Abstract
One of the most used authentication methods is based on short secrets like password, where usually the hash of the secrets are stored in a central database. In case of server compromise the secrets are vulnerable to theft. A possible solution to this problem to apply distributed systems. We propose a mutual authentication protocol with key agreement, where identity verification is carried out by multiple servers applying secret sharing technology on server side. The protocol results in a session key which provides the confidentiality of the later messages between the participants. In our solution we also achieve robustness and scalability as well. To show that the proposed protocol is provably secure, we apply the threshold hybrid corruption model. We assume that among the randomly chosen k servers, there is always at least one uncorrupted and the authentication server reveals at most the long-lived keys. We prove that the protocol is secure in the random oracle model, if Message Authentication Code (MAC) is universally unforgeable under an adaptive chosen-message attack, the symmetric encryption scheme is indistinguishable under chosen plaintext attack, moreover Elliptic Curve Computational Diffie-Hellman assumption holds in the elliptic curve group.
This work was supported by the construction EFOP-3.6.2-16-2017-00015 and the SETIT Project (no. 2018-1.2.1-NKP-2018-00004), which has been implemented with support provided by the European Union, co-financed by the European Social Fund and the National Research, Development and Innovation Fund of Hungary, financed under the 2018-1.2.1-NKP funding scheme.
This is a preview of subscription content, log in via an institution.
Buying options
Tax calculation will be finalised at checkout
Purchases are for personal use only
Learn about institutional subscriptionsReferences
Acar, T., Belenkiy, M., Küpçü, A.: Single password authentication. Comput. Netw. 57(13), 2597–2614 (2013)
Bagherzandi, A., Jarecki, S., Saxena, N., Lu, Y.: Password-protected secret sharing. In: ACM Conference on Computer and Communications Security (2011)
Bellare, M., Pointcheval, D., Rogaway, P.: Authenticated key exchange secure against dictionary attacks. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 139–155. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-45539-6_11
Bellare, M., Rogaway, P.: Entity authentication and key distribution. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 232–249. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48329-2_21
Bellare, M., Rogaway, P.: Provably secure session key distribution: the three party case. In: Proceedings of the Twenty-Seventh Annual ACM Symposium on Theory of Computing, pp. 57–66 (1995)
Bellovin, S.M., Merritt, M.: Encrypted key exchange: password-based protocols secure against dictionary attacks. In: Proceedings of the 1992 IEEE Computer Society Symposium on Research in Security and Privacy. IEEE (1992)
Blake-Wilson, S., Johnson, D., Menezes, A.: Key agreement protocols and their security analysis. In: Darnell, M. (ed.) Cryptography and Coding 1997. LNCS, vol. 1355, pp. 30–45. Springer, Heidelberg (1997). https://doi.org/10.1007/BFb0024447
Boyko, V., MacKenzie, P., Patel, S.: Provably secure password-authenticated key exchange using Diffie-Hellman. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 156–171. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-45539-6_12
Boyen, X.: Hidden credential retrieval from a reusable password. In: Proceedings of the 4th International Symposium on Information, pp. 228–238. ACM (2009)
Boyen, X.: HPAKE: password authentication secure against cross-site user impersonation. In: Garay, J.A., Miyaji, A., Otsuka, A. (eds.) CANS 2009. LNCS, vol. 5888, pp. 279–298. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-10433-6_19
Brainard, J., Juels, A., Kaliski, B., Szydlo, M.: A new two-server approach for authentication with short secrets. In: Proceeding SSYM 2003, Proceedings of the 12th Conference on USENIX Security Symposium, vol. 12, pp. 1–14 (2003)
Chen, N., Jiang, R.: Security analysis and improvement of user authentication framework for cloud computing. J. Netw. 9(1), 198–203 (2014)
Choudhury, A.J., Kumar, P., Sain, M.: A strong user authentication framework for cloud computing. In: Proceedings of IEEE Asia-Pacific Services Computing Conference, pp. 110–115 (2011)
Ford, W., Kaliski, B.S.: Server-assisted generation of a strong secret from a password. In: Enabling Technologies: Infrastructure for Collaborative Enterprises, WET ICE 2000. IEEE (2000)
Hassanzadeh-Nazarabadi, Y., Küpçü, A., Özkasap, O.: LightChain: a DHT-based blockchain for resource constrained environments. arXiv preprint arXiv:1904.00375 (2019)
Huszti, A., Oláh, N.: A simple authentication scheme for clouds. In: Proceedings of IEEE Conference on Communications and Network Security (CNS), pp. 565–569 (2016)
Hwang, M.S., Li, L.H.: A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 46(1), 28–30 (2000)
Jarecki, S., Kiayias, A., Krawczyk, H.: Round-optimal password-protected secret sharing and T-PAKE in the password-only model. In: Sarkar, P., Iwata, T. (eds.) ASIACRYPT 2014. LNCS, vol. 8874, pp. 233–253. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-45608-8_13
İşler, D., Küpçü, A.: Threshold single password authentication. In: Garcia-Alfaro, J., Navarro-Arribas, G., Hartenstein, H., Herrera-Joancomartí, J. (eds.) ESORICS/DPM/CBT -2017. LNCS, vol. 10436, pp. 143–162. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-67816-0_9
Işler, D., Küpçü, A: Distributed Single Password Protocol Framework. IACR Cryptol. ePrint Arch., p. 976 (2018)
Katz, J., MacKenzie, P., Taban, G., Gligor, V.: Two-server password-only authenticated key exchange. In: Ioannidis, J., Keromytis, A., Yung, M. (eds.) ACNS 2005. LNCS, vol. 3531, pp. 1–16. Springer, Heidelberg (2005). https://doi.org/10.1007/11496137_1
Katz, J., Ostrovsky, R., Yung, M.: Efficient password-authenticated key exchange using human-memorable passwords. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 475–494. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44987-6_29
Ku, W.C., Chen, S.M.: Weaknesses and improvements of an efficient password based remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 50(1), 204–207 (2004)
Kurtz, G., Alperovitch, D., Zaitsev, E.: Hacking Exposed: Beyond the Malware, RSA 2015 (slide deck) (2015). https://www.rsaconference.com/writable/presentations/file_upload/expt10_hackingexposedbeyondthemalware.pdf
MacKenzie, P., Shrimpton, T., Jakobsson, M.: Threshold password-authenticated key exchange. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 385–400. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_25
Merkle, R.C.: A digital signature based on a conventional encryption function. In: Pomerance, C. (ed.) CRYPTO 1987. LNCS, vol. 293, pp. 369–378. Springer, Heidelberg (1988). https://doi.org/10.1007/3-540-48184-2_32
Soria-Machado, M., Abolins, D., Boldea, C., Socha, K.: Kerberos Golden Ticket Protection, Mitigating Pass-the-Ticket on Active Directory, CERT-EU Security Whitepaper 2014-007 (2016)
Di Raimondo, M., Gennaro, R.: Provably secure threshold password-authenticated key exchange. In: Biham, E. (ed.) EUROCRYPT 2003. LNCS, vol. 2656, pp. 507–523. Springer, Heidelberg (2003). https://doi.org/10.1007/3-540-39200-9_32
Saeed, M.E.S., Liu, Q.-Y., Tian, G.Y., Gao, B., Li, F.: AKAIoTs: authenticated key agreement for Internet of Things. Wirel. Netw. 25(6), 3081–3101 (2018). https://doi.org/10.1007/s11276-018-1704-5
Sood, S.K., Sarje, A.K., Singh, K.: A secure dynamic identity based authentication protocol for multi-server architecture. J. Netw. Comput. Appl. 34(2), 609–618 (2011)
Wu, T., Lee, Z., Obaidat, M.S., Kumari, S., Kumar, S., Chen, C.: An authenticated key exchange protocol for multi-server architecture in 5G networks. IEEE Access 8, 28096–28108 (2020). https://doi.org/10.1109/ACCESS.2020.2969986
Acknowledgement
We thank the reviewers for their valuable comments which helped to improve the proposed protocol.
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Appendix A
Appendix A
Proof
-
Case 2.
Let \(\mathcal {A}\,\texttt { succeeds}\) denote the event that in \(\mathcal {A}\)’s experiment there is a client oracle \(\prod _{I,J_v}^s\) that is accepted, but there is no server oracle \(\prod _{J_v,I}\) having matching conversation to \(\prod _{I,J_v}^s\). We assume that
$$Pr[\mathcal {A}\,\texttt { succeeds}]=n_C(\kappa ),$$where \(n_C(\kappa )\) is non-negligible.
We can construct a polynomial time adversary that is able to distinguish two plaintexts under chosen plaintext attack against the symmetric encryption scheme.
Challenger generates a key K and flips a bit b. \(\mathcal {F}\) is given an oracle access to \(Enc_K(.)\). \(\mathcal {F}\)’s task is to output a bit \(b'\) on inputs \(m_0,m_1\) chosen by \(\mathcal {F}\) and \(m_b\). \(\mathcal {F}\) picks the protocol participants and a session \(l\in \{1,\dots , T_3(\kappa )\}\), let \(\varDelta =\{I,J_1,\dots ,J_k\}\) denote the identities. Similarly to Case 1, \(\prod _{I,J_v}\) denotes the client, \(\prod _{J_v,I}\) the communicating server and \(\prod _{J_u,J_v}\) the uncorrupted server oracle. If \(u = v\), then the server communicating with the client is uncorrupted. \(\mathcal {F}\) simulates the key generation \(\Gamma \) in the same way as in Case 1. \(\mathcal {F}\) generates long-lived keys \(K_i\) and symmetric encryption keys \(\overline{K}_i\) for corrupted servers for the security parameter \(\kappa \). \(\mathcal {F}\) answers \(\mathcal {A}\)’s oracle queries as follows.
\(\mathcal {F}\) answers queries to oracles \(H(.),H_0(.)\), \(\texttt {Corrupt}\), \(\texttt {Reveal}\) in the same way as in Case 1. \(\mathcal {F}\) answers \(\texttt {Send}\) queries according to \(\Pi \) with the knowledge of the keys of corrupted servers, if they are not sent to \(\prod _{I,J_v}\), \(\prod _{J_v,I}\) or \(\prod _{J_u,J_v}\). If \(\mathcal {A}\) does not involve \(\prod _{J_v,I}\) as a server oracle which communicates to the client oracle \(\prod _{I,J_v}\) and other server oracles \(\prod _{I,J_i}\), then \(\mathcal {F}\) gives up. We consider the case when \(\prod _{J_v,I}\) is weakly corrupted (\(u\ne v\)). If \(\mathcal {A}\) does not invoke \(\prod _{I,J_v}\) as an initiator oracle, then \(\mathcal {F}\) gives up, otherwise \(\mathcal {A}\) asks oracle query \(\texttt {Send}(\prod _{I,J_v}^s, \lambda )\). \(\mathcal {F}\) responses \(M_1=I||J_1||\dots ||J_k||m_0||\dots ||m_k,\) with \(m_j=(Mac_{K_j}(r_j\,\oplus \,J_j)\,\oplus \,w_j)||r_j\) and \(m_v=(Mac_{K_v}(r_v\,\oplus \,xG\oplus J_v)\,\oplus \,w_v)||r_v||xG\), where \(r_i\in \{0,1\}^{\sigma },x\in \mathbb {Z}_n^*, w_i\) and the MAC key \(K_u\) for the uncorrupted server are randomly chosen by \(\mathcal {F}\). Some time later \(\mathcal {A}\) asks oracle queries to Enc(.) and eventually asks query \(\texttt {Send}(\prod _{J_u,J_v}, I||m_u)\).
\(\mathcal {F}\) answers with \(Enc_K(m_b)\). \(\mathcal {F}\) perfectly simulates uncorrupted server \(\prod _{J_u,J_v}\) to \(\mathcal {A}\), since without the knowledge of the MAC key \(\mathcal {A}\) cannot verify correctness of \(m_u\). \(\mathcal {A}\) some time later asks xyG to oracle \(H_0(.)\) and \(H_0(xyG) || yG || xG || w\) to oracle H(.) and asks query \(\texttt {Send}(\prod _{I,J_v}\), \(H(H_0(xyG) || yG || xG || w) || yG)\). \(\mathcal {F}\) answers queries, replies \(H(H_0(xyG)||yG||xG)\), gets accepted and checks whether \(w=H(w_1||\dots ||m_0||\dots ||w_{k-1})\), where \(w_1,\dots , w_{k-1}\) denote the random values generated for corrupted servers. If the equality holds, then \(\mathcal {F}\) outputs bit \(b'=0\), otherwise \(b'=1\).
Assume that \(\mathcal {A}\) is successful, event \(\mathcal {A}\,\texttt { succeeds}\) happens with \(n_C(\kappa )\) non-negligible probability. \(\mathcal {F}\) outputs the correct \(b'\). We show that \(\mathcal {F}\) wins its experiment with non-negligible probability. For the analysis the probability that \(\mathcal {F}\) chooses the correct participants \(\varDelta \), session l and succeeds is calculated:
$$\begin{aligned} \xi _2(\kappa )=\frac{n_C(\kappa )}{T_1(\kappa )T_2(\kappa )\left( {\begin{array}{c}T_2(\kappa )-1\\ k-1\end{array}}\right) T_3(\kappa )}-\lambda (\kappa ), \end{aligned}$$(2)where \(\lambda (\kappa )\) denotes the probability that \(\mathcal {F}\) previously calculated the flow, including the case of uncorrupted \(\prod _{J_v,I}\), when \(\mathcal {F}\) calculates correct MAC message-tag pair for \(\prod _{J_v,I}\). Similarly to Case 1. \(\xi _2(\kappa )\) is non-negligible, if \(n_C(\kappa )\) is non-negligible, \(T_i(\kappa )\) (i = 1,...,3) is polynomial in \(\kappa \) and \(\lambda (\kappa )\) is negligible. That contradicts the security assumption of the symmetric encryption, hence \(n_C(\kappa )\) must be negligible.
We turn to condition 4. Consider an adversary \(\mathcal {A}\) and suppose that \(Adv^{\mathcal {A}}(\kappa )\) is non-negligible.
-
Case 3.
Let \(\mathcal {A}\,\texttt { succeeds}\) against \(\prod _{I,J}^s\) denote the event that \(\mathcal {A}\) asks \(\texttt {Test}(\prod _{I,J}^{s})\) query and outputs the correct bit. Hence
$$Pr[\mathcal {A}\,\texttt {succeeds}]=\frac{1}{2}+n(\kappa ),$$where \(n(\kappa )\) is non-negligible.
Let \(A_{\kappa }\) denote the event that \(\mathcal {A}\) picks either a server or a client oracle \(\prod _{I,J}^s\) and asks its \(\texttt {Test}\) query such that oracle \(\prod _{I,J}^s\) has had a matching conversation to \(\prod _{J,I}^t\).
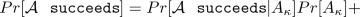

According to the previous section \(Pr[\overline{A}_{\kappa }]=\mu (\kappa )\), where \(\mu (\kappa )\in \{n_C(\kappa ),n_S(\kappa )\}\) and \(Pr[A_{\kappa }]=1-\mu (\kappa )\), where \(\mu (\kappa )\) is negligible, hence
$$\frac{1}{2}+n(\kappa )\le Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }]Pr[A_{\kappa }]+\mu (\kappa )$$and we get
$$\frac{1}{2}+n_1(\kappa )= Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }],$$for a non-negligible \(n_1(\kappa )\). Let \(B_{\kappa }\) denote the event that for given aG, bG adversary \(\mathcal {A}\) or any other oracle besides \(\prod _{I,J}^{s}\) or \(\prod _{J,I}^t\) asks abG to oracle \(H_0(.)\). \(Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }]=Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }\wedge B_{\kappa }]Pr[B_{\kappa }|A_{\kappa }]+Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }\wedge \overline{B}_{\kappa }]Pr[\overline{B}_{\kappa }|A_{\kappa }]\). Since \(Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }\wedge \overline{B}_{\kappa }]=\frac{1}{2}\),
$$\begin{aligned} \frac{1}{2}+n_1(\kappa )\le Pr[\mathcal {A}\,\texttt { succeeds}|A_{\kappa }\wedge B_{\kappa }]Pr[B_{\kappa }|A_{\kappa }]+\frac{1}{2}, \end{aligned}$$(3)hence \(Pr[B_{\kappa }|A_{\kappa }]\) is non-negligible.
We construct a polynomial time adversary \(\mathcal {F}\) that for given aG, bG calculates \(ECCDH(aG,bG)=abG\). \(\mathcal {F}\) picks the protocol participants, \(\varDelta =\{I,J_1,\dots ,J_k\}\) denotes the identities. Similarly to Case 1, \(\prod _{I,J_v}\) denotes the client, \(\prod _{J_v,I}\) the communicating server and \(\prod _{J_u,J_v}\) the uncorrupted server oracle. If \(u = v\), then the server communicating with the client is uncorrupted. \(\mathcal {F}\) sets \(par=(E, q, \mathbf{n} , G, H, H_0, Mac)\) public parameters, where \(G\in E(\mathbb {F}_q)\) is a generator of order n. \(\mathcal {F}\) also simulates the key generation \(\Gamma \) in the same way as in Case 1.
\(\mathcal {F}\) answers queries to oracles \(H(.),H_0(.)\), \(\texttt {Corrupt}\), \(\texttt {Reveal}\) in the same way as in Case 1. Let \(T_4(\kappa )\) denote the polynomial bound on the number of queries allowed to ask to oracle \(H_0(.)\). \(\mathcal {F}\) randomly picks \(j\in \{1, \dots , T_4(\kappa )\}\), assuming that jth query will be on abG. \(\mathcal {F}\) answers \(\texttt {Send}\) queries according to \(\Pi \) except for queries to \(\prod _{I,J_v}^s\) and \(\prod _{J_v,I}^t\). \(\mathcal {F}\) generates messages to \(\prod _{I,J_v}^s\) and \(\prod _{J_v,I}^t\) in a way that instead of choosing x, y randomly inserts aG, bG as inputs. The MAC computations of message \(M_1\) are calculated by the randomly chosen keys \(K_i\) and aG or bG is inserted. \(M_2\) sent to \(\prod _{I,J_v}^s\) is constructed as a concatenation of h and bG or aG, respectively, where h is a freshly generated random value. If \(\mathcal {A}\) does not ask j queries to \(H_0(.)\), then \(\mathcal {F}\) gives up. After the jth query \(\mathcal {F}\) stops and outputs the jth query. If \(\prod _{I,J_v}^s\) and \(\prod _{J_v,I}^t\) do not have matching conversation, then \(\mathcal {F}\) gives up.
The probability that \(\mathcal {F}\) succeeds is at least
$$\xi _3(\kappa )=\frac{n_1(\kappa )}{T_1(\kappa )T_2(\kappa )\left( {\begin{array}{c}T_2(\kappa )-1\\ k-1\end{array}}\right) T_3(\kappa )^2T_4(\kappa )}-\mu (\kappa ),$$that is non-negligible. This contradicts to the ECCDH assumption, hence \(n_1(\kappa )\) and \(Adv^{\mathcal {A}}(\kappa )\) must be negligible.
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Huszti, A., Oláh, N. (2020). Provably Secure Scalable Distributed Authentication for Clouds. In: Krenn, S., Shulman, H., Vaudenay, S. (eds) Cryptology and Network Security. CANS 2020. Lecture Notes in Computer Science(), vol 12579. Springer, Cham. https://doi.org/10.1007/978-3-030-65411-5_10
Download citation
DOI: https://doi.org/10.1007/978-3-030-65411-5_10
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-65410-8
Online ISBN: 978-3-030-65411-5
eBook Packages: Computer ScienceComputer Science (R0)