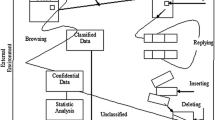
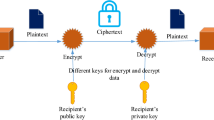
Abstract
Security of confidential information has been always an important issue. It has always been an interesting topic for researchers to develop secure techniques to send and receive data without revealing it to anyone rather than the receiver. Researchers are working every day to achieve a high level of security and consistency for their data during its transmission over the network. Cryptography is a way used to encrypt the data during its transmission so that when there is any attack, the message seen is not the real message, as it is encrypted. On the other hand, Steganography is a method of hiding secret messages in a cover object (image, audio, video, text) while communication takes place between sender and receiver. Steganography is often used with cryptography so that the information is doubly protected; First, it is encrypted and then hidden so that the attacker has to first detect the presence of information that is already hidden (a difficult task) and then decrypt it. In this paper, we will discuss different artificial intelligence techniques used to achieve maximum information hidden and high quality of image as the low quality is a sign of distortion which means that there is something hidden.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Shrija, Somaraj., and Mohammed Ali Hussain, F. 2015. Performance and security analysis for image encryption using key image. Indian Journal of Science and Technology.
Kurukshetra University, Kurukshetra, Haryana. 2016. Image steganography using enhanced LSB technique. International Journal of Scientific & Engineering Research.
Ansari, Arshiya Sajid, Mohammad Sajid Mohammadi, Mohammad Tanvir Parvez. 2019. A Comparative Study of Recent Steganography Techniques for Multiple Image Formats. International Journal of Computer Network and Information Security.
Ram MR Seshan. 2016. Assistant professor, Department of computer science, Challenges in steganography. International Journal for Research in Applied Science & Engineering Technology (IJRASET).
Roy, Ratnakirti, Suvamoy Changder, Anirban Sarkar, Narayan C Debnat. 2013. Department of computer applications, National institute of technology, Durgapur, India, Department of computer science, Winona state university, MN, USA. Evaluating Image Steganography Techniques: Future Research Challenges, IEEE.
Kanan, Hamidreza Rashidy, Bahram Nazeri. 2014. A novel image steganography scheme with high embedding capacity and tunable visual image quality based on a genetic algorithm. Expert Systems with Applications.
Wang Shen, Bian Yang and Xiamu Niu. 2010. A secure steganography method based on genetic algorithm. Journal of Information Hiding and Multimedia Signal Processing.
Sanjutha, MK. 2018. M.Tech, Computer science engineering, An image steganography using particle swarm optimization and transform domain. International Journal of Engineering & Technology.
Ibrahim Saleh University of Mosul. 2016. Alauddin Al-Omary University of Bahrain, Apply Bee Colony Optimization for Image Steganography with Optical Pixel Adjustment. IJCDS Journal.
Ziyad Tariq Tikrit University. 2017. Ziyad Tariq Mustafa Al-Ta’i University of Diyala-College of Science, Image steganography between firefly and PSO algorithms. International Journal of Computer Science and Information Security.
Yang, X.S. 2010. Firefly Algorithm, Levy Flights and Global Optimization, Research and Development in Intelligent Systems XXVI: Incorporating Applications and Innovations in Intelligent Systems XVII, Springer, London, 209–218.
Vaishali Kulkarni M. S. 2018. Ramaiah University of Applied Sciences, Bengaluru, India, Veena V Desai Gogte Institute of Technology, Raghavendra V. Kulkarni M. S. Ramaiah University of Applied Sciences, Comparison of Firefly, Cultural and the Artificial Bee Colony Algorithms for Optimization, RUAS-SASTech Journal.
Kadhim, Inas Jawad, Prashan Premaratne, Peter James Vial, Brendan Halloran. 2018. Comprehensive survey of image steganography: Techniques, Evaluations and trends in future research, Elsevier.
Ms. Ankita Kadu, Prof. Arun Kulkarni, Prof. Deepali Patil. 2016. Secure data hiding using robust firefly algorithm. International Journal of Computer Engineering In Research Trends.
Kale K.V., Najran N.H. Aldawla, and M.M. Kazi. 2012. Steganography enhancement by combining text and image through wavelet technique. International Journal of computer & Applications (IJCA), 51(21):0975–8887.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Georges, J., Magdi, D.A. (2020). Using Artificial Intelligence Approaches for Image Steganography: A Review. In: Ghalwash, A., El Khameesy, N., Magdi, D., Joshi, A. (eds) Internet of Things—Applications and Future. Lecture Notes in Networks and Systems, vol 114. Springer, Singapore. https://doi.org/10.1007/978-981-15-3075-3_16
Download citation
DOI: https://doi.org/10.1007/978-981-15-3075-3_16
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-3074-6
Online ISBN: 978-981-15-3075-3
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)