Abstract
Decentralized, open-access blockchain systems opened up new, exciting possibilities—all without reliance on trusted third parties. Regardless of the employed consensus protocol, the overall security, decentralization and effectiveness of such systems, largely depend upon properly structured incentives. Indeed, as has been previously spotted by Babaiaff et al. Bitcoin-like systems, oftentimes lack some of these. Specifically, current blockchain-systems fail to incentivize one of their crucial aspects–the underlying data exchange. As we rationalize, proper incentivization of that layer could lead to lower transactions’ confirmation-times, improved finalization guarantees and at the same time to discouragement of malicious behaviours such as block-withholding attacks. Indeed, incentivization of the data-exchange layer allows the system to remain operational when all agents, including routing nodes, are assumed to be rational. In this work, while focusing on the problem of sybil-proof data exchange, we revisit previous approaches, showcasing their shortcomings and lay forward the first information exchange framework; with integrated routing and reward-function mechanics, provably secure in thwarting Sybil-nodes in 1-connected or eclipsed networks. The framework neither requires nor assumes any kind of constraints in regard to the network’s topology (i.e. the network is modelled as a random-connected graph) and rewards information propagators through a system-intrinsic virtual asset maintained by the decentralized state-machine. The proposal, while being storage and transmission efficient is suitable for rewarding not only consensus-related datagrams (both data-blocks and transactions) but consensus-extrinsic information as well, thus facilitating an universal sybil-proof data-exchange apparatus, provably valid under the assumption of existence of a data store whose property of non-malleability emerges as time approaches infinity. Our research was conducted under two scenarios—with round leader known and unknown in advance of each transactional round.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Recently, cryptographic protocols allowing for a decentralized consensus, opened-up new, exciting possibilities. Their attractiveness does not stem from new performance breakthroughs. On the contrary—they may be orders of magnitudes slower than their centralized counterparts. Still, these protocols exhibit a remarkable quality—namely, their ability to carry out decentralized Turing-complete computations without imposing trust requirements among the involved agents. In such an open, widely deployed eco-systems, when it comes to the topmost State-Domain [1], we may need to trust the majority, but never a single, or easily countable number of system-intrinsic agents.
Indeed, in [1] we proposed a new, exciting family of Open-Blockchain Aided Multi-Agent Cyber-Physical Systems (OBAMA-CPS), highlighting new possibilities, while depicting limitations, shortcomings and laying forward some of the essential guidelines. We highlighted that resilience of incentivized, decentralized data-exchange could be used to aid innovative autonomous environments by focusing on the case the power-industry in [2]. The sole existence of such decentralized systems would not be possible without one utmost important, yet easily overlooked, probably due to its proliferation and ubiquity aspect—the underlying data exchange. In this paper we put our attention towards incentivization of data-exchange throughout decentralized, cryptographically secure decentralized state machines, oftentimes colloquially nicknamed as open-ledger systems or ‘blockchains’. Here, besides analysing the system’s intrinsic, consensus-related data-exchange (data blocks and transactions) we look at how a decentralized state-machine could be used to incentivize propagation of consensus-extrinsic information as well. Indeed, from such a perspective this effectively constitutes the problem of facilitating incentivized data-transmission in any open computer network, under the premise of existence of a decentralized non-volatile data store whose property of non-malleability emerges as time approaches infinity. As we further explain, proper incentivization of data exchange could benefit anyone. Leading to better qualities of the overall decentralized environment.
With that said, the proposed mechanics would need to assure fair assignment of rewards,—imposing verifiability and accountability of the traversed data paths. On top of everything, the solution would need to be sybil-proof. The protocol needs to assure that attempts to cheat the system, by gaining unwarranted rewards, fall short as counterproductive and effectively end up as an exercise in futility. Further, the solution should allow for a feasible implementation and exhibit acceptable transmission and data-storage overheads. Here, nodes are either rewarded or penalized through a virtual, transitive asset—one maintained by the decentralized state-machine. Throughput the paper we will be steadily introducing reader to data-propagation algorithms. These are used for ensuring fair incentivized, Sybil-proof, both system intrinsic (transactions/data blocks) and system-extrinsic data exchange. Each algorithm comes with precise assumptions and a Threat Model. We shall finish by providing the reward assignment function and proving it to be Sybil-proof.
1.1 Rationalization of why ‘sybil-nodes’ are bad
We assume that a legitimate data-path is one which does not include any sybil identities (Fig. 1), thus upholding a one-to-one relationship between an agent and its virtual, logical identity.
In a decentralized environment, requiring routers to be compensated for their efforts demands a decentralized reward-apparatus. Under the premise of agents being driven by profit, it is logical to presume they would be trying to deceive others, especially ones conducting assignment of rewards, into believing in a distorted state of the system—a state which would yield the dishonest—rewards higher than expected from an upright obedience to the protocol. Apparently, rational, yet unfair behaviour could come at the cost of the others—was the reward pool to be finite.
Now, let us imagine the remuneration apparatus to be pretty naïve. Each agent is to obtain a share from a finite reward pool (\({R}_{N}\)) based on its identifier—one added to the message’s (M) endorsement (E) once published. Now, looking at the figure below, suppose the second agent becomes ‘overly’ greedy, and so to receive an unjust extra reward, he injects an additional mischievous identifier into the endorsement (E) accompanying M, resulting in a situation depicted in (Fig. 2).
Now, once M arrives at the agent responsible for assignment of rewards, meaning one capable of affecting the top-most State-Domain [1], the agent looks at the attached endorsement (E) and distributes rewards based on identifiers included within it. With our limited assumptions in mind, by looking at (Fig. 2) it becomes apparent that agent \((\Lambda )\) operating the second router introduced an artificial identity (denoted by  i allowing for collection of an additional reward for identity
i allowing for collection of an additional reward for identity  \(_{{2}^{^{\prime}}}\)—thus effectively collecting rewards for both of the owned identities
\(_{{2}^{^{\prime}}}\)—thus effectively collecting rewards for both of the owned identities  2 and
2 and  \(_{{2}^{^{\prime}}}\). Notice how this wickedly reduced portion of the reward pool available to others (agents owning identities
\(_{{2}^{^{\prime}}}\). Notice how this wickedly reduced portion of the reward pool available to others (agents owning identities  \(_{i}\forall \mathrm{i}\ge 3\)). This simplistic example illustrates precisely why ‘sybil nodes’ are ‘bad’. They induce a distorted, artificial perspective onto the state of the system, without improving network’s connectivity. Such an unjust yet possibly rational misbehaviour of falsifying the world-view as perceived by others, affects both computations and decision making, here resulting in an unfair spread of rewards. One may conclude that this could lead to messages not being delivered at all—shall the remainder of reward-pool dwindle below a certain ‘attractiveness’ threshold as seen by further intermediaries. Now, since we require the protocol to be game-theoretically sound—its operational logic needs to discourage inclusion of unrighteous, artificial identities. Further, we shall require the mechanics to be ‘sybil-proof’ under the general assumption of agents willing to maximize profits.
\(_{i}\forall \mathrm{i}\ge 3\)). This simplistic example illustrates precisely why ‘sybil nodes’ are ‘bad’. They induce a distorted, artificial perspective onto the state of the system, without improving network’s connectivity. Such an unjust yet possibly rational misbehaviour of falsifying the world-view as perceived by others, affects both computations and decision making, here resulting in an unfair spread of rewards. One may conclude that this could lead to messages not being delivered at all—shall the remainder of reward-pool dwindle below a certain ‘attractiveness’ threshold as seen by further intermediaries. Now, since we require the protocol to be game-theoretically sound—its operational logic needs to discourage inclusion of unrighteous, artificial identities. Further, we shall require the mechanics to be ‘sybil-proof’ under the general assumption of agents willing to maximize profits.
1.1.1 Routing (why integrated)
When designing data-exchange protocols for decentralized environments, aiming to maintain the property of sybil-proofness, one needs to recognize whom to reward and/or whom to penalize. Let us notice that in game theoretical terms, propagation of information constitutes work (at least covering energy losses) performed by intermediary agents, i.e. routers. Thus, under our assumptions, without rewards of any kind, the rational decision for autonomous, independent agents would be not to propagate information at all. On the contrary, if we do decide to reward propagators, then from the perspective of intermediaries—the rational decision would be to attempt to trick the system into receiving additional, ‘unjust’ rewards.
Rewarding intermediaries stands in need for a path assurance apparatus. It needs to enable for non-malleable sequences of nodes’ identifiers. We require these embodiments of identities—of those who took part in data-exchange to be delivered to agent(s) responsible for assignment and distribution of rewards. Typically, this means agents operating the consensus layer, thus capable of affecting the top-most State-Domain [1]. Understandably, this leads to a tight coupling between reward-issuance and data-routing/propagation components. Data-propagation may need to account for delicate, game-theoretical assumptions associated with the transmitted information. Once we consider game-theoretical nature of the transmitted information itself—things become even more interesting.
Now, let us wonder—in whose intention would it be for the information to be delivered? Is the information useful for the intermediaries themselves? Does the information have a specific destination? Is the information routable? For an agent issuing a crypto-currency transaction it might be desirable to have it delivered to another agent who could affect the top-most State Domain, since it might be unlikely for the former to have the transaction confirmed and included within the decentralized storage all by himself. In systems relying on Proof-of-Work, this might be due to his limited computational capabilities. Such a client would need to incentivize others to distribute the transaction further across the network in hope for it to come about a round-leader who confirms it. Routers want to be paid. Nodes operating the top-most state-domain want to be paid as well. The round-leader may not be known in advance. Notice that knowledge of the round-leader’s identity/location could be used to optimize transactions’ propagation and transform it away from a gossip-like dissemination, towards a more efficient routing protocol. In our work, we abstract away from the notion of ‘cryptocurrency transactions’ and portrait these as authenticated data-structures describing and instructing for a transition of the decentralized state-machine into a new state, thus affecting at least one of its internal variables.
1.1.2 Eclipsed networks
A situation might arise when a data-path turns out to be the only one between sender and recipient. We call this an eclipsed communication link or a one-connected network. We require a game-theoretically compatible discouragement of agents, including additional Sybil identities, also in such a scenario. The requirement not met by previous works, which fall short in achieving this for networks of an arbitrary topology.
1.1.3 The nature of information
Once agents are assumed as rational, everything is about the incentives. What could be portrait as a generalized problem of incentivized data-exchange, in reality might require specialized game-theoretical treatment, depending on the accompanying game-theoretical nature of the exchanged information itself. Addressed or not by the protocol’s designers, it would surely be considered and exploited by intermediaries, shall it affect their expected returns. Abstracting away from computer systems and allowing ourselves for a sloppy anecdote,—undeniably transport of gold might evoke other passions than transport of fertilizers. Similarly, stepping aside from the problematics of transactions’ deliveries let us consider distribution of already mined and confirmed data-blocks. Is there anyone in whose intention would it be to have the transaction delivered? Could the reward and data-propagation rules be structured differently so to better accommodate the actual game-theoretical circumstances? For this, we might consider whether the transmitted information would be of use to anyone. Is it a precious secret? Would possession of the information improve one’s situation? Indeed, an entity taking part as a data-router, capable of extending upon the accountable history of events, building upon the current state of the decentralized state-machine, may indeed want to get to know the propagated data-block so to extend upon it. Once it succeeds in ‘confirming’ the received block (the just acquired information), it may receive a reward (as seen fit by the ‘consensus’ mechanics i.e. the majority of peers participating in voting-such would be the case in the majority of current ‘blockchain’ systems).
When deciding whether to retransmit, the agent would first assess its probability of winning. The sources of data-blocks i.e. successful round leaders, may want to have the data-blocks propagated across the network so as to have their confirmation-rewards acknowledged by others. Here, when designing propagation rewards, we might not require data sources to be rewarding intermediaries explicitly. Instead, we might make routers receive fractions of block confirmation rewards coming from new blocks—ones extending those they helped to deliver. Notice the ubiquitous accountability requirements. Now, going beyond the internals, towards system extrinsic data propagation—a love letter from Bob to Alice may not need to affect the decentralized consensus, thus for it to arrive at a round-leader is needless. Still, for it to reach Alice, Bob may need to assure its delivery by properly motivating autonomous, independent, profit-driven propagators, and these propagators need to be assured that the reward mechanics are fool proof and fair.
Apparently, a close-cooperation or even integration of reward-assignment and routing algorithms is conspicuous. Data-paths need to be temper-proof and undeniable. A mechanism meeting the just mentioned requirements had been already proposed in [3]—the idea was for each node (Ni) on a data-path, starting from source—the current leader, to be adding identifiers of consecutive intermediaries (Ni+1) to the endorsement (E) of the propagated data-block in an undeniable and temper-proof manner. This was achieved by making identifier of Ni+1 signed by Ni—and since the identifier of the first intermediary was included within the block itself, this rendered the data-block inseparable from the legitimate sequence on intermediaries. Each time this required Ni to get to known the identifier of Ni+1 first. Any consecutive agent willing to extend upon the received data-block was literally forced to work upon the endorsed version of it and thus the reward function executed by round leader could account for all of the intermediaries leading to it. Another approach to path assurance was introduced in [4]. There, each node added itself to an onion-like data-structure, with each layer encrypted during data retransmission with a secret at its centre circumventing separation of the endorsement from the transmitted information. Yet another approach [5] relied upon hashing together consecutive nodes’ identifiers, resulting in lower transmission overheads compared to ‘chained-identifiers’ solutions.
In a system where agents are rationale, introduction of an additional incentive might affect existing ones. The problem of a block-withholding attack has been well studied and known across the literature [6]. If we provide round-leaders with an additional, explicit encouragement for retransmission of newly minted data-blocks—the expected benefits from conducting an attack could dwindle, making others waste fewer resources (time, computational power, opportunities etc.). Now, while data-propagation rewards are welcome by those who propagate, they require someone willing to cover the costs. Were we to reward intermediaries ‘out of thin air’, then even equipped with a sybil-proof data-transmission apparatus, we would still be encouraging agents to exchange dummy datagrams. It may work for proof-of-work authenticated data-blocks (as often is the case) as every agent’s production capacity is capped by his computational power and thus by the laws of physics, but not for ‘transactions’ whose production is not computationally bound in a significant manner. On the upside, were we to make sender responsible for rewarding of propagation of these, there would be no retransmission were no rewards assured for intermediaries; consequently leading to dramatically lowered network’s susceptibility to spam and/or denial-of-service attacks.
The presumption of agents being driven by profits could be infamously considered as ‘selfish’ and supposedly as leading to deprivation of open community ‘spirits’. Still, the free markets’ approach has been widely proclaimed as the actual basis of any healthy economy [7, 8]. Relationships based on mutual benefits have been vastly observed across nature [9,10,11,12]. Still, leaving aside far-fetched, implicit reasoning and rationalizations—in the current decentralized state-machines’ implementations, there is no tangible incentive for transactions and/or data-blocks to be retransmitted across the network. Let alone for an incentive for current leaders to provide new nodes with older data-blocks so they could re-validate entire history of events leading to the current state—the process which truly adds to the overall security of any open, decentralized state machine. If strength of the system was to rely upon individual decisions, there would be little to no benefit from a myriad of nodes blindly following a few. We as humans currently are used to paying centralized entities for data deliveries—often sacrificing our freedom and privacy.
2 Related work
The problem of motivating data-exchange within blockchain-environments is not new and to the best of our knowledge was spotted first in [13] by Babaiaff et al. Traditional defences against Sybil attacks rely on validated identities issued by a trusted authority. Recently an exciting research paper [14] tackled the problematics of Sybil-proofness in a slightly different context (social networks based on Transitive Trust [15] upon which [14] is based—not decentralized state-machines with global convergence to same state across all of the nodes). The paper made it also into the comparative table below, still probably due to the mentioned differences authors did not compare their approach with any of the other major works referenced here-in; it is worth to notice that [14] requires agents to trust that others present honest timestamps: “(..)The only necessity is that something induces an order on the set of interactions of each agent(..)”. Recently, also there was a very interesting work [16] tackling the problematics of Sybil-proofness, however in an entirely different context (CTI systems). Their work showed how a virtual asset itself could be used to minimize Sybil-incentives within an external system—such as falsified data-uploads to a CTI system, by introducing costs of doing so.
In previous works, because of reasons which have been discussed, often, the routing mechanism, the reward function and the blockchain architecture itself were tightly coupled to maintain both the game-theoretical and security assumptions. That is also true in our work. For instance, the property of the routing mechanisms assuring identifiers of the neighbouring nodes and the investments made by them to be blinded—is required to uphold game-theoretical properties leading to high-finalization guaranties. A simplified high-level comparison, of previous approaches towards blockchain related incentivized data-exchange, in respect to a few of their most important properties, is presented in (Table 1), below:
Please do notice that the novelty in Spide, as seen from the table above is that only it ascertains Sybil-proofness in one-connected and/or eclipsed networks. Also, it is the only one to assure such property when there are no constraints on the network’s topology i.e. when the network is modelled as a random d-regular graph.
Looking at the above, Moshe Babaioff et al. were the first to spot Bitcoin’s [17] lack of incentives for transactions’ propagation and proposed a reward scheme. They proved the effectiveness of it in a rather constrained model in which the peer-to-peer network was assumed to constitute a regular d-ary tree of height H. They did not discuss how to enforce the proposed reward division. Their scheme imposes high reward overheads. If a transaction gives one unit of fee to its successful miner, up to log(H) units of rewards have to be given to propagators [3]. Respectfully, there are three additional works by Oguzhan Ersoy et al. [5, 18, 19], where [5] and [18] provide treatment for transaction propagation, while assuming no topology constraints. To be sybil-proof their proposal requires statistical information to be available throughout the network. Both proposals are valid for a specific blockchain architecture where leader is known first before transaction dissemination begins. In [19] the design is detached from the previously employed leader-first-then-block modus operandi and it is proposed to reward propagation of ‘transaction sets’ through introduction of ‘transaction-collectors’, effectively proposing a new overall architecture.
3 Our contributions
3.1 Contribution statement
Herein, we lay forward an innovative and comprehensive sybil-proof data exchange incentivization framework. The framework covers multiple blockchain architectures, comes with integrated routing and path- assurance mechanics and provides a compatible sybil-proof reward assignment function. Overall, the contributed algorithms ascertain sybil-proof, incentivized propagation of information relevant for intrinsic mechanics of an open, decentralized state-machine (blocks and transactions) but uphold the same for propagation of system-extrinsic, arbitrary information as well. The framework is valid for both ‘Nakamoto’ and = ‘leader-known-first’ consensus-protocols. Previous works did not assure sybil-proofness in 1-connected or eclipsed networks while, in some cases, providing valid under their respective assumptions impossibility theorem [5, 13]. Here, by assuming reliance on even stronger assumptions and incorporating yet another degree of freedom—an unprecedented in this context concept of reliance on system-intrinsic investments, we propose the first protocol, provably effective in thwarting Sybil nodes in 1-connected or eclipsed networks.
3.2 High-level view
Before we head towards depicting details of our contributions, let us give a brief, high-level outlook on how the mechanics are structured. Here, we assume existence of a system intrinsic virtual asset, represented as a variable in the domain of unsigned natural numbers, assigned to every State-Domain [1], with values under a limited control (cannot be arbitrarily incremented) by agents owning the former; with modification rights (ex. ‘value transfer’ operation) under full provisioning of nodes maintaining consensus at the particular level of the State-Domains’ hierarchy tree at which these domains are located. Value-transfers are initiated directly or indirectly (through autonomous code maintained within State-Domains) by agents after providing appropriate authentication to the decentralized consensus. The consensus, as long as it is reached, can cause arbitrary operations on any of the domains’ variables (including reward assignment/penalties). Indeed, such a definition is compatible with what is widely known as a ‘cryptocurrency’. Agents capable of voting and of over-watching consensus decisions can uprightly be deemed as guardians of a certain kind of a monetary-policy [20].
First off, all agents start of as being equal. There are no external points of trust. We separate the notion of agents from the owned by them identities, allowing for their one-to-many relationship to be depicted within equations. All agents are assumed to be taking part in a game. The aim of the game is to maximize profits. Agents are assumed as rationale and thus driven by profits. The game theoretical and technical properties of algorithms to follow were designed to thwart and discourage,—through game rules—when technical mitigation was impossible due to openness of the system,—protocol-compatible yet assumed as unfair actions—such as issuance of unfair rewards.
Second, we make each identity owned by an agent require an initial investment made in system-intrinsic cryptocurrency. Identities of intermediaries are being added into the endorsement of a transmitted information as it traverses the network. Identity on behalf of which a bigger investment is made is expected to gain higher cumulative reward from participation in random game-rounds,—compared to an identity with a lower associated initial investment value. Similarly, to discourage possession of multiple-identities, investment made on behalf of a single identity should yield higher expected cumulative reward than the same amount of investment spread across multiple identities. Thus, inclusion of an identity into a data-path entails cost, whereas agents hope for profit. Rewards and losses are calculated based on initial investment-values associated with identities encountered within a data path. Calculation and assignment of rewards is carried out by nodes maintaining the consensus. Identities encountered on a data-path, with highest and lowest investment values receive highest and lowest rewards respectfully. In order to maintain high-finalization guarantees, data-routing agents should not be able pin-point and participate only in selected game-rounds with identity dealings deemed as favourable. To assure that, we design the game to reassemble a random blinded lottery [21]. Round-leader is rewarded for choosing shortest path to save up on data storage of endorsements within the decentralized data-store. This stays in contrast with other works, where choosing of the shortest data-path was used to guarantee sybil-proofness, yet, such approach and treatment did not allow for sybil-proofness in one-connected and/or eclipsed networks, as per impossibility theorem presented in [18]—valid under their limited assumptions.
According to previous works in 1-connected networks:

N3 should keep including Sybil-identities as depicted in figure below, with Sybil-identities denoted in red (Fig. 3).
Where Ni \(\epsilon\)
 \(_{S}\forall i>3\le {k}_{max-1};\) where
\(_{S}\forall i>3\le {k}_{max-1};\) where  \(_{S}\) is the set of Sybil identities.
\(_{S}\) is the set of Sybil identities.
Now, in previous protocols when assigning rewards based on sequences of encountered identities [5, 13], N3 would continue as long as it believed to be taking part within the shortest data-path, a path whose length does not exceed kmax, which is a maximum acceptable (by the consensus) data-path length.
Conversely, in protocols [3] where agents have the ability of making on-the-spot (when re-propagating), arbitrary reservations of chosen fractions of the reward-pool before handing information over to neighbours—N3 might say (Fig. 4).
That’s entirely possible in [3]
Further notice that, in previous works, N3 would be rewarded only if the re-transmitted information reached a full node, as the algorithms were analysed only for propagation of system-intrinsic transactions and/or data blocks. Now, as time was of the essence,- since the shortest path and only it was rewarded, N3 would have to use his knowledge of the network’s topology before including a sybil-identity hoping to receive additional ‘unjust’ rewards with a satisfactory probability. It is worthwhile to note that reserving arbitrary high fractions of the reward pool might had resulted in information not being delivered at all. Our proposal is immune to this type of attacks since it handles 1-connected/eclipsed networks with ease. Here, rewards are assigned solely based on the data-paths’ lengths and  values,—meaning investment-values, made in the name of Ni encountered within endorsement E (∀Ni ∈ E). Going back to our previous example, in this work the only way for an agent to increase its expected reward would be to forward more information using identity N3 or to create another identity N3′ whose
values,—meaning investment-values, made in the name of Ni encountered within endorsement E (∀Ni ∈ E). Going back to our previous example, in this work the only way for an agent to increase its expected reward would be to forward more information using identity N3 or to create another identity N3′ whose  I value would be greater
I value would be greater  . Thus, it is always best to have higher
. Thus, it is always best to have higher  as it increases the probability of dominating any encountered identity. As per our to be introduced reward-assignment function (Sect. 6), when having an A priori choice on how to spread investment capital among identities, using two or more identities (ex. N3 and N3′) in the same data-path would yield lower cumulative reward than using a just a single identity N3′′ whose
as it increases the probability of dominating any encountered identity. As per our to be introduced reward-assignment function (Sect. 6), when having an A priori choice on how to spread investment capital among identities, using two or more identities (ex. N3 and N3′) in the same data-path would yield lower cumulative reward than using a just a single identity N3′′ whose  . Thus it is always better to have a single identity within a single data path, one with highest
. Thus it is always better to have a single identity within a single data path, one with highest  I value one can afford over a portfolio of multiple.
I value one can afford over a portfolio of multiple.
The value of  lowers with each retransmission (by Г) ∀N—facilitating kind of a blind lottery-participation fee. It is assumed that
lowers with each retransmission (by Г) ∀N—facilitating kind of a blind lottery-participation fee. It is assumed that  I ≫ reward from participation in any single data retransmission.
I ≫ reward from participation in any single data retransmission.
After considering the presumable innocence of the problem of incentive-compatible data exchange, it quickly turns out that a concrete protocol design might be far from obvious as some imminent problems arise, namely:
-
How to make the protocol universal enough to handle both intrinsic and extrinsic data exchange? How to reward propagation of transactions /and/or bundles of these (i.e. blocks) but also of information extrinsic to the decentralized state-machine’s ex. internet traffic?
-
How to incentivize agents to invest into a single identity instead of multiple in order to discourage playing multiple hands at the same time (Sybil-nodes)?
-
How to disincentivize agents from picking and participating only in favourable dealings (in order to maintain high finalization guaranties)?
-
How to design a compatible routing scheme?
-
How to carry on with propagation of system-extrinsic information with temporary lack of access to nodes maintaining the consensus?
-
And last but not least,—how to make the potential solution storage and transmission efficient1 at high data rates (especially important for system-extrinsic data propagation)
4 Problem statement
Let us formulate the problem as: “How to facilitate incentivized, sybil-proof propagation of information both extrinsic and intrinsic to the decentralized state-machine, in the presence of a decentralized data store comprising part of the machine; with the property of non-malleability as time approaches infinity?”.
4.1 System model/network model/agents and identities
4.1.1 Multi-agent approach
We model problematics assuming a multi-agent approach towards system’s design. In particular, each agent Λ might own multiple identities | | ≥ 0. We assume all agents being rationale and willing to maximize their expected returns. Thus, we call them ‘expectation maximisers’ in short. Further, in the context of networking, we might relate to agents simply as ‘nodes’. When we emphasize the fact of an identity being used in a specific role/context we shall indicate it in subscript, ex.
| ≥ 0. We assume all agents being rationale and willing to maximize their expected returns. Thus, we call them ‘expectation maximisers’ in short. Further, in the context of networking, we might relate to agents simply as ‘nodes’. When we emphasize the fact of an identity being used in a specific role/context we shall indicate it in subscript, ex.  \(_{C}\)—with ‘C’ for client/producer of transactions (see Definitions).
\(_{C}\)—with ‘C’ for client/producer of transactions (see Definitions).
As previously noted, the system is an open one, thus in order to achieve sybil-proofness, each agent needs to be motivated to transform his identity-portfolio into a singleton (Fig. 5). Further, due to the lack of authorities—the transformation needs to occur autonomously i.e. by each agent’s own will. Recall that as long as there is something to gain (i.e. when a maximum data path length was not reached and assuming immutability of its already reported identifiers)—the incentive to include Sybil-nodes would remain. Because of the aforementioned overall openness, nothing technically prevents formation of new identities. Similarly—nothing prevents data creation and/or data-copy operations as these are purely physical processes outside of the system’s accountability operandi. Thus, without constraints on network’s topology, one needs to look for statistically and game-theoretically sound game-rules—ones promoting possession of a single identity over a multiple. Effective actions undertaken by agents obeying the protocol need to be accountable and verifiable for. Once we assume,- due to the openness of the system, that it is indeed infeasible to prevent inclusion of Sybil identities into information’s endorsement at each clock-tick, we might still be able to design the game in such a way so as to affect the expected returns from cumulative individual actions, effectively discouraging Sybil-identities in the long run. Indeed, under the assumption that nodes are expectation maximisers deprived from the ability of pin-pointing favourable dealings we may affect agents’ individual decisions during each game-round i.e. at each clock–tick, effectively eliminating Sybil-nodes entirely. Similarly, Bitcoin [17] mitigates Byzantine participants not by solving the Byzantine Consensus problem itself, but rather by providing an efficient probabilistic workaround i.e. practical solution which affects unitary choices of participants. Now, relating to game-theory—we identify multiple simultaneous games: the game between agents trying to become a round leader, the game between clients willing to commit transactions, the game between leaders willing to propagate confirmed data-blocks and the game between agents trying to incentivize propagation of consensus-extrinsic information. By the end of the paper, we shall conclude our communication logic—used to incentivize data-exchange among participants of these games, to be sybil-proof as per the further-introduced operandi.
4.2 Threat model
In this work, we assume that there are no trusted entities. All entities are assumed to be expectation maximisers instead. Parties will strictly execute the designed protocol’s specifications, but may try to infer information related to others and to the network’s topology—by analysing and intercepting data during communication processes and available within the decentralized state-machine’s data-store. Gathered information may then be used to conduct unfair actions, ones technically allowed by the protocol specification, yet not allowed under game-theoretic rules governed by the majority of agents. It is assumed that due to the openness of the system the only way to prevent inappropriate behaviours is through properly structured intrinsic incentives governed through the conjunction of data-transmission protocols and consensus governing the state of the decentralized state-machine. We assume all agents to be capable of colluding, the fact which should not affect game-theoretical guaranties provided by the protocol, as long as, the number of colluding nodes does not exceed the majority of all agents. Data exchange between parties may be intercepted. The numerosity of agents and thus identities is assumed as very high, making inferring relationships between them—unfeasible.
5 Definitions
Blockchain. We model ‘blockchain’ as a decentralized probabilistic state-machine where leader of each game-round is responsible for proposing and of carrying out transitions to new states in cooperation with the rest of the network. The decentralized state machine’s consecutive state representations are buried within a sequence of entangled data-blocks. It is assumed that altering of that sequence(s) of data-blocks/states is prohibitive in the long run [1]. Anyone can propose particular variables of the state machine and/or values of these through ‘transactions’. We model leader(s) as unitary independent agent(s), although the results available herein might be applicable to protocols where a consortium(s) constitutes leader(s)—the case which may be compatible yet not modelled by degrees of freedom employed within our analysis. Further we may relate to is simply as a state machine.
Anonymity. We consider anonymity as routers’ inability of getting to know the system-intrinsic identifiers (ex. public-keys and/or identifiers generated based on these) of other data-path members. Such defined anonymity allows for, loosely defined, high-finalization guaranties in our apparatus, although it is not required to uphold the sybil-proofness guaranties.
Identity.  is created by \(\Lambda\) and registered within the decentralized state machine. \(\Lambda\) can own multiple identities.
is created by \(\Lambda\) and registered within the decentralized state machine. \(\Lambda\) can own multiple identities.  is assigned an Identity Token describing a Token Pool (
is assigned an Identity Token describing a Token Pool ( ). Initial parameters of
). Initial parameters of  and thus
and thus  are set by \(\Lambda\) upon its registration within the state machine. Only
are set by \(\Lambda\) upon its registration within the state machine. Only  associated with
associated with  I > 0 and
I > 0 and  which is not ‘depleted’ can effectively participate in a data exchange. It is assumed agents can query any identities’ public properties from the state machine (Fig. 6).
which is not ‘depleted’ can effectively participate in a data exchange. It is assumed agents can query any identities’ public properties from the state machine (Fig. 6).
-
Dominance
We employ the nomenclature of a ‘dominance relation’. We say that there is a dominance relation between
 \(_{i}\) and
\(_{i}\) and  \(_{i+1}\) and thus
\(_{i+1}\) and thus 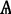 \(_{i}\) dominates
\(_{i}\) dominates  \(_{i+1}\), if and only if,
\(_{i+1}\), if and only if,  i has higher expected cumulative reward for propagation of information than
i has higher expected cumulative reward for propagation of information than 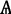 \(_{i+1}\).
\(_{i+1}\). -
Sybil-Proofness
We say that a protocol is sybil-proof if it discourages inclusion of artificial identities which do not improve network’s connectivity. This definition is compatible with definitions used either explicitly or implicitly in previous works mentioned herein.
-
2-or-more connected networks
In 2-or-more connected networks there is over one data-path between source and destination. Previous works achieved sybil-proofness in multiply connected networks but not in 1-connected/eclipsed networks (defined below).
-
1-connected/eclipsed networks
Conversely, in a 1-connected network there is only one data-path between source and destination. This might be due to low network’s connectivity or a result of an eclipsing attack [5].
When depicting communication protocols, for clarity of visual presentation we adopt the following general semantics:
-
M—capital latter, when not postfixed by a non-alphanumerical character—the transmitted information—possibly a data structure (ex. M—for a message/payload)
-
[A, B, C]—a data-structure here,—a concatenation of information A, B and C, the order is of no significance.
-
FA,B..(x0 … xn)—round brackets—the result of performing transformation F over x0 … xn, where A and B may indicate additional, function specific parameters. For example: \({Sig}_{SK}\left(M\right)\)—results in a cryptographic signature computed over message M and secret SK. The result does not include x0 … xn.
-
FA,B..[x0 … xn]—same as above with the exception that here—the result is a data structure—comprising both x0 … xn and the result of FA,B..(x0 … xn). For example: \({Sig}_{SK}\left[M\right]\) = [M,\({Sig}_{SK}\)(M)]. The order of concatenations is of no significance yet assumed as constant throughout agents executing the protocol.
5.1 Association symbol ~
We define the symbol of association ‘∼’ to depict a functional relationship between two data fields or structures. For instance,  ~\({M}_{i}P{E}_{k}\) describes that
~\({M}_{i}P{E}_{k}\) describes that  is an ephemeral secret key issued by
is an ephemeral secret key issued by  , having a functional applicability to data structure \({M}_{i}P{E}_{k}\) such as the ability of decrypting information contained within it.
, having a functional applicability to data structure \({M}_{i}P{E}_{k}\) such as the ability of decrypting information contained within it.
5.2 Data transformations
Within algorithms’ definitions we will be often transforming data-structures by including additional fields ex. M = [M, \({N}_{0}^{PK}\)]. For clarity of presentation, we may treat data fields and/or structures as sets ex.\({N}_{i}^{AD}=\mathrm{\varnothing }\) depicting that \({N}_{i}^{AD}\) is empty.
Token pool ( ) is a data structure representing a store of value, with a unitary, derived token (Г) as the smallest spendable unit of its total value. The pool is stored within decentralized datastore. A one-to-one relationship between the owning identity
) is a data structure representing a store of value, with a unitary, derived token (Г) as the smallest spendable unit of its total value. The pool is stored within decentralized datastore. A one-to-one relationship between the owning identity  is assumed. The structure is signed with
is assumed. The structure is signed with  . The value of a single Г is computed as
. The value of a single Г is computed as  . Let SH be a secret 256-bit value. Hash-values representatives of each token are computed in an ascending manner over i through:
. Let SH be a secret 256-bit value. Hash-values representatives of each token are computed in an ascending manner over i through:  . The value of
. The value of  is part of
is part of  and public, whereas only a limited portion of bits of SH may be made public and stored within
and public, whereas only a limited portion of bits of SH may be made public and stored within  . The amount of revealed bits should not make brute-forcing \({S}_{H}\) feasible. The total number of hashes comprising the Token Pool is stored publicly. In order to make payments or to prove its identity Λ steadily releases Г\(_{i}\) values in an descending order on i. Here, the security relies upon the assumed infeasibility of computing Г\(_{i}\) based on Г\(_{i+1}\) i.e. security of a one-way hash function. Note that the spender of assets may release any number of consecutive hashes and do so efficiently by transmitting only the last to be revealed, consequently revealing all the previous to it. If done so, the resulting value of a transmission token accumulates. Double spends are detected through keeping track of the used-up depth within the state-machine. If, a token at depth i is made public it is assumed tokens of i′ > i have also been spent already as well. Consequently, when Г\(_{1}\) is made public, the
. The amount of revealed bits should not make brute-forcing \({S}_{H}\) feasible. The total number of hashes comprising the Token Pool is stored publicly. In order to make payments or to prove its identity Λ steadily releases Г\(_{i}\) values in an descending order on i. Here, the security relies upon the assumed infeasibility of computing Г\(_{i}\) based on Г\(_{i+1}\) i.e. security of a one-way hash function. Note that the spender of assets may release any number of consecutive hashes and do so efficiently by transmitting only the last to be revealed, consequently revealing all the previous to it. If done so, the resulting value of a transmission token accumulates. Double spends are detected through keeping track of the used-up depth within the state-machine. If, a token at depth i is made public it is assumed tokens of i′ > i have also been spent already as well. Consequently, when Г\(_{1}\) is made public, the  is assumed to be used up in its entirety.
is assumed to be used up in its entirety.
-
Possibly compromised—in threat models to follow we say that the reward process is possibly compromised if data allowing to include Sybil-identities had been disclosed. Thus, possibly under additional requirements and/or circumstances—making compromising of the integrity of legitimate endorsement E feasible. Conversely, if data securing the reward process could be considered as immutable (ex. data buried at a blockchain depth assumed as irreversible), then and only then,—the reward process would not be considered as possibly compromised. In our work, if nodes obey the protocol, the possibly compromised scenario does never arise.
-
Finalization guaranties—we assume that the inability of agents to choose between favourable and non-favourable routing decisions increases the likelihood of the routed information M to arrive at its destination. That is under the assumption that agents are willing to maximize their profits and thus are ready to take a minimal amount of risk. Conversely, the ability to discriminate on less favourable routing-requests obviously results in lower probability of data delivery to succeed, thus—in lower finalization guaranties (Table 2).
Definitions used further throughout the paper are listed in table below:
The rationale behind  I is the same for all algorithms and represents an investment each intermediary needs to make to participate in the routing process. That is to prevent the nothing-at-stake problem. Recall that token-pool’s tokens represent fractions of its entire value and thus are considered spent once revealed and once the corresponding token-pool’s usage metrics are updated—all this needs to be performed at the discretion of decentralized consensus.
I is the same for all algorithms and represents an investment each intermediary needs to make to participate in the routing process. That is to prevent the nothing-at-stake problem. Recall that token-pool’s tokens represent fractions of its entire value and thus are considered spent once revealed and once the corresponding token-pool’s usage metrics are updated—all this needs to be performed at the discretion of decentralized consensus.
Value marked with a colon (ex. X′) represents the transformed, oftentimes received information X′ that logically corresponds to X but it may happen that X′ ≠ X after a possibly malicious, extrinsic modification done to X.
Path accountability We say that a path assurance algorithm thwarts tempering with the content of payload’s endorsement if payload delivered alongside the modified endorsement cannot affect the state of the decentralized state-machine.
6 Reward function
Before proceeding with introduction of the main body of the reward function, we shall first introduce some of its coefficients and describe two variations of the identity rating function across two dominance-relations.
Let the Identity Rating Function \(\epsilon\) be defined as  , where
, where 
 . β is decided upon by leader of each round. i.e. must be a result of decentralized voting. The function assures exponential growth from investment and leads to exponential growth in probability of dominating any set of encountered identities. It also has the property of \(\epsilon\)(
. β is decided upon by leader of each round. i.e. must be a result of decentralized voting. The function assures exponential growth from investment and leads to exponential growth in probability of dominating any set of encountered identities. It also has the property of \(\epsilon\)( ) being always greater than
) being always greater than  for any data-path length.
for any data-path length.
Let us now bring into picture the Reward Function  defined over two dominance relations:
defined over two dominance relations:
-
Global Dominance
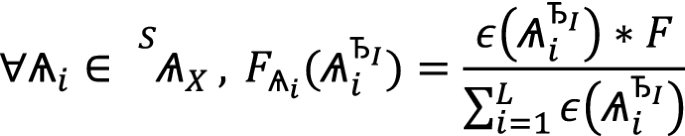
-
Local Dominance
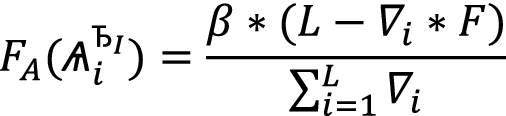
In local dominance, index \({\nabla }_{i}\) is used instead of \(\epsilon\)
 when compared to Global Dominance. In the former, a mapping ∅ is employed to map values of
when compared to Global Dominance. In the former, a mapping ∅ is employed to map values of  onto a family of ascendingly ordered elements ∇, with possibly multiple elements
onto a family of ascendingly ordered elements ∇, with possibly multiple elements  i ∀i ≤ k at each hierarchy level ∇i ∀i ≤ k; i.e. ∇0 = max(
i ∀i ≤ k at each hierarchy level ∇i ∀i ≤ k; i.e. ∇0 = max(
 ). Identity rating function takes the hierarchy’s index ∇i as input. In Global Dominance, stakes are used directly as exponents. It better captures reward-rates when differences between consecutive stakes are low. Still leading to overflows when large values are used. When stakes are high, the discrepancies between rewards might be very large. Conversely, in Local Dominance stakes are not used directly as exponents. Instead, identities are sorted by stakes in a descending order (duplicates removed) with indexes fed into the rating function. Now, due to small exponents, the result is not susceptible to overflows. The spread of rewards is less ‘bumpy’, with more rewards assigned to low-bidders when compared to global dominance, especially when differences between encountered stakes are high.
). Identity rating function takes the hierarchy’s index ∇i as input. In Global Dominance, stakes are used directly as exponents. It better captures reward-rates when differences between consecutive stakes are low. Still leading to overflows when large values are used. When stakes are high, the discrepancies between rewards might be very large. Conversely, in Local Dominance stakes are not used directly as exponents. Instead, identities are sorted by stakes in a descending order (duplicates removed) with indexes fed into the rating function. Now, due to small exponents, the result is not susceptible to overflows. The spread of rewards is less ‘bumpy’, with more rewards assigned to low-bidders when compared to global dominance, especially when differences between encountered stakes are high.
6.1 Routing mechanism
With routing of information there is always the sender, to be transmitted information M and a single or multiple recipients. Because we will take use of a decentralized state machine and stemming from the assumption that routing of information and methods of encryption heavily depend on whether public key of the leader is known—further we shall be considering two scenarios:
-
“Block-First-Then-Leader” (BFTL)—where leader is unknown at the beginning of each transactional round, thus both transactions and blocks are disseminated though a gossip like protocol.
-
“Leader-First-Then-Block” (LFTB)—where leader is known at the beginning of each round, thus, supposedly, transactions can be propagated more efficiently.
Here, let us note that statistical finalization guaranties differ and depend upon game theoretical characteristics of the transmitted information itself (transactions vs data-blocks vs state-machine extrinsic datagrams). They also depend upon the architecture—whether we are dealing with a LFTB or BFTL blockchain as the game-theoretical properties of the employed routing mechanism differ between the two architectures and from the viewpoint of a routing node—portrait divergent incentives for participation. Still, independently from the routing and path assurance methodology; the reward distribution function is always the same and will be proven to be sybil-proof in Sect. 8. Recall that the reward distribution function requires certain guaranties from the underlying data-propagation sub-system in order for its sybil-proof reward distribution guaranties to hold. These include non-malleability of the traversed data path and the previously defined anonymity among protocol-compatible routers.
Let us now proceed by introducing two path assurance algorithms: PA1 and PA2. These will be introduced steadily due to their rather intricate nature. The algorithms do account for the transmitted payload M. In other words, they facilitate both path-assurance and data propagation apparatus. The algorithms do not sensu stricto prove the data-path traversed, as it would indeed be unfeasible to assess everyone physically involved in propagation of information especially of parties not interacting with the data/protocol itself—a situation which could arise if nodes were not interested in being rewarded. Still, such a situation is incompatible with our assumptions and thus outside of the scope of our analysis. We shall require algorithms to ensure non-malleability of the already traversed data path against future intermediaries. Note the sound orchestration between the data-path assurance algorithms, the sybil-proof reward function and the propagation of the payload itself.
From the game-theoretical perspective, we distinguish between three types of transmitted information:
-
o
Information which is supposed to be assessed by the decentralized consensus and thus affect its state.
-
p
Information whose image (ex. SHA256(M)) is supposed to be assessed by the decentralized consensus.
-
q
Information that needs to arrive at its destination but which is otherwise consensus agnostic.
The first two imply the necessity of either M or its image, respectfully, to be included into the decentralized data-store so that the resulting state-transitions can be verified by the current and future leaders. In order to account for imminent game-theoretical differences, the proposed path assurance algorithms support two, related in this context, propagation modes: open and sealed. In latter, there is an additional initial step in which \({\Lambda }_{1}\) queries \({\mathrm{N}}_{0}\) for its identifier and performs transformation Φ(M, N0PK) over M which irreversibly imposes N0′s identifier onto M itself; effectively rendering M game-theoretically inseparable for applications involving the decentralized consensus under the premise that function Φ′ verifying the bond’s (M ↔ E) integrity needs to succeed on each node making up the majority. To allow for equations and to achieve extendibility without data loss, M is treated as a data-structure or a sequence of values. For better visualization let us now provide some sample sealing transformations (Φ) below:
-
M′ = Φ(M,..) =
 —the operation which makes M inseparable from ID = \({\mathrm{N}}_{0}^{\mathrm{PK}}\) under the premise that M needs to be accompanied by ID and signed together in the name of
—the operation which makes M inseparable from ID = \({\mathrm{N}}_{0}^{\mathrm{PK}}\) under the premise that M needs to be accompanied by ID and signed together in the name of  \(_{1}\). Naturally, the strength of this bonding depends on the strength of the signature.
\(_{1}\). Naturally, the strength of this bonding depends on the strength of the signature. -
Similarly, assume M′ = Φ(M,..) = [M, ID = \({\mathrm{N}}_{0}^{\mathrm{PK}}\), PoW([M, ID], σ)]. Now, under the assumption that Φ′ verifies presence of both ID and of the result of Proof-of-Work [22] (PoW) meeting certain difficulty σ ≥ σmin done over [M, ID], then M is inseparable from its coefficients ID and PoW under the difficulty σ used to compute the Proof-of-Work.
Now, the sole purpose of Φ is rendering M otherwise worthless for conceives involving the decentralized consensus when detached from E or shall E be replaced with E′. One such usage scenario would be prevention of M from being used by leaders when delivered through a noncompatible path assurance/route traversal protocol or when a legitimate path was mangled with.
The path traversal and path verification algorithm need to protect the integrity of previously traversed identities at all times in order to uphold sybil-proof guaranties of the data-traversal algorithm. Recall that to achieve sybil-proofness in one-connected and/or eclipsed networks, the reward assignment function needs to promote possession of a single identity over multiple so to discourage inclusion of sybil identities even if such an action would be compatible with the path traversal protocol itself i.e. technically possible. The problem of assuring that M cannot not be replaced from within the MPE and thus of assuring that the endorsement E cannot be used for retransmission of another M′ facilitates a separate dilemma we will need to tackle.
Recall that in order to achieve high finalization guaranties we strive to ensure anonymity between intermediaries during traversal of M under the assumption that agents are expectation maximisers and would omit dealings that are likely not to generate profit, were investment values of their neighbours be known.
The path assurance and data propagation algorithms together with the accompanying threat models and game-theoretical assumptions under which they are valid will be presented below. Note that for now we give generalized protocols without implying M to be a transaction or a data block. We will give case-specific treatments later on when extending upon what is being shown. While the purpose of the following algorithms is detecting if path within the endorsement E was tempered with, the very intentions of including Sybil nodes shall be thwarted by the sybil-proof reward function introduced later on in Sect. 8.
Shall Г\(_{{\mathrm{N}}_{i}}\) be revealed but not make it into the decentralized storage and thus token pool’s usage not be updated within it, the Г\(_{{\mathrm{N}}_{i}}\) value might be consider as compromised and may be reused.
\({PA}_{1}\) supports two routing modes: open and anonymous, together with the already discussed information-sealing features.
6.1.1 Path assurance algorithm PA 1
Assumptions
Initially, \({\Lambda }_{1}\) is not required to be aware of any intermediaries besides the initial intermediary \({N}_{0}\). Now, we require \({\Lambda }_{2}\) to be able to get to know the identities of agents who helped with propagation of M. Let \({\Lambda }_{1}\) be the sender of information and let \({\Lambda }_{2}\) be the recipient. Assume  \(_{1}\)∈ \({\Lambda }_{1}\) and
\(_{1}\)∈ \({\Lambda }_{1}\) and  \(_{2}\) ∈ \({\Lambda }_{2}\). Now dependently on routing mode:
\(_{2}\) ∈ \({\Lambda }_{2}\). Now dependently on routing mode:
-
Anonymous mode: \({\Lambda }_{2}\) is required to be known to \({\Lambda }_{1}\) by
 ∈
∈  2
2 -
Open mode: \({\Lambda }_{2}\) is assumed not be known to \({\Lambda }_{1}\)
The above two modes are self-excluding.
Now, agnostically to routing mode, there are two optional features which can be enabled:
-
Sealing-feature implying use of Φ(M, E)—used by sender and Φ′(M, E)—by verifier
-
Public-Target known-feature—yet to be described.
Now, let us define transformation Φ1 rendering M inseparable from E, together with a function \({{\Phi }^{^{\prime}}}_{1}\left({\mathrm{M}}^{\mathrm{^{\prime}}}\right)\) verifying bond’s (M ↔ E) integrity:


The purpose of a keyed-mac function and thus of R is to thwart intermediaries ability of getting to know \({N}_{0}^{PK}\) under the premise that all identity-related public keys are traversable within public storage. The value of HM does not leak any information regarding \({N}_{0}^{PK}\) under presumption of HMAC being a one way transformation. Thus, not allowing for associating with any of the registered public keys, as long as, R remains secret during path traversal. Here, bond’s verification requires two round trips. During the second, the value of R is released, as required by \({\Phi }_{1}^{^{\prime}}\). Indeed, full validation cannot be performed on sight of MPEk alone. Here, note that M is not required by \({\Phi }_{1}^{^{\prime}}\). and its image is sufficient instead.
Now, let us define yet another bonding (M ↔ E) transformation \({\Phi }_{1}\):

Here, even under the premise that public keys of identities are known, transformation \({\Phi }_{2}\) does not leak information regarding \({\mathrm{N}}_{0}^{\mathrm{PK}}\) thus not allowing for association of transmitted information M with identity-related \({\mathrm{N}}_{0}^{\mathrm{PK}}\). That is because HM is based solely on an ephemeral public key used by intermediaries and sender to encrypt endorsement’s layers on the way to destination. Interestingly, both transformations irreversibly associate any future legitimate version of endorsement Ek with M while only knowledge of a few initial, imminent variables is required. That is under the premise that path assurance algorithm assures non-malleability of Ei−1 against Ni. Note that verification \({\Phi }_{2}^{^{\prime}}\). can be performed on sight of \({MPE}_{k}\), requiring only  \(_{2}^{\mathrm{EPK}}\)
\(_{2}^{\mathrm{EPK}}\)
Let N be an ordered set of identities of agents participating in the routing process, thus |N|= k; where Ni ∈ N; i ≥ 1 represents a particular routing identity. It is assumed that  \(_{2}^{\mathrm{PK}}\in {\Lambda }_{2}\) is known to Λ1.
\(_{2}^{\mathrm{PK}}\in {\Lambda }_{2}\) is known to Λ1.
Threat model (TM1): Attackers are believed to be trying to replace one or more identities within the endorsement. Potential attackers include nodes encountered during traversal of M and the final destination Λ2. The ability of the protocol to detect and thwart tempering with the content of E relies upon the strength of the applied signature function, together with the secrecy of  \(_{1}^{\mathrm{SK}}\). Now dependently on enabled modes and features:
\(_{1}^{\mathrm{SK}}\). Now dependently on enabled modes and features:
-
Anonymous mode: we assume intermediaries to be trying to get to know identities of their peers in order to assess their likelihood of either winning or losing. This should be unfeasible under the assumed strength of the encryption function and secrecy of recipient’s private key.
-
Open mode: intermediaries are free to get to know identities of their peers by looking at endorsement E.
-
Seal-feature: we require M to be usable only when accompanied by a legitimate E under the assumption that Φ(M, E) transforms M in a way that Φ′(M, E′) succeeds only if E′ = E. Intermediaries and \({\Lambda }_{2}\) are assumed to be willing to detach E from M in order to introduce Sybil nodes of their own—all of which should be mitigated and fall short under the requirement that Φ′(M′) needs to succeed at \({\Lambda }_{2}\).
We present the algorithm in (Fig. 7) below:
Note that the bond between M and E established through an image SHA256(M) ∈ P(1st line) is insufficient when requiring M to be unusable without the presence of E, shall M arrive at leader by omitting to the described propagation scheme. That is when the bonding mode comes in handy. Further, we will take use of optional parameters in more complex use-case scenarios. Note that, although PA1 requires round-trips between consecutive agents, no further interaction from Λ1 is needed upon the release of MPE0. Also, as far as incentives go, the above algorithm does not provide any. In order to make the algorithm incentive-compatible we will equip it with the capability of rewarding intermediaries with a ‘virtual asset’ i.e. cryptocurrency. Yet, for this to be possible, the meta-data based upon which rewards are to be issued need to make it into the decentralized storage so to be assessed by the decentralized consensus. Specifically, the payload’s accompanying endorsement has to—so that round leaders, operating the decentralized consensus mechanics can properly recognize the intermediaries and carry out reward assignments, on the decentralized state machine, as dictated by the sybil-proof reward function (Sect. 8). Therefore, in anonymous mode, an ephemeral key is employed to allow others to decrypt E without compromising the recipient’s identity-related private key. Notice that for E to be made available within the decentralized data store, Λ2 first needs to be incentivized to include E into a data-block. If Λ2 is not a leader, we assume that he needs to be incentivized to motivate others (i.e. another leader which might or might not be known to Λ2 and possibly additional intermediaries leading to it)—to help include E into a data-block. All this should happen at the expense of A1—in whose intention it is, as we assume, to deliver M to A2. Above all, the entire process needs to remain incentive-compatible.
Previous algorithm did not allow intermediaries to remain anonymous when recipient’s public key remained unknown. Now, we will propose a data-routing and path assurance algorithm suitable for when  is unknown to Λ1 and for when anonymity among intermediaries is desirable. Here, the only sought for property of a potential recipient is for it be a potential leader. The mechanism requires two round trips between sender and—one or two possibly different leaders. We shall proceed by introducing a simplified non-incentive compatible version of the protocol.
is unknown to Λ1 and for when anonymity among intermediaries is desirable. Here, the only sought for property of a potential recipient is for it be a potential leader. The mechanism requires two round trips between sender and—one or two possibly different leaders. We shall proceed by introducing a simplified non-incentive compatible version of the protocol.
6.1.2 Simplified Path Assurance Algorithm PA2 (two modes: open and sealed)
Assumptions
Let Λ1be the sender of information and let Λ2 be the recipient. Assume  1 ∈ Λ1 and
1 ∈ Λ1 and  2 ∈ Λ2. Let N be an ordered set of identities of agents participating in the routing process, thus |N|= k; Ni ∈ N where i ≥ 1 represents a particular routing identity. We assume all agents to be well connected to the network. The aim of the algorithm is to enable for path assurance and data delivery from Λ1 to Λ2 when
2 ∈ Λ2. Let N be an ordered set of identities of agents participating in the routing process, thus |N|= k; Ni ∈ N where i ≥ 1 represents a particular routing identity. We assume all agents to be well connected to the network. The aim of the algorithm is to enable for path assurance and data delivery from Λ1 to Λ2 when  is unknown under the premise that Λ2 is a round leader. Initially, Λ1 is not obliged to know any intermediaries besides N0. We want transmitted information M to arrive at the ultimate destination as soon as possible and require the protocol to be effective under simplex connectivity between the sender and round leader who is assumed to be selected randomly with uniform distribution and unknown. That stems from an assumption that there might be no time to allow for additional round-trips between the two so to perform a Diffie–Hellman key-exchange and establish a secure channel as leaders might rapidly change.
is unknown under the premise that Λ2 is a round leader. Initially, Λ1 is not obliged to know any intermediaries besides N0. We want transmitted information M to arrive at the ultimate destination as soon as possible and require the protocol to be effective under simplex connectivity between the sender and round leader who is assumed to be selected randomly with uniform distribution and unknown. That stems from an assumption that there might be no time to allow for additional round-trips between the two so to perform a Diffie–Hellman key-exchange and establish a secure channel as leaders might rapidly change.
Threat model (TM2): Potential attackers are nodes encountered during traversal of M including the eventual destination \({\Lambda }_{2}\). Attackers are assumed to be trying to replace one or more \({N}_{i}^{PK}\in E\). The ability of the algorithm to detect and thwart tempering with E relies upon the presumed strength of encryption and secrecy of both \({E}_{S}\) and  . That is until E becomes non-malleable and the two values are made public as part of the Unlocking Data (UD). Information within UD allows to validate, decrypt and possibly rewrite E. In order to ensure non-malleability of E after M reaches its destination and thus to uphold sybil-proof properties of reward-mechanics-it is of an utmost important not to release UD too early, meaning not until E becomes non-malleable. The property of non-malleability is assumed to be acquired by E when stored beneath blockchain-depth ≥ BS which is when \({\Lambda }_{1}\) can safely release the UD. Similarly, here, the algorithm also supports two propagation modes: open and sealed. In latter, transformation Φ irreversibly embarks identifier of the first intermediary N0 onto the transmitted information/data-structure M without revealing information regarding N0 during Epochi to anyone.
. That is until E becomes non-malleable and the two values are made public as part of the Unlocking Data (UD). Information within UD allows to validate, decrypt and possibly rewrite E. In order to ensure non-malleability of E after M reaches its destination and thus to uphold sybil-proof properties of reward-mechanics-it is of an utmost important not to release UD too early, meaning not until E becomes non-malleable. The property of non-malleability is assumed to be acquired by E when stored beneath blockchain-depth ≥ BS which is when \({\Lambda }_{1}\) can safely release the UD. Similarly, here, the algorithm also supports two propagation modes: open and sealed. In latter, transformation Φ irreversibly embarks identifier of the first intermediary N0 onto the transmitted information/data-structure M without revealing information regarding N0 during Epochi to anyone.
The algorithm takes use of ‘clearing transmissions’ nomenclature—the concept which will be explained further.
Do note that the algorithm below is concerned with three epochs in time. The current Epochi—in which sender is willing to dispatch data; Epochi−m which happened in the past—m epochs ago; and Epochi+n—which happens in the future. Like previously, first let us proceed with a non-incentive compatible and thus simplified version of the algorithm presented in (Fig. 8) below:
Notice that letting the decentralized state-machine verify the path traversed always requires two round trips between the sender and any effective round leader. Here all we care for is for the decentralized consensus to assess the decrypted E—the identity of a particular leader is of no significance at all. The value \({M}_{i}^{ID}\) within UD released by \({\Lambda }_{1}\) in \({Epoch}_{i+n}\) allows \({\Lambda }_{2}\) to look up the corresponding Ek from the decentralized storage, values  , \({E}_{S}\) allow \({\Lambda }_{2}\) to decrypt all the layers of \({E}_{k}\), while comparing \({E}_{S}\), with \({E}_{{S}^{^{\prime}}}\), allows round leader the ensure that the sequence of intermediaries was not tempered with. Indeed, mangling with any \({E}_{i}\), ∈ E would result in \({E}_{{S}^{^{\prime}}}\) ≠ \({E}_{S}\). For the tempering to be unexposed by Λ2, the attacker would need to become in possession of the secret value \({E}_{S}\). As a consequence, for the protocol to be valid under TM2, Λ1 should release \({E}_{S}\) only, as soon as, it is positive that E made it into the data block buried at least at blockchain depth ≥ \({B}_{S}\). Indeed, it is crucial for Λ1 to withhold ES until E makes its way towards the decentralized storage and becomes immutable. Indeed, Λ1initiates \({Epoch}_{i+n}\) only after PEk ~ \({Epoch}_{i-n}\) had been buried deep, at the discretion of Λ2, within one of the data blocks, but at least at blockchain depth ≥ \({B}_{S}\).—the depth at which data blocks are deemed to be irreversible. Since, we do not want anyone to be able to trick the majority into believing in another version of E, once UD had been released, we await UD to make it deep into the history of events before proceeding to \({Epoch}_{i+n}\). Now, since Λ1 needs to get a confirmation before proceeding;—stemming from the assumption that all nodes are well connected to the network, Λ1 is presumed to be actively monitoring the incoming blockchain blocks, awaiting an appropriate moment to initiate the second phase of the protocol—\({Epoch}_{i+n}\).
, \({E}_{S}\) allow \({\Lambda }_{2}\) to decrypt all the layers of \({E}_{k}\), while comparing \({E}_{S}\), with \({E}_{{S}^{^{\prime}}}\), allows round leader the ensure that the sequence of intermediaries was not tempered with. Indeed, mangling with any \({E}_{i}\), ∈ E would result in \({E}_{{S}^{^{\prime}}}\) ≠ \({E}_{S}\). For the tempering to be unexposed by Λ2, the attacker would need to become in possession of the secret value \({E}_{S}\). As a consequence, for the protocol to be valid under TM2, Λ1 should release \({E}_{S}\) only, as soon as, it is positive that E made it into the data block buried at least at blockchain depth ≥ \({B}_{S}\). Indeed, it is crucial for Λ1 to withhold ES until E makes its way towards the decentralized storage and becomes immutable. Indeed, Λ1initiates \({Epoch}_{i+n}\) only after PEk ~ \({Epoch}_{i-n}\) had been buried deep, at the discretion of Λ2, within one of the data blocks, but at least at blockchain depth ≥ \({B}_{S}\).—the depth at which data blocks are deemed to be irreversible. Since, we do not want anyone to be able to trick the majority into believing in another version of E, once UD had been released, we await UD to make it deep into the history of events before proceeding to \({Epoch}_{i+n}\). Now, since Λ1 needs to get a confirmation before proceeding;—stemming from the assumption that all nodes are well connected to the network, Λ1 is presumed to be actively monitoring the incoming blockchain blocks, awaiting an appropriate moment to initiate the second phase of the protocol—\({Epoch}_{i+n}\).
Let us wonder; in Step 2 how is \({\Lambda }_{1}\) to be assured of the fact that MiPE arrived at \({\Lambda }_{2}\)? Here, up until now, there had been no incentive for \({\Lambda }_{1}\) to act in \({Epoch}_{i+n}\)—had it not had any additional information to send; also no incentive for \({\Lambda }_{2}\) to include PE into the decentralized data-store for it to become public and non-malleable and also no incentive for intermediaries to act in Step 3 during \({Epoch}_{i+n}\). Additionally, how is \({\Lambda }_{1}\) to provide \({\Lambda }_{2}\) with UD? Even if, in \({Epoch}_{i}\), \({\Lambda }_{1}\) managed, somehow, to incentivize others to route MiPEk towards \({\Lambda }_{1}\)—the same data-path might become unavailable in \({Epoch}_{i+n}\). Thus, the second stage of the algorithm requires a way of providing incentive for additional, possibly unknown intermediaries encountered while M traverses the network. We need to modify the algorithm, let as proceed.
Now, while having in mind algorithm PA2 let us bring into the picture the decentralized datastore and let us unfold the incentive-compatibility requirements by affixing PA2 deeper into our rational, incentive-compatible realities.
Assumptions
It is in the intention of \({\Lambda }_{1}\) for \({\Lambda }_{1}\)—the latter being any round leader, to receive information M; which is why \({\Lambda }_{1}\) is to cover the ‘propagation fees’ paid out to agents whose involvement is indispensable. These include intermediaries and round leaders from both Epochi and Epochi+n who are to include the necessary meta-data into the decentralized state machine’s data-store. One can easily imagine an opposite scenario, say a content delivery network, in which case, it would be in the intention of \({\Lambda }_{2}\) to have M delivered from Λ1. Here, we are not concerned with the nature of M and do not require M to be included within the data store comprising the decentralized state-machine. Additionally, Λ1 needs not to be aware of any intermediaries besides the (sub)set of its imminent neighbours (\({N}_{{E}_{1}}\)) chosen at the discretion of.
\({\Lambda }_{1}\). Further, if M is a ‘transaction’—we desire it to be processable as soon as possible, thus M is delivered to destination already by the end of Epochi. Indeed, the sole purpose of Epochi+n is to assure game-theoretical soundness of the protocol for everyone involved. It is assumed that M has a unique identifier \({M}_{ID}\)∈ M. The protocol rewards intermediaries of a unitary successful data path only. In case of multiple data-paths, the shortest one should prevail. Our reward function (Sect. 6) does not rely on the property of path lengths in order to achieve sybil-proofness. Even though explicit preference of shortest data-paths could have the benefit of saving up on storage for the entire network—it is not enough to discourage sybil nodes in 1-connected networks, also we do not assume the encountered leaders to be willing to participate for more than a single round and so being agnostic to the long-term wellbeing of the entire system. Intuitively, under the additional global premise of agents being expectation maximisers we need to affect leaders’ atomic decisions. We—as designers, have the power of choosing shortest-path incentive compatible.
\({E}^{e}\)—optional endorsement when PA2 invoked by external algorithm.
Let us assume the existence of the following sets of intermediaries:
\({N}_{{E}^{e} }=\sum {N}_{i}\in {E}^{e}\) when \({E}^{e}\ne \varnothing\) otherwise. It is the set of routing identities from an external invocation of another path assurance protocol.
\({N}_{E}\)~ \({Epoch}_{i}\)—the set of routing identities from \({Epoch}_{i}\)
\({N}_{{E}_{k}}\)—the final set of rewarded intermediaries rewarded for propagation of M (including nested invocations of protocols) including propagation of possibly additional meta-data required to end-up within the decentralized storage.
C is assumed to be a protocol defined constant such that C < BS due to an assumption that  ≪ RL.
≪ RL.
Threat model (TM3): Extends TM2. Intermediaries are to remain anonymous until E ~ Epochi is buried deep within the history of events at depth assumed as irreversible (≥ \({E}_{S}\)) which is when Epochi+n begins. After that, nobody (including \({\Lambda }_{1}\) and \({\Lambda }_{2}\)) should be able to trick the majority into believing in a version of \({{M}_{i}{\text{PE}}}_{k}\) other than the one initially published by Λ1. Under these assumptions and under validity of the sybil-proofness Theorem of the reward distribution function laid out in Sect. 8—the protocol should allow for a Sybil-proof distribution of rewards when Λ2 remains unknown to Λ1 at the beginning of Epochi. Shall the consensus mechanism fork out the already published block Bi once unlocking data had been already released—the reward process is to be considered as possibly compromised—shall an adversary come into possession of \({UD}_{{\Lambda }_{1}}^{out}\) and be able to rewrite the content of E, which is assumed as unfeasible under the assumption that data bellow ≥ \({E}_{S}\) is deemed as irreversible. The secret ephemeral key pair used for encryption, which we employ to allow for reusability of the sender’s identity-related key-pair, is to be compromised in \({Epoch}_{i+n}\) once everyone may decrypt the endorsement.
Now we may proceed with an incentive-compatible version of \({PA}_{2}\). Recall that  represented optional, complementary sets of information. Thence, now these might encapsulate a complementary endorsement \({E}^{e}\), when invoked by another protocol. Sample case is yet to follow, namely for propagation of system extrinsic data-packets. Additionally, these fields are now used to carry incentive-related data-structures. Later, when we arrive at incentivized propagation of system-extrinsic datagrams, they will be used for recursive invocations of protocols (algorithms) (Fig. 9).
represented optional, complementary sets of information. Thence, now these might encapsulate a complementary endorsement \({E}^{e}\), when invoked by another protocol. Sample case is yet to follow, namely for propagation of system extrinsic data-packets. Additionally, these fields are now used to carry incentive-related data-structures. Later, when we arrive at incentivized propagation of system-extrinsic datagrams, they will be used for recursive invocations of protocols (algorithms) (Fig. 9).
6.1.3 Incentive compatible path assurance algorithm PA2 (two modes: open and sealed)
Agents may perform arbitrary consecutive invocations of the protocol, thus theoretically allowing for the protocol never to finish, with intermediaries not being rewarded at all. Note that such situation does not lead to a game-theoretical Nash equilibrium. That is because, under our global assumption of agents being expectation maximisers, unwilling to loose, it is rational to presume that senders would be willing to get back the frozen assets from previous epochs. Indeed, at any point in time, there will always be at least a single, set of intermediaries who did not get rewarded as of yet, with one set corresponding to the latest epoch. Here, with each invocation of the protocol, sender provides ‘unlocking data’ for its previous invocation. Note that PE values are signed by sender, thus when a full-node notices same Г\(_{{N}_{i}}\) being re-used for transmission for more than one M, it would include a proof of such fact (containing the two signed PE values), while issuing additional penalty to sender, with the on spotter receiving reward in the same amount the mischievous node is penalized with (preventing out-of-thin air reward formation).
Recall—other nodes maintaining consensus over state-domains would always verify updates to the decentralized State-Machine’s variables based on data present within Bi by reprocessing available information. In case of any discrepancies, as seen by the majority- consequently nobody would be rewarded.
In Step 4 the purpose of \(C\times {B}_{S}\) delay is to allow for \({\mathcal{L}}_{i}\) to be penalized by \({\mathcal{L}}_{{i}^{^{\prime}}}\) (Step 9) for a possibly excessive path length. Separation of the protocol into two independent epochs enables for a-synchronicity. Notice that the decentralized state machine does not need to wait upon \({\Lambda }_{1}\) to release UD. First, \({\Lambda }_{1}\) needs to be assured PEK had been buried deep within storage by \({\Lambda }_{2}\) before it initiates Epoch2. Otherwise, possibly nested endorsements within E would not become non-malleable opening the door to Sybil attacks if the history of events forked and attackers got to know [ES, EphSKC]—the secrecy of which the sybil-proofness guaranties rely upon (TM4).
After all the complexity of PA2 let us now proceed to an incentive compatible version of an earlier algorithm (PA1).
Assumptions
\({\Lambda }_{2}\) is assumed as a round leader known through identity  \(_{2}\) to which corresponds a public key
\(_{2}\) to which corresponds a public key  . It is in the intention of agent \({\Lambda }_{1}\) for \({\Lambda }_{2}\) to receive information M; which is why \({\Lambda }_{1}\) is to cover the ‘propagation fees’ paid out to agents whose involvement is indispensable. These include intermediaries and the final destination \({\Lambda }_{2}\).The protocol rewards intermediaries of a successful data path only, one chosen at the discretion of \({\Lambda }_{2}\) (in case of alternatives).
. It is in the intention of agent \({\Lambda }_{1}\) for \({\Lambda }_{2}\) to receive information M; which is why \({\Lambda }_{1}\) is to cover the ‘propagation fees’ paid out to agents whose involvement is indispensable. These include intermediaries and the final destination \({\Lambda }_{2}\).The protocol rewards intermediaries of a successful data path only, one chosen at the discretion of \({\Lambda }_{2}\) (in case of alternatives).
Threat model (TM5): Extends TM1. Intermediaries are assumed to be willing to get to know their peers so to be able to choose favourable dealings. When in anonymous data-routing mode we take use of the fact that intermediaries are unable to get to know their peers during Epoch1. This leads to higher finalization guaranties under the assumed soundness of the Sybil-proof reward assignment function (Sect. 8). Note that in case the consensus mechanism forks out Bi, the reward mechanism is not considered as potentially compromised, under the presumed secrecy of  \(_{1}^{SK}\)
\(_{1}^{SK}\)
Below, the processing related to various modes and features of PA1 has been omitted for the clarity of presentation—we now focus on incentive-related additions (Fig. 10).
The so far introduced, incentive-compatible protocols allow for accountability of the traversed data-path. When combined with the proposed reward function from Sect. 8, they allow for Sybil-proof exchange of information when target \({\Lambda }_{2}\) is known or unknown. Still, so far, in all cases it used to be paramount for the destination of information to be a leader. Now, we shall extend upon what we have already proposed in order to introduce a mechanics suitable for when \({\Lambda }_{2}\) is not a leader thus allowing for a Sybil proof exchange of arbitrary, consensus extrinsic information also in eclipsed and 1-connected networks in the presence of a data-store with the property of non-malleability as time approaches infinity. Indeed, now the only requirement from \({\Lambda }_{2}\) will be to own an identity ( \(_{2}\)) with a corresponding public key (
\(_{2}\)) with a corresponding public key ( ).
).
Thence, allowing for decoupling of the role of a recipient from that of a round leader. Still, the involvement of the latter and thus of the decentralized state-machine is compulsory. Here, potential leaders are the ones maintaining the decentralized data-store with the property of non- malleability as time approaches infinity. Additionally, we shall be accounting for both scenarios in which leader may be known or unknown in the wake of each round to \({\Lambda }_{2}\).
Here, efficiency of storage makes up an important dilemma. As has been described in our previous works where we introduced the notion of State-Full and State-Less blockchain channels,- including information into the decentralized state-machine regarding every data-packet exchanged between source and destination would impose an unbearable amount of storage-overhead at high redundancy. To cope with that, here it is a wonderful opportunity to employ the previously introduced State-Full channels. The sender of information will reward parties involved through rewards described by frozen assets constituting fractions of previously ‘bought’ Transmission Pools. The assets will be steadily released to parties involved by uncovering secret hashes through Transmission Tokens. Parties involved can detect a change in the data-path by looking at E containing encrypted identities. Closing the state-channel and submitting [P,E] into the state-machine entails cost, thus it pays to wait as long as possible or until the path changes before doing so. State-channel can be closed by any party involved. All it takes is to submit [P,E], which contains sender’s signature, into the full node who would do the processing. PE is included alongside every M and contains the first and the most recently released Transmission Token, also the number of tokens released in total during particular state-channel for efficiency of verification at the leader. Thanks to this number leader can verify if ending hash is at the supposed position without performing unnecessary blind brute-forcing until it comes at the supposed, claimed final value. In that sense PE constitutes the Transit Token described earlier. The total reward pool used to reward parties involved is calculated through accumulation of Transmission Tokens through the entire data transmission.
6.1.4 Data routing algorithm PA 3
Assumptions
As previously, it is possible for intermediaries to be rewarded only if E successfully made it into the data store. We require M to be accessible to \({\Lambda }_{2}\) as soon as possible, thus no protocol-intrinsic encryption of M against \({\Lambda }_{2}\) exists. The algorithm requires target \({\Lambda }_{2}\) to be known to \({\Lambda }_{1}\) by its public key. Now, supporting extrinsic targets, the target destination may not have the ability to affect State-Domains on its own; thus now we provide \({\Lambda }_{2}\) with the ability to incentivize additional, possibly unknown intermediaries to deliver E to a possibly unknown leader. In order to maintain game-theoretical soundness and under the global assumption of all agents, also those extrinsic to consensus-mechanics, being expectation maximisers, we introduce yet another reward \({R}_{T}\) paid out to \({\Lambda }_{2}\)—a reward covered at the expense of \({\Lambda }_{1}\), stemming from the assumption that \({\Lambda }_{2}\) is agnostic to M and that the incentive of delivery resides at source,—assuring that an incentive for \({\Lambda }_{2}\) to proceed after it received M exists. Note that \({R}_{T}\) had already been accounted for in the embodiments of previous algorithms. Again, once information reaches destination we need to incentivize destination to route E across additional intermediaries, who also need to be incentivized on the way to a leader. Here it is assumed that \({R}_{N}\) constitutes a serialized representation of a Transmission Token one most recently used in a data transmission between \({\Lambda }_{1}\) and\({\Lambda }_{2}\). At any time, agents may verify usage of corresponding Token Pools for double spends.
Threat model (\({TM}_{6}\)): Since the protocol may take use of both \({PA}_{1}\) and \({PA}_{2}\), corresponding specialized threat models apply. No reward shall be issued to any agent unless M reaches its destination (\({\Lambda }_{2}\)) Onlookers can verify reward values at any time since RL, RT, RN values are public (Fig. 11).
Note that the value of \({R}_{N}\) accumulates over time as sender of information makes the most recent Transmission Token represent higher and higher subrange of the corresponding Token Pool. The purpose of  is to prove, in the eyes of the leader, that M reached target \({\Lambda }_{2}\). Assets from RN will be used to incentivize all intermediaries involved in transmission between \({\Lambda }_{1}\), \({\Lambda }_{2}\) and \({\mathcal{L}}_{i}\)(possibly also \({\mathcal{L}}_{{i}^{^{\prime}}}\)).Thus, the total reward issued to intermediaries is equal to \({R}_{N}\). The reward assignment function takes into account all intermediaries. Note that in Step 6, \({\Lambda }_{2}\) is obliged to specify
is to prove, in the eyes of the leader, that M reached target \({\Lambda }_{2}\). Assets from RN will be used to incentivize all intermediaries involved in transmission between \({\Lambda }_{1}\), \({\Lambda }_{2}\) and \({\mathcal{L}}_{i}\)(possibly also \({\mathcal{L}}_{{i}^{^{\prime}}}\)).Thus, the total reward issued to intermediaries is equal to \({R}_{N}\). The reward assignment function takes into account all intermediaries. Note that in Step 6, \({\Lambda }_{2}\) is obliged to specify  \(_{T}\), \({R}_{{L}_{\mathrm{1,2}}}\), and \({R}_{N}\). While the last two are copied from ME0, the first is at disposal of \({\Lambda }_{2}\) and its \({\Lambda }_{2}\) who will be responsible for participating in a potential Epoch2 of PA3.
\(_{T}\), \({R}_{{L}_{\mathrm{1,2}}}\), and \({R}_{N}\). While the last two are copied from ME0, the first is at disposal of \({\Lambda }_{2}\) and its \({\Lambda }_{2}\) who will be responsible for participating in a potential Epoch2 of PA3.
The benefits include the possibility for intermediaries to abort the procedure at any point by verifying consistency endorsement E. Intermediaries are not blinded i.e. encrypted, thus, the finalization guaranties are lower (further discussion ahead) compared to the protocol presented below (Fig. 12):
We now have a solid groundwork for facilitating exchange of transactions, data blocks and consensus extrinsic information for both BFTL and LFTB decentralized state-machines. Let us now allow for some game-theoretical divagations and visualizations.
6.2 Transactions
Thanks to \({PA}_{1}\) and \({PA}_{2}\) intermediaries do not know who their neighbours are. Thus, routers cannot guess what rewards their neighbours are to claim. These properties were required to maintain high finalization guaranties. The gist is that during epoch1 T from  C needs to be delivered to ℒ1. Intermediary nodes include themselves into E. Consequently, in accordance to PA2, in epochi+1
C needs to be delivered to ℒ1. Intermediary nodes include themselves into E. Consequently, in accordance to PA2, in epochi+1
 C needs to release the endorsement’s embedded secret \({E}_{S}\) and \({EphSK}_{C}\) so that the endorsement can be decrypted by ℒ1. When M is assumed to make up transaction T both \({PA}_{1}\) and \({PA}_{2}\) can be used to facilitate sybil-proof propagation in both BFTL and LFTB machines.
C needs to release the endorsement’s embedded secret \({E}_{S}\) and \({EphSK}_{C}\) so that the endorsement can be decrypted by ℒ1. When M is assumed to make up transaction T both \({PA}_{1}\) and \({PA}_{2}\) can be used to facilitate sybil-proof propagation in both BFTL and LFTB machines.
6.3 Game-theory behind Epoch i and Epoch i+1
In Epoch1 it is obvious that  C has an incentive to take part since he wants to have the transaction processed. Routers have an incentive to participate since they want a cut from RN (Fig. 13).
C has an incentive to take part since he wants to have the transaction processed. Routers have an incentive to participate since they want a cut from RN (Fig. 13).
6.4 Game-theory at N i
Each agent can see RN and decide whether it wants to risk value of Г by including it within the endorsement. So whether or not to retransmit is a function of ( \(\in {N}_{i},L,{R}_{{L}_{\mathrm{1,2}}},\)
\(\in {N}_{i},L,{R}_{{L}_{\mathrm{1,2}}},\)
 ) i.
) i.
Technically, Ni can always include a Sybil but:
-
At low
 he is most likely not to receive rewards at all and loose
he is most likely not to receive rewards at all and loose -
No matter the number of Sybil nodes, the ones with highest
 \(_{I}\) would profit most
\(_{I}\) would profit most -
\({N}_{i}\) can judge the current path length by looking at the endorsement
6.5 Data arrived at 1
Leader ℒ1 chooses T endorsed by highest \({R}_{{L}_{\mathrm{1,2}}}\). He cannot decide based on routers since at this point they are unknown. Leader will be rewarded with the value of \(0.5\times ({R}_{{L}_{\mathrm{1,2}}}-\)
 ) thus the incentive is to choose the shortest path.
) thus the incentive is to choose the shortest path.
Game Theory during Epoch2
-
The precondition for initiation of Epochi+1 is that TEk is buried at a sufficient blockchain depth which we assume as constant for the protocol, but the value can be easily decided upon by the decentralized governance. In Epochi+1, client
 C has an incentive to release [EphSKC, S] since otherwise it would loose
C has an incentive to release [EphSKC, S] since otherwise it would loose  . Also, \({\mathcal{L}}_{2}\) has an incentive to participate since it receives 0.5 × (RL −
. Also, \({\mathcal{L}}_{2}\) has an incentive to participate since it receives 0.5 × (RL −  ).
).
6.6 Data-blocks
Transactions are data structures encapsulating instructions changing one or more variables of the decentralized state-machine. Naturally, the incentive to act, is on the side of the client who wants to make the particular change. Typical blockchain implementations incentivize leaders to act upon the received transactions by introducing a protocol-intrinsic incentive in the form of transaction-fees specified and covered by clients. Still, as has been described already, these implementations fail to incentivize intermediaries responsible for transaction deliveries. Also there is no incentive for potential leaders to transmit transactions to other nodes if for whatever reason they are unable to do the processing. In our proposal we have already introduced algorithms that provide additional Sybil proof incentive for intermediaries (under validity of the Sybil-proofness Theorem of the reward function described in Sect. 8) within any open-system where leader is either known or unknown in advance. Another important blockchain intrinsic aspect is the propagation of data blocks. Let us proceed with our proposal targeting the matter. Here, we employ the nomenclature of Block Sets (BS) to underline full support of systems in which leader may release multiple consecutive blocks until another leader is elected.
6.6.1 Data Blocks Routing Algorithm (path assurance + incentives)
Assumptions
Routers have an incentive to propagate data blocks since they want to have their re-transmission rewards recognized by other nodes. The more routers propagate, the higher the expected rewards as proven further. When re-transmitting, inseparable meta-data is generated and re-transmitted along the data-block. Once both (the meta-data and the data-block) arrive at a leader it issues propagation-rewards accordingly. Nodes/leaders seeing that meta-data alter the state of variables within their local instances of the decentralized state-machine based on data contained within these very blocks thus taking the rewards into effect, updating balances of routers’ accounts. By propagating they also increase the chance of reaching a round leader in the first place. There might be other incentives influencing withholding of data-blocks depending on other blockchain’s specific incentives and network conditions [6]. It is assumed that longest and/or heaviest path wins, thus other nodes have an incentive to build upon blocks published by others. As has been shown in other works, this depends on nodes’ capabilities versus the rest of the network. These game-theoretical rationale have been well depicted in [5].
Threat model: As usually, misbehaviours are driven by incentives. Here, intermediaries might be trying to replace the path the data-block took in an attempt to introduce Sybil-identities. Also, the recipients (potential leaders) might be trying to separate M = B from the endorsement E, in order to replace identities of intermediaries with their own. We assume intermediaries to be trying to get to know their peers during blocks’ propagation so to increase their chances of winning while decreasing their chances of losing (Fig. 14).
7 Proof of sybil-proofness
We now proceed with proving that the reward function employed by the previously depicted algorithms is sybil-proof indeed. Consequently, under the premise that the reward function is being used to reward data-propagation within the previously depicted games, it renders data-exchange within these games sybil-proof under validity of the provided theorem.
7.1 Preliminaries
The game agents participate in can be compared to a First-Price Sealed-Bid Auction (FPSBA) [14, 23,24,25] where the auctioneer is the round leader \(\mathcal{L}\) and the item being auctioned off is the propagation fee F set by  . That is with some notable differences. Here, agents receive fractions of F, in proportion to how they are rated in scope of a path by an exponential identity rating function \(\upepsilon\). All bids are collected by \(\mathcal{L}\). Agent would lose if his reward is dominated by others to turn out to be below Г\(_{V}\) (the payoff might be negative). \(\mathcal{L}\) does not know the bids and cannot issue rewards unless in \({{\varvec{e}}{\varvec{p}}{\varvec{o}}{\varvec{c}}{\varvec{h}}}_{{\varvec{i}}}\) (
. That is with some notable differences. Here, agents receive fractions of F, in proportion to how they are rated in scope of a path by an exponential identity rating function \(\upepsilon\). All bids are collected by \(\mathcal{L}\). Agent would lose if his reward is dominated by others to turn out to be below Г\(_{V}\) (the payoff might be negative). \(\mathcal{L}\) does not know the bids and cannot issue rewards unless in \({{\varvec{e}}{\varvec{p}}{\varvec{o}}{\varvec{c}}{\varvec{h}}}_{{\varvec{i}}}\) ( needs to release \({E}_{S}\)). Agents bid with Г\(_{V}\) which is constant for a given
needs to release \({E}_{S}\)). Agents bid with Г\(_{V}\) which is constant for a given  (for simplicity agents allowed to associate only a single Identity Token with any given identity).
(for simplicity agents allowed to associate only a single Identity Token with any given identity).
Notice that the uncertainty about the other agent’s  I, alongside the exponential reward drives
I, alongside the exponential reward drives  I to higher values and prevents inclusion of Sybil identities under the assumption of agents willing to make profit.
I to higher values and prevents inclusion of Sybil identities under the assumption of agents willing to make profit.
Assume nodes cannot get to know  I of other identities included in a data-path. Assume agents act rationally. They are expectation maximisers and use all of their available resources to gain profit. Without loss of generality, the fact that inclusion of an identity which further discourages inclusion of nodes owning low
I of other identities included in a data-path. Assume agents act rationally. They are expectation maximisers and use all of their available resources to gain profit. Without loss of generality, the fact that inclusion of an identity which further discourages inclusion of nodes owning low  has been omitted. (Note that this further improves the Sybil-proofness property). Penalty for a leader to include paths of higher lengths also has been omitted. Let
has been omitted. (Note that this further improves the Sybil-proofness property). Penalty for a leader to include paths of higher lengths also has been omitted. Let  \(_{M}\) be a set of legitimate identities owned by Λ,
\(_{M}\) be a set of legitimate identities owned by Λ,  \(_{S}\)—the set of Sybil identities, R—the achievable reward, \({R}_{max}^{\Lambda }\)—Λ′′s amount of limited, system-intrinsic currency.
\(_{S}\)—the set of Sybil identities, R—the achievable reward, \({R}_{max}^{\Lambda }\)—Λ′′s amount of limited, system-intrinsic currency.
Lemma 1
In previous works, sybil-proofness is often achieved by the \({f}_{i}^{k}\ge {f}_{i}^{k+1}+{f}_{i+1}^{k+1}\) requirement. In our proposal the order of inclusion into E is irrelevant, on the contrary,—the amount of investment ( \(_{i}\) i.e.
\(_{i}\) i.e.  ) is relevant instead, thus intuitively, we employ sets and require
) is relevant instead, thus intuitively, we employ sets and require  (Lemma 1) for sybil-proofness; i.e. greater sum of investments into
(Lemma 1) for sybil-proofness; i.e. greater sum of investments into  M alone results in higher expected rewards.
M alone results in higher expected rewards.
Speaking plainly, we begin by ascertaining two sets  M and
M and  S, with the second deemed as ‘Sybil/malicious’ and see how the game-mechanics cause the overall number of identities to tend towards 1, effectively rendering arity of the 2nd set
S, with the second deemed as ‘Sybil/malicious’ and see how the game-mechanics cause the overall number of identities to tend towards 1, effectively rendering arity of the 2nd set  \(_{S}\) to become 0. i.e. |
\(_{S}\) to become 0. i.e. | \(_{S}\)| tends towards 1 as |
\(_{S}\)| tends towards 1 as | M| tends towards 0 the process which is equivalent to elimination of Sybil nodes/identities.
M| tends towards 0 the process which is equivalent to elimination of Sybil nodes/identities.
Theorem 1
Now, let us prove that a given reward mechanism with a given reward function leads to highest rewards for Λ as the arity of \({\Lambda }_{S}\in\Lambda\) containing Sybil nodes tends towards 0 and  M is driven down to become a singleton for any path length L for any number of agents; i.e.
M is driven down to become a singleton for any path length L for any number of agents; i.e.  results in \(max(F({R}_{max}^{\Lambda }))\)—highest expected reward. i.e.
results in \(max(F({R}_{max}^{\Lambda }))\)—highest expected reward. i.e.  \(\Rightarrow max(F({R}_{max}^{\Lambda }))\).
\(\Rightarrow max(F({R}_{max}^{\Lambda }))\).
Lemma 2
Higher investment leads to higher ratings. To prove this lemma it suffices to note that the function grows exponentially with  for a given path length L.
for a given path length L.
Corollary 1
Higher rating value leads to higher values of the reward function. We employ a Reward Function defined as:
(Definition of Reward Function)
 denotes reward assigned to an ith identity in a data path,
denotes reward assigned to an ith identity in a data path,  , when X is a set, the function denotes cumulative a reward i.e.
, when X is a set, the function denotes cumulative a reward i.e.  . Here, it suffices to note that the reward function is a strictly increasing monotonic function, thus producing higher values for higher input values.
. Here, it suffices to note that the reward function is a strictly increasing monotonic function, thus producing higher values for higher input values.
7.2 Proof of sybil-proofness (global dominance)
-
1.
(Entity Ranking Function)
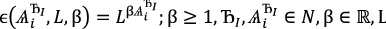 —path length
—path length -
2.
⇒(Lemma 2)
 (higher investment
(higher investment  \(_{I}\) leads to higher rating values for any given identity)
\(_{I}\) leads to higher rating values for any given identity)
Now, let  denote a set identities within a data path of length L.
denote a set identities within a data path of length L.
-
1.
(Definition of Reward Function)
 ;
; -
2.
(Definition 1) ⇒
 (the sum of member-rewards equals F—the achievable reward)
(the sum of member-rewards equals F—the achievable reward) -
3.
Thus,
 (total reward for members of
(total reward for members of 
-
4.
(Using 2) summing
 (data-path of length L filled entirely with Sybil nodes will yield lower rank than a path with just a single node of
(data-path of length L filled entirely with Sybil nodes will yield lower rank than a path with just a single node of  I greater by 1)
I greater by 1) -
5.
Thus, (using 4 and 1):
 (this translates to a higher expected total reward for any path length and any number of agents and identities)
(this translates to a higher expected total reward for any path length and any number of agents and identities) -
6.
Assuming the strategy of Λ it to maximize F (definition of Λ), (Using 5), node will prefer to accumulate \({R}_{max}^{\Lambda }\) within a single identity.
-
7.
Now notice that
 , thus
, thus  (and for
(and for  to exist i.e. be part of any set, and receive reward it needs to have
to exist i.e. be part of any set, and receive reward it needs to have  I ≥ 1 definition of
I ≥ 1 definition of  S)
S) -
8.
Thus, (using 2, 5 and 6)
 for any L. (proved Lemma 1)
for any L. (proved Lemma 1) -
9.
Thus, (using Lemma 1, 5 and 8)

 and thus (using definition of
and thus (using definition of
 )
) 
 or
or  (from a game-theoretic view)
(from a game-theoretic view) -
10.
⇒
 (proved Theorem 1)
(proved Theorem 1)
8 Conclusions
In this work, while focusing on the problem of sybil-proof data exchange, we have revisited previous approaches, showcasing their shortcomings, and laid forward the first information exchange framework; with integrated routing and reward-function mechanics, provably secure in thwarting Sybil-nodes in 1-connected or eclipsed networks. The framework neither requires nor assumes any kind of constraints regarding the network’s topology (i.e. network is modelled as a random-connected graph). The proposal, while being storage and transmission efficient, is suitable for rewarding not only consensus-related datagrams (both data-blocks and transactions) but consensus-extrinsic information as well, thus facilitating an universal sybil-proof data exchange apparatus, provably valid under the assumption of existence of a data store whose property of non-malleability emerges as time approaches infinity. We conducted our research under two scenarios—with round leader known and unknown in advance of each transactional round.
9 Future work
As of this writing, during revision of this manuscript, the here-in described mechanics have been already implemented and made operational on the test-net of our large research project (GRIDNET OS, available at https://gridnet.org), which is doing more than fine, soon to-be-made open-source. We have further research already pending, allowing for rewarding of multiple peers simultaneously from a single data-structure registered on a Decentralized State Machine through the concept of the to-be-introduced Multi-Dimensional Token Pools Currently these are employed as a show-off functionality in the Single/Multiplayer Snake game available on GRIDNET OS (for efficiently rewarding a large number of a-priori unknown peers from an on-the-chain registered relatively small data-structure once the player collects in-game-coins, without imposing excessive burden onto the decentralized state-machine). The crypto-mechanics have also been implemented in JavaScript and thus may be operational across a variety of protocols such as WebRTC for incentivizing data propagation across web-browsers also aiding the well-known problematics for incentivizing WebRTC TURN servers. Currently, we are working on incorporating the mechanics into file and audio/video transmissions happening over onion-routed data transmissions across full-nodes and web-browsers. As of this writing, the Web-part of GRIDNET OS is pending public deployment. It might be interesting to note that large portions of the project have been implemented on YouTube live since the early 2017.
References
Skowroński, R.: The open blockchain-aided multi-agent symbiotic cyber–physical systems. Futur. Gener. Comput. Syst. 94, 430–443 (2019)
Skowronski, R.: On the applicability of the GRIDNET protocol to Smart Grid environments. In: 2017 IEEE International Conference on Smart Grid Communications (SmartGridComm). IEEE, 2017
Abraham, I., et al.: Solidus: An incentive-compatible cryptocurrency based on permissionless byzantine consensus. CoRR, abs/1612.02916 (2016).
Skowronski, R.: Fully distributed GRIDNET protocol, with no trusted authorities. In: 2017 International Conference on Information Networking (ICOIN). IEEE, 2017
Ersoy, O., et al.: Information propagation on permissionless blockchains. arXiv preprint arXiv 1712 (2017)
Bag, S., Ruj, S., Sakurai, K.: Bitcoin block withholding attack: analysis and mitigation. IEEE Trans. Inf. Forensics Secur. 12(8), 1967–1978 (2016)
Smith, A.: 1723–1790. The Wealth of Nations/Adam Smith; Introduction by Robert Reich; Edited, with Notes, Marginal Summary, and Enlarged Index by Edwin Cannan. New York: Modern Library, 2000.
Matthews, R., Brauer, P., Dunne, J.: Defense Offsets: Policy Versus Pragmatism. Routledge, London (2004)
Connor, R.C.: The benefits of mutualism: a conceptual framework. Biol. Rev. 70(3), 427–457 (1995)
Archetti, M., et al.: Economic game theory for mutualism and cooperation. Ecol. Lett. 14(12), 1300–1312 (2011)
Boucher, D.H. (ed.): The Biology of Mutualism: Ecology and Evolution. Oxford University Press, New York (1985)
Bronstein, J.L.: Our current understanding of mutualism. Q. Rev. Biol. 69(1), 31–51 (1994)
Babaioff, M., et al.: On bitcoin and red balloons. In: Proceedings of the 13th ACM Conference on Electronic Commerce (2012)
Otte, P., de Vos, M., Pouwelse, J.: TrustChain: a sybil-resistant scalable blockchain. Future Gener. Comput. Syst. 107, 770–780 (2020)
Seuken, S, Parkes, D.C.: Sybil-proof accounting mechanisms with transitive trust. In: Proceedings of the International Foundation for Autonomous Agents and Multiagent Systems (2014).
Gong, S., Lee, C.: Blocis: blockchain-based cyber threat intelligence sharing framework for sybil-resistance. Electronics 9(3), 521 (2020)
Nakamoto, S.: “Bitcoin: A peer-to-peer electronic cash system.” Decentralized Business Review, 21260 (2008)
Ersoy, O., et al.: Transaction propagation on permissionless blockchains: incentive and routing mechanisms. In: 2018 Crypto Valley Conference on Blockchain Technology (CVCBT). IEEE, 2018
Ersoy, O., Zekeriya, E., Lagendijk, R.L.: TULIP: a fully incentive compatible blockchain framework amortizing redundant communication. In: 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW). IEEE, 2019.
Sauer, B.: Virtual currencies, the money market, and monetary policy. Int. Adv. Econ. Res. 22(2), 117–130 (2016)
Goldschlag, D.M., Stubblebine, S.G.: Publicly verifiable lotteries: applications of delaying functions. In: International Conference on Financial Cryptography. Springer, Berlin, 1998.
Liu, D., Camp, L.J.: Proof of Work can Work. In: WEIS. 2006.
Likelihood of winning and overbidding in first price auctions, Paolo Crosetto, Antonio Filippin, Peter Katuscak
McFadden, D.: The theory of first-price, sealed-bid auctions. Institute of Business and Economic Research, Economics at the University of California: Berkeley. Available in: http://eml.berkeley.edu/~mcfadden/eC103_f03/auctionlect.pdf. Accessed 7 Jan 2016 (2003). Auction Theory, Jonathan Levin
Predicting the probability of winning sealed bid auctions: the effects of outliers on bidding models, Skitmore, Martin
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Skowroński, R., Brzeziński, J. SPIDE: sybil-proof, incentivized data exchange. Cluster Comput 25, 2241–2270 (2022). https://doi.org/10.1007/s10586-021-03411-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03411-3














 i has higher expected cumulative reward for propagation of information than
i has higher expected cumulative reward for propagation of information than 
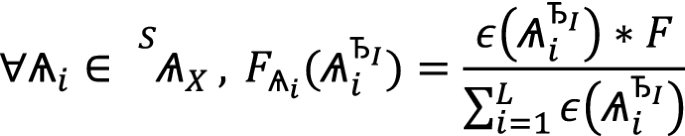
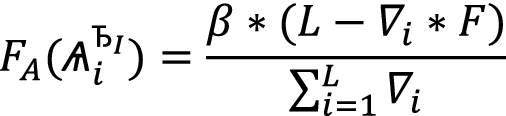
 —the operation which makes M inseparable from ID =
—the operation which makes M inseparable from ID = 
 ∈
∈  2
2






 he is most likely not to receive rewards at all and loose
he is most likely not to receive rewards at all and loose
 C has an incentive to release [EphSKC, S] since otherwise it would loose
C has an incentive to release [EphSKC, S] since otherwise it would loose  . Also,
. Also,  ).
).
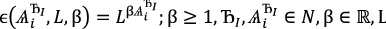 —path length
—path length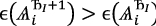 (higher investment
(higher investment 
 ;
; (the sum of member-rewards equals F—the achievable reward)
(the sum of member-rewards equals F—the achievable reward) (total reward for members of
(total reward for members of 
 (data-path of length L filled entirely with Sybil nodes will yield lower rank than a path with just a single node of
(data-path of length L filled entirely with Sybil nodes will yield lower rank than a path with just a single node of  I greater by 1)
I greater by 1) (this translates to a higher expected total reward for any path length and any number of agents and identities)
(this translates to a higher expected total reward for any path length and any number of agents and identities) , thus
, thus  (and for
(and for  to exist i.e. be part of any set, and receive reward it needs to have
to exist i.e. be part of any set, and receive reward it needs to have  I ≥ 1 definition of
I ≥ 1 definition of  S)
S) for any L. (proved Lemma 1)
for any L. (proved Lemma 1)
 and thus (using definition of
and thus (using definition of
 )
) 
 or
or  (from a game-theoretic view)
(from a game-theoretic view) (proved Theorem
(proved Theorem