parameter estimation of Lorenz chaotic system using a hybrid swarm intelligence algorithm. Phys Lett A 380(11–12):1164–1171
Yang F, Mou J, Luo C et al (2019) An improved color image encryption scheme and cryptanalysis based on a hyperchaotic sequence. Phys Scr 94(8):085206
Hua Z, Zhou Y (2016) Image encryption using 2D Logistic-adjusted-Sine map. Inf Sci 339:237–253
Yang F, Mou J, Ma C et al (2020) Dynamic analysis of an improper fractional-order laser chaotic system and its image encryption application. Opt Lasers Eng 129:106031
Erkan U, Toktas A, Lai Q (2023) Design of two dimensional hyperchaotic system through optimization benchmark function. Chaos Soli Fractals 167:113032
Wu R, Gao S, Wang X et al (2022) AEA-NCS: An audio encryption algorithm based on a nested chaotic system. Chaos Solit Fractals 165:112770
Erkan U, Toktas A, Lai Q (2023) 2D hyperchaotic system based on Schaffer function for image encryption. Expert Syst Appl 213:119076
Wang X, Gao S (2019) Application of matrix semi-tensor product in chaotic image encryption. J Franklin Inst 356(18):11638–11667
Wang X, Gao S (2021) A chaotic image encryption algorithm based on a counting system and the semi-tensor product. Multimed Tools Appl 80(7):10301–10322
Chai X, Zhi X, Gan Z et al (2021) Combining improved genetic algorithm and matrix semi-tensor product (STP) in color image encryption. Signal Process 183:108041
Wang X, Su Y, Luo C et al (2022) Color image encryption algorithm based on hyperchaotic system and improved quantum revolving gate. Multimed Tools Appl 81(10):13845–13865
Qobbi Y, Jarjar A, Essaid M et al (2022) Image encryption algorithm based on genetic operations and chaotic DNA encoding. Soft Comput 26(12):5823–5832
Zhang X, Yan X (2021) Adaptive chaotic image encryption algorithm based on RNA and pixel depth. Electronics 10(15):1770
Patel S, Thanikaiselvan V, Pelusi D et al (2021) Colour image encryption based on customized neural network and DNA encoding. Neural Comput Appl 33(21):14533–14550
May RM (1976) Simple mathematical models with very complicated dynamics. Nature 261(5560):459–467
Gallas JAC (1993) Structure of the parameter space of the Hénon map. Phys Rev Lett 70(18):2714
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber J 1(2):31–38
Man Z, Li J, Di X et al (2021) Double image encryption algorithm based on neural network and chaos. Chaos Solit Fractals 152:111318
Gan Z, Chai X, Zhang J et al (2020) An effective image compression–encryption scheme based on compressive sensing (CS) and game of life (GOL). Neural Comput Appl 32:14113–14141
Hua Z, Zhu Z, Chen Y et al (2021) Color image encryption using orthogonal Latin squares and a new 2D chaotic system. Nonlinear Dyn 104:4505–4522
Lin H, Wang C, Cui L et al (2022) Brain-like initial-boosted hyperchaos and application in biomedical image encryption. IEEE Trans Industr Inf 18(12):8839–8850
Njitacke ZT, Isaac SD, Nestor T et al (2021) Window of multistability and its control in a simple 3D Hopfield neural network: application to biomedical image encryption. Neural Comput Appl 33:6733–6752
Yu F, Shen H, Yu Q et al (2023) Privacy Protection of Medical Data Based on Multi-scroll Memristive Hopfield Neural Network. IEEE Trans Netw Sci Eng 10(2):845–858
Gao S, Wu R, Wang X et al (2023) EFR-CSTP: Encryption for face recognition based on the chaos and semi-tensor product theory. Inf Sci 621:766–781
Wang X, Gao S, Yu L et al (2019) Chaotic image encryption algorithm based on bit-combination scrambling in decimal system and dynamic diffusion. IEEE Access 7:103662–103677
Gao S, Wu R, Wang X et al (2023) Asynchronous updating Boolean network encryption algorithm. IEEE Trans Circuits Syst Video Technol 33(8):4388–4400. https://doi.org/10.1109/TCSVT.2023.3237136
Su Y, Xu W, Li T et al (2021) Optical color image encryption based on fingerprint key and phase-shifting digital holography. Opt Lasers Eng 140:106550
Acknowledgements
This research was supported by the National Natural Science Foundation of China (No. 61672190).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gao, S., Liu, S., Wang, X. et al. New image encryption algorithm based on hyperchaotic 3D-IHAL and a hybrid cryptosystem. Appl Intell 53, 27826–27843 (2023). https://doi.org/10.1007/s10489-023-04996-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10489-023-04996-5