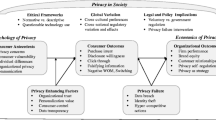
Abstract
Two technological behemoths, the computer and the Internet, have greatly facilitated the ease of collecting, managing, processing, and sharing information about individuals. This has been beneficial in accomplishing some socially and economically valuable objectives such as preventing fraud, tracking illegal behavior, and introducing potential customers to goods and services in which they may be interested. Unfortunately, the unfettered accumulation and analysis of personal data—both knowingly and inadvertently while web browsing online—has also ushered in significant privacy concerns. This thought piece introduces the issue, provides case studies and relevant legislation to underscore its gravity, and presents two rough theoretical models to aid in construing the phenomenon of online privacy. Suggestions for how the interpretive frameworks can be tested are also provided, along with a general call for increased legislation of transactional activity in cyberspace.
Similar content being viewed by others
References
Berman, J. and Mulligan, D. (1999). “Privacy in the Digital Age: Work in Progress,” Nova Law Review, 23 (2), http://www.cdt.org/publications/lawreview/1999nova.shtml
Cable Communications Policy Act of 1984, 47 U.S.C. § 551 (1996)
“Carnivore: FBI Surveillance Software.” (2001). Computer World, Inc., <http://www.computerworld.com/resources/carnivore>.
Clarke, R. (1994). “The Technique of Computer Matching.” Information Technology and People, 7(2): 46–85.
“Communications Assistance for Law Enforcement Act.” (1994). Electronic Privacy Information Center, >http://www.epic.org/privacy/wiretap/calea/calea_law.html>.
Culnan, M.J. and Milberg, S.J. (1999). Consumer Privacy. In M.J. Culnan, R.J. Beis, and M.B. Levy (Eds), Information Privacy: Looking Forward, Looking Back. Washington, D.C.: Georgetown University Press.
“DMV Access.” (1998). Cohn and Marks, Washington, D.C., <http://www.cohnmarks.com/WhatsNews/dmvacces.htm>.
“Echelon watch.” (2001). American Civil Liberties Union, <http://www.echelonwatch.org>.
“Email Encryption Made Simple.”(1999). Information and Privacy Commissioner, Toronto, Ontario, <http://www.ipc.on.ca/english/pubpres/papers/encryp-e.htm>.
“Equifax/Harris Consumer Privacy Survey: Executive Summary.” (1994). Equifax, Inc. and Louis Harris & Associates, <http://www.privacyexchange.org/iss/surveys/eqfx.execsum.1994.html>.
Fair Credit Reporting Act of 1970, 15 U.S.C. § 1681 et seq.
Goldhamer, D. (2004). “Privacy concerns.” SHARE, Boston, MA, 24 July, <http://home.uchicago.edu/~dhgo/privacy-intro/>.
“Graphs and Tables of the Results.” (1999). GVU’s 10th WWW User Survey. Graphics, Visualization, & Usability Center. Georgia Tech Research Corporation, <http://www.gvu.gatech.edu/user_surveys/survey-1998-10/graphs/graphs.html#general>.
Hansell, S. (1998). “Big Web Sites to Track Steps of Their Users.” New York Times, 16 August.
Hirschi, T. (1969). Causes of Delinquency. Berkeley: University of California Press.
Hong, T. (2001). “Freenet: A Distributed Anonymous Information Storage and Retrieval System.” in Designing Privacy Enhancing Technologies: International Workshop on Design Issues in Anonymity and Unobservability, LNCS 2009. Federrath, H. (ed.). New York: Springer.
“How PGP Works.” (1999). Introduction to Cryptography. PGP 6.5.1 documentation. Network Associates, Inc., <http://www.pgpi.org/doc/pgpintro/>.
“Image Data Contracted by Secret Service.” (1999). Cipherwar, 7 December <http://cipherwar.com/news/99/imagedata.htm>.
Information Security and Privacy in Network Environments. (1994). United States Office of Technology Assessment. OTA-TCT-606 (September). Washington, D.C.: U.S. Government Printing Office.
Katz v. United States 389 U.S. 347. (1967). Legal Information Institute. Cornell Law School. 〈http://supct.law.cornell.edu:8080/supct/historic_idx/389_347.htm〉.
Kling, R. (1995). Information Technologies and the Shifting Balance between Privacy and Social Control.” Part VI, Article A of Computerization and Controversy: Value Conflicts and Social Choices, 2nd Ed. San Diego, Academic Press, 〈http://www.slis.indiana.edu/kling/cc/6-CNTR4.html〉.
Kornblum, J. (1997). “AOL to Give Out Phone Numbers.” CNET News.com, 22 July, 〈http://news.cnet.com/news/0-1005-200-320749.html〉.
Laufer, R.S. and Wolfe, M. (1977). “Privacy as a Concept and a Social Issue: A Multidimensional Developmental Theory.” Journal of Social Issues, 33(3): 22–42.
Lessig, L. (1998). “The Architecture of Privacy.” (Draft 2). Taiwan Net '98, Taipei, Taiwan, 〈http://cyber.law.harvard.edu/works/lessig/architecture_priv.pdf〉.
Lind, E.A. and Tyler, T.R. (1988). The Social Psychology of Procedural Justice. New York, NY: Plenum Press.
Lindsay, G. (1999). “The Government Is Reading Your E-Mail.” Infowar.com, LLC, 24 June, 〈http://www.infowar.com/class_1/99/class1_063099b_j.shtml〉.
Martin, J. (2001). “Opting Out or Not: Financial Privacy Forms Criticized for Length, Complexity.” ABCNews.com, 21 June, 〈http://abcnews.go.com/sections/wnt/DailyNews/privacy_notices_010621.html〉.
Mayer-Schonberger, V. (1997). The Internet and Privacy Legislation: Cookies for a Treat? West Virginia Journal of Law and Technology, 1(1).
“Nearly 40 Million Internet Users Connect Via Broadband, Growing 49 Percent.” (2003). Nielsen Net Ratings, 〈http://www.nielsen-netratings.com/news.jsp〉.
Novak, T.P. and Hoffman, D.L. (1999). “Building Consumer Trust in Online Environments: The Case for Information Privacy.” Communications of the ACM, 〈http://www2000.ogsm.vanderbilt.edu/papers/CACM.privacy98/CACM.privacy.htm〉.
Oram, A. (2000). “The Value of Gnutella and Freenet.” Web Review—Cross Training for Web Teams, 12 May, 〈http://www.webreview.com/pi/2000/05_12_00.shtml〉.
Osterhus, T.L. (1997). Pro-Social Consumer Influence Strategies: When and How Do They Work? Journal of Marketing, 61: 16–29.
“Persistent Client State—HTTP Cookies.” (1999). Netscape Corporation, 〈http://home.netscape.com/newsref/std/cookie_spec.html〉.
Poulsen, K. (1999). “Echelon Revealed.” TechTV, LLC, 9 June, 〈http://www.techtv.com/cybercrime/chaostheory/story/0,23008,2120457,00.html〉.
“Privacy and the National Information Infrastructure: Principles for Providing and Using Personal Information.” (1995). Privacy Working Group, Information Policy Committee. Information Infrastructure Task Force, 6 June, 〈http://www.iitf.doc.gov/documents/committee/infopol/niiprivprin_final.html〉.
Quinn, J. B. (2001). “New Privacy Law Gives Consumers ‘Opt Out’ Rights.” The Washington Post Company, 15 May, 〈http://washingtonpost.com/wpsrv/business/longterm/quinn/columns/051501.htm〉.
“Records maintained on individuals.” (2000). U.S. Code, Title 5, Section 552a. The Legal Information Institute. Cornell Law School. 〈http://www.4.law.cornell.edu/uscode/5/552a.html〉.
Right to Financial Privacy Act of 1978, 12 U.S.C. § 3401–34 (1996).
“Secret Service Aided License Photo Database.” (1999). Associated Press, Cable News Network, 18 February, 〈http://www.cnn.com/US/9902/18/license.photos/〉.
Singleton, S. (1999). “Privacy and Human Rights: Comparing the United States to Europe.” CATO Institute, 1 December, 〈http://www.cato.org/pubs/wtpapers/991201paper.html〉.
Sobel, D. (2000). “EPIC Complaint Against DoubleClick Inc.” Electronic Privacy Information Center, 〈http://www.epic.org/privacy/internet/DCLK_complaint.pdf〉.
Steinhardt, B. (2000). “Carnivore Needs to be Caged.” Computerworld, 9 August 〈http://www.computerworld.com/cwi/story/0,1199,NAV47_STO48349,00.html〉.
Stone, M. (2000). “DoubleClick Accused of Double-Dealing Double-Cross.” Newsbytes. E-Commerce Times, 2 February, 〈http://www.ecommercetimes.com/news/articles2000/000202-nb3.shtml〉.
Syverson, P. F., Reed, M. G., and Goldschlag, D. M. (2000). “Onion Routing Access Configurations.” DISCEX 2000: Proceedings of the DARPA Information Survivability Conference and Exposition, Volume I, Hilton Head, SC, IEEE CS Press, 34–40, 〈http://www.onion-router.net/Publications/DISCEX-2000.pdf〉.
Toby, J. (1957). “Social Disorganization and Stake in Conformity: Complementary Factors in the Predatory Behavior of Hoodlums.” Journal of Criminal Law, Criminology, and Police Science, 48, 12–17.
Tribe, L. H. (1991). The Constitution in Cyberspace: Law and Liberty Beyond the Electronic Frontier. Keynote address at the first conference on Computers, Freedom & Privacy.
“Universal Declaration of Human Rights.” (1948). The Office of the High Commissioner for Human Rights. United Nations Department of Public Information, Geneva, Switzerland, 〈http://www.unhchr.ch/udhr/lang/eng.htm〉.
Video Privacy Protection Act of 1988, 18 U.S.C. § 2710.
Wacks, R. (1998). “The Death of Online Privacy?” 13 th Annual BILETA Conference: “The Changing Jurisdiction,” Trinity College, Dublin, 〈http://www.bileta.ac.uk/98papers/wacks.html〉.
Warren, S. and Brandeis, L. (1890). “The Right to Privacy,” Harvard Law Review, 4 (193).
Walton, T. J. (1999). “Internet Privacy Law.” Internet Attorney, 〈http://www.netatty.com/privacy/privacy.html〉.
Whalen, D. (2001). “The Unofficial Cookie FAQ,” Section 1.2, Version 2.53, 〈http://cookiecentral.com/faq〉.
“Where Is Our Data?” (1997). Secure Computing: The Magazine for the Protection of Information, 18–22, August.
Wire and Electronic Communications Interception and Interception of Oral Communications. (2000). U.S. Code, Title 18, Chapter 19. The Legal Information Institute. Cornell Law School. 〈http://www.4.law.cornell.edu/uscode/18/ch119.html〉.
“Yahoo Pulls Phone Search.” (1997). CNET News.com, 3 January, 〈http://news.cnet.com/news/0-1005-200-315556.html〉.
Author information
Authors and Affiliations
Additional information
His research interests include computer crime, corporate security, and criminological theory.
Rights and permissions
About this article
Cite this article
Hinduja, S. Theory and policy in online privacy. Know Techn Pol 17, 38–58 (2004). https://doi.org/10.1007/BF02687075
Issue Date:
DOI: https://doi.org/10.1007/BF02687075