Abstract
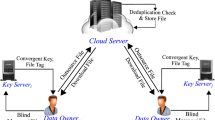
Day by day the usage of smart devices is increasing and communication between devices which improves data growth in cloud storage. The growth of data affects the performance of storage system. The data deduplication system can optimize performance of data storage by eliminating redundant data, reducing storage cost and improves storage utilization. Deduplication technique classified into few types based on that it produces results. Along with that data deduplication performs on encrypted data will be used to prevent unauthorized users from accessing data. Subsequently, various methods perform deduplication (file or block level) safely over encrypted data in cloud. This paper represents different methods which have used different deduplication technique.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
OpenDedup: OpenDedup, global inline deduplication for block storage and files. [Online] 2012 Available from: http://opendedup.org/index.php
Douceur, J., Adya, A., Bolosky, W., Simon, D., Theimer, M.: Reclaiming space from duplicate files in a server less cloud file system. In: Cloud Computing Systems, 2002. Proceedings of 22nd International Conference on IEEE, pp. 617–624 (2002)
Drop Box: http://www.dropbox.com. Tion
AmazonS3: http://aws/amazon.com/s3s
Google Drive: http://www.drive.google.com
SNIA: Advanced deduplication concepts. [Online] 2011. Available from http://www.snia.org/sites/default/education/tutorials/2011/fall/DataProtectionManagement/ThomasRiveria_Advanced_Dedupe_Concepts_FINAL.pdf
Meyer, D.T., Bolosky, W.J.: A study of practical deduplication. ACM Trans. Storage (TOS) 7(4), 14 (2012)
Yang, C., Ma, J., Ren, J.: Provable ownership of encrypted files in de-duplication cloud storage. Ad Hoc Sens. Wireless Netw. 26(1-4), 43–72 (2015)
Li, J., Li, Y.K., Chen, X., Lee, P.P.C., Lou, W.: A hybrid cloud approach for secure authorized deduplication. Parallel CloudSystems Trans. IEEE 26(5), 1206–1216 (2015)
Halevi, S., Harnik, D., Pinkas, B., Shulman-Peleg, A.: Proofs of ownership in remote storage systems. In: Proceedings of ACM Conference on Computer and Communications Security, pp. 491–500 (2011)
Bellare, M., Keelveedhi, S., Ristenpart, T.: Message-locked encryption and secure deduplication. In: Advances in Cryptology–EUROCRYPT 2013, pp. 296–312. Springer, Berlin, Heidelberg (2013)
Miguel, R., Aung, K.M.M.: HEDup: secure deduplication with homomorphic encryption. In: International Conference on Networking, Architecture and Storage (NAS), 2015 IEEE, pp. 215–223 (2015)
Bellare, M., Keelveedhi, S., Ristenpart, T.: DupLess: server-aided encryption for deduplicated storage. In: Proceedings of the 22nd USENIX Conference on Security. USENIX Association (2013)
Chen, R., Mu, Y., Yang, G., Guo, F.: BL-MLE: block-level message-locked encryption for secure large file deduplication. Inf. Forensics Sec. IEEE Trans. 26(12), 2643–2652 (2015)
Puzio, P., Molva, R., Önen, M., Loureiro, S.: ClouDedup: secure deduplication with encrypted data for cloud storage. In: 2013 IEEE 5th International Conference on Cloud Computing Technology and Science (CloudCom), vol. 1, pp. 363–370 (2013)
Bugiel, S., Nurnberger, S., Sadeghi, A., Schneider, T.: Twin clouds: an architecture for secure cloud computing. In: Proceedings of Workshop Cryptography Security Clouds, pp. 32–44 (2011)
Storer, M.W., Greenan, K., Long, D.D.E., Miller, E.L.: Secure data deduplication. In: Proceedings of 4th ACM International Workshop Storage Security Survivability, pp. 1–12 (2008)
Li, J., Chen, X., Huang, X., Tang, S., Xiang, Y., Hassan, M., Alelaiwi, A.H.: Secure cloud deduplication systems with improved reliability. Comput. IEEE Trans. 64(12), 3569–3579 (2015)
Blakley, G.R., Meadows, C.: Security of ramp schemes. Proc. Adv. Cryptol. 196, 242–268 (1985)
Santis, A.D., Masucci, B.: Multiple ramp schemes. IEEE Trans. Inf. Theory 45(5), 1720–1728 (1999)
Zhou, Y., Feng, D., Xia, W., Fu, M., Huang, F., Zhang, Y., Li, C.: SecDep: a user-aware efficient fine- grained secure deduplication scheme with multi-level key management. In: 2015 31st Symposium on Mass Storage Systems and Technologies (MSST), pp. 1–14 (2015)
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Stanek, J., Sorniotti, A., Androulaki, E., Kencl, L.: A secure data deduplication scheme for cloud storage. In: Technology Report IBM Research, Zurich, ZUR 1308-022 (2013)
Li, J., Chen, X., Li, M., Li, J., Lee, P.P.C., Lou, W.: Secure deduplication with efficient and reliable convergent key management. Parallel CloudSyst. IEEE Trans 25(6), 1615–1625 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Mahesh, B., Pavan Kumar, K., Ramasubbareddy, S., Swetha, E. (2020). A Review on Data Deduplication Techniques in Cloud. In: Bhateja, V., Satapathy, S., Satori, H. (eds) Embedded Systems and Artificial Intelligence. Advances in Intelligent Systems and Computing, vol 1076. Springer, Singapore. https://doi.org/10.1007/978-981-15-0947-6_78
Download citation
DOI: https://doi.org/10.1007/978-981-15-0947-6_78
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-0946-9
Online ISBN: 978-981-15-0947-6
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)