Abstract
We first begin with an artificial intelligence approach to crime scenario modelling once a dead body has been found. We then turn to a panoply of contexts and approaches to the processing of human faces: face recognition methods and tools for identification; foreseeing how aging would affect a face (e.g., of a child who went missing); facial expression recognition; digital image forensics (with doctored photographs); facial reconstruction from skeletal remains; and factors in portraiture analysed in the TIMUR episodic formulae model. Having begun with these two major areas (crime scenario modelling, and face processing), we take a broad view of the forensic disciplines of expert opinion, and the sometimes controversial role of statistics in them. We then consider the contribution to forensic science of anthropology and archaeology, as well as software tools for human anatomy. Next, we turn to forensic geology and techniques from geophysics; scent-detection and electronic noses; forensic palynology and its databases; computing in environmental forensics; and forensic engineering. Two large sections, each internally subdivided into nine units, conclude this chapter: “Individual Identification”, and “Bloodstain Pattern Analysis, and the Use of Software for Determining the Angle of Impact of Blood Drops”. The former begins with a history of identification methods, and continues with DNA evidence, and a controversy among statisticians concerning this; we then discuss human fingerprints, and growing skepticism concerning reliability of identification by fingerprints. We then turn to computational techniques for fingerprint recognition, and having surveyed these, we proceed to describe in detail two such techniques.
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsNotes
- 1.
Concerning fact investigation in general, see Binder and Bergman’s book (1984), as well as, e.g., Zander (1979). In a British context, Cook and Tattersall (2008) is a pocket-sized handbook about the processes and actions involved in the role of Senior Investigating Officer. The issues covered comprise, among the other things, crime scene examination and investigative strategies.
- 2.
In the shorter compass of a book chapter, crime scene investigation is the subject of an introductory article by Marilyn Miller (2003, 3rd edn. 2009).
- 3.
- 4.
For this concept, see Dror and Hamard (2009). Baber remarks (2010, p. 424): “While I suggest that Crime Scene Examination necessarily involves several agents performing cognitive activity, this is not to argue that this results in an ‘extended mind’ across these agents; as Dror and Hamard (2009) point out, to argue for an extended mind is analogous to arguing for extended migraine – just because an event occurs in one brain does not inevitably mean that other brains will share this event. Dror and Hamard’s (2009) argument is that one should not separate cognitive states from mental states. This criticism raises a core problem for the notion of ‘Distributed Cognition’, because it implies that cognition cannot be ‘distributed’ across agents because one cannot share mental states. A primary assumption of ‘Distributed Cognition’ is that it is not ‘cognition’ which is distributed so much as objects-in-the-world, which plays a role in supporting, structuring and aiding the activities of cognition.”
- 5.
Baber (2010, p. 430) concedes that there may be problems with striving to be objective by only providing descriptions, in that some useful information may be missed: “One could make a strong argument that this lack of information helps an analysis to be as objective as possible, by focussing only on the item at hand (and avoiding the potential for bias that Dror et al. (2005) demonstrated). On the other hand, it might be useful to have some knowledge of the item in situ, so as to decide how best to conduct analysis. If the Forensic Scientist had recovered the item herself then such information would be recalled by her, but when it is delivered in a batch of bags then such information is not obviously available. As an example of why this could be problematic, consider a finger-mark left on a window. This mark might not be detailed enough to form a print, but could indicate whether the window has been forced up or whether someone climbed down the window, knowing the orientation of the mark on the window can help decide how best to analyse it, but this might not have been provided in the evidence log.”
- 6.
Araucaria is available for free at http://www.computing.dundee.ac.uk/staff/creed/araucaria
- 7.
A definition of association rules as a form of data mining is found in fn. 36 in Chapter 3.
- 8.
Ronald Wright (2005, 2nd edn.; 2009, 3rd death) provides an overview of the investigation of traumatic deaths.
- 9.
In Section 2.1.2 above (see in particular some historical information in fn. 1 in Chapter 1) we have already come across the approach known in artificial intelligence as Assumption-based Truth Maintenance System (ATMS). An ATMS is a mechanism that enables a problem solver to make inferences under different hypothetical conditions, by maintaining the assumptions on which each piece of information and each inference depends (de Kleer, 1986, 1988). The goal of computation with an ATMS is to find minimal sets of premises sufficient for the support of each node. One has to find all minimally inconsistent subsets (NOGOODSs), and to find all maximally consistent subsets (GOODSs).
- 10.
Keppens and Schafer (2006, section 2.1), citing McConville, Saunders, and Leng (1991) and Greer (1994). Once investigators think they already have the culprits, they tend to apply confirmationism, also known as cognitive dissonance, by which they privilege such information that confirm their preconceptions, and tend to disregard contrary evidence. “While the police service might pay lip service to a falsificationist model of rationality (‘asking witnesses to come forward to eliminate them from the inquiry’) existing reward structures make it difficult to implement this in practice. Our proposed system accounts for this by combining a ‘backchaining’ abductivist model of reasoning with a ‘forward chaining’ model that is based on the idea of indirect proof, sidestepping the issue of falsification and induction in a universe with only finitely many alternatives” (Keppens & Schafer, 2006, section 2.2). Forward chaining and its opposite, backchaining, are standard concepts from rule-based knowledge-based systems in artificial intelligence.
- 11.
An example of uncertain state is node n 4, “johndoe was unable to end his hanging”.
- 12.
An example of uncertain event is node n 15, “johndoe asphyxiated”.
- 13.
An example of hypothesis is node n 21, “johndoe’s death was suicidal”.
- 14.
Take for example the syllogism “All men are mortal, and Socrates is a man; therefore Socrates is mortal”. In predicate calculus, the three expressions
$$\begin{array}{c} \forall {\textsf{X} (\textsf{man} (\textsf{X}) \Rightarrow \textsf{mortal}\left(\textsf{X}\right))}.\\ {\textsf{man(socrates)}}. \\ {\textsf{man(socrates)}} \Rightarrow {\textsf{mortal(socrates)}}. \\\end{array}$$respectively stand for “All men are mortal”, “Socrates is a man”, and “Socrates is a man, therefore Socrates is mortal”. Unification is an algorithm that an automated problem solver can use in order to determine that socrates may be substituted for X. For it to apply inference rules, “an inference system must be able to determine when two expressions are the same or match. In propositional calculus, this is trivial: two expressions match if an only if they are syntactically identical. In predicate calculus, the process of matching two sentences is complicated by the existence of variables in the expressions. Universal instantiation allows universally quantified variables [that is: for all X] to be replaced by terms from the domain. This requires a decision process for determining the variable substitutions under which two or more expressions can be made identical (usually for the purpose of applying inference rules). Unification is an algorithm for determining the substitutions needed to make two predicate calculus expressions match” (Luger & Stubblefield, 1998, section 2.3.2., p. 68). “Generally, a problem-solving process will require multiple inferences and, consequently, multiple successive unifications. Logic problem solvers must maintain consistency of variable substitutions. It is important that any unifying substitution be made consistently across all occurrences of the variable in both expressions being matched” (ibid., p. 69). “Once a variable has been bound, future unifications and inferences must take the value of this binding into account. If a variable is bound to a constant, that variable may not be given a new binding in a future unification. If a variable X 1 is substituted for another variable X 2 and at a later time X 1 is replaced with a constant, then X 2 must also reflect this binding” (ibid.). Unification substitutions are combined and returned thanks to the composition of unification substitutions.
- 15.
In the section 5.2.2 in their article, Keppens and Shafer (2006) supplied the formal algorithm for generating the scenario space.
- 16.
Peg unification is useful for coreference resolution. Keppens and Schafer explained (2003b, section 4):
The task of identifying different references to the same entity is known as coreference resolution in computational linguistics. In the analysis of a discourse, it is important that references to the same entity are correctly associated with one another because each of the expressions that contains one of these references may add some information about the entity in question. For example, in the sentence “Every farmer who owns a donkey, beats it.” “a donkey” and “it” refer to the same entity. The first half of the sentence conveys that the entities of interest are all donkeys owned by farmers. The second half of the sentence communicates that the entities of interest are beaten. Thus, the sentence as a whole imparts the knowledge that all donkeys owned by farmers are beaten.
A wide range of techniques has been devised to perform coreference resolution tasks, such as the one illustrated in the example. The vast majority of these techniques specialise in examining texts for discourse analysis or information extraction. An important property of the existing approaches is that they tend to consider only a single possible solution at any one time, while the present problem domain requires a method that can represent and reason with multiple possible worlds simultaneously.
As to pegs (Keppens & Schafer, 2003b, section 4.1):
The objective of this work is to identify possible references to the same unknown or partially specified entities in the scenario space. In order to correctly distinguish such entities, the notion of pegs is adopted from the literature on coreference resolution [(Karttunen, 1976; Landman, 1986)]. Pegs refer to a specific entity whose exact identity remains unknown (or partially specified). In this paper, each peg is identified by an expression of the form _n, where n is a non-negative natural number. At the start of the scenario space generation algorithm n = 0, and n is incremented by 1 after each generation of a new peg. As such, each new peg is identified uniquely.
New pegs may be introduced into the scenario space during the instantiation of causal rules of the form \(\texttt{if} \left\{\textrm{A}_{\textrm{n}} \right\} {\texttt{assuming}}\left\{ A_s \right\} {\texttt{then}}\left\{c\right\}\), where An is a set of antecedent predicates, A s is a set of assumption predicates and c is a consequent predicate. Whenever a rule, whose antecedent or assumption predicates contain variables that do not occur in the consequent sentence, is applied during the inverse modus ponens phase of the scenario space generation algorithm (i.e. step 2), then those variables are instantiated by pegs. Consider, for instance, applying inverse modus ponens on rule
$$\begin{array}{l} \texttt{if} \left\{\textrm{scene}(S)\right\} \texttt{assuming}\left\{person \left(P\right), \textrm{took} \left(P,G\right)\right\} \\ \texttt{then} \left\{\neg {\textrm{evidence}}\left(recover \left(G,S\right)\right)\right\} \\ \end{array}$$given the piece of evidence: ¬evidence(recover(handgun, home(victim))}. The required substitution {G/handgun, S/home(victim)} does not provide an instance for P. Here, P refers to an unknown entity and it is therefore substituted by a peg, say, _0. Therefore, the assumptions person(_0) and took(_0, handgun) are added to the scenario space. Similarly, pegs may also be introduced during the modus ponens phase of the scenario generation algorithm (i.e. step 3). In this case pegs are introduced when a rule whose consequent predicates contain variables that do not occur in the antecedent or assumption sentences, is applied.
Keppens and Schafer (2003b, section 4.2) explained peg unification as follows:
Because a peg refers to an unknown entity, it can be treated as a constant that uniquely identifies that entity, or it can be unified with a ground term, including another peg or terms containing other pegs. In the latter case, the unification is possible if it is hypothesised that the entity represented by the peg and the entity represented by the term unified to the peg are the same one. This hypothesis must therefore be made explicit by means of an assumption whenever an inference is made that depends on the unification of a peg and a ground term. In the remainder of this paper, such assumptions are referred to as peg unification assumptions.
In this paper, each peg unification assumption takes the form bind(_n, t), where _nψ is a peg and t is a ground term (which may include a peg). A peg unification assumption bind(_n,ψt) is added to the scenario space for each pair of predicates that can be matched using a substitution that contains a mapping of the form _n/t.
The binding relation implied by these assumptions is transitive. Therefore, peg unification can not only be assumed, but also be entailed by other peg unification assumptions. This knowledge is represented explicitly in the scenario space: for each pair of peg unification assumptions
$${\textrm{bind}}\left(\_i,\;t_1 \left( \ldots ,\;\_j, \ldots \right)\right)\;\;\;\;\;{\textrm{and}}\;\;\;\;\;{\textrm{bind}}\left(\_j,\;t_2 \left(\ldots ,\;\_k, \ldots \right)\right),$$the following new justification is added to the emerging scenario space:
$$\begin{array}{l} {\textrm{bind}}\left(\_i,\;t1\left( \ldots ,\_{\textrm{j}}, \ldots \right)\right) \wedge {\textrm{bind}}\left(\_j,\;{t2} \left( \ldots ,\_k, \ldots \right)\right) \\ \to {\textrm{bind}}\left(\_i,\;t_1 \left( \ldots ,\;t_2 \left( \ldots ,\_k, \ldots \right), \ldots \right)\right) \\ \end{array}$$Scenario space generation first unifies the relevant sentences (i.e. the consequent of the causal rule during inverse modus ponens, the antecedents of the causal rule during modus ponens, or the inconsistent sentences of the constraint) with nodes in the emerging scenario space, and return the substitution σ required to achieve the unification. Next, scenario space generation records each binding that unifies a peg with a term in the scenario space and a newly created set A p . Then, the process instantiates the remaining sentences (i.e. the antecedents and assumptions during inverse modus ponens or the assumptions and consequent during modus ponens) by applying the substitution σ and the process adds those that do not already exist in the scenario space as new nodes. And finally, scenario space generation generates a justification if applying a causal rule, or a nogood if applying a constraint.
- 17.
Fuzzy approaches are the subject of Section 6.1.15 in this book.
- 18.
There are studies in the psychology of eyewitness testimony that researched the effects of exposure duration on eyewitness accuracy and confidence (e.g., Memon, Hope, & Bull, 2003).
- 19.
- 20.
- 21.
- 22.
- 23.
The E-FIT website is interesting; Amina Memon recommends it in her course handouts: http://www.visionmetric.com/index.php?option=com_content%26;task=view%26;id=17%26;Itemid=25
- 24.
Frowd et al. (2005) presented what they referred to as being a forensically valid comparison of facial composite systems. Brace [sic], Pike, Kemp, Tyrner, and Bennet (2006) discussed whether the presentation of multiple facial composites improves suspect identification. Bruce [sic], Hancock, Newman, and Rarity (2002) had claimed that combining face composites yields improvements in face likeness. McQuiston-Surret, Topp, and Malpass (2006) discussed the use of facila composite systems in the United States. Frowd, McQuiston-Surret, Anandaciva, Ireland, and Hancock (2007) provided an evaluations of some systems for making facial composites, from the United States. Frowd, McQuiston-Surret, et al. (2007) tried to apply caricature in the attempt to improve the recognition of facial composites. Hasel and Wells (2006) claimed that applying morphing to facial composites helps with identifications, but Wells and Charman (2005) had claimed that building composites can harm lineup identification performance.
- 25.
Genetic algorithms are the subject of Section 6.1.16.1 in this book.
- 26.
- 27.
The EvoFIT website is at http://www.evofit.co.uk/ Charlie Frowd’s website is at this other address: http://www.uclan.ac.uk/psychology/research/people/Frowd.html
- 28.
The quotation is from http://www.psychology.stir.ac.uk/staff/cfrowd/index.php ABM is the industrial partner for EvoFIT; they also produce PRO-fit, one of the two facial composite systems used in the UK (the other one is E-FIT).
- 29.
Genetic algorithms are the subject of Section 6.1.16.1 in this book.
- 30.
At http://www.evofit.co.uk/ (accessed in 2010).
- 31.
http://www.aprilage.com “Founded in 1998, Aprilage Development Inc. has developed APRIL® Age Progression Software in association with the Ontario Science Centre and with the support of the National Research Council of Canada. The software is used in more than a dozen countries for health and science education, entertainment and product marketing.”
- 32.
- 33.
Johnson and Farid (2007a, figure 1) gave a poignant example, by showing a fake cover of a celebrity magazine. The original Star magazine cover showed actress Katie Holmes on the right side, with her left hand on the left shoulder of actor Tom Cruise. The cover headline claimed: “Tom & Katie Are They Faking It?”. The fake cover, instead, showed the paper’s first author, Kimo Johnson, in place of Tom Cruise, and the pre-headline read “Kimo & Katie”. One could tell it was fake, however, because there was a shadow on the right side of Kimo’s face, whereas there was mcuh light in the environment (as could be seen from Holmes’ own face, and also from Cruise’s face in the original). In Johnson (2007, p. 26), figure 3.1 shows a “photograph of the American Idol host and judges” which “is a digital composite of multiple photographs. The inconsistencies in the shape and location of the specular highlight on the eyes suggest that these people were originally photographed under different lighting conditions.” Enlarged details show the eyes of the various persons in that photograph.
- 34.
Light probe images by Paul Debevec, available at http://www.debevec.org/Probes.
- 35.
“The standard approaches for estimating light direction begin by making some simplifying assumptions about the surface of interest: (1) it is Lambertian (i.e., it reflects light isotropically); (2) it has a constant reflectance value; (3) it is illuminated by a point light source infinitely far away; and (4) the angle between the surface normal and the light direction is in the range 0°–90°” (Johnson, 2007, p. 7).
- 36.
Flickr home page, at http://www.flickr.com.
- 37.
- 38.
Computational forensics is about what computing can do for forensic science. It should not be mistaken for computer forensics (itself part of digital forensics), i.e., the forensic discipline concerned with illegal actions involving a computer. In a sense, we find here a distinction similar to the one between computational science – i.e., scientific computing: what computing can do for science – and computer science, the science of computing.
- 39.
Nijboer’s (2000) was an overview of current issues in legal evidence. In the tenth anniversary issue of the e-journal International Commentary on Evidence, published at Berkeley in California, Nijboer (2008) provided comparative comments on current issues in evidence and procedure from a Continental perspective, as have emerged during the 2000s. He “discusses three dimensions of generality in evidence and procedure: (1) generality of fundamental issues in evidence and fact-finding and insights about them across national borders, (2) generality of issues of criminal evidence across various relevant disciplines (and professions), and (3) generality with respect to specific issues of criminal evidence and its principles and rules addressing the various probanda of specific crimes (murder, theft, rape, arson, negligence causing a serious traffic accident, et cetera).” Nijboer (2008) made frequent references to case law of the European Court of Human Rights (ECHR).
- 40.
- 41.
There is a literature about expert evidence. For example, Carol Jones (1994) is concerned with expert evidence in Britain.
- 42.
See for example a volume, Forensic Psychology, edited by Joanna Adler (2010, 2nd edn. [originally of 2004]). In that book, section 1, entitled ‘Forensic Psychology in Context’, comprises chapter 1, ‘Forensic psychology: concepts, debates and practice’, by Joanna R. Adler; and chapter 2, ‘Public perceptions of crime and punishment’, by Jane Wood and G. Tendayi Viki. Section 2, ‘Investigation and Prosecution’, comprises chapter 3, ‘USA and UK responses to miscarriages of justice’, by Tom Williamson; chapter 4, ‘The interpretation and utilisation of offender profiles: a critical review of ‘traditional’ approaches to profiling’, by Laurence Alison and Emma Barrett. Section 3, ‘Testimony and Evidence’, comprises chapter 5, ‘Eliciting evidence from eyewitnesses in court’, by Mark R. Kebbell and Elizabeth L. Gilchrist; and chapter 6, ‘The ageing eyewitness’, by Amina Memon, Fiona Gabbert and Lorraine Hope. Section 4, ‘Correlates of Criminality – sensations and substances’, comprises chapter 7, ‘The status of sensational interests as indicators of possible risk’, by Vincent Egan; chapter 8, ‘Drug use and criminal behaviour: indirect, direct or causal relationship?’, by Ian P. Albery, Tim McSweeney and Mike Hough; and chapter 9, ‘Drug arrest referral schemes and forensic perspectives on the treatment of addiction’, by Andrew Guppy, Paul Johnson and Mark Wallace-Bell. Section 5, ‘Persistent Offending’, comprises chapter 10, ‘Life-course persistent offending’, by Alex R. Piquero and Terrie E. Moffitt; and chapter 11, ‘Stalking, Lorraine Sheridan and Graham Davies’. Section 6, ‘Intervention and Prevention’, comprises chapter 12, ‘Domestic violence: current issues in definitions and interventions with perpetrators in the UK’, by Elizabeth L. Gilchrist and Mark Kebbell, chapter 13, ‘Effective programmes to prevent delinquency’, by Brandon C. Welsh and David P. Farrington; and chapter 14, ‘Parenting projects, justice and welfare’, by Anthony H. Goodman and Joanna R. Adler. Section 7, ‘Punishment and Corrections’, comprises chapter 15, ‘Women in prison’, by Nancy Loucks; and chapter 16, ‘Applied psychological services in prisons and probation’, by Graham Towl.
- 43.
For a treatment of the psychology of person identification, see Clifford and Bull (1978). In Bull and Carson (1995), the chapter ‘Assessing the Accuracy of Eye-witness Identifications’ (Cutler & Penrod, 1995) has long been a useful entry point to the subject. Eyewitness psychology (e.g., Loftus, 1974 sqq, Ross et al., 1994) is but one area of forensic psychology. The American Journal of Forensic Psychology was established in the early 1980s; the British Journal of Forensic Psychiatry & Psychology, at the end of that same decade.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
For a U.S. perspective, see Ackerman (1995).
- 50.
- 51.
Also see Hollien (1990), about voice in forensic contexts.
- 52.
Kaye’s (1995) Science and the Detective: Selected Reading in Forensic Science is a useful introduction. Lane, Tingey, and Tingey (1993) is a specialised encyclopaedia, but in a rather popularistic perspective.As to the Encyclopedia of Forensic Sciences (Siegel, Knupfer, & Saukko, 2000), its 1440 pages contain more than 200 articles.
- 53.
Concerning forensic ballistics, http://en.wikipedia.org/wiki/Ballistics states the following: “In the field of forensic science, forensic ballistics is the science of analyzing firearm usage in crimes. It involves analysis of bullets and bullet impacts to determine the type. Rifling, which first made an appearance in the fifteenth century, is the process of making grooves in gun barrels that imparts a spin to the projectile for increased accuracy and range. Bullets fired from rifled weapons acquire a distinct signature of grooves, scratches, and indentations which are somewhat unique to the weapon used. The first firearms evidence identification can be traced back to England in 1835 when the unique markings on a bullet taken from a victim were matched with a bullet mold belonging to the suspect. When confronted with the damning evidence, the suspect confessed to the crime. The first court case involving firearms evidence took place in 1902 when a specific gun was proven to be the murder weapon. The expert in the case, Oliver Wendell Holmes, had read about firearm identification, and had a gunsmith test-fire the alleged murder weapon into a wad of cotton wool. A magnifying glass was used to match the bullet from the victim with the test bullet. Calvin Goddard, physician and ex-army officer, acquired data from all known gun manufacturers in order to develop a comprehensive database. With his partner, Charles Waite, he catalogued the results of test-firings from every type of handgun made by 12 manufacturers. Waite also invented the comparison microscope. With this instrument, two bullets could be laid adjacent to one another for comparative examination. In 1925 Goddard wrote an article for the Army Ordnance titled ‘Forensic Ballistics’ in which he described the use of the comparison microscope regarding firearms investigations. He is generally credited with the conception of the term ‘forensic ballistics’, though he later admitted it to be an inadequate name for the science. In 1929 the St. Valentine’s Day Massacre led to the opening of the first independent scientific crime detection laboratory in the United States.”
- 54.
- 55.
- 56.
- 57.
Those authors themselves were affiliated with the Department of Clothing and Textiles, at the Faculty of Human Ecology of the University of Manitoba in Winnipeg, Canada.
- 58.
- 59.
- 60.
Ward and Duffield (1992) is in a U.S. perspective.
- 61.
Within automotive engineering, Peters and Peters (1994) is relevant for U.S. law.
- 62.
Also see José Almirall’s paper (2001), “Manslaughter Caused by a Hit-and-Run: Glass as Evidence of Association”.
- 63.
Sellier and Kneubuehl (1994) is in forensic ballistics, in a medical context.
- 64.
It is remarkable that there are concise, yet valuable introductions to various forensic science disciplines, posted as entries on Wikipedia. These include a general entry “Forensic science”; various entries from the physiological sciences (“Forensic pathology”, “Forensic dentistry”, “Forensic anthropology”, “Forensic entomology”); entries with affinity to the social sciences (“Forensic psychology”, “Forensic psychiatry”); entries in other specdialisations (“Fingerprint analysis”, “Forensic accounting”, “Ballistics”, “Bloodstain pattern analysis”, “DNA analysis”, “Forensic toxicology”, “Forensic footwear evidence”, “Questioned document examination”, “Explosion analysis”); entries on cybertechnology in forensics (“Information forensics”, “Computer forensics”); entries related to engineering (“Forensic engineering”, “Fire investigation”, “Vehicular accident reconstruction”); entries on people in forensics (“Edmond Locard”, “Bill Bass”); and related articles (“Crime scene”, “CSI effect”, “Trace evidence”). For all of these, see http://en.wikipedia.org/wiki/ followed with the name of the entries, with each blank space replaced with an underscore.
- 65.
Don Foster’s stylometric analysis (see Foster, 2001, chapter 3) was important for identifying the Unabomber. Also the latter’s sister-in-law, a professor of philosophy came to believe she knew he was the Unabomber because of what he wrote and the way he wrote. See in Section 6.1.10, and in fn. 94 in Chapter 6 in particular.
- 66.
- 67.
As http://en.wikipedia.org/wiki/Fire_investigation points out: “Fire investigation is one of the most difficult of the forensic sciences to practice. In most forensic disciplines, even the basic question of whether a crime has been committed is normally obvious. During a fire investigation, an entire process must be undertaken just to determine if the case involves arson or not. The difficulty of determining whether an arson fire has occurred or not arises because fires destroy evidence. A fire investigator looks at what is left behind after a fire and obtains information to piece together the events that occurred in the moments leading up to the fire. One of the challenging aspects of fire investigation is the multi-disciplinary base of the investigator’s job. Fires can be caused by or involve most things people see or use. For this reason, fire investigators need to know not only basic science of fire behavior, but knowledge of many different areas of study (including construction, electricity, human behaviour, vehicles etc.) is helpful. If the fire origin has, for example, a gas appliance, an investigator should know enough about appliances to either include or exclude it as a possible cause of the fire. Fire investigators must also know their own limitations and call upon experts to assist when needed. Accordingly, fire investigators sometimes work with forensic electrical engineers (when examining electrical appliances, household wiring, etc.) or others skilled in forensic engineering (gas-powered appliances, air handling equipment, gas delivery systems, etc.).” Concerning certification of the experts, the same entry explains: “In the USA, some states require that fire investigators obtain certification as a Certified Fire Investigator (CFI). The International Association of Arson Investigators, a professional group of fire investigators, grants CFI certification. The National Association of Fire Investigators (NAFI), a professional association of fire and explosion investigators, offer several National Board Certified fire investigation certifications, including Certified Fire and Explosion Investigatior (CFEI), Certified Vehicle Fire Investigator (CVFI), and Certified Fire Investigation Instructor (CFII). For more information, please visit their website at http://www.nafi.org.”
- 68.
- 69.
See Hunter et al. (1997).
- 70.
Marcella Sorg (2005; 3rd edn. 2009) provides an overview of forensic anthropology.
- 71.
William Haglund (2005; 3rd edn. 2009) provides an overview of forensic taphonomy, which is about burial.
- 72.
Within artificial intelligence, see e.g. Shoham and McDermott (1988) about temporal reasoning.
- 73.
A useful online survey of temporal logic is Galton (2008). van Benthem (1995) is more detailed and more technical; whereas van Benthem (1983, 2nd edn. 1991) is a book on temporal logic. Fisher, Gabbay, and Vila (2005) is a handbook. Cf. Antony Galton’s book (1987) and critique (1990) of James Allen’s theory of action and time. Also consider Alur, Henzinger, Kupferman (2002) alternating-time temporal logic, which eventually gave rise to Wooldridge and van der Hoek’s (2005) Action-based Alternating Transition Systems (AATS), used by Bex et al. (2009) in order to represent reasoning about the narrative of an alleged crime (see Section 3.4.4.4 in this book).
Surveying the broader context of kinds of temporal representations, Fabio Alberto Schreiber explains (1994, section 3): “In the logicians’ community there is a strong debate on the need of creating a non standard Temporal Logic. Scholars having mathematical and physical background and interests claim that times can be designated by terms in a first order theory, which is more than adequate for time modeling. Besides [Bertrand] Russel and [Willard] Quine, these authors – referred often to as detensers – comprise [James] Allen, [Drew] McDermott, [Robert] Kowalski and others. People interested in linguistic aspect of logic, on the other hand, feel that time is tightly woven into languages, under the form of different tenses of the verb, and they relate modal to temporal notions […] [Arthur] Prior and [Georg Hendrik] Von Wright belong to this tensers school. Just to show how things become complicate, we only mention that, in his theory of tense, [Hans] Reichenbach defines three different times for each tense: an utterance time, at which the sentence is expressed, a reference time, which we refer to in the sentence, and an event time, which is the object of the sentence”.
- 74.
- 75.
Also by Anatol Holt, cf. Holt (1971, 1988). In Holt (1988), diplans were introduced, for the purposes of studying coordination in the workplace and of automation. “Diplans are the expressions of a new graphical language used to describe plans of operation in human organizations. With diplans, systems of constraint, which may or may not take the form of procedure definitions, can be specified. Among the special strengths of diplans is their ability to render explicit the interactive aspects of complex work distributed over many people and places – in other words, coordination. Diplans are central to coordination technology, a new approach to developing support for cooperative work on heterogeneous computer networks.” (ibid., from the abstract).
- 76.
- 77.
Nadia Magnenat-Thalmann leads a team in Geneva, whereas Daniel Thalmann leads a team in Lausanne. Cf. in Section 5.2.15 above.
- 78.
At http://www-sop.inria.fr/asclepios/projects/ARCBrainVar/ a description is found of Pennec’s project.
- 79.
- 80.
- 81.
- 82.
Also Fenning and Donnelly (2004) point out that, e.g., coins could be located at depths up to 0.5 m using a sophisticated instrument, but only larger objectsd would be detected if buried deeper (ibid., p. 15).
- 83.
- 84.
http://en.wikipedia.org/wiki/Bullet_time (accessed in March 2007).
- 85.
Wilson and Baietto (2009, p. 5101).
- 86.
http://en.wikipedia.org/wiki/Electronic_nose (when accessed in April 2011, it had been last modified in March of the same year).
- 87.
- 88.
Also see Pearce, Schiffman, Nagle, Nagle, & Gardner’s (2002) Handbook of Machine Olfaction: Electronic Nose Technology.
- 89.
- 90.
- 91.
- 92.
- 93.
- 94.
- 95.
- 96.
Staples (1999).
- 97.
Again in Staples (1999).
- 98.
On pp. 221–245 in Gardner and Bartlett’s (1999) Electronic Noses: Principles and Applications.
- 99.
But nevertheless, olfactometers (when used in one of the senses of that terms) are used to both qualify and quantify. The following is quoted from http://en.wikipedia.org/wiki/Olfactometer
An olfactometer is an instrument typically used to detect and measure ambient odor dilution. Olfactometers are utilized in conjunction with human subjects in laboratory settings, most often in market research, to quantify and qualify human olfaction. Olfactometers are used to gauge the odor detection threshold of substances. To measure intensity, olfactometers introduce an odorous gas as a baseline against which other odors are compared. Many scientists use the term “olfactometer” to refer to a device used to study insect behavior in presence of an olfactory stimulus. It consists of a tube with a bifurcation (with “T” or “Y” shape) where an insect walks and decides between to choices, usually clean air versus air carrying an odor. This is why this device is also called dual choice olfactomenter. Alternatively, an olfactometer is a device used for producing aromas in a precise and controlled manner.
The following sense (as defined ibid.) is unrelated to electronic noses: “A flow-olfactometer is a complex instrument for creation of well defined, reproducible smell or pain stimuli in the nose without tactile or thermal stimulation. Stimulus rise time is fast enough to allow for recording of Olfactory Evoked Potentials (OEPs).” This device “produces a constant heated and humidified flow of pure air. This air flow runs continuously to the subjects nose. For the length of the stimulus pulse the continuous air flow is replaced by a bloc of odorized air” (ibid.). Contrast this to dynamic dilution olfactometers (ibid.):
The new generations of dynamic dilution olfactometers quantify odors using a panel and can allow different complementary techniques:
-
odor concentration and odor threshold determination
-
odor suprathreshold determination with comparison to a reference gas
-
hedonic scale assessment to determine the degree of appreciation
-
evaluation of the relative intensity of odors
-
allow training and automatic evaluation of expert panels
These analyses are often used in site diagnostics (multiple odor sources) performed with the goal of establishing odor management plans.
A concept related to the latter is electrogustometry, i.e., the measurement of taste threshold, i.e., the minimum amount of electrical current required to excite the sensation of taste. When using an electrogustometer, current is made to pass through the tongue, and a metallic taste is perceived. “Electrogustometric taste threshold depends on the duration of current pulse and area of contact of electrode and tongue” (http://en.wikipedia.org/wiki/Electrogustometry).
-
- 100.
http://en.wikipedia.org/wiki/Machine_olfaction (when accessed in April 2011, it had been last modified in February of the same year).
- 101.
As listed at http://en.wikipedia.org/wiki/Electronic_nose tasks of electronic noses within quality control include: conformity of raw materials, as well as of intermediate and final products; batch to batch consistency; detection of contamination, spoilage, or adulteration; origin or vendor selection; and monitoring of storage conditions.
- 102.
Tasks of electronic noses at R&D laboratories include: formulation or reformulation of products; benchmarking with competitive products; shelf life and stability studies; selection of raw materials; packaging interaction effects; simplification of consumer preference test (ibid).
- 103.
Tasks of electronic noses in process and production departments include: managing raw material variability; comparison with a reference product; measurement and comparison of the effects of manufacturing process on products; following-up cleaning in place process efficiency; scale-up monitoring; and the monitoring of cleaning in place (ibid.).
- 104.
- 105.
Ibid.
- 106.
- 107.
- 108.
Ibid.
- 109.
Neural networks are the subject of Section 6.1.14 in this book.
- 110.
Fuzzy logic is the subject of Section 6.1.15 in this book.
- 111.
- 112.
- 113.
Electronic noses for the detection of explosives are the subject of Pamula (2003); Yinon (2003); Gardner and Yinon (2004); Jha and Yadava (2010). Of course, there are venues of research into the detection of explosives, other than resorting to electronic noses. For example, David Moore (2007) provided a survey of advances in trace explosives detection instrumentation. In particular, section 4.2 in Morre (2007) is concerned with vapour concentration methods, and also section 5 is on trace vapour detection. Wang (2004) discussed microchip devices for detecting terrorist weapons. Brenda Klock’s project plan (2001) concerns aviation in the United States: her plan outlined “the field evaluation for threat detection in X-ray images of bags containing explosives at full and subcertification weights” (ibid., from the abstract). “X-ray systems in airports are designed to display images of baggage and its contents, including guns, knives, other weapons, and explosives. X-ray systems include a function designed to maintain on-the-job vigilance. Threat Image Projection (TIP) was developed to increase the proficiency of the primary skills required of a screener to interdict threats at the checkpoint. TIP exposes screeners to images of threats (e.g., weapons or explosives) by randomly projecting these threat images onto passenger bags as the bags move through the X-ray system. Alternately, TIP can also project the image of an entire bag containing a threat when there is a suitable gap between passenger bags” (ibid., p. iv).
- 114.
- 115.
- 116.
Neural networks are the subject of Section 6.1.14 in this book.
- 117.
Also see Persaud’s (2005) ‘Medical applications of odor-sensing devices’.
- 118.
Staples (2000).
- 119.
White, Kauer, Dickinson, and Walt (1996).
- 120.
- 121.
- 122.
On Edmond Locard, a star in the history of French and world criminalistics, see in Section 8.7.1 below.
- 123.
- 124.
- 125.
- 126.
- 127.
- 128.
- 129.
- 130.
- 131.
In Garland, Texas. See the website http://www.pazsoftware.com/
- 132.
At the website http://www.biostratigraphy.com
- 133.
At the website http://www.paleolab.com
- 134.
Accessible at http://www.staff.ncl.ac.uk/stephen.juggins/int_nn.htm
- 135.
James I. Ebert is an envirnmental and forensic scientist who is also a certified photogrammetrist, and a trained archaeologist and anthropologist who has taken part in a project in palaeoanthropology and environmental research at Olduvai Gorge in Tanzania.
- 136.
For eigenvectors, see in fn. 24 in Chapter 6.
- 137.
In James and Nordby (2005, 2nd edn.; 2009, 3rd edn.), a volume on forensic science, the chapters about forensic engineering comprise one about structural failures, by Randall Noon (2005a; 2009a, 3rd edn.), then a chapter about basic fire and explosion investigation, by David Redsicker (2005, 2009, 3rd edn.), and a chapter on vehicular accident reconstruction, by Randall Noon (2005b; 2009b, 3rd edn.).
- 138.
- 139.
- 140.
Around 1980s, such circumstances were still secret, but by 2010, when I was informed verbally, they were in the public domain.
- 141.
E.g., in Goode, Morris, and Wells (1979), a team from the Atomic Weapons Research Establishment of the British Ministry of Defence, based at Aldermaston, Berkshire, described the application of radioactive bromine isotopes for the visualisation of latent fingerprints. A vapour phase bromination procedure was investigated for reaction with unsaturated lipids present in a fingerprint deposit.
- 142.
The light-sensitive chemicals used in photographic film and paper are silver halides. A silver halide is one of the compounds formed between silver and one of the halogens, namely: silver bromide (AgBr), silver chloride (AgCl), silver iodide (AgI), and three forms of silver fluorides. As a group, they are often given the pseudo-chemical notation AgX. Silver halides, except for silver fluoride, are extremely insoluble in water.
“Silver halides are used in photographic film and photographic paper, as well as graphic art film and paper, where silver halide crystals in gelatin are coated on to a film base, glass or paper substrate. The gelatin is a vital part of the emulsion as the protective colloid of appropriate physical and chemical properties. Gelatin may also contain trace elements (such as sulfur) which increase the light sensitivity of the emulsion, although modern practice uses gelatin without such components. When absorbed by an AgX crystal, photons cause electrons to be promoted to a conduction band (de-localized electron orbital with higher energy than a valence band) which can be attracted by a sensitivity speck, which is a shallow electron trap, which may be a crystalline defect or a cluster of silver sulfide, gold, other trace elements (dopant), or combination thereof, and then combined with an interstitial silver ion to form silver metal speck” (http://en.wikipedia.org/wiki/Silver_halide).
Apart from applications to photography, experiments have been conducted for medical purposes: silver halide optical fibres for transmitting mid-infrared light from carbon dioxide lasers, allow laser welding of human tissue, as an alternative to traditional sutures. Another use is in the making of lenses, exploiting photochromism: Silver halides are also used to make corrective lenses darken when exposed to ultraviolet light. “When a silver halide crystal is exposed to light, a sensitivity speck on the surface of the crystal is turned into a small speck of metallic silver (these comprise the invisible or latent image). If the speck of silver contains approximately four or more atoms, it is rendered developable – meaning that it can undergo development which turns the entire crystal into metallic silver. Areas of the emulsion receiving larger amounts of light (reflected from a subject being photographed, for example) undergo the greatest development and therefore results in the highest optical density” (ibid.).
- 143.
The historical origins of identification by fingerprints have been discussed, e.g., by Simon Cole (1999), a criminologist who is prominent among those who question the accuracy, sufficiency, and individuality of fingerprint identification.
- 144.
Berthold Laufer, who was the United States leading Sinologist during the first three decades of the twentieth century, also authored a report on the history of fingerprinting (Laufer, 1913, 1917). Berthold Laufer was born in Cologne, Germany, in 1874. After earning his doctorate at the University of Leipzig in 1874, Berthold Laufer moved on the following year to the United States. He had obtained an invitation to the American Museum of Natural History in New York City, thanks to the famous anthropologist Franz Boas (1858–1942). Laufer eventually became curator of Asiatic Ethnology and Anthropology at the Field Museum of Natural History, Chicago, where he had moved in 1907, leaving a lectureship in Anthropology and East-Asiatic Languages at Columbia University. He died in 1934, upon leaping from the roof of the hotel in which he lived in Chicago, but the mode of his demise goes unmentioned in Latourette’s (1936) biographical memoir of Berthold Laufer for the U.S. National Academy of Sciences.
- 145.
Confirmation bias as occurring in the police interrogation rooms, see e.g. Kassin, Goldstein, and Savitsky (2003), Meissner and Kassin (2002), and Hill, Memon, and McGeorge (2008). Confirmationism is sometimes referred to as cognitive dissonance. This name for the concept was spread by a book by Leon Festinger (1919–1989), A Theory of Cognitive Dissonance (Festinger, 1957).
- 146.
An overview of techniques of DNA analysis is provided by Duncan, Tacey, and Stauffer (2005, 2nd edn.; 2009, 3rd edn.), whereas in the same volume, Susan Herrero (2005, 2nd edn.; 2009, 3rd edn.) provides an overview of legal issues in forensic DNA. DNA fingerprinting is treated, e.g., in Baldin (2005), Inman and Rudin (2002), National Research Council (1996), Stockmarr (1999), Lauritzen and Mortera (2002), Meester and Sjerps (2004), Easteal, McLeod, and Reed (1991), Krawczak and Schmidtke (1994), and Butler (2001). See a brief, yet important debate (Krane et al., 2008), with useful bibliographies by the various commentators, about sequential unmasking in DNA identification. It was republished in http://www.bioforensics.com under the rubric forensic bioinformatics.
- 147.
- 148.
Of course, historically there was interest in ascertaining paternity even before medical knowledge and technology would enable such checks credibly. For example, discussing early modern English midwifery books, Mary Fissell remarks (2003, p. 65): “Midwifery books of the 1670s and 1680s were obsessed by the issues of fatherhood. How could you know the father of a child? In certain circumstances, such as illegitimate births, knowing the father had long been important. These texts devoted much more attention to resemblance between parents and their children than did previous midwifery texts. This crisis in paternity had multiple roots. There was no sudden increase in illegitimate births that might have prompted such an interest. Some of the crisis may be due to longer-term intellectual changes that gradually made similitude a happenstance rather than an indicator of profound connection. No longer did resemblance mean something important about relatedness.” Fissell further explains (ibid., pp. 65–66): “The crisis can also be understood in political terms. In [the] 1670s and 1680s, the question of monarchical succession – the transmission from one generation to another – became ever more pressing. Charles II did not have any legitimate sons, and his brother James’s Catholicism made him a highly problematic successor. The duke of Monmouth’s rebellion (the duke being the king’s illegitimate son), the Rye House Plot, the Popish Plot [i.e., a libel against Catholics leading to executions] – all kept political instability at the forefront of popular awareness. The high politics of legitimate succession moved right into the birthing room in the Warming Pan Baby scandal, which erupted when James II’s wife, Mary of Modena, gave birth a male heir – or did she? She had had eight previous pregnancies, all stillbirths or very short-lived infants. This baby was full-term and healthy, and some observers claimed it was a fraud. They suggested that a healthy baby had been smuggled into the birthing room, concealed in a warming pan, and substituted for Mary’s sickly or stillborn babe.”
From antiquity to the mid eighteenth century, the theory of maternal imagination had currency. It claimed that white parents could have a black child (or vice versa) if the mother, at the time of conception, saw or imagined a man with the other skin colour. A pregnant woman seeing an image of St. John the Baptist wearing hairy skins (or himself hairy) was believed to have given birth to a hairy daughter, who was depicted on the frontispiece of several 17th and early eighteenth century midwifery books. Fissell discussed such imagery. And books sometimes even suggested, Fissell points out, that a woman could deceive her husband by imagining her husband while having intercourse with her lover, so her illegitimate child would resemble her husband rather than her lover.
- 149.
It can be accessed at http://www.ucl.ac.uk/~ucak06d/research.html Philip Dawid’s work on identification evidence, disputed paternity, and in forensic statistics includes Dawid (1994, 1998, 2001a, 2001b, 2002, 2004a, 2005a, 2005b, 2008), Dawid and Mortera (1996, 1998), Dawid and Evett (1997, 1998), Dawid and Pueschel (1999), Dawid et al. (1999, 2001), Dawid, Mortera, Pascali, and van Boxel (2002), Dawid, Mortera, Dobosz, and Pascali (2003), Dawid, Mortera and Vicard (2006), Mortera, Dawid, and Lauritzen (2003), Vicard and Dawid (2004, 2006).
- 150.
- 151.
- 152.
The kind of situations across which one may come is illustrated, e.g., by DNA mixtures: “A mixed DNA profile is typically obtained from an unidentified biological stain or other trace thought to be associated with a crime. This commonly happens in rape cases, in robberies where an object might have been handled by more than one individual, and also in a scuffle of brawl. For a mixed DNA trace there is no constraint on the number of distinct alleles observed for each marker, since the trace might have been formed as a mixture of biological material from more than one person” (Mortera & Dawid, 2006, section 6.3, p. 16).
- 153.
Criticism also comes from critics of the application of probability theory to juridical proof in general, such as Ron Allen: even though one would have thought that DNA evidence would be a “safer” domain for statisticians, it is not quite so. Allen and Pardo (2007a) offered a critique, in terms of the reference-class problem (see Section 2.4 above) of how probability theory was applied to juridical proof concerning DNA random-match evidence in Nance and Morris (2002, 2005).
- 154.
bayesian-evidence@vuw.ac.nz
- 155.
- 156.
Sometimes, the terms fingerprint and fingerprinting are used metaphorically. We have already come across soil fingerprinting techniques in a project in forensic geology that resorts to a decision support system, at the end of Section 8.5.1. In Section 8.5.6, we considered chemical fingerprints, identifying an individual component in a mixture (taken to be a multivariate, mixed chemical system). Another metaphorical use of the term fingerprint is found in digital steganography, a discipline we dealt with in Section 6.2.1.5 (which itself spans more, thematically). One sometimes talks about fingerprints, and a fingerprint vault scheme, in digital steganography: see Li et al. (2005). In forensic ballistics, one speaks of ballistic fingeprinting. Also in intrusion detection within computer security, metaphorically one speaks of fingerprints and fingeprinting (Section 6.2.1.12), in relation to attempts to identify an intruder.
One sometimes speaks of fingerprinting for the identification of an individual rhinoceros. Amin, Bramer, and Emslie (2003) described experiments with “rhino horn fingerprint identification”, i.e., “the identification of the species and origin of illegally traded or confiscated African rhino horn”, using techniques of intelligent data analysis. Rhino horns are akin to compacted hair and fingernails, and their chemical composition refelcts what the animal has been eating throughout its life. In turn, the chemistry of the food is affected by climate and geology. The so-called fingerprint of a rhino horn is a combination of variable values. In the project reported about by Amin et al. (ibid.), Discriminant Function Analysis was the principal technique of data analysis used, the prediction of the category in which a given case belongs is obtained by deriving mathematical functions that provide the greatest possible discrimination among categories. The same paper discussed a further stage, at which it was intended to use artificial neural nets for classification, or the automatic induction of classification trees (for the latter, cf. Quinlan, 1986; Kothari & Dong, 2002; Siroky, 2009; Chen et al., 2011). Contrast the task in the rhino project, to the task of identifying an individual, which is the case of techniques for the recognition of cattle based on characteristics of the animal’s back skin that are akin to fingerprints.
- 157.
A discussion of fingerprint development and imaging, with the chemistry involved in the development explained in clear detail, can be found in an excellent PowerPoint presentation posted online, and authored by Steve Bleay of Britain’s Home Office Scientific Development Branch (Bleay, 2009).
- 158.
- 159.
- 160.
- 161.
On which, see http://en.wikipedia.org/wiki/Henry_Classification_System.
- 162.
Psychologist and anthropologist Francis Galton (1821–1911), Charles Darwin’s cousin.
- 163.
Allegedly, the first edition was a bestseller of Lee and Gaensslen’s (1991) Handbook of Fingerprint Recognition. The second edition, of 2001, is a major revision. A more recent handbook is Handbook of Fingerprint Recognition by Davide Maltoni, Dario Maio, Anil K. Jain, and Salil Prabhakar (2003, 2nd edn. 2009).
- 164.
- 165.
- 166.
Cf. Moenssens (2003).
- 167.
- 168.
The quotation is from the webpage “About the Inquiry: Background” at the site of the inquiry itself, at http://www.thefingerprintinquiryscotland.org.uk/inquiry/23.html
- 169.
Set up under the Inquiries Act 2005, it is one of the first inquiries under that Act to use the Inquiries (Scotland) Rules 2007.
- 170.
The uniqueness claim was rejected by Balding (2005), Cole (2004) and Saks and Koehler (2008). Koehler noted (2008, p. 85): “Kaye (2003) points out the serious flaws in a study that some rely on as proof of fingerprint uniqueness. As for the certainty of fingerprint identifications, the data (not surprisingly) show that fingerprint examiners are fallible. Many commit false-positive and false-negative errors in proficiency tests and in casework (Cole, 2005, 2006a, 2006b). Indeed, some critics argue that there is no scientific reason to believe that fingerprint examiners can make reliable identifications at all (Epstein, 2002).” A bibliography of legal scholarship rejecting the validity of fingerprint identification can be found in the long very last footnote of Cole (2009), and it should be looked up there.
- 171.
Tthe Scientific Working Group on Friction Ridge Analysis, Study and Technology (SWGFAST) was established in 1995, and its mission is to establish consensus guidelines and standards for the forensic examination of friction ridges. See http://www.swgfast.org/ Several resports are posted at that site.
- 172.
AFIS stands for “automated fingerpint identification system”.
- 173.
Incidentally, note that Srihari, Srinivasan, and Beal (2008) discussed the discriminability of the fingerprints of twins. Sargur Srihari’s team at the University of Buffalo is active in both computer-assisted handwriting recognition, and computer-assisted fingerprint recognition.
- 174.
For example, see fn. 177 in Chapter 6.
- 175.
Support vector machines or vector support machines are the subject of Section 6.1.9.3. Moreover, we have said something about support vector machines at the end of Section 6.1.2.3.
- 176.
From Wikipedia (http://en.wikipedia.org/wiki/Gabor_filter). The impulse response of a Gabor filter “is defined by a harmonic function multiplied by a Gaussian function. Because of the multiplication-convolution property (Convolution theorem), the Fourier transform of a Gabor filter’s impulse response is the convolution of the Fourier transform of the harmonic function and the Fourier transform of the Gaussian function. The filter has a real and an imaginary component representing orthogonal directions. The two components may be formed into a complex number or used individually” (ibid.). With the convention that “λ represents the wavelength of the sinusoidal factor, θ represents the orientation of the normal to the parallel stripes of a Gabor function, ψ is the phase offset, σ is the sigma of the Gaussian envelope and γ is the spatial aspect ratio, and specifies the ellipticity of the support of the Gabor function” (ibid.), the Gabor filter is given by the following formulae. As a complex number:
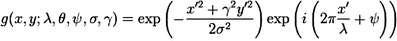
The real component is:

The imaginary component is:

where

and

- 177.
The article by Fasel et al. (2002) “presents a systematic analysis of Gabor filter banks for detection of facial landmarks (pupils and philtrum). Sensitivity is assessed using […] a non-parametric estimate of sensitivity independent of bias commonly used in the psychophysical literature. We find that current Gabor filter bank systems are overly complex. Performance can be greatly improved by reducing the number of frequency and orientation components in these systems. With a single frequency band, we obtained performances significantly better than those achievable with current systems that use multiple frequency bands. […]” (ibid., from the abstract).
- 178.
Cf. Kovács-Vajna, Rovatti, and Frazzoni (2000); Farina, Kovács-Vajna, and Leone (1999); and cf. Zs. Kovács-Vajna, “Method and Device for Identifying Fingerprints”, U.S.A. Patent No. US6,236,741, filing date: 19.02.1997, issued: 22.05.2001; Zs. Kovács-Vajna, “Method and Device for Identifying Fingerprints Using an Analog Flash Memory”, U.S.A. Patent No. US6,330,347, filing date: 28.07.1998, issued: 11.12.2001.
- 179.
Genetic algorithms are the subject of Section 6.1.16.1 in this book.
- 180.
On which, see http://www.javacardforum.org/ See Chen (2000b) about the architecture of Java Card. “Performing a biometric verification inside a smartcard is notoriously difficult, since the processing capabilities of standard smartcard processors are limited for such a complex task. With Match-on-Card (MoC) technology, the fingerprint template is stored inside the card, unavailable to the external applications and the outside world. In addition, the matching decision is securely authenticated by the smartcard itself, in this way, the card has only to trust in itself for eventually unblocking stored sensitive information, such as digital certificates or private keys for digital signature. Our verification MoC algorithm was developed to work in this very strictly bounded environment” (Bistarelli et al., 2006, p. 359).
- 181.
“The algorithm scans sequentially the minutiae of the reference template until a good match for the input minutia is found. Both candidate and reference minutiae lists are stored according to the increasing minutia reliability value: in this way we try to stop the procedure more quickly by scanning a reduced portion of the template minutiae lists. In fact, a minutia with a high reliability in a given template, when not cut away by partial overlapping, will probably have a high reliability also in other templates obtained from the same finger. Thus, the stopping conditions can be met earlier than in a casual disposition of the minutiae in the list. Moreover, it is obviously better to prematurely stop the procedure with few but ‘good’ minutiae than with low quality ones. The minutia of the reference template matched in this way, is then marked as ‘already matched’ and is not considered in the successive iterations.” (Bistarelli et al., 2006, p. 368).
- 182.
Such as the ending of one ridge, and a bifurcation point of two other ridges close by.
- 183.
The orientation difference angle is the difference between two angles, which are each an angle between a horizontal straight line, and the straight line that is tangent to the respective ridge (thus being the central minutia ridge direction) at the given minutia point (such as the ending of the ridge, or a bifurcation point). It is the minutia point being one of the two ends of the segment we mentioned concerning the distance relative angle.
- 184.
- 185.
Bloodstain pattern analysis is the subject of a valuable short introduction by Louis Akin (2005), of books by Tom Bevel and Ross Gardner (2008), and by Stuart James and William Eckert (1999), whereas the book by James et al. (2005a) is more recent (whereas their James et al., 2005b is an overview article about the recognition of bloodstain patterns). MacDonell (1993) is still cited sometimes, in the 2000s, in such studies that also cite more recent literature. Cf. MacDonell and Bialousz (1979). Stuart James also edited a paper collection on the subject (James, 1999). With respect to the second edition of 2002, the third edition of Bevel and Gardner’s book (2008) includes new chapters that “detail a true taxonomic classification system, with a supporting decision map to aid analysts in the field; a specific methodology based on scientific method; conducting experiments in support of bloodstain pattern analysis; anatomical issues associated to bloodstain pattern analysis; issues surrounding the examination of clothing in bloodstain pattern analysis; as well as a chapter detailing the various presumptive testing and enhancement techniques for bloodstains” (ibid., from the summary). The contents of the third edition include: Bloodstain pattern analysis: its function and a historical perspective – Bloodstain pattern terminology – Bloodstain classification – A methodology for bloodstain pattern analysis – The medium of blood – Anatomical considerations in bloodstain pattern analysis – Determining motion and directionality – Determining the point of convergence and the area of origin – Evaluating impact spatter bloodstains – Understanding and applying characteristic patterns of blood – Bloodstained clothing issues – Presumptive testing and enhancement of blood – Documenting bloodstains – An introduction to crime scene reconstruction and analysis [this is also the subject of a book by those same authors: Gardner and Bevel (2009)] – Presenting evidence – Experimentation in bloodstain pattern analysis – Dealing with the risk of bloodborne pathogens – Appendix A weight/measurement conversion table – Appendix B: Trigonometric functions and their application in bloodstain pattern analysis.
- 186.
- 187.
The point of origin is also called the point of hemorrhage. Louis Akin “prefers to use the term point of hemorrhage to distinguish the area from which the blood was disgorged from other points of origin, the latter phrase being a widely used term in blood spatter, ballistics, crime, and accident scene investigation and reconstruction. Although most experts use the word point, the word area is a more conservative one to use” (Akin, 2005, p. 7).
- 188.
The author of MacDonell (1993).
- 189.
The plumb line is parallel to the z axis, in a Euclidean space in three dimensions.
- 190.
190In the public domain; http://en.wikipedia.org/wiki/File:BPA_ellipse_example.png Image made by Kevin Maloney.
- 191.
191In the public domain; http://en.wikipedia.org/wiki/File:BPA_AOI.png Image made by Kevin Maloney.
http://upload.wikimedia.org/wikipedia/en/9/91/BPA_AOI.png is the full resolution version.
- 192.
- 193.
Concerning first responding officers, also called first responders (which strictly speaking is a broader category, as sometimes the earliest responders are members of the public), Miller (2003) writes: “The first responders at a crime scene are usually police officers, fire department personnel or emergency medical personnel. They are the only people who view the crime scene in its original condition. Their actions at the crime scene provide the basis for the successful or unsuccessful resolution of the investigation. They must perform their duties and remember that they begin the process that links victims to suspects to crime scenes and must never destroy the links” (ibid., p. 118).
- 194.
- 195.
195In the public domain; http://en.wikipedia.org/wiki/File:BPA_Origin.gif (animation). Image made by Kevin Maloney in 2005.
- 196.
196In the public domain; http://en.wikipedia.org/wiki/File:BPA_POC.png Image made by Kevin Maloney.
- 197.
197In the public domain; http://en.wikipedia.org/wiki/File:BPA_AOC.png Image made by Kevin Maloney.
- 198.
- 199.
See http://hemospat.com/index.php FORident Software Canada, Inc., 132-207 Bank St., Ottawa, Ontario, Canada K2P 2N2. Their email address is inf@hemospat.com
- 200.
References
Ackerman, M. J. (1995). Clinician’s guide to child custody evaluations. New York: Wiley.
Agur, A., Ng-Thow-Hing, V., Ball, K., Fiume, E., & McKee, N. (2003). Documentation and three-dimensional modelling of human soleus muscle architecture. Clinical Anatomy, 16(4), 285–293.
Akin, L. L. (2004). Blood spatter interpretation at crime and accident scenes: A step by step guide for medicolegal investigators. Austin, TX: On Scene Forensics.
Aitken, C. (1995). Statistics and the evaluation of evidence for forensic scientists. Chichester: Wiley.
Aitken, C., & Taroni, F. (2004). Statistics and the evaluation of evidence. Chichester: Wiley.
Aitken, C., Taroni, F., & Garbolino, P. (2003). A graphical model for the evaluation of cross-transfer evidence in DNA profiles. Theoretical Population Biology, 63(3), 179–190.
Allen, J. F. (1983b). Maintaining knowledge about temporal intervals. Communications of the ACM, 26, 832–843.
Allen, J. F. (1984). Towards a general theory of action and time. Artificial Intelligence, 23(2), 123–154.
Allen, R. J. (1991). The nature of juridical proof. Cardozo Law Review, 13, 373–422.
Allen, R. J., & Pardo, M. S. (2007a). The problematic value of mathematical models of evidence. Journal of Legal Studies, 36, 107–140.
Alur, R, Henzinger, T. A., & Kupferman, O. (2002). Alternating-time temporal logic. Journal of the ACM, 49(5), 672–713.
Anderson, G. S. (2005). Forensic entomology. In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Ardrey, B. (1994). Mass spectrometry in the forensic sciences. (VG Monographs in Mass Spectrometry.) Manchester: Fisons Instruments.
Aulsebrook, W. A., Iscan, M. Y., Slabbert, J. H., & Becker, P. (1995). Superimposition and reconstruction in forensic facial identification: A survey. Forensic Science International, 75(2/3), 101–120.
Baber, C. (2010). Distributed cognition at the crime scene. AI & Society, 25, 423–432. doi://10.1007/s00146 010 0274 6
Baddeley, A. D. (1979). Applied cognitive and cognitive applied psychology: The case of face recognition. In L. G. Nilsson (Ed.), Perspectives on memory research. Hillsdale, NJ: Lawrence Erlbaum Associates.
Balding, D. J. (2005). Weight-of-evidence for forensic DNA profiles. Chichester: Wiley.
Balding, D. J., & Donnelly, P. (1995). Inferring identity from DNA profile evidence. Proceedings of the National Academy of Sciences, USA, 92(25), 11741–11745.
Baldus, D., & Cole, J. W. L. (1980). Statistical proof of discrimination. Colorado Springs, CO: Shepard’s/McGraw-Hill.
Ballim, A., By, T., Wilks, Y., & Liske, C. (2001). Modelling agent attitudes in legal reasoning. Computing and Informatics, 20(6), 581–624.
Ballou, S. (2001). Wigs and the significance of one fiber. Chapter 2 In M. M. Houck (Ed.), Mute witnesses: Trace evidence analysis. London: Academic.
Barnden, J. A. (2001). Uncertain reasoning about agents’ beliefs and reasoning. Artificial Intelligence and Law, 9(2/3), 115–152.
Bauer-Bernet, H. (1986). Temporal aspects of the formalization and computerization of law. In A. A. Martino & F. Socci Natali (Eds.), Automated analysis of legal texts: Logic, informatics, law (pp. 451–472). Amsterdam: North-Holland.
Belfrage, H. (1995). Variability in forensic psychiatric decisions: Evidence for a positive crime preventive effect with mentally disordered violent offenders? Studies in Crime and Crime Prevention, 4(1), 119–123.
Bergslien, E., Bush, P., & Bush, M. (2006). Application of field portable Xray fluorescence (FPXRF) spectrometry in forensic and environmental geology: Theory and examples (abstract). In A. Ruffell (Ed.), Abstract book of geoscientists at crime scenes: First, inaugural meeting of the Geological Society of London, 20 December 2006 (pp. 17–20). London: Forensic Geoscience Group. http://www.geolsoc.org.uk/pdfs/FGtalks&abs_pro.pdf.
Berlière, J.-M. (2005). L’Affaire Scheffer: une victoire de la science contre le crime? La première identification d’un assassin à l’aide de ses empreintes digitales (octobre 1902). Les Cahiers de la sécurité, 56(1), 349–360. Posted at http://www.inhes.interieur.gouv.fr/fichiers/CS56BerliereINHES2005.pdf by the Institut national des hautes études de sécurité (INHES), France.
Bernez, M. O. (1994). Anatomy and aesthetics: Gérard de Lairesse’s illustrations for Bidloo’s Anatomia Humani Corporis. In M. Baridon (Ed.), Interfaces: Image, texte, langage, 5 (pp. 207–229). Dijon, France: Université de Bourgogne.
Best, E., & Hall, J. (1992). The box calculus: A new causal algebra with multilabel communication. (Technical Report Series, 373.) Newcastle upon Tyne, England: University of Newcastle upon Tyne, Computing Laboratory.
Bettini, C., Jajodia, S., & Wang, S. (2000). Time granularities in databases, data mining, and temporal reasoning. Berlin: Springer.
Bettini, C., Wang, X. S., & Jajodia, S. (2002). Solving multi-granularity temporal constraint networks. Artificial Intelligence, 140(1/2), 107–152.
Bevan, B. W. (1991). The search for graves. Geophysics, 56, 1310–1319.
Bevel, T., & Gardner, R. M. (2008). Bloodstain pattern analysis, with an introduction to crime scene reconstruction (3rd ed.). (CRC Series in Practical Aspects of Criminal and Forensic Investigations.) Boca Raton, FL: CRC Press (of Taylor & Francis). The 1st edn. was of 1997, and the 2nd edn. was of 2002.
Bex, F., Bench-Capon, T., & Atkinson, K. (2009). Did he jump or was he pushed? Abductive practical reasoning. Artificial Intelligence and Law, 17(2), 79–99. http://www.computing.dundee.ac.uk/staff/florisbex/Papers/AILaw09.pdf
Biermann, T. W., & Grieve, M. C. (1996). A computerized data base of mail order garments: A contribution toward estimating the frequency of fibre types found in clothing. Part 1: The system and its operation. Part 2: The content of the data bank and its statistical evaluation. Forensic Science International, 77(1/2), 75–92. Amsterdam: Elsevier.
Bistarelli, S., Santini, F., & Vaccarelli, A. (2006). An asymmetric fingerprint matching algorithms for Java CardTM. Pattern Analysis Applications, 9, 359–376. doi://10.1007/s10044 006 0048 4
Boddington, A., Garland, A. N., & Janaway, R. C. (Eds.). (1987). Death, decay and reconstruction: Approaches to archaeology and forensic science. Manchester: Manchester University Press.
Bodziak, W. J. (2005a). Forensic tire impression and tire track evidence. Chapter 18 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Bohan, T. L. (1991). Computer-aided accident reconstruction: Its role in court (SAE Technical Paper Series (12 p.)). Warrendale, PA: Society of Automotive Engineers (SAE).
Bologna, J., & Lindquist, R. J. (1995). Fraud auditing and forensic accounting: New tools and techniques (2nd ed.). New York: Wiley.
Bookspan, S., Gravel, A. J., & Corley, J. (2002). Site history: The first tool of the environmental forensic team. Chapter 2 In B. L. Murphy & R. D. Morrison (Eds.), Introduction to environmental forensics (pp. 19–42). San Diego, CA & London: Academic.
Bowers, M. C. (2002). Forensic dentistry: A field investigator’s handbook. London: Academic.
Brenner, J. C. (2000). Forensic science glossary. Boca Raton, FL: CRC Press.
Brown, C. T. (1989a, June). Relating Petri nets to formulae of linear logic (Internal report, CSR 304 89). Edinburgh, Scotland: Department of Computer Science, University of Edinburgh.
Brown, C. T. (1989b, November). Petri nets as quantales. Internal report, CSR 314 89. Edinburgh, Scotland: Department of Computer Science, University of Edinburgh.
Bruce, V., & Hancock, P. (2002). CRIME-VUs: Combined recall images from multiple experts and viewpoints. Scotland: Department of Psychology, University of Stirling. http://www.stir.ac.uk/Departments/HumanSciences/Psychology/crimevus/index.htm
Bruce, V., Henderson, Z., Greenwood, K., Hancock, P. J. B., Burton, A. M., & Miller, P. I. (1999). Verification of face identities from images captured on video. Journal of Experimental Psychology: Applied, 5(4), 339–360.
Bruce, V., & Young, A. W. (1986). Understanding face recognition. British Journal of Psychology, 77, 305–327.
Bryant, V. M., Jr., & Mildenhall, D. C. (1996). Forensic palynology in the United States of America. Palynology, 14, 193–208.
Bull, R., & Carson, D. (1995). Handbook of psychology in legal contexts. Chichester: Wiley.
Burton, A. M., Bruce, V., & Hancock, P. J. B. (1999). From pixels to people: A model of familiar face recognition. Cognitive Science, 23(1), 1–31.
Burton, A. M., Miller, P., Bruce, V., Hancock, P. J. B., & Henderson, Z. (2001). Human and automatic face recognition: A comparison across image formats. Vision Research, 41, 3185–3195.
Butler, J. M. (2001). Forensic DNA typing: Biology and technology behind STR markers. London: Academic.
Caldwell, C., & Johnston, V. S. (1991). Tracking a criminal suspect through ‘face-space’ with a genetic algorithm. In R. Belew & L. Booker (Eds.), Proceedings of the fourth international conference on genetic algorithms (pp. 416–421). San Mateo, CA: Morgan Kaufmann.
Carter, A. L. (2001a). The directional analysis of bloodstain patterns theory and experimental validation. Canadian Society for Forensic Science Journal, 34(4), 173–189.
Carter, A. L. (2001b). Carter’s compendium for bloodstain analysis with computers: Directional analysis of bloodstain patterns. Ottawa, ON: Forensic Computing of Ottawa Inc. BackTrack Analysis page (electronic book provided with BackTrack Suite).
Carter, A. L., Illes, M., Maloney, K., Yamashita, A. B., Allen, B., Brown, B., et al. (2005). Further Validation of the backtrack™ computer program for bloodstain pattern analysis: Precision and accuracy. IABPA News,54 21(3), 15–22.
Catts, E. P., & Goff, M. L. (1992). Forensic entomology in criminal investigations. Annual Review of Entomology, 37, 253–272.
Catts, E. P., & Haskell, N. H. (1990). Entomology & death: A procedural guide. Clemson, SC: Joyce’s Print Shop.
Champod, C. (1995). Edmond Locard – Numerical standards and ‘probable’ identifications. Journal of Forensic Identification, 45, 136–163.
Champod, C., Lennard, C., Margot, P., & Stilovic, M. (2004). Fingerprints and other ridge skin impressions. Boca Raton, FL: CRC Press.
Chen, X., Wang, M., & Zhang, H. (2011). The use of classification trees for bioinformatics. Wiley Interdisciplinary Reviews (WIREs): Data Mining and Knowledge Discovery, 1(1), 55–63. doi://10.1002/widm.14
Chen, Z. (2000b). Java card technology for smart cards: Architecture and programmer’s guide. Boston: Addison-Wesley.
Cherry, M., & Imwinkelried, E. J. (2006). A cautionary note about fingerprint analysis and reliance on digital technology. Judicature, 89, 334–338.
Chiswick, D., & Cope, R. (Eds.). (1995). Seminars in practical forensic psychiatry. (Royal College of Psychiatrists, College Seminars Series.) London: Gaskell.
Clark, M., & Crawford, C. (Eds.). (1994). Legal medicine in history. Cambridge History of Medicine. Cambridge: Cambridge University Press.
Clarke, P. H. (1985). The surveyor in court. London: Estates Gazette.
Clements, R. V. (1994). Safe practice in obstetrics and gynaecology: A medico-legal handbook. Edinburgh: Churchill Livingstone.
Clifford, B., & Bull, R. (1978). The psychology of person identification. London: Routledge.
Cohn, A. G., Gotts, N. M., Cui, Z., Randell, D. A., Bennett, B., & Gooday, J. M. (1994). Exploiting temporal continuity in qualitative spatial calculi. In R. G. Golledge & M. J. Egenhofer (Eds.), Spatial and temporal reasoning in geographical information systems. Amsterdam: Elsevier.
Cole, D. J., & Ackland, P. R. (1994). The detective and the doctor: A murder casebook. London: Hale.
Cole, S. A. (1999). What counts for identity? The historical origins of the methodology of latent fingerprint identification. Science in Context,55 12, 139–172.
Cole, S. A. (2001). Suspect identities: A history of fingerprinting and criminal identification. Cambridge, MA: Harvard University Press.
Cole, S. A. (2004). Grandfathering evidence: Fingerprint admissibility rulings from Jennings to Llera Plaza and back again. American Criminal Law Review, 41, 1189–1276.
Cole, S. A. (2005). More than zero: Accounting for error in latent print identification. Journal of Criminal Law and Criminology, 95, 985–1078.
Cole, S. A. (2006a). The prevalence and potential causes of wrongful conviction by fingerprint evidence. Golden Gate University Law Review, 37, 39–105.
Cole, S. A. (2006b). Is Fingerprint identification valid? Rhetorics of reliability in fingerprint proponents’ discourse. Law Policy, 28, 109–135.
Cole, S. A. (2009). Daubert revisited. Don’t shoot the messenger by one of the messengers: A response to Merlino et al. Tulsa Law Review, 45, 111–132. http://www.tulsalawreview.com/wp content/uploads/2010/10/Cole.Final_.pdf
Cole, S. A., Welling, M., Dioso-Villa, R., & Carpenter, R. (2008). Beyond the individuality of fingerprints: A measure of simulated computer latent print source attribution accuracy. Law, Probability and Risk, 7, 165–189.
Cone, E. J., & Deyl, Z. (Eds.). (1992). Toxicology and forensic applications. Special issue, Journal of Chromatography, B: Biomedical Applications, 580(1/2). Amsterdam: Elsevier.
Console, L., & Torasso, P. (1991). A spectrum of logical definitions of model-based diagnosis. Computational Intelligence, 7(3), 133–141.
Cook, R., Evett, I., Jackson, G., Jones, P., & Lambert, J. (1998). A model for case assessment and interpretation. Science and Justice, 38, 151–156.
Cook, T., & Tattersall, A. (2008). Blackstone’s senior investigating officer’s handbook. Oxford: Oxford University Press.
Cox, M., & Mays, S. (Eds.). (2000). Human osteology in archaeology and forensic science. London: Greenwich Medical Media.
Cummins, H., & Midlo, C. (1943). Finger prints, palms and soles: An introduction to dermatoglyphics. Philadelphia, PA: Blakiston.
Cutler, B. L., & Penrod, S. D. (1995). Assessing the accuracy of eye-witness identifications. Chapter 3.3 In R. Bull & D. Carson (Eds.), Handbook of psychology in legal contexts (pp. 193–213). Chichester: Wiley.
Davenport, G. C., France, D. L., Griffin, T. J., Swanburg, J. G., Lindemann, J. W., Tranunell, V., et al. (1992). A multidisciplinary approach to the detection of clandestine graves. Journal of Forensic Science, 37(6), 1445–1458. (Also, posted at http://www.terraplus.ca/case histories/dave1.htm)
David, R., & Alla, H. (1992). Petri nets and grafcet: Tools for modelling discrete event systems. New York: Prentice Hall. Translation of: Du Grafcet aux reseaux de Petri.
Davide, F. A. M., Di Natale, C., & D’Amico, A. (1995). Self-organizing sensory maps in odour classification mimicking. Biosensors and Bioelectronics, 10, 203–218.
Davies, G. M., & Christie, D. (1982). Face recall: An examination of some factors limiting composite production accuracy. Journal of Applied Psychology, 67(1), 103–109.
Davies, G. M., Ellis, H. D., & Shepherd, J. W. (1978). Face identification: The influence of delay upon accuracy of Photofit construction. Journal of Police Science and Administration, 6(1), 35–42.
Allen, R. J. (2008a). Explanationism all the way down. Episteme, 3(5), 320–328.
Davies, G. M, Ellis, H. D., & Shepherd, J. W. (1981). Perceiving and remembering faces. New York: Academic.
Dawid, A. P. (1994). The island problem: Coherent use of identification evidence. Chapter 11 In P. R. Freeman & A. F. M. Smith (Eds.), Aspects of uncertainty: A tribute to D. V. Lindley (pp. 159–170). Chichester: Wiley.
Dawid, A. P. (2001a). Comment on Stockmarr’s ‘Likelihood ratios for evaluating DNA evidence when the suspect is found through a database search’ (with response by A. Stockmarr). Biometrics, 57, 976–980.
Dawid, A. P. (2004a). Which likelihood ratio? (Comment on ‘Why the effect of prior odds should accompany the likelihood ratio when reporting DNA evidence’, by R. Meester & M. Sjerps). Law, Probability and Risk, 3, 65–71.
Dawid, A. P. (2005b). Probability and proof. On-line Appendix to Analysis of evidence (2nd ed., pp. 119–148), by T. J. Anderson, D. A. Schum, & W. L. Twining. Cambridge: Cambridge University Press. Posted at http://tinyurl.com/7g3bd, 94 pp.
Dawid, A. P. (2008). Statistics and the law. In A. Bell, J. Swenson-Wright, & K. Tybjerg (Eds.), Evidence. Cambridge.: Cambridge University Press, pp. 119–148. Also: Research Report 244, May 2004, Department of Statistical Science, University College London, May 2004.
Dawid, A. P., & Evett, I. W. (1997). Using a graphical method to assist the evaluation of complicated patterns of evidence. Journal of Forensic Science, 42, 226–231.
Dawid, A. P., & Mortera, J. (1996). Coherent analysis of forensic identification evidence. Journal of the Royal Statistics Society, B, 58, 425–443.
Dawid, A. P., & Mortera, J. (1998). Forensic identification with imperfect evidence. Biometrika, 85, 835–849. Correction: Biometrika, 86 (1999), p. 974.
Dawid, A. P., Mortera, J., Dobosz, M., & Pascali, V. L. (2003). Mutations and the probabilistic approach to incompatible paternity tests. In B. Brinkmann & A. Carracedo (Eds.), Progress in forensic genetics 9: Proceedings from the 19th congress of the international society for forensic haemogenetics (pp. 637–638). (International Congress Series, Vol. 1239.) Amsterdam: Elsevier Science.
Dawid, A. P., Mortera, J., & Pascali, V. L. (2001). Non-fatherhood or mutation? A probabilistic approach to parental exclusion in paternity testing. Forensic Science International, 124, 55–61.
Dawid, A. P., Mortera, J., & Vicard, P. (2010). Paternity testing allowing for uncertain mutation rates. In A. O’Hagan & M. West (Eds.), The Oxford handbook of applied bayesian analysis (pp. 188–215). Oxford: Oxford University Press.
Dawid, A. P., & Pueschel, J. (1999). Hierarchical models for DNA profiling using heterogeneous databases (with Discussion). In J. M. Bernardo, J. O. Berger, A. P. Dawid, & A. F. M. Smith (Eds.), Bayesian statistics 6 (pp. 187–212). Oxford: Oxford University Press.
Dawid, A. P., van Boxel, D. W., Mortera, J., & Pascali, V. L. (1999). Inference about disputed paternity from an incomplete pedigree using a probabilistic expert system. Bulletin of the International Statistics Institute, 58, 241–242. Contributed Papers Book 1.
Dawson, L., Macdonald, L., Ball, J., & “other members of the SoilFit team”. (2006). Integration of soil fingerprinting techniques for forensic application (abstract). In A. Ruffell (Ed.), Abstract book of geoscientists at crime scenes: First, inaugural meeting of the Geological Society of London, 20 December 2006 (p. 23). London: Forensic Geoscience Group. http://www.geolsoc.org.uk/pdfs/FGtalks&abs_pro.pdf.
Deedrick, D. W. (2001). Fabric processing and “nubs”. Chapter 1 In M. M. Houck (Ed.), Mute witnesses: Trace evidence analysis. London: Academic.
de Kleer, J. (1986). An assumption-based TMS. Artificial Intelligence, 28, 127–162.
Dixon, D. (1999). Police investigative procedures. In C. Walker & K. Starmer (Eds.), Miscarriage of justice: A review of justice in error (2nd ed.). London: Blackstone Press.
Donnelly, L. J. (2002a, May). Finding the silent witness. Geoscientist, 12(5), 16–17. The Geological Society of London.
Donnelly, L. J. (2003, December). The applications of forensic geology to help the police solve crimes. European Geologist: Journal of the European Federation of Geologists, 16, 8–12.
Donnelly, L. J. (2004, March–April). Forensic geology: The discovery of spades on Saddleworth Moor. Geology Today, 20(2), 42. Oxford: Blackwell.
Donnelly, L. J. (2006). Introduction & welcome. In A. Ruffell (Ed.), Abstract book of geoscientists at crime scenes: First, inaugural meeting of the Geological Society of London, 20 December 2006 (pp. 3–5). London: Forensic Geoscience Group. http://www.geolsoc.org.uk/pdfs/FGtalks&abs_pro.pdf
Dror, I., & Hamard, S. (2009). Cognition distributed: How cognitive technology extends our minds. Amsterdam: Benjamins.
Dror, I. E., & Charlton, D. (2006). Why experts make errors. Journal of Forensic Identification, 56, 600–616. http://www.bioforensics.com/sequential_unmasking/Dror_Errors_JFI.pdf
Dror, I. E., Charlton, D., & Péron, A. (2006). Contextual information renders experts vulnerable to making erroneous identifications. Forensic Science International, 156, 74–78. http://www.bioforensics.com/sequential_unmasking/Dror_Contextual_FSI_2006.pdf
Dror, I. E., Péron, A., Hind, S.-L., & Charlton, D. (2005). When emotions get the better of us: The effect of contextual top-down processing on matching fingerprints. Applied Cognitive Psychology, 19(6), 799–809. http://www.bioforensics.com/sequential_unmasking/Dror_emotions.pdf
Dror, I. E., & Rosenthal, R. (2008). Meta-analytically quantifying the reliability and biasability of forensic experts. Journal of Forensic Sciences, 53(4), 900–903. http://www.bioforensics.com/sequential_unmasking/dror_meta analysis_JFS_2008.pdf
Duncan, G. T., Tacey, M. L., & Stauffer, E. (2005). Techniques of DNA analysis. In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Easteal, S., McLeod, N., & Reed, K. (1991). DNA profiling: Principles, pitfalls and potential. Chur, Switzerland: Harwood.
Ebert, J. I. (2002). Photogrammetry, photointerpretation, and digital imaging and mapping in environmental forensics. Chapter 3 In B. L. Murphy & R. D. Morrison (Eds.), Introduction to environmental forensics (pp. 43–69). San Diego, CA & London, U.K.: Academic.
Eckert, W. G., & James, S. H. (1993). Interpretation of bloodstain evidence at crime scenes. Boca Raton, FL: CRC Press. [Later, Eckert & James (1999).]
Egashira, M., & Shimizu, Y. (1993). Odor sensing by semiconductor metal oxides. Sensors & Actuators, 14, 443–446.
Egeland, T., Mostad, P., & Olaisen, B. (1997). A computerised method for calculating the probability of pedigrees from genetic data. Science & Justice, 37(4), 269–274. http://www.nr.no/~mostad/pater
Eigen, J. P. (1995). Witnessing insanity: Madness and mad-doctors in the English court. New Haven, CT: Yale University Press.
Ellis, H. D., Davies, G. M., & Shepherd, J. W. (1986). Introduction: Processes underlying face recognition. In R. Bruyer (Ed.), The neuropsychology of face perception and facial expression (pp. 1–38). Hillsdale, NJ: Lawrence Erlbaum Associates.
Ellis, H. D., Shepherd, J. W., & Davies G. M. (1975). An investigation of the use of the Photofit technique for recalling faces. British Journal of Psychology, 66(1), 29–37.
Epstein, R. (2002). Fingerprints meet Daubert: The myth of fingerprint “science” is revealed. Southern California Law Review, 75, 605–657.
Esparza, J., & Bruns, G. (1994). Trapping mutual exclusion in the box calculus. (LFCS Report Series, ECS LFCS 94 295.) Edinburgh, Scotland: LFCS, Department of Computer Science, University of Edinburgh.
Evett, I. W., & Williams, R. L. (1996). A review of the sixteen points fingerprint standard in England and Wales. Journal of Forensic Identification, 46, 49–73.
Faegri, K., & Iversen, J. (1989). Textbook of pollen analysis. Fourth Edition by K. Faegri, P. E. Kaland, & K. Krzywinski. New York: Wiley. First edition, Copenhagen: Munksgaars, 1950.
Falkenhainer, B., & Forbus, K. (1991). Compositional modeling: finding the right model for the job. Artificial Intelligence, 51, 95–143.
Farina, A., Kovács-Vajna, Z. M., & Leone, A. (1999). Fingerprint minutiae extraction from skeletonized binary images. Pattern Recognition, 32(5), 877–889.
Faulk, M. (1994). Basic forensic psychiatry (2nd ed.). Oxford: Blackwell Scientific.
Fernandez, C., & Best, E. (1988). Nonsequential processes: A petri net view (EATCS Monographs on Theoretical Computer Science, 13). Berlin: Springer.
Festinger, L. (1957). A theory of cognitive dissonance. Evanston, IL: Row Peterson. Reissues of the same edition, Stanford, California: Stanford University Press, 1962, 1970; London: Tavistock Publications, 1962. Revised and enlarged German translation: Theorie der kognitiven Dissonanz (1978).
Field, D., & Raitt, F. (1996). Evidence. Edinburgh, Scotland: W.Green.
Finkelstein, M. (1978). Quantitative methods in law. New York: The Free Press.
Finkelstein, M. (1980). The judicial reception of multiple regression studies in race and sex discrimination cases. Columbia Law Review, 80, 737–754.
Finkelstein, M. O., & Levin, B. (2003). On the probative value of evidence from a screening search. Jurimetrics Journal, 43, 265–290.
Firestein, S. (2001). How the olfactory system makes sense of scents. Nature, 413, 211–218.
Fisher, M., Gabbay, D., & Vila, L. (Eds.). (2005). Handbook of temporal reasoning in artificial intelligence (electronic resource; Foundations of Artificial Intelligence, 1). Amsterdam: Elsevier.
Foster, D. (2001). Author unknown: On the trail of anonymous. London: Macmillan; with respect to New York: Holt, 2000, the U.K. edition is corrected, and includes as well the new Ch. 7, on current British journalism.
Frank, P. B., Wagner, M. J., & Weil, R. L. (1994). Litigation services handbook: The role of the accountant as expert witness. 1994 cumulative supplement. New York: Wiley.
Franke, K., & Srihari, S. N. (2008). Computational forensics: An overview. In Computational forensics: Proceedings of the international workshop, Washington, DC (pp. 1–10). (Lecture Notes in Computer Science, 5158). Berlin: Springer.
Freund, M. S., & Lewis, N. S. (1995). A chemically diverse conducting polymer-based electronic nose. Proceedings of the National Academy of Sciences USA, 92, 2652–2656.
Frowd, C. D., Bruce, V., & Hancock, P. J. B. (2008). Changing the face of criminal identification. The Psychologist, 21, 670–672.
Frowd, C. D., Carson, D., Ness., H., Richardson, Morrison, L., McLanaghan, S., et al. (2005). A forensically valid comparison of facial composite systems. Psychology, Crime & Law, 11, 33–52.
Frowd, C. D., Hancock, P. J. B., & Carson, D. (2004). EvoFIT: A holistic, evolutionary facial imaging technique for creating composites. ACM Transactions on Applied Psychology (TAP), 1, 1–21.
Frowd, C. D., McQuiston-Surret, D., Anandaciva, S., Ireland, C. G. & Hancock, P. J. B. (2007). An evaluation of US systems for facial composite production. Ergonomics, 50, 187–198.
Fu, X., Boongoen, T., & Shen, Q. (2010). Evidence directed generation of plausible crime scenarios with identity resolution. Applied Artificial Intelligence, 24(4), 253–276.
Full, W. E., Ehrlich, R., & Bezdek, J. C. (1982). Fuzzy QModel: A new approach for linear unmixing. Journal of Mathematical Geology, 14, 259–270.
Full, W. E., Ehrlich, R., & Klovan, J. E. (1981). Extended Qmodel [sic]: Objective definition of external end members in the analysis of mixtures. Journal of Mathematical Geology, 13, 331–344.
Gaffney, C., & Gater, J. (2003). Revealing the buried past: Geophysics for archaeologists. Gloucester: Tempus Publishing.
Gardner, J. W. (1991). Detection of vapours and odours from a multisensor array using pattern recognition: Principal component and cluster analysis. Sensors & Actuators, 4, 109–115.
Gardner, R. M., & Bevel, T. (2009). Practical crime scene analysis and reconstruction. With contributions by M. Noedel, S. A. Wagner, & I. Dalley. (CRC Series in Practical Aspects of Criminal and Forensic Investigations.) Boca Raton, FL: CRC Press.
Garrett, R. E. (1987). The overlooked business aspects of forensic engineering. Forensic Engineering, 1(1), 17–19.
Gastwirth, J. L., & Miao, W. (2009). Formal statistical analysis of the data in disparate impact cases provides sounder inferences than the U.S. government’s ‘four-fifths’ rule: An examination of the statistical evidence in Ricci v. DeStefano. Law, Probability and Risk, 8, 171–191. doi:10.1093/lpr/mgp017
Geddes, L. (2010, August 21). What are the chances? ([pre-headline:] Special report: DNA evidence; [subheadline:] In the second part of our investigation, Linda Geddes shows that the odds attached to a piece of DNA evidence can vary enormously). New Scientist, 207(2274), 8–10. With an inset: ‘When lawyers question DNA’, on p. 9.
Gemperline, P. J. (1984). A priori estimates of the elution [sic] profiles of pure components in overlapped liquid chromatography peaks using target transformation factor analysis. Journal of Chemical Information and Computer Sciences, 24, 206–212.
Genrich, H., & Lautenbach, K. (1979). Predicate/transitions nets. In W. Brauer (Ed.), Net theory and application (Lecture Notes in Computer Science, 84). Berlin: Springer.
Geradts, Z. (2005). Use of computers in forensic science. Chapter 26 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Gerasimov, M. (1971). The face finder. London: Hutchinson.
Gibson, J. J. (1977). The theory of affordances. In R. Shaw & J. Bransford (Eds.), Perceiving, acting and knowing (pp. 67–82). Hillsdale, NJ: Erlbaum.
Gibson, J. J. (1979). The ecological approach to visual perception. Hillsdale, NJ: Erlbaum.
Gibson, S. J., Solomon, C. J., Maylin, M. I. S., & Clark, C. (2009). New methodology in facial composite construction: From theory to practice. International Journal of Electronic Security and Digital Forensics, 2, 156–168.
Glass, R. T. (2005). Forensic odontology. Chapter 6 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Goldstein, A. G., & Chance, J. E. (1981). Laboratory studies of face recognition. In G. Davies, H. Ellis, & J. Shepherd (Eds.), Perceiving and remembering faces (pp. 81–104). New York: Academic.
González Ballester, M. A., Büchler, P., & Reimers, N. (2007). Combined statistical model of bone shape and biomechanical properties for evidence-based orthopaedic implant design. In The Digital Patient, special issue of ERCIM News, 69 (April), 27–28. Accessible at the webpage http://ercim news.ercim.org/ of the European Research Consortium for Informatics and Mathematics.
Goode, G. C., Morris, J. R., & Wells, J. M. (1979). The application of radioactive bromine isotopes for the visualisation of latent fingerprints. Journal of Radioanalytical [and Nuclear] Chemistry, 48(1/2), 17–28.
Greer, S. (1994). Miscarriages of criminal justice reconsidered. Modern Law Review, 58, 71.
Gunn, J., & Taylor, P. J. (1993). Forensic psychiatry: Clinical, legal and ethical issues. Oxford & Boston: Butterworth-Heinemann.
Gutés, A., Céspedes, F., & del Valle, M. (2007). Electronic tongues in flow analysis. Analytica Chimica Acta, 600, 90–96.
Gutiérrez, M., García-Rojas, A., Thalmann, D., Vexo, F., Moccozet, L., Magnenat-Thalmann, N., et al. (2007). An ontology of virtual humans: Incorporating semantics into human shapes. The Visual Computer, 23(3), 207–218.
Haber, L., & Haber, R. N. (2003). Error rates for human fingerprint examiners. In N. K. Ratha & R. Bolle (Eds.), Automatic fingerprint recognition systems (pp. 339–360). New York: Springer.
Haber, L,. & Haber, R. N. (2006). Letter Re: A report of latent print examiner accuracy during comparison training exercises. Journal of Forensic Identification, 56, 493–499.
Haber, L., & Haber, R. N. (2008). Scientific validation of fingerprint evidence under daubert. Law, Probability and Risk, 7, 87–109.
Haglund, W. D. (2005). Forensic taphonomy. Chapter 8 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Hammersley, R., & Read, J. D. (1993). Voice identification by humans and computers. In S. L. Sporer, R. S. Malpass, & G. Köhnken (Eds.), Suspect identification: Psychological knowledge, problems and perspectives. Hillsdale, NJ: Lawrence Erlbaum Associates.
Hammon, W. S., McMechan, G. A., & Zeng, X. (2000). Forensic GPR-finite-difference simulation of responses from buried remains. Journal of Applied Geophysics, 45, 171–186.
Hamscher, W., Console, L., & de Kleer, J. (Eds.). (1992). Readings in model-based diagnosis. San Mateo, CA: Morgan-Kaufmann.
Hancock, P. J. B. (2000). Evolving faces from principal components. Behaviour Research Methods, Instruments and Computers, 32(2), 327–333.
Hancock, P. J. B., Bruce, V., & Burton, A. M. (1998). A comparison of two computer-based face recognition systems with human perceptions of faces. Vision Research, 38, 2277–2288.
Hancock P. J. B., Bruce, V., & Burton, A. M. (2000). Recognition of unfamiliar faces. Trends in Cognitive Sciences, 4(9), 330–337.
Hancock, P. J. B., & Frowd, C. D. (2001). Evolutionary generation of faces. In P. J. Bentley & D. W.Corne (Eds.), Creative evolutionary systems. London: Academic.
Hasel, L. E., & Wells, G. L. (2006). Catching the bad guy: Morphing composite faces helps. Law and human Behavior, 31, 193–207.
Hatfield, J. V., Neaves, P., Hicks, P. J., Persaud, K. C., & Tavers, P. (1994). Toward an integrated electronic nose using conducting polymer sensors. Sensors & Actuators, 18, 221–228.
Hauser, K., & Ng-Thow-Hing, V. (2010). Randomized multi-modal planning for precision pushing on a humanoid robot. Chapter 9 In K. Harada, E. Yoshida, & K. Yokoi (Eds.), Motion planning for humanoid robots (pp. 251–276). Berlin: Springer.
Henry, R. C., & Kim, B. M. (1990). Extension of self-modeling curve resolution to mixtures of more than three components. Part 1: Finding the basic feasible region. Chemometrics and intelligent Laboratory Systems, 8, 205–216.
Herrero, S. (2005). Legal issues in forensic DNA. In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Hildebrand, J. A., Wiggins, S. M., Henkart, P. C., & Conyers, L. B. (2002). Comparison of seismic reflection and ground penetrating radar imaging at the controlled archaeological test site, Champaign, Illinois. Archaeological Prospection, 9, 9–21.
Hill, C., Memon, A., & McGeorge, P. (2008). The role of confirmation bias in suspect interviews: A systematic evaluation. Legal & Criminological Psychology, 13, 357–371.
Hoare, C. A. R. (1985). Communicating sequential processes. (Prentice Hall Series in Computer Science). Hemel Hempstead, Hertfordshire, England: Prentice Hall.
Hohns, H. M. (1987). The place of forensics in engineering. Forensic Engineering, 1(1), 3–5.
Hollien, H. F. (1990). The acoustics of crime: The new science of forensic phonetics. New York: Plenum.
Holt, A. W. (1971). Introduction to occurrence systems. In E. L. Jacks (Ed.), Associative information techniques (pp. 175–203). New York: American Elsevier.
Holt, A. W. (1988). Diplans: A new language for the study and implementation of coordination. ACM Transactions on Information Systems (TOIS), 6(2), 109–125.
Holt, A. W., & Meldman, J. A. (1971). Petri nets and legal systems. Jurimetrics, 12(2), 65–75.
Hopke, P. K. (1989). Target transformation factor analysis. Chemometrics and Intelligent Laboratory Systems, 6, 7–19.
Houck, M. M. (1999). Statistics and trace evidence: The tyranny of numbers. Forensic Science Communications, 1(3), 1–8.
Hunter, J. R., Roberts, C., & Martin, A. (with Heron, C., Knupfer, G. and Pollard, M.). (1997). Studies in crime: An introduction to forensic archaeology. London: Batsford, 1995, 1996; London: Routledge, 1997.
Hutchinson, J. R., Ng-Thow-Hing, V., & Anderson, F. C. (2007). A 3D interactive method for estimating body segmental parameters in animals: Application to the turning and running performance of Tyrannosaurus rex. Journal of Theoretical Biology, 246(4), 660–680.
Hyde, H. A., & Williams, D. W. (1944). The right word. Pollen Analisis Circulars, 8, 6.
Ineichen, M., & Neukom, R. (1995). Daktyloskopieren von mummifizierten Leichen [in German; Dactyloscopy of mummified bodies; with German and English summaries]. Archiv für Kriminologie, 196(3/4), 87–92. Our quotation is from the English summary, as reproduced in Forensic Science Abstracts, Section 49, 22(2) (1996): p. 57, sec. 4, §395.
Inman, K., & Rudin, V. (2002). An introduction to forensic DNA analysis. Boca Raton, FL: CRC Press.
Isenor, D. K., & Zaky, S. G. (1986). Fingerprint identification using graph matching. Pattern Recognition, 19, 111–112.
Jain, A. K., Hong, L., Pankanti, S., & Bolle, R. (1997). An identity-authentication system using fingerprint. Proceedings of the IEEE, 85(9), 1365–1388.
Jain, A. K., & Maltoni, D. (2003). Handbook of fingerprint recognition. Berlin: Springer.
Jain, A. K., Prabhakar, S., Hong, L., & Pankanti, S. (2000). Filterbank-based fingerprint matching. IEEE Transactions on Image Processing, 9(5), 846–859.
James, S. H. (Ed.). (1999). Scientific and legal applications of bloodstain pattern interpretation. Boca Raton, FL: CRC Press.
James, S. H., & Eckert, W. G. (1999). Interpretation of bloodstain evidence at crime scenes (2nd ed.). Boca Raton, FL: CRC Press.
James, S. H., & Nordby, J. J. (Eds.). (2003) Forensic science: An introduction to scientific and investigative techniques (1st ed.). Boca Raton, FL: CRC Press. 2nd edition, 2005. Also published in the 3rd edition, 2009.
James, S. H., Kish, P. E., & Sutton, T. P. (2005a). Principles of bloodstain pattern analysis (3rd ed.). Boca Raton, FL: CRC Press.
James, S. H., Kish, P. E., & Sutton, T. P. (2005b). Recognition of bloodstain patterns. In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (1st ed.) [with that title opf the book]. Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Jamieson, A. (2004). A rational approach to the principles and practice of crime scene investigation: I, principles. Science & Justice, 44(1), 3–7.
Jha, S. K., & Yadava, R. D. S. (2010). Development of surface acoustic wave electronic nose using pattern recognition system. Defence Science Journal, 60(4), 364–376.
Jiang, X., Yau, W., & Ser, W. (2001). Detecting the fingerprint minutiae by adaptively tracing the gray-level ridge. Pattern Recognition, 34, 999–1013.
Johnson, S. L. (1985). Two actions equals no response: Misinterpretations of motorcycle collision causes. In I. D. Brown, R. Goldsmith, K. Coombes, & M. A. Sinclair (Eds.), Ergonomics international 85: Proceedings of the ninth congress of the international ergonomics association, Bournemouth, England, September. Basingstoke, Hamsphire: Taylor & Francis.
Johnson, G. W., Ehrlich, R., & Full, W. (2002). Principal components analysis and receptor models in environmental forensics. Chapter 12 In B. L. Murphy & R. D. Morrison (Eds.), Introduction to environmental forensics (pp. 461–515). San Diego, CA & London, U.K.: Academic.
Johnson, M. K., & Farid, H. (2006b). Metric measurements on a plane from a single image. Technical Report TR2006 579. Hanover, New Hampshire: Department of Computer Science, Dartmouth College.
Johnson, M. K., & Farid, H. (2007a). Exposing digital forgeries in complex lighting environments. IEEE Transactions on Information Forensics and Security, 2(3), 450–461.
Johnston, V. S., & Caldwell, C. (1997). Tracking a criminal suspect through face space with a genetic algorithm. In T. Bäck, D. B. Fogel, & Z. Michalewics (Eds.), Handbook of evolutionary computation. Bristol, England: Institute of Physics Publishing, & New York & Oxford: Oxford University Press.
Jones, C. A. G. (1994). Expert witnesses: Science, medicine, and the practice of law. Oxford Socio-Legal Studies. Oxford: Clarendon Press.
Joyce, C. (1984). The detective from the laboratory. New Scientist, 15 November 1984, pp. 12–16.
Junger, E. P. (1996). Assessing the unique characteristics of close-proximity soil samples: Just how useful is soil evidence? Journal of Forensic Science, 41(1), 27–34.
Karttunen, L. (1976). Discourse referents. Syntax and Semantics, 7, 363–385.
Kassin, S. M., Goldstein, C. J., & Savitsky, K. (2003). Behavioral confirmation in the interrogation room: On the dangers of presuming guilt. Law and Human Behavior, 27, 187–203.
Kaye, D. (1982). Statistical evidence of discrimination. Journal of the American Statistical Association, 77(380), 773–783.
Kaye, D. H. (2003). Questioning a courtroom proof of the uniqueness of fingerprints. International Statistical Review, 71, 521–533.
Kearey, P., & Brooks, M. (1984). An introduction to geophysical exploration (1st ed.). Oxford: Blackwell Science (as cited); 2nd edn.: 1991. 3rd edn.: Kearey, P., Brooks, M., & Hill, I., ibid., 2002.
Keh, B. (1984). Scope and applications of forensic entomology. Annual Review of Entomology, 30, 137–154. Palo Alto, CA: Annual Reviews.
Keppens, J., & Schafer, B. (2004). “Murdered by persons unknown” – Speculative reasoning in law and logic. In T. Gordon (Ed.), Legal knowledge and information systems. Jurix 2004: The seventeenth annual conference (pp. 109–118). Amsterdam: IOS Press.
Keppens, J., & Schafer, B. (2006). Knowledge based crime scenario modelling. Expert Systems with Applications, 30(2), 203–222.
Keppens, J., & Shen, Q. (2001). On compositional modelling. Knowledge Engineering Review, 16(2), 157–200.
Keppens, J., & Shen, Q. (2004). Compositional model repositories via dynamic constraint satisfaction with order-of-magnitude preferences. Journal of Artificial Intelligence Research, 21, 499–550.
Khuwaja, G. A. (2006). A multimodal biometric identification system using compressed finger images. Cybernetics and Systems, 37(1), 23–46.
Kim, B. M., & Henry, R. C. (1999). Extension of self-modeling curve resolution to mixtures of more than 3 components. Part 2: Finding the complete solution. Chemometrics and Intelligent Laboratory Systems, 49, 67–77.
Knott, A. W. (1987). Are you an expert? Forensic Engineering, 1(1), 7–16.
Koehler, J. J. (2008). A welcome exchange on the scientific status of fingerprinting (Editorial). Law, Probability and Risk, 7, 85–86.
Kong, A., Zhang, D., & Kamel, M. (2006). Palmprint identification using feature-level fusion. Pattern Recognition, 29(3), 478–487.
Kothari, R., & Dong, M. (2002). Decision trees for classification: A review and some new results. In S. K. Pal & A. Pla (Eds.), Pattern Recognition from classical to modern approaches (pp. 169–186). Singapore: World Scientific.
Kovács-Vajna, Z. M. (2000). A fingerprint verification system based on triangular matching and dynamic time warping. IEEE Transactions on Pattern Analysis and Machine Intelligence (IEEE PAMI), 22(11), 1266–1276.
Kovács-Vajna, Z. M., Rovatti, R., & Frazzoni, M. (2000). Fingerprint ridge distance computation methodologies. Pattern Recognition, 33(1), 69–80.
Krane, D., Ford, S., Gilder, J., Inman, K., Jamieson, A., Koppl, R., et al. (2008). Sequential unmasking: A means of minimizing observer effects in forensic DNA interpretation. Journal of Forensic Sciences, 53(4),1006–1007. http://www.bioforensics.com/sequential_unmasking/http://www.bioforensics.com/sequential_unmasking/Sequential_Unmasking_2008.pdf
Krawczak, M., & Schmidtke, J. (1994). DNA fingerprinting. Medical Perspectives Series. Oxford: BIOS Scientific.
Krogman, W. M., & İşcan, M. Y. (1986). The human Skeleton in forensic medicine. Springfield, IL: Charles C. Thomas.
Landman, F. (1986). Towards a theory of information: The status of partial objects in semantics. Dordrecht, The Netherlands: Foris.
Lane, B., Tingey, M., & Tingey, R. (Eds.). (1993). The encyclopedia of forensic science. London: Headline.
Langenburg, G. M. (2004). Pilot study: A statistical snalysis of the ACE V methodology – Analysis stage. Journal of Forensic Identification, 54, 64–79.
Laughery, K. R., & Fowler, R. H. (1980). Sketch artist and Identi-kit procedures for recalling faces. Journal of Applied Psychology, 65(3), 307–316.
Lauritzen, S. L., & Mortera, J. (2002). Bounding the number of contributors to mixed DNA stains. Forensic Science International, 130, 125–126.
Lee, H. C., & Gaensslen, R. E. (Eds.). (1991). Advances in fingerprint technology. Elsevier Series in Forensic and Police Science. New York & Amsterdam: Elsevier. 2nd edition published in the CRC Series in Forensic and Police Science, Boca Raton, Florida: CRC Press, 2001.
Lee, H. C., Palmbach, T., & Miller, M. T. (2001). Henry Lee’s crime scene handbook. London: Academic.
Lemar, C., & Chilvers, D. R. (1995). Litigation support (3rd ed.). (The Coopers & Lybrand Guide to the Financial Assessment of Damages and Forensic Accounting.) London: Butterworths.
Lewis, P. R., Gagg, C., & Reynolds, K. (2004). Forensic materials engineering: Case studies. Boca Raton, FL: CRC Press.
Lewis, P. R., & Hainsworth, S. (2006). Fuel line failure from stress corrosion cracking. Engineering Failure Analysis, 13, 946–962.
Li, Q., Niu, X., Wang, Zh., Jiao, Y., & Sun, Sh. H. (2005). A verifiable fingerprint vault scheme. In R. Khosla, R. J. Howlett, & L. C. Jain (Eds.), Knowledge-based intelligent information and engineering systems: 9th international conference, KES 2005, Melbourne, Australia, September 14–16, 2005, Proceedings, Part III (pp. 1072–1078). (Lecture Notes in Computer Science, Vol. 3684.) Berlin: Springer.
Lloyd, C. (1995). Forensic psychiatry for health professionals. London: Chapman & Hall.
Locard, E. (1930). Analysis of dust traces. American Journal of Police Science, 1(276), 401–496.
Loftus, E. F. (1974). Reconstructing memory: The incredible witness. Psychology Today, 8, 116–119.
Lonergan, M. C., Severin, E. J., Doleman, B. J., Beaber, S. A., Grubbs, R. H., & Lewis, N. S. (1996). Array-based vapor sensing using chemically sensitive, carbon black-polymer resistors. Chemistry of Materials, 8, 2298–2312.
Lonsdorf, R. G. (1995). Review of H. Bluestone, S. Travin, & D. Marlowe, Psychiatric-legal decision making by the mental health practitioner: The clinician as de facto magistrate. (New York: Wiley, 1994). The Journal of Legal Medicine, 16(2), 319–324.
Lucy, D. (2005). Introduction to statistics for forensic scientists. Chichester: Wiley.
Luger, G. F., & Stubblefield, W. A. (1998). Artificial intelligence: Structures and strategies for complex problem solving (3rd ed.). Reading, MA: Addison Wesley Longman.
MacDonell, H. L. (1993). Bloodstain patterns. Corning, NY: Laboratory of Forensic Science.
MacDonell, H. L., & Bialousz, L. F. (1979). Laboratory manual for the geometric interpretation of human bloodstain evidence (2nd ed.). Corning, NY: Laboratory of Forensic Science.
MacDougall, K. A., Fenning, P. J., Cooke, D. A., Preston, H., Brown, A., Hazzard, J., et al. (2002). Non intrusive investigation techniques for groundwater pollution studies. Research & Development Technical Report P2 178/TR/10. Bristol, England: Environment Agency.
Malinowski, E. R. (1991). Factor analysis in chemistry. New York: Wiley.
Maloney, K., Carter, A. L., Jory, S., & Yamashita, B. (2005). Three-dimensional representation of bloodstain pattern analysis. Journal of Forensic Identification, 55(6), 711–725.
Maloney, K., Killeen, J., & Maloney, A. (2009). The use of HemoSpat to include bloodstains located on nonorthogonal surfaces in area-of-origin calculations. Journal of Forensic Identification, 59(5), 513–524. http://hemospat.com/papers/pdf/JFI%20 %20HemoSpat%20Using%20Nonorthogonal%20Surfaces.pdf
McCann, D., Culshaw, M. G., & Fenning, P. J. (1997). Setting the standard for geophysical surveys in site investigations. In D. M. McCann, M. Eddleston, P. J. Fenning, & G. M. Reeves (Eds.), Modern geophysics in engineering geology (pp. 3–34). (Engineering Geology Special Publications, 12.) London: Geological Society.
McConville, M., Saunders, A., & Leng, R. (1991). The case for the prosecution. London: Routledge.
McCulloch, M., Jezierski, T., Broffman, M., Hubbard, A., Turner, K., & Janecki, T. (2006). Diagnostic accuracy of canine scent detection in early- and late-stage lung and breast cancers. Integrative Cancer Therapies, 5, 1–10.
McQuiston-Surret, D., Topp, L. D. & Malpass, R. S. (2006). Use of facial composite systems in US law enforcement agencies, Psychology, Crime & Law, 12, 505–517.
Meester, R. W. J., & Sjerps, M. (2004). Why the effect of prior odds should accompany the likelihood ratio when reporting DNA evidence (with discussion between A. P. Dawid, D. J. Balding, J. S. Buckleton and C. M. Triggs). Law, Probability and Risk, 3, 51–86.
Meissner, C., & Kassin, S. (2002). He’s guilty: Investigator bias in judgements of truth and deception. Law and Human Behavior, 26, 469–480.
Memon, A., Hope, L., & Bull, R. H. C. (2003). Exposure duration: Effects on eyewitness accuracy and confidence. British Journal of Psychology, 94, 339–354.
Mena, J. (2003). Investigative data mining for security and criminal detection. Amsterdam & Boston (Newton, MA): Butterworth-Heinemann (of Elsevier).
Miller, M. T. (2003). Crime scene investigation. Chapter 8 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (1st ed.). Boca Raton, FL: CRC Press. Also as Chapter 10 in 2nd edition, 2005. Also published in the 3rd edition, 2009.
Miller, R. E. (1973). A comparison of some theoretical models of parallel computation. IEEE Transactions on Computers, C 22, 710–717.
Mitchell, T. M. (1997). Machine learning. New York: McGraw-Hill.
Moenssens, A. (2003). Fingerprint identification: A valid reliable “forensic science”? Criminal Justice, 18, 31–37.
Moore, D. S. (2007). Recent advances in trace explosives detection instrumentation. Sense Imaging, 8, 9–38. doi://10.1007/s11220 007 0029 8
Morrison, R. D. (2002). Subsurface models used in environmental forensics. Chapter 8 In B. L. Murphy & R. D. Morrison (Eds.), Introduction to environmental forensics (pp. 311–367). San Diego, CA & London: Academic pp. 311–367.
Mortera, J., Dawid, A. P., & Lauritzen, S. L. (2003). Probabilistic expert systems for DNA mixture profiling. Theoretical Population Biology, 63, 191–205.
Murphy, B. L., & Morrison, R. D. (Eds.). (2002). Introduction to environmental forensics. San Diego, CA & London: Academic.
Murray, R. C., & Tedrow, J. C. F. (1975). Forensic geology: Earth sciences and criminal investigations. New Brunswick, NJ: Rutgers University Press.
Na, H.-J., Yoon, D.-H., Kim, Ch.-S., & Hwang, H. S. (2005). Vulnerability evaluation tools of matching algorithm and integrity verification in fingerprint recognition. In R. Khosla, R. J. Howlett, & L. C. Jain (Eds.), Knowledge-based intelligent information and engineering systems: 9th international conference, KES 2005, Melbourne, Australia, September 14–16, 2005, Proceedings, Part IV (pp. 993–999). (Lecture Notes in Computer Science, Vol. 3684). Berlin: Springer.
Nambiar, P., Bridges, T. E., & Brown, K. A. (1995). Quantitative forensic evaluation of bite marks with the aid of a shape analysis computer program. I: The development of SCIP and the similarity index. Journal of Forensic Odontostomatology, 13(2), 18–25.
Nance, D. A., & Morris, S. B. (2002). An empirical assessment of presentation formats for trace evidence with a relatively large and quantifiable random match probability. Jurimetrics Journal, 42, 403–445.
Nance, D. A., & Morris, S. B. (2005). Juror understanding of DNA evidence: An empirical assessmeng of presentation formats for trace evidence with a relatively small random-match probability. Journal of Legal Studies, 34, 395–443.
Nanto, H., Sokooshi, H., & Kawai, T. (1993). Aluminum-doped ZnO thin film gas sensor capable of detecting freshness of sea foods. Sensors & Actuators, 14, 715–717.
Ng-Thow-Hing, V. (1994). A biomechanical musculotendon model for animating articulated objects. MSc Thesis (supervised by E. Fiume). Toronto, Canada: University of Toronto, Department of Computer Science.
Ng-Thow-Hing, V. (2001). Anatomically based models for physical and geometric reconstruction of animals. PhD Thesis (supervised by E. Fiume). Toronto, Canada: University of Toronto, Department of Computer Science.
Nicolle, D. (1990). The Mongol Warlords: Genghis Khan, Kublai Khan, Hülegü, Tamerlane, with plates by R. Hook. Poole, Dorset, England: Firebird Books.
Nielsen, L., & Nespor, S. (1993). Genetic test, screening, and use of genetic data by public authorities: In criminal justice, social security, and alien and foreigners acts. Copenhagen: Danish Centre for Human Rights.
Nissan, E. (1998b). Review of: A. G. B. ter Meulen, Representing time in natural language: The dynamic interpretation of tense and aspect (Cambridge, MA: The MIT Press, 1997). Computers and Artificial Intelligence, 17(1), 98–100.
Nissan, E. (2001b). Can you measure circumstantial evidence? The background of probative formalisms for law. [A review essay on I. Rosoni, Quae singula non prosunt collecta iuvant: la teoria della prova indiziaria nell’età medievale e moderna. Milan, Italy: Giuffrè, 1995.]. Information and Communications Technology Law, 10(2), 231–245.
Nissan, E. (2001f). Review of: R. Bull and D. Carson (Eds.), Handbook of Psychology in Legal Contexts (Chichester, West Sussex, England: Wiley, 1995). Artificial Intelligence and Law, 9(2/3), pp. 219–224.
Nissan, E. (2001 g). Modelling spatial relations in the traveller’s conditional divorce problem. In M. Koppel & E. Merzbach (Eds.), Higgaion: Studies in rabbinic logic (Vol. 5, pp. 8–21). Jerusalem: Aluma.
Nissan, E. (2003b). Identification and doing without it, II: Visual evidence for pinpointing identity. How Alexander was found out: Purposeful action, enlisting support, assumed identity, and recognition. A goal-driven formal analysis. Cybernetics and Systems, 34(4/5), 359–380.
Nissan, E. (2003 h). Review of Mani (2001). Cybernetics & Systems, 34(4/5), 559–569.
Nissan, E. (2008b). Tools from artificial intelligence for handling legal evidence. In M. Quigley (Ed.), Encyclopedia of information ethics and security (pp. 42–48). Hershey, PA: IGI Global.
Nissan, E. (2011a). The rod and the crocodile: Temporal relations in textual hermeneutics: An application of Petri nets to semantics. Semiotica, 184(1/4), 187–227.
Noon, R. K. (1992). Introduction to forensic engineering. (The Forensic Library). Boca Raton, FL: CRC Press.
Noon, R. K. (2005a). Structural failures. Chapter 23 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Noon, R. K. (2005b). Vehicular accident reconstruction. Chapter 25 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Oatley, G., Zeleznikow, J., & Ewart, B. (2004). Matching and predicting crimes. In A. Macintosh, R. Ellis, & T. Allen (Eds.), Applications and innovations in intelligent systems XII. Proceedings of AI2004, the 24th SGAI international conference on knowledge based systems and applications of artificial intelligence (pp. 19–32). Berlin: Springer.
Olderog, E.-R. (1991). Nets, terms and formulas: Three views of concurrent processes and their relationship. (Cambridge Tracts in Theoretical Computer Science, 23.) Cambridge: Cambridge University Press.
Ormerod, T. C., Barrett, E. C., & Taylor, P. J. (2008). Investigating sensemaking in criminal contexts. In J. M. Schraagen, L. G. Militello, T. C. Ormerod, & R. Lipshitz (Eds.), Naturalistic decision making and macrocognition (pp. 81–102). Farnham, England: Ashgate.
Osborne, C. (1997). Criminal litigation (5th ed.). London: Blackstone.
Osuna, R. G., & Nagle, H. T. (1999). A method for evaluating data preprocessing techniques for odour classification with an array of gas sensors. IEEE Transactions on Systems, Man and Cybernetics, B, 29(5), 626–632.
Ouellette, J. (1999). Electronic noses sniff our new markets. Industrial Physics, 5, 26–29.
Pankanti, S., Prabhakar, S., & Jain, A. K. (2002). On the individuality of fingerprints. IEEE Transactions on Pattern Analysis & Machine Intelligence (IEEE PAMI), 24, 1010–1025.
Pardue, H. L. (Ed.). (1994). Analytical aspects of forensic science. Special issue, Analytica Chimica Acta, 288(1/2). Amsterdam: Elsevier.
Peirce, C. S. (1903). Harvard lectures on pragmatism. In C. Hartshorne & P. Weiss (Eds.), Collected papers of Charles Sanders Peirce (Vol. 5). Cambridge, MA: Harvard University Press. (8 vols. published in 1931–1958 (vols. 7 and 8, ed. A. W. Burks).70 Volumes reissued as 8 vols. in 4 by the Belknap Press of Harvard University Press, ca. 1965–1967. The 1931–1958 edn. was reprinted as 8 vols. in Bristol, England: Thoemmes Press, 1998.)
Pelosi, P., & Persaud, K. C. (1988). Gas sensors: towards an artificial nose. In P. Dario (Ed.), Sensors and sensory systems for advanced robotics (pp. 361–381). Berlin: Springer.
Pennec, X. (2007). From Riemannian geometry to computational anatomy of the brain. In The Digital Patient, special issue of ERCIM News, 69 (April), pp. 15–16. Article downloadable from the webpage http://ercim news.ercim.org/content/view/166/314/ of the European Research Consortium for Informatics and Mathematics.
Penry, J. (1974). Photo-Fit. Forensic Photography, 3(7), 4–10.
Persaud, K. C. (1992). Electronic gas and odor detectors that mimic chemoreception in animals. TRAC Trends in Analytical Chemistry, 11, 61–67.
Persaud, K. C., Bartlett, J., & Pelosi, P. (1993). Design strategies for gas and odour sensors which mimic the olfactory system. In P. Dario, G. Sandini, & P. Aebisher (Eds.), Robots and biological systems: Towards a new bionics? (pp. 579–602). Berlin: Springer.
Persaud, K. C., & Dodd, G. (1982). Analysis of discrimination mechanisms in the mammalian olfactory system using a model nose. Nature, 299, 352–355.
Persaud, K. C., Qutob, A. A., Travers, P., Pisanelli, A. M., & Szyszko, S. (1994). Odor evaluation of foods using conducting polymer arrays and neural net pattern recognition. In K. Kurihara, N. Suzuki, & H. Ogawa (Eds.), Olfaction and taste XI (pp. 708–710). Tokyo & Berlin: Springer.
Peters, G. A., & Peters, B. J. (1994). Automotive engineering and litigation. (Wiley Law Publications.) New York: Wiley.
Peterson, J. L. (1981). Petri net theory and the modelling of systems. Englewood Cliffs, NJ: Prentice Hall.
Petri, C. A. (1966). Communication with automata. Supplement 1 to Technical Report RADC TR 65 377, Vol. 1. Rome, NY: Rome Air Development Center, Griffiths Air Force Base, January 1966. Translated by C. F. Greene, Jr., from: Kommunikation mit Automaten, University of Bonn, Bonn, West Germany, 1962.
Pharr, M., & Humphreys, G. (2004). Physically based rendering: From theory to implementation. San Francisco: Morgan Kaufmann.
Philp, R. P. (2002). Application of stable isotopes and radioisotopes in environmental forensics. Chapter 5 In B. L. Murphy & R. D. Morrison (Eds.), Introduction to environmental forensics (pp. 99–136). San Diego, CA & London: Academic.
Pickel, D., Manucy, G., Walker, D., Hall, S., & Walker, J. (2004). Evidence for canine olfactory detection of melanoma. Applied Animal Behaviour Science, 89, 107–116.
Pisanelli, A. M., Qutob, A. A., Travers, P., Szyszko, S., & Persaud, K. C. (1994). Applications of multi-array polymer sensors to food industries. Life Chemistry Reports, 11, 303–308.
Popescu, A. C., & Farid, H. (2004). Exposing digital forgeries by detecting duplicated image regions. Technical Report TR2004 515. Hanover, NH: Department of Computer Science, Dartmouth College.
Popescu, A. C., & Farid, H. (2005a). Exposing digital forgeries by detecting traces of re sampling. IEEE Transactions on Signal Processing, 53(2), 758–767.
Popescu, A. C., & Farid, H. (2005b). Exposing digital forgeries in color filter array interpolated images. IEEE Transactions on Signal Processing, 53(10), 3948–3959. http://www.cs.dartmouth.edu/farid/publications/sp05a.html
Prakken, H., Reed, C., & Walton, D. N. (2003). Argumentation schemes and generalisations in reasoning about evidence. In G. Sartor (Ed.), Proceedings of the ninth International Conference on Artificial Intelligence and Law (ICAIL 2003), Edinburgh, Scotland, 24–28 June 2003 (pp. 32–41). New York: ACM Press.
Proth, J.-M., & Xie, X. (1996). Petri nets: A tool for design and management of manufacturing systems. Chichester: Wiley.
Pye, K. (2007). Geological and soil evidence: Forensic applications. Boca Raton, FL: CRC Press.
Pye, K., & Croft, D. J. (Eds.). (2004). Forensic geoscience: Principles, techniques and applications. (Special Publications, 232.) London: Geological Society.
Quinlan, J. R. (1986). Induction of decision trees. Machine Learning, 1, 81–106.
Rakover, S. S., & Cahlon, B. (1989). To catch a thief with a recognition test: The model and some empirical results. Cognitive Psychology, 21, 423–468.
Rakover, S. S., & Cahlon, B. (2001). Face recognition: Cognitive and computational processes. (Advances in Consciousness Research, Series B, Vol. 31.) Amsterdam: Benjamins.
Redmayne, M. (2002). Appeals to reason. The Modern Law Review, 65(1), 19–35. Oxford: Blackwell.
Redsicker, D. R. (2005). Basic fire and explosion ivestigation. Chapter 24 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press, 2005. Also in 3rd edition, 2009.
Reutenauer, C. (1990). The mathematics of petri nets. London: Prentice-Hall International.
Ribaux, O., & Margot, P. (1999). Inference structures for crime analysis and intelligence: The example of burglary using forensic science data. Forensic Science International, 100, 193–210.
Riepert, T., Drechsler, T., Schild, H., Nafe, B., & Mattern, R. (1996). Estimation of sex on the basis of radiographs of the calcaneus. Forensic Science International, 77(3), 133–140.
Roberts, L. (1991). Fight erupts over DNA fingerprinting. Science, 254, 1721–1723.
Robertson, B., & Vignaux, G. A. [T.] (1995). Interpreting evidence: Evaluating forensic science in the courtroom. Chichester: Wiley.
Roscoe, A. W. (1998). The theory and practice of concurrency. (Prentice Hall Series in Computer Science.) Hemel Hempstead, Hertfordshire: Prentice Hall.
Roscoe, B. A., & Hopke, P. K. (1981). Comparison of weighted and unweighted target transformation rotations in factor analysis. Computers and Chemistry, 5, 1–7.
Rosoni, I. (1995). Quae singula non prosunt collecta iuvant: la teoria della prova indiziaria nell’età medievale e moderna. Milan, Italy: Giuffrè. [Reviewed in Nissan (2001b).]
Ross, D. F., Read, J. D., & Toglia, M. P. (Eds.). (1994). Adult eyewitness testimony: Current trends and developments. Cambridge: Cambridge University Press.
Rossiter, B. N., Sillitoe, T. J., & Heather, M. A. (1993). Models for legal documentation: Using formal methods for quality assurance in hypertext systems. (Technical Report Series, 464.) Newcastle upon Tyne, England: University of Newcastle upon Tyne, Computing Science.
Ryan, P. Y. A, Schneider, S. A., Goldsmith, M., Lowe, G., & Roscoe, A. W. (2000). Modelling and analysis of security protocols. Harlow: Pearson Education.
Saferstein, R. E. (1995). Criminalistics: An introduction to forensic science (5th ed.). Englewood Cliffs, NJ: Prentice-Hall. 6th edn., 1998.
Scampicchio, M., Ballabio, D., Arecchi, A., Cosio, S. M., & Mannino, S. (2008). Amperometric electronic tongue for food analysis. Microchimica Acta, 163, 11–21.
Shirley, S. G., & Persaud, K. C. (1990). The biochemistry of vertebrate olfaction and taste. Seminars Neuroscience., 2, 59–68.
Schneider, S. A. (1999). Concurrent and real time systems: The CSP approach. Chichester: Wiley.
Schneider, S. A. (2001). The B-method: An introduction. Palgrave Cornerstones in Computer Science. London: Palgrave Macmillan.
Schneider, V., Nagano, T., & Geserick, G. (Eds). (1994). Advances in legal medicine. Special issue, Forensic Science International, 69(3). Amsterdam: Elsevier.
Schoenlein, R. W., Chattopadhyay, S., Chong, H. H. W., Glover, T. E., Heimann, P. A., Shank, C. V., et al. (2000). Generation of femtosecond pulses of synchrotron radiation. Science, 287, 2237.
Schraagen, J. M., & Leijenhorst, H. (2001). Searching for evidence: Knowledge and search strategies used by forensic scientists. In E. Salas & G. Klein (Eds.), Linking expertise and naturalistic decision making (pp. 263–274). Mahwah, NJ: LEA.
Schreiber, F. A. (1991). State and time granularity in systems description: An example. IEEE Real-Time Systems Newsletter, 7(3), 12–17. http://home.dei.polimi.it/schreibe/papers/states2.ps(sic: /schreibe/ not /schreiber/ )
Schreiber, F. A. (1994). Is time a real time? An overview of time ontology in informatics. In W. A. Halang & A. D. Stoyenko (Eds.), Real time computing (pp. 283–307). (NATO ASI, Vol. F 127.) Berlin: Springer.
Schum, D. A. (1994). The evidential foundations of probabilistic reasoning. (Wiley Series in Systems Engineering.) New York: Wiley. Reprinted, Evanston, IL: Northwestern University Press, 2001.
Sellier, K. G., & Kneubuehl, B. P. (1994). Wound ballistics and the scientific background. Amsterdam: Elsevier.
Shoham, Y., & McDermott, D. (1988). Problems in formal temporal reasoning. Artificial Intelligence, 36(1), 49–90.
Shuirman, G., & Slosson, J. E. (1992). Forensic engineering: Environmental case histories for civil engineers and geologists. San Diego, CA: Academic.
Shurmer, H. V. (1990). An electronic nose: A sensitive and discrimination substitute for a mammalian olfactory system. International Electrical Engineering Proceedings, 137, 197–204.
Siegel, J. A., Knupfer, G. C., & Saukko, P. J. (Ed.). (2000). Encyclopedia of forensic sciences (3 Vols.). London: Academic.
Sigmund, W. (Ed.). (1995). Environmental poisoning and the law: Proceedings of the conference, 17 September 1994, Kings College, London. London: South West Environmental Protection Agency & Environmental Law Foundation, 1995.
Siroky D. S. (2009). Navigating random forests and related advances in algorithmic modeling. Statistics Surveys, 3,147–163. Accessible online by searching the journal’s site at http://www.i journals.org/ss/search.php
Smith, P. A., Baber, C., Hunter, J., & Butler, M. (2008). Measuring team skills in crime scene examination: Exploring ad hoc teams. Ergonomics, 51, 1463–1488.
Söderström, C., Borén, H., Winquist, F., & Krantz-Rülcker, C. (2003). Use of an electronic tongue to analyze mold growth in liquid media. International Journal of Food Microbiology, 83, 253–261.
Sorg, M. H. (2005). Forensic anthropology. Chapter 7 In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Specter, M. M. (1987). The national academy of forensic engineers. Forensic Engineering, 1(1), 61–63.
Srihari, S. N., Srinivasan, H., & Beal, M. (2008). Machine learning for signature verification. In S. Marinai & H. Fujisawa (Eds.), Machine learning in document analysis and recognition (pp. 387–408). (Studies on Computational Intelligence, Vol. 90). Berlin: Springer.
Stockmarr, A. (1999). Likelihood ratios for evaluating DNA evidence when the suspect is found through a database search. Biometrics, 55, 671–677.
Stoney, D. A. (1997). Fingerprint identification: Scientific status. In D. L. Faigman, D. H. Kaye, M. J. Saks, & J. Sanders (Eds.), Modern scientific evidence: The law and science of expert testimony (Vol. 2). St. Paul, MN: West Publishing.
Stoney, D. A. (2001). Measurement of fingerprint individuality. In H. C. Lee & R. E. Gaensslen (Eds.), Advances in fingerprint technology (pp. 327–387). Boca Raton, FL: CRC Press.
Suprenant, B. A. (1988). Introduction to forensic engineering. Oxford: Pergamon.
Sutton, P. T. (1998). Bloodstain pattern interpretation. Short Course Manual. Memphis, TN: University of Tennessee.
Tan, X., & Bhanu, B. (2006). Fingerprint matching by genetic algorithms. Pattern Recognition, 29(3), 465–477.
Taroni, F., Aitken, C., Garbolino, P., & Biedermann, A. (2006). Bayesian networks and probabilistic inference in forensic science. (Statistics in Practice Series.) Chichester: Wiley.
Tebbett, I. (1992). Gas chromatography in forensic science. (Ellis Horwood Series in Forensic Science.) London: Ellis Horwood.
ter Meulen, A. G. B. (1995). Representing time in natural language: The dynamic interpretation of tense and aspect. Cambridge, MA: The MIT Press. Paperback, 1997. The paperback edition is augmented with an appendix.
Teran, J., Sifakis, E., Blemker, S., Ng-Thow-Hing, V., Lau, C., & Fedkiw, R. (2005). Creating and simulating skeletal muscle from the visible human data set. IEEE Transactions on Visualization and Computer Graphics, 11(3), 317–328.
Tinsley, Y. (2001). Even better than the real thing? The case for reform of identification procedures. The International Journal of Evidence & Proof, 5(2), 99–110. Sark, Channel Islands: Vathek Publishing (vatheksubs@cassis.co.uk).
Tredoux, C. G., Nunez, D. T., Oxtoby, O., & Prag, B. (2006). An evaluation of ID: An eigenface based construction system. South African Computer Journal, 37, 1–9.
Turner, B. (1987). Forensic entomology: Insects against crime. Science Progress, 71(1)281, pp. 133–144. Abingdon, Oxfordshire: Carfax (Taylor & Francis).
Ukpabi, P., & Peltron, W. (1995). Using the scanning electron microscope to identify the cause of fibre damage. Part I: A review of related literature. Journal of the Canadian Society of Forensic Science, 28(3), 181–187.
van Benthem, J. (1983). The logic of time (1st ed.). Dordrecht, The Netherlands: Kluwer. 2nd edition, 1991.
van Benthem, J. (1995). Temporal logic. In D. M. Gabbay, C. J. Hogger, & J. A. Robinson (Eds.), Handbook of logic in artificial intelligence and logic programming (Vol. 4, pp. 241–350). Oxford: Clarendon Press.
Vicard, P., & Dawid, A. P. (2004). A statistical treatment of biases affecting the estimation of mutation rates. Mutation Research, 547, 19–33.
Vicard, P., & Dawid, A. P. (2006). Remarks on: ‘Paternity analysis in special fatherless cases without direct testing of alleged father’ [Forensic Science International 146S (2004) S159–S161]. Forensic Science International, 163(1–2), 158–160. http://tinyurl.com/pur8q
Vicard, P., Dawid, A. P., Mortera, J., & Lauritzen S. L. (2008). Estimating mutation rates from paternity casework. Forensic Science International: Genetics, 2, 9–18. doi:10.1016/j.fsigen.2007.07.002
Vila, L., & Yoshino, H. (2005). Time in automated legal reasoning. In M. Fisher, D. Gabbay, & L. Vila (Eds.), Handbook of temporal reasoning in artificial intelligence (electronic resource; Foundations of Artificial Intelligence, 1). Amsterdam: Elsevier.
Wang, J. (2004). Microchip devices for detecting terrorist weapons. Analytical Chimica Acta, 507, 3–10.
Ward, K. M., & Duffield, J. W. (1992). Natural resource damages: Law and economics. (Environmental Law Library, Wiley Law Publications.) New York: Wiley (with pocket supplements).
Watson, J. A. F. (1975). Nothing but the truth: Expert evidence in principle and practice for surveyors, valuers and others (2nd ed.). London: Estates Gazette.
Watson, J. G., & Chow, J. C. (2002). Particulate pattern recognition. Chapter 11 In B. L. Murphy & R. D. Morrison (Eds.), Introduction to environmental forensics (pp. 429–460). San Diego, CA & London: Academic.
Wells, G. L., & Charman, S. D. (2005). Building composites can harm lineup identification performance. Journal of Experimental Psychology: Applied, 11, 147–156.
Wertheim, K., Langenburg, G., & Moenssens, A. (2006). A report of latent print examiner accuracy during comparison training exercises. Journal of forensic identification, 56, 55–93.
Wertheim, K., & Maceo, A. (2002). The critical stage of friction ridge pattern formation. Journal of Forensic Identification, 52, 35–85.
White, J., Kauer, J. S., Dickinson, T. A., & Walt, D. R. (1996). Rapid analyte recognition in a device based on optical sensors and the olfactory system. Analytical Chemistry, 68, 2191–2202.
Wilder, H. H., & Wentworth, B. (1918). Personal identification: methods for the identification of individuals, living or dead. Boston: Gorham.
Wilkinson, C. (2004). Forensic facial reconstruction. Cambridge: Cambridge University Press.
Willis, C. M., Church, S. M., Guest, C. M., Cook, W. A., McCarthy, N., Bransbury, A. J., et al. (2004). Olfactory detection of human bladder cancer by dogs: proof of principle study. British Medical Journal, 329, 712–715.
Wilson, A. D., & Baietto, M. (2009). Applications and advances in electronic-nose technologies. Sensors, 9(7), 5099–5148. Open access. doi://10.3390/s90705099 http://www.mdpi.com/1424-8220/9/7/5099/pdf
Winquist, F. (2008). Voltammetric electronic tongues: Basic principles and applications. Mikrochimica Acta, 163, 3–10.
Winquist, F., Holmin, S., Krantz-Rülcker, C., Wide, P., & Lundström, I. (2000). A hybrid electronic tongue. Analytica Chimica Acta, 406, 147–157.
Wogalter, M. S., & Marwitz, D. B. (1991). Face composite construction: In-view and from-memory quality and improvement with practice. Ergonomics, 34(4), 459–468.
Wright, R. K. (2005). Investigation of traumatic deaths. In S. H. James & J. J. Nordby (Eds.), Forensic science: An introduction to scientific and investigative techniques (2nd ed.). Boca Raton, FL: CRC Press. Also in 3rd edition, 2009.
Wu, F., Ng-Thow-Hing, V., Singh, K., Agur, A., & McKee, N. H. (2007). Computational representation of the aponeuroses as NURBS surfaces in 3 D musculoskeletal models. Computer Methods and Programs in Biomedicine, 88(2), 112–122.
Yarmey, A. D. (1995). Eyewitness and evidence obtained by other senses. Chapter 3.7 In R. Bull & D. Carson (Eds.), Handbook of psychology in legal contexts (pp. 216–273). Chichester: Wiley.
Yea, B., Konishi, R., Osaki, T., & Sugahara, K. (1994). The discrimination of many kinds of odor species using fuzzy reasoning and neural networks. Sensors & Actuators, 45, 159–165.
Yim, H. S., Kibbey, C. E., Ma, S. C., Kliza, D. M., Liu, D., Park, S. B., et al. (1993). Polymer membrane-based ion , gas , and bio-selective potentiometric sensors. Biosensors and Bioelectronics, 8, 1–38.
Yinon, J. (2003). Detection of explosives by electronic noses. Analytical Chemistry, 75(5), 99A–105A.
Young, A. W., & Ellis, H. D. (Eds.). (1989). Handbook of research on face processing. Amsterdam: Elsevier.
Zabell, S. L. (1988). The probabilistic analysis of testimony. Journal of Statistical Planning and Inference, 20, 327–354.
Zander, M. (1979). The investigation of crime: A study of cases tried at the Old Bailey. Criminal Law Review, 1979, 203–219.
Zier, J. (1993). The expert accountant in civil litigation. Toronto, ON: Butterworths.
Binder, D. A., & Bergman, P. (1984). Fact investigation: From hypothesis to proof (American Casebook Series.). St Paul, MN: West Publ.
Devlin, P. (1976). Report to the secretary of state for the Home Department of the Departmental Committee on Evidence of identification in criminal cases. London: HMSO.
de Kleer, J. (1988). A general labeling algorithm for assumption-based truth maintenance. In Proceedings of the 7th national conference on artificial intelligence, pp. 188–192.
Keppens, J., Shen, Q, & Lee, M. (2005). Compositional Bayesian modelling and its application to decision support in crime investigation. In Proceedings of the 19th international workshop on qualitative reasoning, pp. 138–148.
Keppens, J., & Zeleznikow, J. (2003). A model based reasoning approach for generating plausible crime scene scenarios from evidence In G. Sartor (Ed.), Proceedings of the ninth International Conference on Artificial Intelligence and Law (ICAIL 2003), Edinburgh, Scotland, 24–28 June 2003. New York: ACM Press, pp. 51–59.
Keppens, J., Shen, Q, & Shafer, B. (2005). Probabilistic abductive computation of evidence collection strategies in crime investigation. In Proceedings of the 10th international conference on artificial intelligence and law, pp. 215–224.
Keppens, J., & Schafer, B. (2003a). Using the box to think outside it: Creative skepticism and computer decision support in criminal investigations. In Proceedings of the IVR 21st world congress special workshop on artificial intelligence in the law: Creativity in legal problem solving. http://www.meijigakuin.ac.jp/~yoshino/documents/ivr2003/keppens schafer.pdf
Keppens, J., & Schafer, B. (2003b). Assumption based peg unification for crime scenario modelling. In Proceeding of the 2003 conference on legal knowledge and information systems; JURIX 2003: The eighteenth annual conference. Amsterdam: IOS Press. http://www.jurix.nl/pdf/j05 07.pdf
Keppens, J., Shen, Q., & Price, C. (2010). Compositional Bayesian modelling for computation of evidence collection strategies. Applied Intelligence. In press. doi://10.1007/s10489-009-0208-5
Keppens, J. (2007). Towards qualitative approaches to bayesian evidential reasoning. In Proceedings of the 11th international conference on artificial intelligence and law, pp. 17–25.
Keppens, J. (2009). Conceptions of vagueness in subjective probability for evidential reasoning. In Proceedings of the 22nd annual conference on legal knowledge and information systems, pp. 89–99.
Esuli, A. (2009a). PP-Index: Using permutation prefixes for efficient and scalable approximate similarity search. In Proceedings of the seventh workshop on Large-Scale Distributed Systems for information retrieval (LSDS IR’09), Boston, MA, 2009, pp. 17–24. http://www.esuli.it/fp content/attachs/publications/LSDS IR09.pdf
Esuli, A. (2009b). MiPai: using the PP-Index to build an efficient and scalable similarity search system. In Proceedings of the second International Workshop on Similarity Search and Applications (SISAP’09), Prague, 2009, pp. 146–148.
Esuli, A. (2010). PP-Index: Using permutation prefixes for efficient and scalable similarity search. In Proceedings of the eighteenth Italian Symposium on Advanced Database Systems (SEBD 2010), Rimini, Italy, 2010, pp. 318–325.
Bolettieri, P., Esuli, A., Falchi, F., Lucchese, C., Perego, R., & Rabitti, F. (2009). Enabling content-based image retrieval in very large digital libraries. In Proceedings of the second workshop on very large digital libraries 2 October 2009, Corfu, Greece. Pisa, Italy: DELOS, an Association for Digital Libraries, pp. 43–50.
Frowd, C. D., Pitchford, M., Bruce, V., Jackson, S., Hepton, G., Greenall, M., et al. (2010a). The psychology of face construction: Giving evolution a helping hand. Applied Cognitive Psychology. doi:10.1002/acp.1662.
Johnson, M. K. (2007). Lighting and optical tools for image forensics. Ph.D. dissertation, Dartmouth College, September 2007. Posted at http://www.cs.dartmouth.edu/farid/publications/mkjthesis07.html
Toland, J., & Rees, B. (2005). Applying case-based reasoning to law enforcement. International Association of Law Enforcement Intelligence Analysts Journal, 15.
Keppens, J., & Zeleznikow, J. (2002). On the role of model-based reasoning in decision support in crime investigation. In Proceedings of the IASTED third international conference on Law and Technology (LawTech2002). Anaheim, CA: ACTA Press, pp. 77–83.
Keppens, J., & Schafer, B. (2005). Assumption based peg unification for crime scenario modelling. In Proceeding of the 2005 conference on legal knowledge and information systems; JURIX 2005: The eighteenth annual conference. (Frontiers in Artificial Intelligence and Applications, 134). Amsterdam: IOS Press, pp. 49–58.
Frowd, C., Nelson, L., Skelton, F., Noyce, R., Heard, P., Henry, J., et al. (2010b). Interviewing techniques for Darwinian facial composite systems. Submitted.
Lisetti, C. L., & Schiano, D. J. (2000). Automatic facial expression interpretation: Where human-computer interaction, artificial intelligence and cognitive science intersect. In I. E. Dror & S. V. Stevenage (Eds.), Facial information processing: A multidisciplinary perspective. Special issue of Pragmatics & Cognition, 8(1): 185–235.
Dror, I. E., & Stevenage, S. V. (Eds.). (2000). Facial information processing: A multidisciplinary perspective. Special issue of Pragmatics & Cognition, 8(1). Amsterdam: Benjamins.
Wierzbicka, A. (2000). The semantics of human facial expressions. In I. E. Dror & S. V. Stevenage (Eds.), Facial information processing: A multidisciplinary perspective. Special issue of Pragmatics & Cognition, 8(1), 147–183.
Ng, T.-T., & Chang, S.-F. (2004). A model for image splicing. At the IEEE International Conference on Image Processing (ICIP), Singapore, October 2004.
Avcıbaş, İ., Bayram, S., Memon, N., Sankur, B., & Ramkumar, M. (2004). A classifier design for detecting image manipulations. In 2004 International Conference on Image Processing, ICIP ’04 (Vol. 4, pp. 2645–2648).
Johnson, M. K., & Farid, H. (2005). Exposing digital forgeries by detecting inconsistencies in lighting. At the ACM Multimedia and Security Workshop, 2005.
Johnson, M. K., & Farid, H. (2007b). Exposing digital forgeries through specular highlights on the eye. At the Ninth International Workshop on Information Hiding, Saint Malo, France, 2007.
Johnson, M. K., & Farid, H. (2006a). Exposing digital forgeries through chromatic aberration. At the ACM Multimedia and security Workshop, Geneva, Switzerland, 2006.
Ramamoorthi, R., & Hanrahan, P. (2001) An efficient representation for irradiance environment maps. In SIGGRAPH ’01: Proceedings of the 28th Annual Conference on Computer Graphics and Interactive Techniques. New York: ACM Press, 2001, pp. 497–500.
Farid, H. (2008, June). Digital image forensics. Scientific American, 42–47.
Debevec, P. (1998). Rendering synthetic objects into real scenes: Bridging traditional and imagebased graphics with global illumination and high dynamic range photography. In SIGGRAPH ’98: Proceedings of the 25th annual conference on computer graphics and interactive techniques. New York: ACM Press, pp. 189–198.
Prag, J., & Neave, R. (1997) Making faces: Using forensic and archaeological evidence. London: Published for the Trustees of the British Museum by British Museum Press.
Gerasimov, M. M. (about) (2007). Mikhail Gerasimov. Biographical Wikipedia [English] http://en.wikipedia.org/wiki/Mikhail_Gerasimov. Last modified on 24 April 2007, when accessed in August 2007. A Russian entry (Михаи́л Миха́йлович Гера́симов) is also available under http://ru.wikipedia.org/wiki/
Wojtas, O. (1996). Forensics unmask dead poet. The Times Higher Education Supplement, London, August 23, p. 4.
Nijboer, J. F. (2000). Challenges for the law of evidence. In C. M. Breur, M. M. Kommer, J. F. Nijboer, & J. M. Reijntjes (Eds.), New trends in criminal investigation and evidence, Vol. 2 = Proceedings of the second world conference on new trends in criminal investigation and evidence, Amsterdam, 10–15 December 1999. Antwerp, Belgium: Intersentia, 2000, pp. 1–9.
Nijboer, J. F. (2008). Current issues in evidence and procedure: Comparative comments from a Continental perspective. International Commentary on Evidence, 6(2), Article 7. http://www.bepress.com/ice/vol6/iss2/art7
Mahendra, B. (2007). Expert witness update. In an Expert Witness Supplement to The New Law Journal, 157(7294) (London, 26 October 2007), 1490–1491.
Kaye, B. H. (1995). Science and the detective: Selected readings in forensic science. Weinheim, Baden-Württemberg: VCH Verlag.
Arutyunov. (1963). See citations inside Keh (1984).
Stærkeby, M. (2002). Forensic Entomology Pages, International (website). Division of Zoology, Department of Biology, University of Oslo, Oslo, Norway. http://www.uio.no/~mostarke/forens_ent/forensic_entomology.html
Molina, D. K. (2009). Handbook of forensic toxicology for medical examiners. Boca Raton, FL: CRC Press.
Dawid, A. P., Mortera, J., & Vicard, P. (2006). Representing and solving complex DNA identification cases using Bayesian networks. In Progress in forensic genetics 11 (Proceedings of the 21st international ISFG congress). International Congress Series, Vol. 1288. Amsterdam: Elsevier Science, pp. 484–91. doi:10.1016/j.ics.2005.09.115
Dawid, A. P., & Mortera, J. (1994). Elementary Watson!: Coherent analysis of forensic evidence. Research Report 136, May. Department of Statistical Science, University College London.
Rumelhart, D. E. (1975). Notes on a schema for stories. In D. G. Bobrow & A. Collins (Eds.), Representation and understanding: studies in cognitive science (pp. 185–210). New York: Academic.
Pye, K. (2006). Evaluation of the significance of geological and soil trace evidence (abstract). In A. Ruffell (Ed.), Abstract book of geoscientists at crime scenes: First, inaugural meeting of the Geological Society of London, 20 December 2006 (pp. 24–15). Forensic Geoscience Group. http://www.geolsoc.org.uk/pdfs/FGtalks&abs_pro.pdf
Bodziak, W. J. (2000). Footwear impression evidence. Boca Raton, FL: CRC Press.
Galton, A. P. (1987). Temporal logics and their applications. London: Academic.
Wooldridge, M., & van der Hoek, W. (2005). On obligations and normative ability: Towards a logical analysis of the social contract. Journal of Applied Logic, 3, 396–420.
Knight, B., Nissan, E., & Ma, J. (Eds.). (1999). Temporal logic in engineering. Special issue, Artificial Intelligence for Engineering Design, Analysis and Manufacturing (AIEDAM), 13(2).
Cohn, A. G., Gooday, J. M., & Bennett, B. (1995). A comparison of structures in spatial and temporal logics. In R. Casati & G. White (Eds.), Philosophy and the cognitive sciences (pp. 409–422). Vienna: Holder-Pichler-Tempsky.
Brace, N., Pike, G., Kemp, R., Tyrner, J., & Bennet, P. (2006). Does the presentation of multiple facial composites improve suspect identification? Applied Cognitive Psychology, 20, 213–226.
Bruce, V., Ness, H., Hancock, P. J. B., Newman, C., & Rarity, J. (2002). Four heads are better than one: Combining face composites yields improvements in face likeness. Journal of Applied Psychology, 87(5), 894–902.
Poulin, D., Mackaay [sic], E., Bratley, P., & Frémont, J. (1992). Time server: A legal time specialist. In A. Martino (Ed.), Expert systems in law (pp. 295–312). Amsterdam: North-Holland.
Vila, L., & Yoshino, H. (1995). Temporal representation for legal reasoning. In: Proceedings of the Third International Workshop on Legal Expert Systems for the CISG, May 1995.
Vila, L., & Yoshino, H. (1998). Time in automated legal reasoning. In A. A Martino & E. Nissan (Eds.), Law, computers and artificial intelligence: Special issue on Formal Models of Legal Time. In Information and Communications Technology Law, 7(3), 173–197.
Knight, B., Ma, J., & Nissan, E. (1998). Representing temporal knowledge in legal discourse. In A. A. Martino & E. Nissan (Eds.), Formal models of legal time., Special issue, Information and Communications Technology Law, 7(3), 199–211.
Allen, J. F. (1983a). Recognizing intentions from natural language utterances. Chapter 2 In M. Bradie & R. C. Berwick (Eds.), Computational models of discourse (pp. 108–166). Cambridge, MA: MIT Press.
Farook, D. Y., & Nissan, E. (1998). Temporal structure and enablement representation for mutual wills: A Petri-net approach. In A. A. Martino & E. Nissan (Eds.), Formal models of legal time, special issue, Information and Communications Technology Law, 7(3), 243–267.
Valette, R., & Pradin-Chézalviel, B. (1998). Time Petri nets for modelling civil litigation. In A. A. Martino & E. Nissan (Eds.), Formal models of legal time, special issue, Information and Communications Technology Law, 7(3), 269–280.
Raskin, J.-F., Tan, Y.-H., & van der Torre, L. W. N. (1996). Modeling deontic states in Petri nets. Discussion Paper 111. Rotterdam, The Netherlands: Erasmus University Research Institute for Decision and Information Systems (EURIDIS).
Arbabi, E., Boulic, R., & Thalmann, D. (2007a). A fast method for finding maximum range of motion in the hip joint. In Computer assisted orthopaedic surgery: 7th annual meeting of CAOS, international proceedings (pp. 497–500). [CAOS’07.] Germany: Pro BUSINESS, on behalf of the International Society for Computer Assisted Orthopaedic Surgery. Also, Report VRLAB CONF 2007 139. Lausanne: Virtual Reality Lab at the Swiss Federal Institute of Technology. http://infoscience.epfl.ch/getfile.py?recid=109304&mode=best
Arbabi, E., Boulic, R., & Thalmann, D. (2007b). A fast method for finding range of motion in the human joints. In Proceedings of the 29th annual international conference of the IEEE Engineering in Medicine and Biology Society (EMBS’07), Lyon, France, August 23–26, 2007. Also, Report VRLAB CONF 2007 140. Lausanne: Virtual Reality Lab at the Swiss Federal Institute of Technology.
Abaci, T., Mortara, M., Patane, G., Spagnuolo, M., Vexo, F., & Thalmann, D. (2005). Bridging geometry and semantics for object manipulation and grasping. In Proceedings of workshop towards Semantic Virtual Environments (SVE 2005). Also, Report VRLAB CONF 2005 021. Lausanne: Virtual Reality Lab at the Swiss Federal Institute of Technology. http://infoscience.epfl.ch/getfile.py?recid=99017&mode=best
Gutiérrez, M., Thalmann, D., Vexo, F., Moccozet, L., Magnenat-Thalmann, N., Mortara, M., et al. (2005). An ontology of virtual humans: Incorporating semantics into human shapes. In Proceedings of the workshop towards Semantic Virtual Environments (SVE05), Villars, Switzerland, March 2005, pp. 57–67. Posted at http://vrlab.epfl.ch/Publications of the Virtual Reality Lab at the Swiss Federal Institute of Technology in Lausanne.
Sawday, J. (1996). The body emblazoned: Dissection and the human body in renaissance culture. London: Routledge.
Taubes, G. (2002). An interview with Dr. Michael I. Miller. In Cytes, ISI accessible at http://www.incites.com/scientists/DrMichaelIMiller.html
Linford, N. (2002). The English heritage geophysical survey database. http://www.eng h.gov.uk/SDB/
Mellett, J. S. (1996). GPR in forensic and archaeological work: Hits and misses. In Symposium on the Application of Geophysics to Environmental Engineering Problems (SAGEEP), 1991. Environmental & Engineering Geophysical Society Co., USA, pp. 487–491.
Cui, Z., Cohn, A. G., & Randell, D. A. (1992). Qualitative simulation based on a logical formalism of space and time. In Proceedings of AAAI 92. Menlo Park, CA: AAAI Press, pp. 679–684.
Hayes, P. J. (1985). Naive physics I: Ontology for liquids. Chapter 3 In J. R. Hobbs & R. C. Moore (Eds.), Formal theories of the commonsense world. Norwood, NJ: Ablex.
Pearce, T. C., Schiffman, S. S., Nagle, H. T., & Gardner, J. W. (Eds.). (2002). Handbook of machine olfaction: Electronic nose technology. Weinheim, Baden-Württemberg: Wiley VCH. doi://10.1002/3527601597
Gardner, J. W., & Bartlett, P. N. (1999). Electronic noses: Principles and applications. Oxford: Oxford University Press.
Pamula, V. K. (2003). Detection of explosives. Chapter 23 In T. C. Pearce, S. S. Schiffman, H. T. Nagle, & J. W. Gardner (Eds.), Handbook of machine olfaction: Electronic nose technology (pp. 547–560). Weinheim, Baden-Württemberg: Wiley VCH Verlag. Published online: 2004. doi://10.1002/3527601597.ch23
Gardner, J. W., & J. Yinon, J. (Eds.). (2004). Proceedings of the NATO advanced research workshop on electronic noses and sensors for the detection of explosives. (NATO Science Series 2003, Vol. 159). Dordrecht: Kluwer.
Klock, B. A. (2001, April). Project plan for the evaluation of X ray threat detection of explosives at different subcertification weights. DOT/FAA/AR 01/81, Washington, DC: Office of Aviation Research. http://www.tc.faa.gov/its/worldpac/techrpt/ar01 81.pdf
Casalinuovo, I. A., Di Pierro, D., Coletta, M., & Di Francesco, P. (2006). Application of electronic noses for disease diagnosis and food spoilage detection. Sensors, 6, 1428–1439.
Davis, O. (1999). Palynomorphs. At the website whose address is Retrieved in March 2007 http://www.geo.arizona.edu/palynology/ppalydef.html
Hoen, P. (1999). The glossary: Part 4 (P–R). Laboratory of Palaeobotany and Palynology, University of Utrecht. Retrieved in March 2007 http://www.bio.uu.nl/~palaeo/glossary/glos p4.htm. Part of his Glossary of Pollen and Spore Terminology, 2nd edn. (http://www.bio.uu.nl/~palaeo/glossary/glos int.htm). First edition (LPP Contribution Series, No. 1, 1994) was by W. Punt, S. Blackmore, S. Nilsson, & A. Le Thomas [sic].
Tschudy, R. H. (1961). Palynomorphs as indicators of facies environments in Upper Cretaceous and Lower Tertiary strata, Colorado and Wyoming. Wyoming Geological Association Guidebook 16. In Annual Field Conference, pp. 53–59.
McBurney, P., & Parsons, S. (2001). Intelligent systems to support deliberative democracy in environmental regulation. In D. M. Peterson, J. A. Barnden, & E. Nissan (Eds.), Artificial Intelligence and Law, special issue, Information and Communications Technology Law, 10(1), 79–89.
de Vey Mestdagh, K. (1999). Can computers administer the law? An expert system for environmental permit law. In Proceedings of legal knowledge based systems: JURIX 1999. Nijmegen, The Netherlands: Gerard Noodt Instituut, pp. 134–135.
Henry, R. C., Lewis, C. W., & Collins, J. F. (1994). Vehicle related hydrocarbon source composition from ambient data: The GRACE/SAFER method. Environmental Science and Technology, 28, 823–832.
Henry, R. C., Spiegelman, C. H., Collins, J. F., & Park, J. F. [sic] (1997). Reported emissions of organic gases are not consistent with observations. Proceedings of the National Academy of Sciences USA, 94, 6596–6599.
Srihari, S. N., & Su, C. (2008). Computational methods for determining individuality. In Computational Forensics: Proceedings of the International Workshop, Washington, DC. (Lecture Notes in Computer Science, Vol. 5158). Berlin: Springer, pp. 11–21.
Dawid, A. P. (1998). Modelling issues in forensic inference. In 1997 ASA proceedings Section on Bayesian Statistics, pp. 182–186. Alexandria, VA: The American Statistical Association.
Dawid, A. P. (2001b). Bayes’s theorem and weighing evidence by juries. Research Report 219, April. Department of Statistical Science, University College London.
Dawid, A. P. (2002). Bayes’s theorem and weighing evidence by juries. In R. Swinburne (Ed.), Bayes’s theorem. Proceedings of the British Academy, 113,71–90.
Dawid, A. P. (2005a). Probability and statistics in the law. In Z. Ghahramani & R.G. Cowell (Eds.) Proceedings of the tenth international workshop on artificial intelligence and statistics, January 6–8 2005, Barbados. (Online at http://tinyurl.com/br8fl).
Dawid, A. P., Mortera, J., Pascali, V. L., & van Boxel, D. W. (2002). Probabilistic expert systems for forensic inference from genetic markers. Scandinavian Journal of Statistics, 29, 577–595.
Bleay, S. (2009). Fingerprint development and imaging: Fundamental research to operational implementation. PowerPoint presentation, 1 July 2009. Home Office Scientific Development Branch, Sandridge, England. Posted at the website of the Higher Education Academy, York Science Park, York, England. Retrieved in 2010 at http://www.heacademy.ac.uk/assets/ps/documents/FORREST/2009/presentations/k2_bleay.pdf
Moenssens, A. (1999). Is fingerprint identification a “science”? Forensic-Evidence.com. http://www.forensicevidence.com/site/ID0004 2.html
Brislawn, C. M., Bradley, J. N., Onyshczak, R. J., & Hopper, T. (1996). The FBI compression standard for digitized fingerprint images. In Proceedings of the international society for optical engineering Denver, CO, pp. 344–355.
Costello, B. D., Gunawardena, C. A., & Nadiadi, Y. M. (1994). Automated coincident sequencing for fingerprint identification. In Proceedings of the IEE colloquium on image processing for biometric measurement London, pp. 3.1–3.5.
Emiroglu, I., & Akhan, M. B. (1997). Preprocessing of fingerprint images. In Proceedings of the IEE European conference on security and detection, Hertfordshire, England, pp. 147–151.
Kristensen, T. (2010). Fingerprint identification: A support vector machine approach. In Proceedings of the second International Conference on Agents and Artificial Intelligence, ICAART 2010, Valencia, Spain, 22–24 January 2010, pp. 451–458.
Lee, C.-J., & Wang, S.-D. (1999). A Gabor filter-base approach to fingerprint recognition. In Proceedings of the IEEE workshop on Signal Processing Systems (SiPS 99), pp. 371–378.
Hao, Y., Tan, T., & Wang, Y. (2002). An effective algorithm for fingerprint matching. In TENCON ’02. Proceedings. 2002 IEEE region 10 conference on computers, communications, control and power engineering, 28–31 October 2002, Vol. 1, pp. 519–522. Also, technical report, National Laboratory of Pattern Recognition, Institute of Automation, Chinese Academy of Sciences, Beijing. http://nlpr web.ia.ac.cn/english/irds/papers/haoying/tencon.pdf
Ross, A., & Jain, A. K. (2003). Information fusion in biometrics. Pattern Recognition Letters, 24(13), 2115–2125.
Kenji, T., Aoki, T., Sasaki, Y., Higuchi, T., & Kobayashi, K. (2003). High-accuracy subpixel image registration based on phase-only correlation. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, E86 A(8), 1925–2934.
Akin, L. L. (2005). Blood interpretation at crime scenes. The Forensic Examiner, Summer 2005, 6–10. http://www.onsceneforensics.com/PDFs%20Forms/ACFEI_BLOOD_SPATTER_AKIN.pdf
Hueske, E.E. (2002). Shooting incident investigation/Reconstruction tranining manual.
Lukáš, J., Fridrich, J., & Goljan, M. (2006). Detecting digital image forgeries using sensor pattern noise. In Proceedings of the SPIE, Vol. 6072.
Nissan, E. (1997b). Notions of place, II. In A. A. Martino (Ed.), Logica delle norme (pp. 303–361). Pisa, Italy: SEU.
EnVision (2002). Computational anatomy: An emerging discipline. EnVision, 18(3). National Partnership for Advanced Computational Infrastructure. http://www.npaci.edu/enVision/v18.3/anatomy.html
Donnelly, L. J. (2002c, May). Finding the silent witness: How forensic geology helps solve crimes. All-Party Parliamentary Group for Earth Science, Westminster Palace, Houses of Parliament. The Geological Society of London. Geoscientist, 12(5), 24.
Fasel, I. R., Bartlett, M. S., & Movellan, J. R. (2002). A comparison of Gabor filter methods for automatic detection of facial landmarks. In Proceedings of the fifth international conference on automatic face and gesture recognition, Washington, DC, 21–21 May 2002, pp. 242–246.
Kuglin, C. D., & Hines, D. C. (1975). The phase correlation image alignment method. In Proceedings of the international conference on cybernetics and society, pp. 163–165.
Staples, E. J. (2000). Electronic nose simulation of olfactory response containing 500 orthogonal sensors in 10 seconds. In Proceedings of the 1999 IEEE Ultrasonics Frequency Control and Ferroelectrics Symposium, Lake Tahoe, CA, 2000, pp. 307–313.
Amin, R., Bramer, M., & Emslie, R. (2003). Intelligent data analysis for conservation: Experiments with rhino horn fingerprint identification. Knowledge Based Systems, 16(5–6).
Jain, A. K., Ross, A., & Prabhakar, S. (2001). Fingerprint matching using minutiae and texture features. In Proceedings of Image Processing International Conference (ICIP), Thessaloniki, Greece, 7–10 October 2001, Vol. 3, pp. 282–285.
FORident Software. (2009). HemoSpat validation. [A white paper.] FORidenti Software Technical Paper. Ottawa, ON: FORident Software. 9 August 2009. http://hemospat.com/technical_papers/pdf/FORident%20Software%20Technical%20Paper%20-%20HemoSpat%20Validation.pdf
Shurmer, H. V., Gardner, J. W., & Chan, H. T. (1989). The application of discrimination techniques to alcohols and tobacco using tin oxide sensors. Sensors & Actuators, 18, 359–369.
Maloney, A., Nicloux, C., Maloney, K., & Heron, F. (2001). One-sided impact spatter and area-of-origin calculations. Journal of Forensic Identification, 61(2), 123–135. http://hemospat.com/papers/pdf/JFI%20-%20One-Sided%20Impact%20Spatter%20and%20Area-of-Origin%20Calculations.pdf
Ito, K., Nakajima, H., Kobayashi, K., Aoki, T., & Higuchi, T. (2004). A fingerprint matching algorithm using phase-only correlation. IEICE Transactions on Fundamentals, E87-A(3), 682–691. (IEICE stands for ‘The Institute of Electronics, Information and Communication Engineers’).
Staples, E. J. (1999). Electronic nose simulation of olfactory response containing 500 orthogonal sensors in 10 seconds. In Proceedings of the 1999 IEEE Ultrasonics Frequency Control and Ferroelectrics Symposium, Lake Tahoe, CA, 2000, pp. 307–313.
Persaud, K. C. (2005). Medical applications of odor-sensing devices. International Journal of Lower Extremities Wounds, 4, 50–56.
Laufer, B. (1913). History of the fingerprint system. In Smithsonian Report for 1912 (pp. 631–652) (with 7 plates). Washington, DC: Smithsonian Institution.
Laufer, B. (1917, May 25). Concerning the history of finger-prints. Science, 504, 505.
Latourette, K. S. (1936). Biographical Memoir of Berthold Laufer, 1874–1934. Biographical Memoirs, 18(3). National Academy of Sciences of the United States of America. http://books.nap.edu/html/biomems/blaufer.pdf
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Copyright information
© 2012 Springer Science+Business Media B.V.
About this chapter
Cite this chapter
Nissan, E. (2012). The Forensic Disciplines: Some Areas of Actual or Potential Application. In: Computer Applications for Handling Legal Evidence, Police Investigation and Case Argumentation. Law, Governance and Technology Series, vol 5. Springer, Dordrecht. https://doi.org/10.1007/978-90-481-8990-8_8
Download citation
DOI: https://doi.org/10.1007/978-90-481-8990-8_8
Published:
Publisher Name: Springer, Dordrecht
Print ISBN: 978-90-481-8989-2
Online ISBN: 978-90-481-8990-8
eBook Packages: Humanities, Social Sciences and LawSocial Sciences (R0)