Abstract
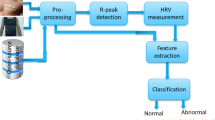
This article uses a machine learning approach to analyze and detect burst signals in a smart healthcare system to protect and safeguard the public health. We consider the time-series electrocardiogram (ECG) waveforms for the detection of burst signals. For this purpose, we propose an intelligent differential correlation burst detection (DCBD) approach by establishing a mathematical model and deriving the analytical expressions to detect false alarm rate and missed detection rate in ECG signals. DCBD feeds the burst signals of a large-scale ECG waveform into various filters for noise removal, which are then passed through data augmentation to achieve high specificity and sensitivity. These waveforms are then segmented for feature extraction and machine learning (ML) classification. Finally, burst-free ECG waveforms are broadcast to a database server, where ML algorithms are used to detect the presence of any abnormal activities. Furthermore, the ECG signal is classified to a set of heart diseases using the well-known LSTM (Long Short-Term Memory) and CNN (Convolutional Neural Network) models. Our proposed approach highlights that the probability of false alarm rate is similar to that caused by pure noise within the ECG waveforms. Our evaluation, using numerical experiments, suggests that the accuracy of the LSTM based ECG signal classification could be approximately 11.7% and 12.8% improved, subsequently, using the proposed burst detection method.

















Similar content being viewed by others
References
Guo F, Wan W, Yu X (2019) Performance analysis of a differential-correlation based burst detection method. Wireless Personal Commun 107(2):1171–1186
Song J, Zhang C, Peng K, Wang J, Pan C, Yang F, Wang J, Yang H, Xue Y, Zhang Y, Yang Z (2018) Key technologies and measurements for DTMB-A system. IEEE Trans Broadcast 65(1):53–64
Khalifa, A.H., Shehata, M.K., Gasser, S.M. and El-Mahallawy, M.S., 2020. Enhanced cooperative behavior and fair spectrum allocation for intelligent IoT devices in cognitive radio networks. Phys Commun, 43, p.101190.
Sodhro AH, Malokani AS, Sodhro GH, Muzammal M, Zongwei L (2020) An adaptive QoS computation for medical data processing in intelligent healthcare applications. Neural Comput Appl 32(3):723–734
Satija U, Ramkumar B, Manikandan MS (2017) Automated ECG noise detection and classification system for unsupervised healthcare monitoring. IEEE J Biomed Health Inform 22(3):722–732
Yu X, Jiang F, Du J, Gong D (2019) A cross-domain collaborative filtering algorithm with expanding user and item features via the latent factor space of auxiliary domains. Pattern Recogn 94:96–109
Yu X, Chu Y, Jiang F, Guo Y, Gong D (2018) SVMs classification based two-side cross domain collaborative filtering by inferring intrinsic user and item features. Knowl Based Syst 141:80–91
Wang H, Jiang H, Gong K (2020) ML-based forward symbol timing offset estimation for burst signals. IEEE Access 8:200875–200882
Yuan-Ling H (2010) Robust burst detection based on the average likelihood ratio test. J Elect Inf Technol 32(2):345–349
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: IEEE symposium on security and privacy (SP'07), Berkeley, pp 321–334.
Chase M (2007) Multi-authority attribute based encryption. Lecture notes in computer science, vol 4392. Springer, Berlin, pp 515–534.
Hur J, Noh DK (2011) Attribute-based access control with efficient revocation in data outsourcing systems. IEEE Trans Parallel Distrib Syst 22(7):1214–1221
Green M, Ateniese G (2007) Identity-based proxy re-encryption. Lecture notes in computer science, vol 4521. Springer, Berlin, pp 288–306.
Mizuno T, Doi H. Secure and efficient IBE-PKE proxy re-encryption. IEICE Trans Fundam Elect Commun Comput Sci, 2011, 94(1):36–44.
Zhao J, Feng DG, Yang L et al (2011) CCA-secure type-based proxy re-encryption without pairings. Acta Elect Sin 39(11):2513–2519
Wu XX, Xu L, Zhang XW (2011) A certificateless proxy re-encryption scheme for cloud-based data sharing. In: The 18th ACM conference on computer and communications security (CCS), pp 869–871.
Liang KT, Liu JK, Wong DS, et al (2014) An efficient cloud-based revocable identity-based proxy re-encryption scheme for public clouds data sharing. In: The 19th European symposium on research in computer security (ESORICS), pp 257–272.
Yang G, Jan MA, Menon VG, Shynu PG, Aimal MM, Alshehri MD (2020) A centralized cluster-based hierarchical approach for green communication in a smart healthcare system. IEEE Access.
Wang C, Wang Q, Ren K, et al (2010) Privacy-preserving public auditing for data storage security in cloud computing. In: The 29th IEEE Infocom, pp 1–9.
Yang K, Jia X (2013) An efficient and secure dynamic auditing protocol for data storage in cloud computing. IEEE Trans Parallel Distrib Syst 24(9):1717–1726
Li N, Li T, Venkatasubramanian S (2007) T-Closeness: privacy beyond k-anonymity and l-diversity. In: The 23rd IEEE international conference on data engineering (ICDE), pp 6–115.
Elkhodr M, Alsinglawi B, Alshehri M (2019) A privacy risk assessment for the internet of things in healthcare. In: Applications of intelligent technologies in healthcare (pp. 47–54). Springer, Cham.
Sandhu RS, Coyne EJ, Feinstein HL et al (2009) Role-based access control models. Ansi Incits 4(3):554–563
Ray I, Kumar M, Yu L (2006) LRBAC: a location-aware role-based access control model. In: The 2nd international conference on information systems security, pp 147–161.
Taha B (2017) Deep learning network for ECG signals classification. The University of Idaho
Acknowledgements
Taif University Researchers Supporting Project number (TURSP-2020/126), Taif University, Taif, Saudi Arabia
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yong, Z., Xiaoming, Z. & Alshehri, M.D. A machine learning-enabled intelligent application for public health and safety. Neural Comput & Applic 35, 14551–14564 (2023). https://doi.org/10.1007/s00521-021-06301-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-021-06301-2