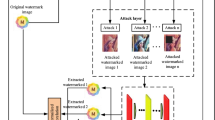
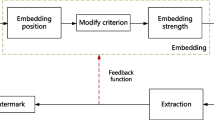
Abstract
Image watermarking embeds information in the image that is visually imperceptible and can be recovered even if the image is modified or attacked during distribution, thus protecting the image copyright. Current image watermarking methods make the learned model resistant to attacks by simulating specific attacks but lack robustness to unspecified attacks. In this paper, we propose to hide the information in the frequency domain. To control the distribution and intensity of watermarking information, we introduce a channel weighting module based on modified Gaussian distribution. In the spatial domain, we design a spatial weighting module to improve the watermarking visual quality. Moreover, a channel attention enhancement module designed in the frequency domain senses the distribution of watermarking information and enhances the frequency domain channel signals to improve the watermarking robustness. Abundant experimental results show that our method guarantees high image visual quality and high watermarking capacity. The generated watermarking images can robustly resist unspecified attacks such as noise, crop, blur, color transform, JPEG compression, and screen-shooting.








Similar content being viewed by others
Data availability
The datasets generated during the current study are available from the corresponding author on reasonable request.
References
Ahmadi, M., Norouzi, A., Karimi, N., Samavi, S., Emami, A.: Redmark: framework for residual diffusion watermarking based on deep networks. Expert Syst. Appl. 146, 113157 (2020)
Baluja, S.: Hiding images in plain sight: deep steganography. In: Advances in Neural Information Processing Systems, vol. 30 (2017)
Barni, M., Bartolini, F., Cappellini, V., Piva, A.: A DCT-domain system for robust image watermarking. Signal Process. 66(3), 357–372 (1998)
Bas, P., Chassery, J.M., Macq, B.: Geometrically invariant watermarking using feature points. IEEE Trans. Image Process. 11(9), 1014–1028 (2002)
Celik, M.U., Sharma, G., Tekalp, A.M., Saber, E.: Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 14(2), 253–266 (2005)
Chang, Q., Huang, L., Liu, S., Liu, H., Yang, T., Wang, Y.: Blind robust video watermarking based on adaptive region selection and channel reference. In: Proceedings of the 30th ACM International Conference on Multimedia, pp. 2344–2350 (2022)
Ding, H., Tao, R., Sun, J., Liu, J., Zhang, F., Jiang, X., Li, J.: A compressed-domain robust video watermarking against recompression attack. IEEE Access 9, 35324–35337 (2021)
Fang, H., Zhang, W., Zhou, H., Cui, H., Yu, N.: Screen-shooting resilient watermarking. IEEE Trans. Inf. Forensics Secur. 14(6), 1403–1418 (2018)
Ganic, E., Eskicioglu, A.M.: Robust DWT-SVD domain image watermarking: embedding data in all frequencies. In: Proceedings of the 2004 Workshop on Multimedia and Security, pp. 166–174 (2004)
Hartung, F., Kutter, M.: Multimedia watermarking techniques. Proc. IEEE 87(7), 1079–1107 (1999)
Hinton, G.E., Osindero, S., Teh, Y.W.: A fast learning algorithm for deep belief nets. Neural Comput. 18(7), 1527–1554 (2006)
Huiskes, M.J., Lew, M.S.: The MIR flickr retrieval evaluation. In: Proceedings of the 1st ACM International Conference on Multimedia Information Retrieval, pp. 39–43 (2008)
Jaderberg, M., Simonyan, K., Zisserman, A., et al.: Spatial transformer networks. In: Advances in Neural Information Processing Systems, vol. 28 (2015)
Jia, J., Gao, Z., Zhu, D., Min, X., Zhai, G., Yang, X.: Learning invisible markers for hidden codes in offline-to-online photography. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 2273–2282 (2022)
Jiang, N., Zhao, N., Wang, L.: LSB based quantum image steganography algorithm. Int. J. Theor. Phys. 55(1), 107–123 (2016)
Jing, J., Deng, X., Xu, M., Wang, J., Guan, Z.: HiNet: deep image hiding by invertible network. In: Proceedings of the IEEE/CVF International Conference on Computer Vision, pp. 4733–4742 (2021)
Khare, P., Srivastava, V.K.: A reliable and secure image watermarking algorithm using homomorphic transform in DWT domain. Multidimens. Syst. Signal Process. 32, 131–160 (2021)
Khayam, S.A.: The discrete cosine transform (DCT): theory and application. Mich. State Univ. 114(1), 31 (2003)
Lee, Y.K., Chen, L.H.: High capacity image steganographic model. IEE Proc. Vis. Image Signal Process. 147(3), 288–294 (2000)
Lin, S.D., Shie, S.C., Guo, J.Y.: Improving the robustness of DCT-based image watermarking against jpeg compression. Comput. Stand. Interfaces 32(1–2), 54–60 (2010)
Poobathy, D., Chezian, R.M.: Edge detection operators: peak signal to noise ratio based comparison. IJ Image Gr. Signal Process. 10, 55–61 (2014)
Shensa, M.J., et al.: The discrete wavelet transform: wedding the a trous and Mallat algorithms. IEEE Trans. Signal Process. 40(10), 2464–2482 (1992)
Stewart, G.W.: On the early history of the singular value decomposition. SIAM Rev. 35(4), 551–566 (1993)
Su, Q., Chen, B.: Robust color image watermarking technique in the spatial domain. Soft Comput. 22, 91–106 (2018)
Tancik, M., Mildenhall, B., Ng, R.: Stegastamp: invisible hyperlinks in physical photographs. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 2117–2126 (2020)
Wallace, G.K.: The jpeg still picture compression standard. Commun. ACM 34(4), 30–44 (1991)
Wang, Z., Bovik, A.C., Sheikh, H.R., Simoncelli, E.P.: Image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13(4), 600–612 (2004)
Woo, S., Park, J., Lee, J.Y., Kweon, I.S.: Cbam: convolutional block attention module. In: Proceedings of the European Conference on Computer Vision (ECCV), pp. 3–19 (2018)
Xu, K., Qin, M., Sun, F., Wang, Y., Chen, Y.K., Ren, F.: Learning in the frequency domain. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 1740–1749 (2020)
Yuan, Z., Liu, D., Zhang, X., Wang, H., Su, Q.: DCT-based color digital image blind watermarking method with variable steps. Multimed. Tools Appl. 79, 30557–30581 (2020)
Zhang, C., Benz, P., Karjauv, A., Sun, G., Kweon, I.S.: Udh: universal deep hiding for steganography, watermarking, and light field messaging. Adv. Neural Inf. Process. Syst. 33, 10223–10234 (2020)
Zhang, R., Isola, P., Efros, A.A., Shechtman, E., Wang, O.: The unreasonable effectiveness of deep features as a perceptual metric. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pp. 586–595 (2018)
Zhu, J., Kaplan, R., Johnson, J., Fei-Fei, L.: Hidden: hiding data with deep networks. In: Proceedings of the European Conference on Computer Vision (ECCV), pp. 657–672 (2018)
Funding
This work was supported in part by the Fundamental Research Funds for the Central Universities (No. 2021ZY86), the Natural Science Foundation of China (NSFC) (No. 61703046) and the open fund of Science and Technology on Complex Electronic System Simulation Laboratory (No. 614201004012102).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
When writing the manuscript, we considered all ethical concerns and followed all guidelines to the best of our ability. The authors declare that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, Z., Wang, H. & Fu, H. A convolutional neural network-based blind robust image watermarking approach exploiting the frequency domain. Vis Comput 39, 3533–3544 (2023). https://doi.org/10.1007/s00371-023-02967-y
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00371-023-02967-y