Abstract
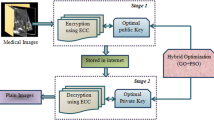
The revolution of IoT systems surpasses daily human facilities for providing financial, mechanical and social aspects. However, the secure transmission of health data over the Internet is a challenging task. Thus, to solve this issue, the proposed study presents the security of medical images in IOT through a new Lightweight Hybrid Encryption (LHE) method with optimization strategies. Initially, the input medical images are encrypted to access the data with higher security through an efficient substitution box (S-box) block cipher and elliptic curves. The proposed encryption scheme assists in minimizing the computational time to several extents by utilizing the Finite Elliptic Curves (FEC) of smaller sizes to generate the S-boxes. Then, a cover image is chosen to hide the information or the confidential images with different pixel sizes. The cover image is partitioned into several non-overlapping blocks. From this, an optimal block is selected by using an adaptive COOT optimization algorithm. After selecting the best block, the cipher image is decomposed and is concealed with the selected block through a Least Significant Bit (LSB) mechanism. Finally, the encrypted medical image data are securely stored in the cloud storage platform through the Internet. The simulation results show that the proposed model obtains better results in terms of security level (97.82%), encryption time (15.4 s), minimum energy consumption (1.33 pJ/bit) and better execution time (18.41 s) related to the data size (bits).








Similar content being viewed by others
Data Availability
Data sharing is not applicable to this article.
References
Arunkumar, S., Vairavasundaram, S., Ravichandran, K. S., & Ravi, L. (2019). RIWT and QR factorization based hybrid robust image steganography using block selection algorithm for IOT devices. Journal of Intelligent and Fuzzy Systems, 36(5), 4265–4276.
Hasan, M. K., Islam, S., Sulaiman, R., Khan, S., Hashim, A. H. A., Habib, S., & Hassan, M. A. (2021). Lightweight encryption technique to enhance medical image security on internet of medical things applications. IEEE Access, 9, 47731–47742.
Hassan, A. (2022). An effective lightweight cryptographic algorithm to secure internet of things devices. In Proceedings of the future technologies conference (FTC) 2021 (vol. 1, pp. 403–419). Springer International Publishing.
Gaurav, A., Psannis, K., & Peraković, D. (2022). Security of cloud-based medical internet of things (miots): A survey. International Journal of Software Science and Computational Intelligence (IJSSCI), 14(1), 1–16.
Abounassar, E. M., El-Kafrawy, P., & Abd El-Latif, A. A. (2022). Security and interoperability issues with internet of things (IoT) in healthcare industry: A survey. Security and Privacy Preserving for IoT and 5G Networks: Techniques, Challenges, and New Directions, 95, 159–189.
Hedayati, R., & Mostafavi, S. (2021). A lightweight image encryption algorithm for secure communications in multimedia internet of things. Wireless Personal Communications. https://doi.org/10.1007/s11277-021-09173-w
Rani, S. S., Alzubi, J. A., Lakshmanaprabu, S. K., Gupta, D., & Manikandan, R. (2020). Optimal users based secure data transmission on the Internet of healthcare things (IoHT) with lightweight block ciphers. Multimedia Tools and Applications, 79(47), 35405–35424.
Lu, Q., Zhu, C., & Deng, X. (2020). An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access, 8, 25664–25678.
Anuradha, M., Jayasankar, T., Prakash, N. B., Sikkandar, M. Y., Hemalakshmi, G. R., Bharatiraja, C., & Britto, A. S. F. (2021). IOT enabled cancer prediction system to enhance the authentication and security using cloud computing. Microprocessors and Microsystems, 80, 103301.
Ullah, A., Azeem, M., Ashraf, H., Alaboudi, A. A., Humayun, M., & Jhanjhi, N. Z. (2021). Secure healthcare data aggregation and transmission in IOT—A survey. IEEE Access, 9, 16849–16865.
Mohiyuddin, A., Javed, A. R., Chakraborty, C., Rizwan, M., Shabbir, M., & Nebhen, J. (2022). Secure cloud storage for medical IoT data using adaptive neuro-fuzzy inference system. International Journal of Fuzzy Systems, 24(2), 1203–1215.
Zaabar, B., Cheikhrouhou, O., Jamil, F., Ammi, M., & Abid, M. (2021). HealthBlock: A secure blockchain-based healthcare data management system. Computer Networks, 200, 108500.
Dutta, A., Misra, C., Barik, R. K., & Mishra, S. (2021). Enhancing mist assisted cloud computing toward secure and scalable architecture for smart healthcare. In G. S. Hura, A. K. Singh, & L. S. Hoe (Eds.), Advances in communication and computational technology (Vol. 668, pp. 1515–1526). Springer.
Selvaraj, S., & Sundaravaradhan, S. (2020). Challenges and opportunities in IOT healthcare systems: A systematic review. SN Applied Sciences, 2(1), 1–8.
Hathaliya, J. J., & Tanwar, S. (2020). An exhaustive survey on security and privacy issues in healthcare 4.0. Computer Communications, 153, 311–335.
Mubarakali, A. (2020). Healthcare services monitoring in cloud using secure and robust healthcare-based BLOCKCHAIN (SRHB) approach. Mobile Networks and Applications, 25(4), 1330–1337.
Rashid, M., Parah, S. A., Wani, A. R., & Gupta, S. K. (2020). Securing E-health IOT data on cloud systems using novel extended role based access control model. In M. Alam, K. A. Shakil, & S. Khan (Eds.), Internet of things (IOT) (pp. 473–489). Cham: Springer.
Sivan, R., & Zukarnain, Z. A. (2021). Security and privacy in cloud-based E-health system. Symmetry, 13(5), 742.
Ayub, M. F., Mahmood, K., Kumari, S., & Sangaiah, A. K. (2021). Lightweight authentication protocol for e-health clouds in IOT-based applications through 5G technology. Digital Communications and Networks, 7(2), 235–244.
Geetha, R., Suntheya, A. K., & Srikanth, G. U. (2020). Cloud integrated IOT enabled sensor network security: Research issues and solutions. Wireless Personal Communications, 113(2), 747–771.
Akhbarifar, S., Javadi, H. H. S., Rahmani, A. M., & Hosseinzadeh, M. (2020). A secure remote health monitoring model for early disease diagnosis in cloud-based IOT environment. Personal and Ubiquitous Computing. https://doi.org/10.1007/s00779-020-01475-3
Atiewi, S., Al-Rahayfeh, A., Almiani, M., Yussof, S., Alfandi, O., Abugabah, A., & Jararweh, Y. (2020). Scalable and secure big data IOT system based on multifactor authentication and lightweight cryptography. IEEE Access, 8, 113498–113511.
Alzahrani, B. A. (2021). Secure and efficient cloud-based IOT authenticated key agreement scheme for e-health wireless sensor networks. Arabian Journal for Science and Engineering, 46(4), 3017–3032.
Sharma, G., & Kalra, S. (2020). Advanced lightweight multifactor remote user authentication scheme for cloud-IOT applications. Journal of Ambient Intelligence and Humanized Computing, 11(4), 1771–1794.
Vedaraj, M., & Ezhumalai, P. (2021). HERDE-MSNB: A predictive security architecture for IOT health cloud system. Journal of Ambient Intelligence and Humanized Computing, 12(7), 7333–7342.
Al-Zubaidie, M., Zhang, Z., & Zhang, J. (2019). RAMHU: A new robust lightweight scheme for mutual users authentication in healthcare applications. Security and Communication Networks, 2019, 1–26.
Sarosh, P., Parah, S. A., & Bhat, G. M. (2022). An efficient image encryption scheme for healthcare applications. Multimedia Tools and Applications, 81(5), 7253–7270.
Das, S., & Namasudra, S. (2022). A novel hybrid encryption method to secure healthcare data in IoT-enabled healthcare infrastructure. Computers and Electrical Engineering, 101(3), 107991.
Funding
No funding is provided for the preparation of manuscript.
Author information
Authors and Affiliations
Contributions
All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
Authors declare that they have no conflict of interest.
Ethical Approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Consent to Participate
All the authors involved have agreed to participate in this submitted article.
Consent to Publish
All the authors involved in this manuscript give full consent for publication of this submitted article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Padma Vijetha Dev, B., Venkata Prasad, K. An Adaptive Lightweight Hybrid Encryption Scheme for Securing the Healthcare Data in Cloud-Assisted Internet of Things. Wireless Pers Commun 130, 2959–2980 (2023). https://doi.org/10.1007/s11277-023-10411-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10411-6