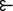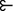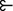Abstract
We prove that pillage games (Jordan in J Econ Theory 131.1:26–44, 2006, “Pillage and property”, JET) can have multiple stable sets, constructing pillage games with up to \(2^{\tfrac{n-1}{3}}\) stable sets, when the number of agents, \(n\), exceeds four. We do so by violating the anonymity axiom common to the existing literature to establish a power dichotomy: for all but a small exceptional set of endowments, powerful agents can overcome all the others; within the exceptional set, the lesser agents can defend their resources. Once the allocations giving powerful agents all resources are included in a candidate stable set, deriving the rest proceeds by considering dominance relations over the finite exceptional sets—reminiscent of stable sets’ derivation in classical cooperative game theory. We also construct a multi-good pillage game with only three agents that also has two stable sets.
Similar content being viewed by others
1 Introduction
Pillage games are cooperative games which allow a coalition’s power to depend on its resources as well as its membership. As cooperative games, they do not require agents to follow any predetermined game form, making them well-suited to the study of power struggles without third party enforcement, in which any proposed game form may itself be contested. Allowing transferrable resources to contributed to both power and value is a similarly appealing extension to standard cooperative games.
Concretely, consider coalition formation problems. Non-cooperative analyses typically specify rules for determining a proposer and a sequence of respondents, which often seem contrived. Standard cooperative analyses, on the other hand, do not recognize that prospective coalition partners may be attractive not just for intrinsic reasons, but for their transferrable holdings. Google, for example, seeking to defend hardware manufacturers using its Android operating system from Apple’s legal attacks, has sold patents to HTC, allowing HTC to—days later—launch its own patent case against Apple (Kwong 2011; Milford and Decker 2011). In international politics, great powers often transfer power—in the form of military aid—to their clients. Such behavior is pervasive and intuitively obvious, but poses problems for the standard analyses mentioned.
Analysis of pillage games has focused on their stable sets: these are both intrinsically interesting, and have been shown to be equivalent to a (farsighted) core in expectation (Jordan 2006). Thus, if the property of being undominated is an appealing one, and if forward looking agents are seen as natural, stable sets are a compelling solution concept. There is evidence that pillage games’ stable sets behave better than those of other cooperative games: they are small, and often unique—in sharp contrast to the famous ‘signature’ example of Shapley (1959) which constructed a game in characteristic function form with an infinite number of stable sets, each potentially infinite.Footnote 1
Both stable sets’ small size and their apparent uniqueness owe to pillage games’ structure: coalitions’ power must satisfy a coalitional monotonicity axiom (larger coalitions, in the sense of set inclusion, are more powerful) as well as weak and strong versions of a resource monotonicity axiom (coalitions whose members have more resources are more powerful).
On size, Jordan (2006) used the strong resource monotonicity axiom to prove that pillage games’ stable sets were finite.Footnote 2 Kerber and Rowat (2011) further exploited the same axiom to tighten Jordan’s bound to a Ramsey number. Saxton (2011) also made use of the coalitional monotonicity axiom to tighten the bound yet further to one that nonetheless remained doubly-exponential. Kerber and Rowat (2014) identified three axioms satisfied by all examples of pillage games previously studied—anonymity (or symmetry), continuity, and responsiveness—and derived a tight bound of 15 allocations for three agent pillage games satisfying these additional axioms.
On uniqueness, Jordan (2006) proved that the wealth is power pillage game—his leading example—had a unique stable set; he did not find examples of multiple stable sets. Kerber and Rowat (2014) proved uniqueness in three agent pillage games satisfying the three additional axioms; a draft of their paper that preceded the present paper’s results (Kerber and Rowat 2009) also conjectured that pillage games’ monotonicity axioms might lead to fine balances of power, such that stable sets either existed uniquely, or did not exist at all.
This paper presents a family of counter-examples to that uniqueness conjecture, each more general than its predecessor. All extend the majority pillage game (or strength in numbers game) analyzed by Jordan and Obadia (2014) and Jordan (2006). In the classic majority game (Lucas 1992), domination only occurs if one coalition has strictly more members than the other. For three agent majority games, there are a continuum of stable sets, each containing a continuum of allocations such that one agent’s resources are held constant; the choice between two allocations within such sets pits one agent against one other, satisfying internal stability. Three agent majority games also have a degenerate stable set containing three allocations, each of which splits the resource equally between two of the agents. By contrast, the majority pillage game breaks ties in coalitional size in favour of the coalition with greater aggregate resource holdings; this additional mode of dominance eliminates the majority game’s continuum stable sets.
The examples presented here extend the majority pillage game by violating the anonymity axiom that grants each agent identical intrinsic strength. Insofar as most empirical applications will not involve intrinsically identical agents, it is clearly important that the theory be developed to handle violations of anonymity.
The present constructions all include one or more powerful agents with a large, fixed intrinsic strength, and many lesser agents with variable—but lower—strengths. Specifically, they all exhibit the following power dichotomy: for all but a handful of exceptional allocations, the powerful agents are more powerful than the lesser agents; however, at those exceptional allocations, the lesser agents just match the powerful agents.
The logic behind these constructions is that stable sets must satisfy both internal stability—harder for large sets—and external stability—harder for small sets. As pillage games’ stable sets are small, the existence of powerful agents with the ability to dominate all but a small number of exceptional allocations overcomes the usual problem with external stability.
Once the allocations sharing the endowment between the powerful agents are included in candidate stable sets, the problem of constructing stable sets reduces to one of assessing stability over the finite exceptional sets. This problem is both straightforward, and reminiscent of classical cooperative analysis (see, for example, Lucas (1971)). Section 3 presents the first counter-example, a four-agent game whose exceptional set is defined to create a cyclical dominance relation among its four elements. Thus, either the even or odd elements of the exceptional set may belong to a stable set, yielding two stable sets. While most of the examples use power functions violating the continuity axiom, we show that this is an expositional aid rather than an intrinsic feature of the examples. Section 3.1 applies the same construction to a pillage game with an empty core.
Section 4 generalizes the initial example by defining an exceptional set for each non-overlapping set of three lesser agents. By creating these to exclude the possibility of dominance across them, stable sets are constructed by independently picking either the even or odd elements from each such exceptional set. Thus, an \(n\)-agent game yields \(2^{\tfrac{n-1}{3}}\) stable sets. Section 5 shows how to introduce dominance relations across exceptional sets, making choices of even or odd elements from one dependent on choices from another. This can arbitrarily reduce the number of stable sets below \(2^{\tfrac{n-1}{3}}\).
Finally, Sect. 6 constructs a multi-good pillage game with two stable sets, but only three agents. Multi-good pillage games (Rowat 2009) add qualitatively to the original single-good pillage game by treating consensual trade in the same framework as non-consensual ‘pillage’. In this richer environment, dominance can be symmetric, allowing construction of two-element exceptional sets for two agents, each element of which dominates the other. In single good pillage games, domination cannot be symmetric (Jordan 2006), making four-element exceptional sets the smallest that can support two stable sets.
The Appendix collects proofs. An earlier version of the paper (MacKenzie et al. 2013) contained more detail at various points.
In conclusion, this paper replaces the conjecture that pillage games have no more than one stable set with new questions. First, do the additional axioms of anonymity, continuity and responsiveness—sufficient for uniqueness with three agents (Kerber and Rowat 2014)—guarantee that larger pillage games also have no more than one stable set? As the constructions presented here rely on violating anonymity, is that condition alone sufficient for uniqueness? Finally, as the present constructions only produce finite numbers of stable sets, are there pillage games capable of producing infinite sets of stable sets?
2 Pillage games
Let \(I = \left\{ 0, \ldots , n-1 \right\} \) be a finite set of agents; when indexed by \(i\), \(j\), and \(k\), these refer to distinct agents. An allocation divides a unit resource among them, so that the feasible set of allocations is a compact, continuous \(n-1\) dimensional simplex:
Let \(\subset \) denote a proper subset, and use \(\subseteq \) to allow the possibility of equality. A power function is defined over subsets of agents and allocations, so that \(\pi : 2^I \times X \rightarrow {\mathbb {R}}\) satisfies:
-
(WC)
if \(C \subset C' \subseteq I\) then \(\pi \left( C', \varvec{x} \right) \ge \pi \left( C, \varvec{x} \right) \forall \varvec{x} \in X\);
-
(WR)
if \(y_i \ge x_i \forall i \in C \subseteq I\) then \(\pi \left( C, \varvec{y} \right) \ge \pi \left( C, \varvec{x} \right) \); and
-
(SR)
if \(\emptyset \ne C \subseteq I\) and \(y_i > x_i \forall i \in C\) then \(\pi \left( C, \varvec{y} \right) > \pi \left( C, \varvec{x} \right) \).
Axiom WC requires weak monotonicity in coalitional inclusion; WR requires weak monotonicity in resources; SR requires strong monotonicity in resources.
A pillage game is then a triple, \(\left( n, X, \pi \right) \).
Kerber and Rowat (2014) noted that all examples of power functions in Jordan (2006) satisfied the following additional axioms:
-
(AN)
if \(\sigma : I \rightarrow I\) is a 1:1 onto function permuting the agent set, then \(i \in C \Leftrightarrow \sigma \left( i \right) \in C'\), and \(x_i = x'_{\sigma \left( i \right) }\) then \(\pi \left( C, \varvec{x} \right) = \pi \left( C', \varvec{x}' \right) \).
-
(CX)
\(\pi \left( C, \varvec{x} \right) \) is continuous in \(\varvec{x}\).
-
(RE)
if \(i \not \in C\) and \(\pi \left( \left\{ i \right\} , \varvec{x} \right) > 0\) then \(\pi \left( C \cup \left\{ i \right\} , \varvec{x} \right) > \pi \left( C, \varvec{x} \right) \).
Axiom AN is an anonymity axiom which means that power does not depend on the identity of agents, merely their cardinality and resources.Footnote 3 Axiom RE is the responsiveness axiom of Jordan (2009): the addition of an agent which has power even as a singleton strictly increases the power of its new coalition. With continuity axiom CX, these ensure that three agent pillage games have no more than one stable set, containing no more than 15 allocations (Kerber and Rowat 2014).
An allocation \(\varvec{y}\) dominates an allocation \(\varvec{x}\), written \(\varvec{y}\)

\(\varvec{x}\), iff
where \(W \equiv \left\{ i \left| y_i > x_i \right. \right\} \) is the win set and \(L \equiv \left\{ i \left| x_i > y_i \right. \right\} \) is the lose set. For \(Y \subseteq X\), let

be the dominion of \(Y\), the set of allocations dominated by an allocation in \(Y\). Similarly, \(U \left( Y \right) = X \backslash D \left( Y \right) \), is the set of allocations undominated by any allocation in \(Y\).
The core, \(K\), is the set of undominated allocations, \(U \left( X \right) = X \backslash D \left( X \right) \).
A set of allocations, \(S \subseteq X\), is a stable set iff it satisfies internal stability,
and external stability,
The conditions combine to yield \(S = X \backslash D \left( S \right) \). While stable sets may not exist, or may be non-unique in general cooperative games, the core necessarily belongs to any stable set; when the core also satisfies external stability, it is the unique stable set.
3 Four agents and two stable sets
This section presents a power function based on the strength in numbers (SIN) power function (Jordan 2006),
This defines a majority pillage game (Jordan and Obadia 2014) in which the larger coalition is always the more powerful, with ties in coalitional size resolved by comparing their aggregate resource holdings. Our version extends the original in two ways. First, it violates anonymity axiom AN by granting the zeroth agent an intrinsic strength much greater than each of the others’. Second, it allows these intrinsic strengths to depend on coalitions and their resource holdings; in particular, it creates a small exceptional set of allocations, outside of which the zeroth agent alone is stronger than the other three together; inside it, however, they can resist the zeroth. This power dichotomy is the key to all of the following examples.
Our power function is therefore:
where \(v_0 \left( C, \varvec{x} \right) = 10\), and
where \(\bar{q} \equiv 3\), \(q\) is bounded by
with \(0 < \delta < \tfrac{1}{6}\), and the exceptional set is
Thus, the upper bound on \(q\) in inequality 3 prevents the three lesser agents overpowering the zeroth, while lower bound ensures that any two weak agents can overpower the third at any \(\varvec{x} \in E\).Footnote 4 \({^,}\) Footnote 5 The \(\delta \) parameter ensures that the three weaker agents have positive endowments in the exceptional allocations, and will therefore resist pillage to \(\varvec{t}^0\); its upper bound ensures that \(q > 0\), whose importance shall be seen below.
The power dichotomy here owes to this inequality:
This will be seen to allow, on the one hand, the powerful zeroth agent to seize the resources of the other three for any non-exceptional allocation while, on the other, never allowing the lesser agents to seize the zeroth agent’s resources.
It may seem that the discontinuity in the three agents’ intrinsic power at the exceptional set risks violating resource monotonicity. This is not the case:
Lemma 1
Equations 1 and 2 define a power function.
Proof
Equation 1 defines a function: the auxiliary conditions partition the domain, and each condition maps onto a single-valued term.
Now demonstrate that function 1 satisfies the three pillage axioms. As, on \(X \backslash E\), the function is the SIN power function, the axioms need only be tested on the exceptional set, \(E\), and across that set and its complement.
-
WC As \(\varvec{x}\) is held constant, only increases in \(C\) to \(C'\) for \(\varvec{x} \in E\) need to be considered. There are three cases to consider:
-
1.
not all \(i \in \left\{ 1, 2, 3 \right\} \) are in \(C\) or in \(C'\). In this case, each agent \(i\) in \(C' \backslash C\) contributes \(x_i + q > 0\) to coalitional power if \(i > 0\) and \(x_i + 10 > 0\) if \(i = 0\). As \(\pi \left( C', \varvec{x} \right) \) is additive across agents, and as the contributions of the agents in \(C\) do not change, the result holds in this case.
-
2.
not all \(i \in \left\{ 1, 2, 3 \right\} \) are in \(C\) but \(\left\{ 1, 2, 3 \right\} = C'\). Now each agent \(i\) in \(C' \backslash C\) contributes \(x_i + \bar{q} > 0\); further, the contributions of those \(i\) in \(C\) are increased from \(x_i + q\) to \(x_i + \bar{q}\). Again, \(\pi \left( C', \varvec{x} \right) > \pi \left( C, \varvec{x} \right) \), consistent with the result.
-
3.
\(\left\{ 1, 2, 3 \right\} \in C\) so that \(C' = I\). As the newcomer, \(i = 0\) adds \(x_0 + 10\), and as the others’ contributions do not change, the axiom is satisfied.
-
1.
-
WR Now there are two cases to consider:
-
1.
\(0 \in C\), which subdivides into:
-
(a)
\(\left\{ 1, 2, 3 \right\} \subseteq C\), which implies that \(y_i \ge x_i \forall i \in I\). By the aggregate endowment constraint, this implies that \(\varvec{y} = \varvec{x}\), for which axiom WR is trivially satisfied.
-
(b)
\(\left\{ 1, 2, 3 \right\} \not \subseteq C\), so that \(v_i \left( C, \varvec{y} \right) = v_i \left( C, \varvec{x} \right) \forall i \in I\), allowing these terms to cancel when calculating \(\pi \left( C, \varvec{y} \right) - \pi \left( C, \varvec{x} \right) = \sum _{i \in C} \left( y_i - x_i \right) \). That \(y_i \ge x_i\) for all \(i \in C\) then upholds the result.
-
(a)
-
2.
\(0 \not \in C\) further subdivides into two non-trivial cases:
-
(a)
\(\left\{ 1, 2, 3 \right\} = C\), which implies that, if \(\varvec{x} \in E\), then \(\varvec{y} = \varvec{x}\): \(\sum _{i \in C} x_i = 1\) for \(\varvec{x} \in E\), and \(y_i \ge x_i\) for all \(i \in C\) with \(\sum _{i \in C} y_i = 1\). Then, for all \(i \in C\), \(v_i \left( C, \varvec{y} \right) = v_i \left( C, \varvec{x} \right) \) so that \(\pi \left( C, \varvec{y} \right) - \pi \left( C, \varvec{x} \right) \) depends only on relative resource holdings, as above.
-
(b)
\(\left\{ 1, 2, 3 \right\} \ne C\), implying that \(\left\{ 1, 2, 3 \right\} \not \subseteq C\) so that for all \(i \in C\), it is again the case that \(v_i \left( C, \varvec{y} \right) = v_i \left( C, \varvec{x} \right) \).
-
(a)
-
1.
-
SR The proof is analogous to that for WR. \(\square \)
Following Jordan (2006), let \(\varvec{t}^i \in X\) be a tyrannical allocation such that \(t^i_i = 1\) and \(t^i_j = 0\). Then:
Lemma 2
For the pillage game defined by Eqs. 1 and 2, the core is \(\left\{ \varvec{t}^0 \right\} \).
Proof
First establish that \(\varvec{t}^0\) belongs to the core:
Second, show that \(\varvec{t}^0\) dominates all allocations, \(\varvec{y}\), in \(X \backslash \left( E \cup \left\{ \varvec{t}^0 \right\} \right) \). Noting that \(\left\{ i \left| t^0_i > y_i \right. \right\} = \left\{ 0 \right\} \) and \(\left\{ i \left| y_i > t^0_i \right. \right\} \subseteq \left\{ 1, 2, 3 \right\} \) we calculate
Third, show that \(\varvec{t}^0\) does not dominate any \(\varvec{z} \in E\):
Finally, for each allocation \(\varvec{z}\) in \(E\), it can be confirmed that there is another, \(\varvec{w} \in E\), such that \(\varvec{w}\)

\(\varvec{z}\). Concretely:

(Consider, for example, \(\varvec{a}\)

\(\varvec{d}\): \(W = \left\{ 2, 3 \right\} \) and \(L = \left\{ 1 \right\} \) as direct implications of \(\delta \in \left( 0, \tfrac{1}{6} \right) \); thus, \(\pi \left( W, \varvec{d} \right) = 2q + \tfrac{1}{2} + \tfrac{1}{2} \delta > q + \tfrac{1}{2} - \tfrac{1}{2} \delta = \pi \left( L, \varvec{d} \right) \).)
Thus, the only undominated allocation is \(\varvec{t}^0\), establishing the result. \(\square \)
As shall be seen, the cores in our examples, when they are non-empty, are small, but have large dominions—precisely the conditions that led Lucas to discover games in characteristic function form that had no stable sets (Lucas 1971). Here, the condition contributes to multiplicity of stable sets.
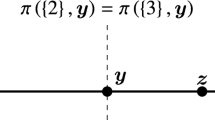
Figure 1 illustrates some of the dominance relations generated by power function 1: arrows flow from dominating to dominated allocations. Their cyclical behaviour is key to the counter-example.
Theorem 1
The pillage game defined by functions 1 and 2 yields exactly two stable sets, \(S_1 \equiv \left\{ \varvec{t}^0, \varvec{a}, \varvec{b} \right\} \), and \(S_2 \equiv \left\{ \varvec{t}^0, \varvec{c}, \varvec{d} \right\} \).
Proof
First confirm that \(S_1\) and \(S_2\) are stable. As established in Lemma 2, \(\varvec{t}^0\) dominates all allocations in \(X \backslash \left( E \cup \left\{ \varvec{t}^0 \right\} \right) \), and no allocations in \(E\). As \(\varvec{a}, \varvec{b}\) are in \(E\), and neither \(\varvec{a}\)

\(\varvec{b}\) nor \(\varvec{b}\)

\(\varvec{a}\) is true, \(S_1\) is internally stable. The cyclical dominance within \(E\) ensures that \(\left\{ \varvec{c}, \varvec{d} \right\} \in D \left( \left\{ \varvec{a}, \varvec{b} \right\} \right) \), establishing external stability. Thus, \(S_1\) is stable. A parallel argument establishes that \(S_2\) is as well.
To prove that there are no other stable sets, denote any stable set of the game by \(S_i\). In any cooperative game, the core belongs to any such stable set. In this case, \(\varvec{t}^0 \in S_i\). As allocations dominated by the core, \(D \left( K \right) \), cannot belong to a stable set, the problem of finding another stable set reduces to that of considering inclusions and exclusions of the allocations in \(E\). As \(\varvec{t}^0\) does not dominate them, the core is not a stable set on its own. By the cyclical dominance, suppose that one other element, \(\varvec{a}\), also belonged to \(S_i\); this is insufficient for external stability as it leaves \(\varvec{b}\) and \(\varvec{c}\) undominated. Adding \(\varvec{b}\) to \(\varvec{a}\) yields \(S_1\), which was already identified; as that satisfies external stability, adding either \(\varvec{c}\) or \(\varvec{d}\) would then violate internal stability. Allocation \(\varvec{c}\) (and supersets containing it) cannot be added to \(\varvec{a}\) without violating internal stability. Finally, attempting to add allocation \(\varvec{d}\) (or supersets) to \(\varvec{a}\) also violates internal stability. Identical reasoning beginning, in turn, with each of \(\varvec{b}, \varvec{c}\) and \(\varvec{d}\) establishes that no further stable sets exist. \(\square \)
All the examples of pillage games studied by Jordan (2006), Jordan and Obadia (2014) and Kerber and Rowat (2014)—including a discontinuous example in Kerber and Rowat (2014)—were such that each allocation, \(\varvec{x}\), generated a dominion, \(D \left( \varvec{x} \right) \), whose components had no holes. In the present example, the core’s dominion has holes at the edge of the simplex—the exceptional set. Once the core is included in a candidate stable set, analysis resembles classical analysis of games in characteristic function form.
The preceding example can be replicated with a continuous power function, and an empty core, isolating violations of the anonymity axiom as the common feature in all of our constructions. Constructing an example in which the power of the lesser agents increases continuously to that of the zeroth agent as the allocations approach the exceptional set merely requires replacing Eq. 2 with
where \(r \left( \varvec{z}, \varvec{x} \right) \equiv \sum _{i \in I} \left| z_i - x_i \right| \) is the rectilinear distance between \(\varvec{x}\) and \(\varvec{z}\), and
where \(q\) and \(\bar{q}\) are as defined on page 7. Worked details can be found in MacKenzie et al. (2013).
3.1 Two stable sets with an empty core
The emptiness or non-emptiness of the core is often linked to other phenomena in cooperative games; however, we now extend the construction above to produce multiple stable sets in pillage games with empty cores.Footnote 6 To do so, triplicate agent 0 to create agents 00 and 000. The exceptional set again has four elements, \(E \equiv \left\{ \varvec{a}, \varvec{b}, \varvec{c}, \varvec{d} \right\} \): for the lesser agents, \(i > 0\), the allocations remain identical to the original ones defined by Eq. 4; the triplicated zeroth agents each receive nothing under the exceptional allocations, \(x_{0} = x_{00} = x_{000} = 0 \forall \varvec{x} \in E\). Finally, modify the membership premium defined in Eq. 2 so that (for this subsection alone) \(\bar{q} = \tfrac{19}{3}\) rather than 3; maintain the upper bound \(q < 3\). Let split allocations, \(\varvec{s}^{i,j}\), divide the resource equally between \(i\) and \(j\), so that \(s^{i,j}_i = s^{i,j}_j = \tfrac{1}{2}\); \(\varvec{s}^{0,00}, \varvec{s}^{0,000}\) and \(\varvec{s}^{00,000}\) shall play the same role as \(\varvec{t}^0\) did in the original example, although they are not core allocations.
Theorem 2
For the six agent pillage game defined by modified Eqs. 4, 2 and original Eq. 1, the core is empty, and the only stable sets are \(S_1 = \left\{ \varvec{s}^{0,00}, \varvec{s}^{0,000}, \varvec{s}^{00,000}, \varvec{a}, \varvec{b} \right\} \) and \(S_2 = \left\{ \varvec{s}^{0,00}, \varvec{s}^{0,000}, \varvec{s}^{00,000}, \varvec{c}, \varvec{d} \right\} \).
The theorem’s proof relies on the following definition and lemma. Denote the set of allocations partitioning the endowment between the zero agents by
The lemma is then:
Lemma 3
If \(\varvec{f}\) is an allocation that belongs to neither the exceptional set, \(E\), nor to the zero simplex, \(Z\), then \(\varvec{f}\) cannot belong to any stable set in the pillage game of Theorem 2.
Proof of Theorem 2
Proposition 2.6 of Jordan (2006) states that a pillage game has an empty core if no agent can defend itself from pillage even when it possesses the entire allocation.Footnote 7 Here, confirming that the strongest agents cannot defend themselves also confirms that the core is empty:
Second, establish internal stability. Dominance within the exceptional set remains as described in expression 6. Thus, an internally stable set may contain only one of \(\left\{ \varvec{a}, \varvec{b} \right\} \) and \(\left\{ \varvec{c}, \varvec{d} \right\} \). By symmetry, it only remains to show that neither \(\varvec{a}\)

\(\varvec{s}^{0,00}\) nor \(\varvec{s}^{0,00}\)

\(\varvec{a}\):
Third, establish external stability. By expression 6, including either \(\left\{ \varvec{a}, \varvec{b} \right\} \) or \(\left\{ \varvec{c}, \varvec{d} \right\} \) ensures that all excluded allocations in \(E\) are dominated by an included one. For allocations outside \(E\), the power of a coalition formed of any two of the zero agents is at least 20. The strongest opposition that they can face has power \(10 + 3 q + 1 < 20\). Any allocation not in \(E\) which does not split the unit endowment between two of the zero agents therefore allows formation of a coalition of two zero agents who stand to benefit by splitting the endowment equally between themselves; such equal splits belong to the proposed stable sets. As, by the previous logic, these two agents can overpower their opposition, external stability holds.
Finally, show that no other stable sets are possible. By Lemma 3, only allocations in \(E \cup Z\) may belong to any stable set. As its proof establishes that no allocation in \(E\) dominates one in \(Z\), ES on \(Z\) must be satisfied using only allocations from \(Z\) itself. As the allocations dominating the rest of \(Z\) must also be internally stable amongst themselves, and as the game played over \(Z\) is a three agent majority pillage game, the result follows directly from Theorem 3.4 of Jordan and Obadia (2014), which proved a unique stable set equal to \(\left\{ \varvec{s}^{12}, \varvec{s}^{23}, \varvec{s}^{13} \right\} \) in the three agent majority pillage game. \(\square \)
The pillage game above is based on a majority pillage game played among the three zero agents, which has \(\left\{ \varvec{s}^{0,00}, \varvec{s}^{0,000}, \varvec{s}^{00,000} \right\} \) as its unique stable set. Adding the three lesser agents thus creates new stable sets containing the original one.
4 Independent exceptional sets: \(2^{\tfrac{n-1}{3}}\) stable sets
This section extends the original construction, defining exceptional sets for each disjoint set of three consecutive lesser agents. As these are designed to ensure that there are no dominance relations across sets, stable sets may be constructed by independently choosing the even or odd allocations in each of these, yielding \(2^{\tfrac{n-1}{3}}\) stable sets when \(n-1\) is a multiple of three.
Define the index \(J = \left\{ 1, \ldots , \tfrac{n-1}{3} \right\} \) so that the family of sets of three consecutive, disjoint agents is \(\left\{ P_j \right\} _{j \in J}\), with \(P_j = \left\{ k, l, m \right\} \), where \(k = 3 (j-1)+1\), \(l = 3 (j-1)+2\) and \(m = 3 (j-1)+3\). The exceptional set belonging to each \(j \in J\) is \(E_j \equiv \left\{ \varvec{a}_j, \varvec{b}_j , \varvec{c}_j, \varvec{d}_j \right\} \subset X\), where
and \(a_{ji}, b_{ji}, c_{ji}, d_{ji} = 0\) for all \(i \not \in P_j\).
As before, Eq. 1 defines the base of the power function. Now generalize the power dichotomy so that—for \(q\) bounded below by the inequality in 3—its upper bound, \(\bar{q}\) and \(v_0 \left( C, \varvec{x} \right) \) are determined by
Again, this allows the zeroth agent to seize all resources other than those in exceptional allocations, while always protecting its own resources from seizure.
The other \(v_i \left( C, \varvec{x} \right) \) are again defined to give the lesser agents less intrinsic power except when allied at their exceptional allocations:
Lemma 1 generalizes as expected:
Lemma 4
Equations 1 and 10 define a power function.
This section’s main result is:
Theorem 3
The \(n\)-agent pillage game defined by Eqs. 1 and 10 yields exactly \(2^{\tfrac{n-1}{3}}\) stable sets, each containing \(\varvec{t}^0\) and exactly one of \(S_{j,1} \equiv \left\{ \varvec{a}_j, \varvec{b}_j \right\} \) or \(S_{j,2} \equiv \left\{ \varvec{c}_j, \varvec{d}_j \right\} \) for each \(j \in J\).
The construction is illustrated for six agents in Fig. 2. Before proving the theorem, we state and prove an auxiliary lemma:
Lemma 5
For all distinct \(E_i\) and \(E_j\), there are no \(\varvec{x} \in E_i\) and \(\varvec{y} \in E_j\) such that \(\varvec{x}\)

\(\varvec{y}\).
Proof of Theorem 3
Internal stability: each individual \(S_{j,1}\) and \(S_{j,2}\) is internally stable by Theorem 1. Lemma 5 proves that the series of such sets defined in the theorem are also internally stable. Finally, to show that \(\varvec{t}^0\) does not dominate any of the exceptional allocations, it suffices to show that
External stability: the core is again \(\left\{ \varvec{t}^0 \right\} \); it dominates all other allocations outside the \(E_j\). As in Theorem 1, the elements in any \(S_{j,1}\) and \(S_{j,2}\) dominate the remaining allocations in the corresponding \(E_j\); as the theorem constructs a set from \(\varvec{t}^0\) and one of these for each \(E_j\), external stability follows.
Finally, show that these are the only possibilities. As already noted, the core belongs to any stable set. This leaves the allocations in the \(E_j\) to be included or excluded. As, by Lemma 5, no allocation in one exceptional set can dominate an allocation in another, each \(\varvec{a}_j\) must either be included, or dominated by an included allocation from \(E_j\), reducing the problem to that in Theorem 1. \(\square \)
5 Dependency: arbitrary numbers of stable sets
Theorem 3 restricted the number of stable sets to a power of two. By violating Lemma 5 to allow dominance across the exceptional sets, choices about inclusion of allocations in one exceptional set become dependent on these choices in other exceptional sets, reducing the possible number of stable sets. This section builds a six agent game with three stable sets to illustrate.Footnote 8
Define the sets \(\tilde{E}_1 = \left\{ \varvec{a}_1, \varvec{b}_1, \varvec{c}_1, \varvec{d}_1 \right\} \) and \(\tilde{E}_2 = \left\{ \varvec{a}_2, \varvec{b}_2, \varvec{c}_2, \varvec{d}_2 \right\} \), where \(0 < \delta < \tfrac{1}{6}, 0 < \alpha < \tfrac{1}{6}\), and
Three parameters therefore define the exceptional sets. As before, \(\delta \) ensures that exceptional allocations are split between three lesser agents. Now, as agent \(i = 1\) receives resources in both \(\tilde{E}_1\) and \(\tilde{E}_2\), it has strict preferences across exceptional sets. The new parameter, \(\alpha \), overturns Lemma 5 to establish dominance relations across the exceptional sets. Its upper bound of \(\tfrac{1}{6}\) reflects the requirement that agent 2 (resp. 3) gain from the transition from \(\varvec{b}_1\) to \(\varvec{d}_1\) (resp. from \(\varvec{a}_1\) to \(\varvec{c}_1\)), as it did previously. Finally, two further bounds are added to \(q\) (in addition to inequality 3), also assisting in establishing dominance relations across exceptional sets:
Otherwise, the power function’s base remains defined by Eq. 1 and \(v_0 \left( C, \varvec{x} \right) \) by Eq. 9. The remaining \(v_i \left( C, \varvec{x} \right) \), for all \(i > 0\), are then expressed symmetrically as
where \(\bar{q}\) is as defined in Eq. 9.
Theorem 4
The six agent pillage game defined by Eqs. 1 and 13 yields exactly three stable sets, \(\left\{ \varvec{t}^0, \varvec{a}_1, \varvec{b}_1, \varvec{a}_2, \varvec{b}_2 \right\} , \left\{ \varvec{t}^0, \varvec{a}_1, \varvec{b}_1, \varvec{c}_2, \varvec{d}_2 \right\} \) and \( \left\{ \varvec{t}^0, \varvec{c}_1, \varvec{d}_1, \varvec{a}_2, \varvec{b}_2 \right\} \).
The proof uses the following lemmas:
Lemma 6
For each \(i \in \left\{ 1, 2 \right\} \), \(\varvec{a}_i\)

\(\varvec{d}_i\)

\(\varvec{b}_i\)

\(\varvec{c}_i\)

\(\varvec{a}_{i}\).
Lemma 7
No allocation in \(\tilde{E}_1\) is dominated by an allocation in \(\tilde{E}_2\).
Lemma 8
Neither \(\varvec{a}_2\) nor \(\varvec{b}_2\) is dominated by an allocation in \(\tilde{E}_1\).
Lemma 9
Neither \(\varvec{c}_2\) nor \(\varvec{d}_2\) is dominated by either \(\varvec{a}_1\) or \(\varvec{b}_1\).
Lemma 10
Across exceptional sets, the following hold: \(\varvec{c}_1\)

\(\varvec{c}_2, \varvec{d}_1\)

\(\varvec{c}_2, \varvec{c}_1\)

\(\varvec{d}_2\) and \(\varvec{d}_1\)

\(\varvec{d}_2\).
Figure 3 depicts the dominance relations established by Lemmas 6 to 10.
Proof of Theorem 4
As before, the core is \(\varvec{t}^0\), which must belong to any stable set. Similarly, by definition of \(v_0 \left( C, \varvec{x} \right) \) and \(\bar{q}\), the remaining set of allocations undominated by it are \(\tilde{E}_1\) and \(\tilde{E}_2\). Thus, any stable set must be the union of \(\varvec{t}^0\) and sets stable on the restriction of the allocation space to \(\tilde{E}_1\) and \(\tilde{E}_2\).
Lemmas 6–10, which establish all dominance relations among and between the members of \(\tilde{E}_1\) and \(\tilde{E}_2\), make the task of finding stable sets on these restricted spaces trivial.
As previously, for each \(i=1,2\), \(\varvec{a}_i\) pairs with \(\varvec{b}_i\) and \(\varvec{c}_i\) with \(\varvec{d}_i\): a stable set including one of a pair but not the other will—by Lemma 6—violate either internal stability or external stability.
First consider including \(\varvec{a}_1\) and \(\varvec{b}_1\), which dominate \(\varvec{c}_1\) and \(\varvec{d}_1\), but do not dominate allocations in \(\tilde{E}_2\). Thus, as before, either \(\left\{ \varvec{a}_2, \varvec{b}_2 \right\} \) or \(\left\{ \varvec{c}_2, \varvec{d}_2 \right\} \) may be added to the candidate stable set, completing it. This produces the theorem’s first two stable sets.
Now include \(\varvec{c}_1\) and \(\varvec{d}_1\) instead. This excludes \(\varvec{c}_2\) and \(\varvec{d}_2\), forcing the inclusion of \(\varvec{a}_2\) and \(\varvec{b}_2\), the theorem’s third stable set.
Finally, no other stable sets are possible: \(\varvec{t}^0\) dominates all allocations outside \(\tilde{E}_1\) and \(\tilde{E}_2\). Within these exceptional sets, \(\varvec{a}_1\) must either be included or excluded, both of which have been considered above. \(\square \)
6 A three agent counter-example with multiple goods
While Jordan noted that domination is asymmetric in the original pillage environment, Rowat (2009) showed that it may be symmetric in a multi-good pillage game. This allows construction of exceptional sets of two allocations, each dominating the other. Economically, the multi-good pillage game allows one to model trade as a form of pillage with an empty lose set, allowing analysis of trade in the absence of externally enforced property rights.
The objects of the single good pillage game generalise naturally to the case of \(m > 1\) goods, each in unitary endowment. The set of allocations becomes
a subset of \({\mathbb {R}}^{mn}\). The allocation of each agent \(i\) is \(\varvec{x}_i = \left( x_{1i}, \ldots , x_{mi} \right) \), where \(0 \le x_{ji} \le 1\) for each \(i\) and \(j\). Allocations of the goods are vectors, \(\varvec{x} =(\varvec{x}_1, \ldots , \varvec{x}_n)\); as inequality no longer provides a complete order, they are compared according to a preference relation, \(\succsim _i\), defined on \({\mathbb {R}}^m_+\); denote strict preference by \(\succ _i\) and indifference by \(\sim _i\).
The axioms defining coalitional power extend naturally to the multi-goods environment, by replacing the original \(\varvec{x} \in {\mathbb {R}}^n\) with \(\varvec{x} \in {\mathbb {R}}^{mn}\). The definition of dominance remains unchanged, but the win and lose sets are now formed on the basis of strict preference rather than strict inequality. Determining whether \(\varvec{x}\)

\(\varvec{y}\) thus requires construction of \(W \equiv \left\{ i \left| \varvec{x}_i \succ _i \varvec{y}_i \right. \right\} \) and \(L \equiv \left\{ i \left| \varvec{y}_i \succ _i \varvec{x}_i \right. \right\} \). The definition of stability is unchanged.
Figure 4 illustrates a two agent counter-example to acyclicity. In it, \(\varvec{a} = \left( \left( \tfrac{19}{20}, \tfrac{7}{25} \right) , \left( \tfrac{1}{20}, \tfrac{18}{25} \right) \right) \) and \(\varvec{b} = \left( \left( \tfrac{1}{20}, \tfrac{18}{25} \right) , \left( \tfrac{19}{20}, \tfrac{7}{25} \right) \right) \), with \(\hat{E} \equiv \left\{ \varvec{a}, \varvec{b} \right\} \) . Agents’ preferences are represented by the utility functions
In the figure, \(\sim _i\) denotes their indifference curves. Their power is described by an extension of the majority pillage game’s power function (Rowat 2009):
and
for \(1 < q < \bar{q} = 3\), maintaining the power dichotomy. The figure indicates the locus of allocations such that \(\pi \left( \left\{ 1 \right\} , \varvec{x} \right) = \pi \left( \left\{ 2 \right\} , \varvec{x} \right) \) by a dashed line.
Thus, \(\varvec{a}_1 \succ _1 \varvec{b}_1\), \(\varvec{b}_2 \succ _2 \varvec{a}_2\), \(\pi \left( \left\{ 1 \right\} , \varvec{b} \right) > \pi \left( \left\{ 2 \right\} , \varvec{b} \right) \) and \(\pi \left( \left\{ 2 \right\} , \varvec{a} \right) > \pi \left( \left\{ 1 \right\} , \varvec{a} \right) \) so that \(\varvec{a}\)

\(\varvec{b}\)

\(\varvec{a}\). This demonstrates symmetry, the minimal example of cyclicity. Intuitively, goods contribute linearly to agents’ power, but non-linearly to utility, creating trade-offs between power and utility.
To form multiple stable sets, add a zeroth agent defined by
These values again maintain the power dichotomy: \(2q + 1 < v_0 \left( C, \varvec{x} \right) = 2 \bar{q} + 1 = 7\), for all \(C \subseteq I\) and \(\varvec{x} \in X\).
Theorem 5
In the three agent, multigood pillage game defined in this section, the core is \(\left\{ \varvec{t}^0 \right\} \), and there are exactly two stable sets, \(\left\{ \varvec{t}^0, \varvec{a} \right\} \) and \(\left\{ \varvec{t}^0, \varvec{b} \right\} \).
Proof
First show that \(\varvec{t}^0\) is undominated:
To show that no other allocation is undominated, we have already eliminated \(\varvec{a}\) and \(\varvec{b}\), which dominate each other. This leaves \(X \backslash \left\{ \varvec{t}^0, \varvec{a}, \varvec{b} \right\} \), all of which are dominated by \(\varvec{t}^0\). Consider \(\varvec{x} \in X \backslash \left\{ \varvec{t}^0, \varvec{a}, \varvec{b} \right\} \) with \(\varvec{x}_1, \varvec{x}_2 \ne 0\). Then:
If either \(\varvec{x}_1\) or \(\varvec{x}_2\) sets either component to zero, \(x_{mi} = 0\), then the coalition opposing the zeroth agent is even weaker.
Finally, we show that the game has the two stable sets stated in the theorem. As before, the core must belong to any stable set. Once \(\varvec{t}^0\) is included, only the two named allocations must be considered. As they dominate each other, both cannot be without violating IS; for the same reason, including either satisfies ES. \(\square \)
7 Discussion
The examples above all violate anonymity axiom AN, allowing powerful agents to dominate all but a small, finite set of allocations even if they initially hold none of the resource. The resulting multiplicity, while unexpected, is practically disappointing: pillage games’ independence of game forms make them appealing for analyses of environments with weak institutions; however, as intrinsic asymmetries between agents are likely to be a feature of empirical work, this paper’s link between violating axiom AN and multiple stable sets suggests that pillage games may not offer as precise predictions as previously hoped. Selten (1987) discussed the interpretation of set-valued solutions in empirical cooperative game theory more generally; Leonard (2010, pp. 244, 260–262) presented early concerns about testable implications of the stable sets. Nevertheless, it remains the case that stable sets of pillage games—when they exist—are finite, and the worst example that we have been able to construct only produces exponentially many stable sets as a function of the number of agents.
The introduction compared the classic majority game in characteristic function form to the majority pillage game, showing that the ability to use resource holdings to break ties arising purely from coalitional membership refined the stable sets of the former. Other games in characteristic function form may be similarly extended when the characteristic function, \(v \left( C \right) \), is superadditive, so that \(v \left( C \cup C' \right) \ge v \left( C \right) + v \left( C' \right) \) for disjoint coalitions \(C\) and \(C'\). Consider the \(n=3\) veto-power or market game in Lucas (1992), in which
To create a pillage game extension, replace the power function in Eq. 1 with
where \(v \left( C \right) \) is defined above, \(\Delta \in \left( 0, \min _{C,C'} \left| v \left( C \right) - v \left( C' \right) \right| \text {s.t.} v \left( C \right) \ne v \left( C' \right) \right) \). Thus, \(\Delta \) ensures that resource holdings only influence dominance when opposing coalitions alone are evenly balanced.
In both the classic market game and its pillage extension, the core is the singleton \(\varvec{t}^2\).Footnote 9 In the classic market game, any continuous curve in the simplex from \(\varvec{t}^2\) to any \(\left( x_1, 0, 1-x_1 \right) \) satisfying the Lipschitz condition
for all \(\varvec{y}\) and \(\varvec{z}\) on the curve is a stable set. In the pillage extension, the unique stable set is \(\left\{ \varvec{t}^2, \varvec{s}^{12}, \varvec{s}^{13}, \varvec{s}^{23}, \varvec{q}^2 \right\} \), where \(\varvec{q}^2 \equiv \left( \tfrac{1}{4}, \tfrac{1}{2}, \tfrac{1}{4} \right) \): \(\varvec{t}^2\) must be included; all \(\varvec{x}\) such that \(x_2 > \tfrac{1}{2}\) are dominated by \(\varvec{t}^2\), so excluded; none of the remaining allocations dominate \(\varvec{s}^{12}, \varvec{s}^{23}\) and \(\varvec{q}^2\), so they must belong to any stable set; the only allocation that remains undominated is \(\varvec{s}^{13}\), which must therefore be included in any stable set.Footnote 10
Thus, while there is a unique stable set in the pillage market game, it is not—unlike that of the introduction’s majority pillage game—a subset of one of the infinitely many stable sets in the market game: in breaking coalitional ties in dominance, the pillage extension introduces dominance into previously internally stable sets, forcing the removal of some such allocations which may have contributed to external stability, forcing—in this example—the inclusion of \(\varvec{s}^{12}\) and \(\varvec{s}^{23}\).
Finally, note that the construction based on the power function in Eq. 1 breaks down as \(n \rightarrow \infty \), as inequality 9 would require \(\bar{q} \rightarrow \infty \) as well. For this to hold for any \(n\) requires something like a power function that sets \(q\) to be a decreasing function of \(n\), with \(\lim _{n \rightarrow \infty } q^n = 0\); this, in turn, disables the requisite dominance among the exceptional allocations in \(E\). Thus, the constructions presented here do not extend to infinite agents, and cannot be used to generate infinite numbers of stable sets.
Notes
Beardon and Rowat (2013) extended the original result to multi-good pillage games, showing that stable sets had measure zero, and bounding their Hausdorff dimension.
Fully expressed, the lower bound is \(2 q + 2 \delta + \tfrac{1}{3} \left( 1 - 3 \delta \right) > q + \delta + \tfrac{2}{3} \left( 1 - 3 \delta \right) \).
While the allocations in \(E\) can be written more simply—e.g. \(\varvec{a} = \left( 0, \delta , \tfrac{2}{3} - \delta , \tfrac{1}{3} \right) \)—the current presentation will be clearer in the more general constructions.
Lucas (1992, p. 586) argued that the stable set became a particularly important solution concept when the core was empty, as the core was generally a good solution concept, and its emptiness often implied the emptiness of related solution concepts. Lucas (1992, p. 552) also noted that the initial focus of von Neumann and Morgenstern (1953) was on constant sum essential games in characteristic function form, all of which have empty cores.
The Bondareva–Shapley theorem provides a parallel result for games in characteristic function form.
See MacKenzie et al. (2013) for the general construction.
For the classic game, see Lucas (1992). For the pillage game, \(\pi \left( \left\{ 2 \right\} , \varvec{t}^2 \right) = \Delta > 0 = \pi \left( \left\{ 1, 3 \right\} , \varvec{t}^2 \right) \); for any \(\varvec{x} \in X\) such that \(x_2 < 1\), \(i=2\) can successfully pillage any agent holding resources by allying itself with the other.
See Kerber and Rowat (2014) for a less condensed version of this sort of reasoning.
References
Aumann RJ (1985) What is game theory trying to accomplish? In: Arrow K, Honkapohja S (eds) Frontiers of economics. Basil Blackwell, Oxford
Beardon AF, Rowat C (2013) Efficient sets are small. J Math Econ 49(5):367–374
Jordan JS (2006) Pillage and property. J Econ Theory 131(1):26–44
Jordan JS (2009) Power and efficiency in production pillage games. Rev Econ Des 13(3):171–193
Jordan JS, Obadia D (2014) Stable sets in majority pillage games. Int J Game Theory 1–14. doi:10.1007/s00182-014-0440-z
Kerber M, Rowat C (2009) Stable sets in three agent pillage games. Working Paper 09–07. University of Birmingham, Department of Economics
Kerber M, Rowat C (2011) A Ramsey bound on stable sets in Jordan pillage games. Int J Game Theory 40(3):461–466
Kerber M, Rowat C (2014) Sufficient conditions for unique stable sets in three agent pillage games. Math Soc Sci 69:69–80
Kwong R (2011) Google helps HTC in patent battle. In: Financial times
Leonard R (2010) von Neumann, Morgenstern and the creation of game theory: from chess to social science, 1900–1960. Cambridge University Press, Cambridge
Lucas WF (1971) Some recent developments in n-person game theory. SIAM Rev 13(4):491–523
Lucas WF (1992) von Neumann–Morgenstern stable sets. In: Aumann RJ, Hart S (eds) Handbook of game theory with economic applications, vol 1. Elsevier, Amsterdam, pp 543–590 Chap. 17
MacKenzie S, Kerber M, Rowat C (2013) Pillage games with multiple stable sets. Discussion Paper 13–07. University of Birmingham, Department of Economics
Milford P, Decker S (2011) HTC sues apple using google patents bought last week as battle escalates. In: Bloomberg
Rowat C (2009) An exchange economy with pillage. mimeo
Saxton D (2011) Strictly monotonicmultidimensional sequences and stable sets in pillage games. J Comb Theory Ser A 118(2):510–524
Selten R (1987) Equity and coalition bargaining in experimental threeperson games. In: Roth AE (ed) Laboratory experiments in economics: six points of view. Cambridge University Press, Cambridge, pp 42–98 Chap. 3
Shapley LS (1959) A solution containing an arbitrary closed component. In: Tucker AW, Luce RD (eds) Contribution to the theory of games. Vol. IV. Annals of Mathematical Studies 40. Princeton University Press, Princeton, pp. 87–93
von Neumann J, Oskar M (1953) Theory of games and economic behavior, 2nd edn. Princeton University Press, Princeton
Acknowledgments
We are grateful to Jim Jordan, the audience at SAET 2013, and two referees for comments, and to the EPSRC for financial support (EP/J007498/1); Rowat thanks Birkbeck for its hospitality.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
Proof of Lemma 3
Proceed by contradiction, assuming that at least one such allocation, \(\varvec{f}\), exists. Each such \(\varvec{f}\) therefore induces an open triangle, \(T \left( \varvec{f} \right) \), on \(Z\) such that each zero agent has strictly more wealth than in \(\varvec{f}\). As allocations in \(T \left( \varvec{f} \right) \) cannot be dominated by \(\varvec{f}\), ES requires either that they belong to a stable set, or that they are dominated by another member of a stable set. As, by Jordan (2006, Theorem 2.9), stable sets are finite, and \(T \left( \varvec{f} \right) \) has positive area, there must exist at least one member of a stable set that individually dominates a positive measure of \(T \left( \varvec{f} \right) \).
We now attempt to find such an allocation. Exceptional allocations, in \(E\), cannot dominate any \(\varvec{z} \in T \left( \varvec{f} \right) \subseteq Z\): the attempt would set \(L = \left\{ 0, 00, 000 \right\} \), and therefore \(\pi \left( L, \varvec{z} \right) = 31 > 19 \ge \pi \left( W, \varvec{z} \right) \). For \(\varvec{x}\) to dominate a \(\varvec{z}\) in \(T \left( \varvec{f} \right) \), \(\varvec{x}\) must belong to \(X \backslash E\). There are only three ways in which such domination may occur:
-
1.
Coalitions in which fewer zero agents belong to \(W\) than do to \(L\). No \(\varvec{x}\) can dominate a \(\varvec{z}\) in this way: as all three lesser agents are collectively less powerful than a single zero agent, \(\varvec{x}\)
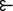
\(\varvec{z}\) in this way requires that \(W\) include more zero agents than \(L\) does.
-
2.
Coalitions in which the same number of zero agents belong to \(W\) and \(L\). As \(\varvec{z}\) is in \(Z\) it shares the resource between the zero agents; for any distinct \(\varvec{x}\), at least one such agent must belong to \(L\); as there are only three zero agents, the coalitions cannot each contain two or more of them. Thus, the two coalitions each contain exactly one zero agent, with the third remaining indifferent. The third agent’s indifference restricts the possible \(\varvec{x}\) that may dominate \(\varvec{z}\) to, at most, lines along \(Z\); a finite number of these cannot cover \(T \left( \varvec{f} \right) \).
-
3.
Coalitions in which more zero agents belong to \(W\) than do to \(L\). As in the previous case, at least one zero agent must belong to \(L\); as there are only three zero agents, it follows that two must belong to \(W\). When this is so, any \(\varvec{x}\) such that \(\varvec{x}\)
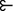
\(\varvec{z}\) implies that \(\varvec{x}\)
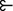
\(\varvec{f}\): the set of zero agents benefiting from a transition from \(\varvec{f}\) to \(\varvec{x}\) contains at least the two benefiting from the \(\varvec{x}\)
\(\varvec{z}\) operation; by definition, as \(\varvec{f} \not \in E\), the two zero agents are able to overcome all other agents. The presence of both \(\varvec{f}\) and \(\varvec{x}\) in a candidate stable set therefore violates IS.
These cases are exhaustive: as \(\varvec{z} \in Z\), any distinct \(\varvec{x}\) ensures that at least one zero agent belongs to \(L\).
To summarize: any \(\varvec{f} \not \in E \cup Z\) belonging to a stable set is dominated by a \(\varvec{z} \in T \left( \varvec{f} \right) \); ES therefore requires the existence of at least one \(\varvec{x}\) in any stable set containing \(\varvec{f}\) that dominates \(\varvec{x}\); the three cases above show that dominating \(T \left( \varvec{f} \right) \), an object of positive measure, therefore requires the support of two of the zero agents; this, in turn, causes \(\varvec{x}\)

\(\varvec{f}\), violating IS. \(\square \)
Proof of Lemma 5
A possible move from \(\varvec{y} \in E_j\) to \(\varvec{x} \in E_i\) generates \(W = P_i\) and \(L = P_j\). Thus, \(\varvec{x}\)

\(\varvec{y}\) is equivalent to
a contradiction. \(\square \)
Proof of Lemma 6
Comparison of any two allocations in \(\tilde{E}_1\) does not allow \(\left\{ 1, 2, 3 \right\} \) to be a subset of either \(W\) or \(L\). Thus, the second clause of Eq. 13 ensures that \(v_i \left( C, \varvec{x} \right) = q\) for any \(\varvec{x} \in \tilde{E}_1\). (Similarly, for \(\tilde{E}_2\), comparison splits agents \(\left\{ 1, 4, 5 \right\} \), so that \(v_i \left( C, \varvec{x} \right) = q\) for any \(\varvec{x} \in \tilde{E}_2\).) Thus, the result is ensured by constraint 3, which ensures that—for any such allocation and coalitions—any two-member coalition is more powerful than any one-member agent. \(\square \)
Proof of Lemma 7
Let \(\varvec{x} \in \tilde{E}_2\) and \(W \equiv \{ i \in I | x_i > c_{1,i} \}\) and \(L \equiv \{ i \in I | x_i < c_{1,i} \}\). Then \(W\) and \(L\) do not depend on the choice of \(\varvec{x}\) as all four possibilities yield the same results: \(W = \left\{ 4, 5 \right\} \) and \(L = \left\{ 1, 2, 3 \right\} \). Therefore to show that \(\varvec{c}_1\) is not dominated by any allocation from \(\tilde{E}_2\), one computes the relevant powers:
which holds as \(q < \bar{q}\). By symmetry, the same argument holds for \(\varvec{d}_1\).
For \(\varvec{a}_1\) and \(\varvec{b}_1\), two cases are identified. First consider \(\varvec{y} \in \left\{ \varvec{c}_2, \varvec{d}_2 \right\} \) so that \(W \equiv \left\{ i \in I \left| y_i > a_{1,i} \right. \right\} \) and \(L \equiv \left\{ i \in I \left| y_i < a_{1,i} \right. \right\} \). This yields \(W = \left\{ 1, 4, 5 \right\} \) and \(L = \left\{ 2, 3 \right\} \), so that
whose inequality is equivalent to constraint 12. Again, symmetry extends the result to \(\varvec{b}_1\).
The second case considers elements \(\varvec{z} \in \left\{ \varvec{a}_2, \varvec{b}_2 \right\} \). Defining \(W\) and \(L\) as above sets \(W = \left\{ 4, 5 \right\} \) and \(L = \left\{ 2, 3 \right\} \). As this case differs from the previous only by removing \(i=1\) from \(W\)—reducing \(\pi \left( W, \varvec{a}_1 \right) \) to \(2q\)—coalitional monotonicity axiom WC guarantees that \(\varvec{a}_1\) is not dominated by any element from \(\tilde{E}_2\). Symmetry again applies the result to \(\varvec{b}_1\). \(\square \)
Proof of Lemma 8
The sections of the proof of Lemma 7 corresponding to allocations \(\varvec{a}_1\) and \(\varvec{b}_1\) establish this result as well if allocations in \(\tilde{E}_1\) are replaced by the corresponding allocations in \(\tilde{E}_2\) and vice versa, and if coalition \(\left\{ 2, 3 \right\} \) is replaced by coalition \(\left\{ 4, 5 \right\} \), and coalition \(\left\{ 1, 4, 5 \right\} \) by coalition \(\left\{ 1, 2, 3 \right\} \). \(\square \)
Proof of Lemma 9
For \(\varvec{c}_2\) or \(\varvec{d}_2\) to be dominated by either \(\varvec{a}_1\) or \(\varvec{b}_1\), coalition \(\left\{ 1, 4, 5 \right\} \) must be weaker in \(\varvec{c}_2\) or \(\varvec{d}_2\) than is coalition \(\left\{ 2, 3 \right\} \). Formally, this requires that
a contradiction as \(\bar{q} > q\). \(\square \)
Proof of Lemma 10
We prove only the first dominance relationship; the rest follow by symmetry. Defining \(W \equiv \left\{ i \in I \left| c_{1,i} > c_{2,i} \right. \right\} \) and \(L \equiv \left\{ i \in I \left| c_{1,i} < c_{2,i} \right. \right\} \) sets \(W = \left\{ 1, 2, 3 \right\} \) and \(L = \left\{ 4, 5 \right\} \). The coalitions’ powers are therefore
where the inequality follows from constraint 11. This is equivalent to \(\varvec{c}_1\)

\(\varvec{c}_2\), the result. \(\square \)
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution License which permits any use, distribution, and reproduction in any medium, provided the original author(s) and the source are credited.
About this article
Cite this article
MacKenzie, S., Kerber, M. & Rowat, C. Pillage games with multiple stable sets. Int J Game Theory 44, 993–1013 (2015). https://doi.org/10.1007/s00182-015-0462-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00182-015-0462-1