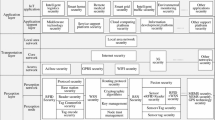
Abstract
The emerging use of Wireless Multimedia Sensor Networks (WMSNs) and communication facilities have increased the need for network security measures to protect different types of multimedia data either real time or non-real time during the transmission period. A lot of researchers are becoming more interested on secure WMSNs due to the broad application necessities which can be range over smart environment, security surveillance and smart health-care; so requirements on secure aggregation of multimedia data, Quality of Service (QoS) and privacy should be satisfied. Current technologies vs. proposed security techniques in WMSNs and its pros and cons from a security point of view are explored in details. In addition to promising future trends of this research area by giving more attention for new challenging problems including secure routing protocol, fault tolerant, robustness and recovery process. We believe that this paper will add significantly a valuable discussion among the researchers and promote them to fetch new research ideas to design approximately best model by combining the most important security issues in order to reach secure WMSNs.




Similar content being viewed by others
References
Akyildiz I, Mehmet V (2010) Wireless sensor networks. Wiley, UK
Akyildiz I, Melodia T, Chowdhury R (2007) Wireless multimedia sensor networks: a survey. IEEE Wirel Commun 14:32–39. doi:10.1109/MWC.2007.4407225
Akyildiz I, Tommaso M, Kaushik R (2007) A survey on wireless multimedia sensor networks. Comput Netw 51:921–960. doi:10.1016/j.comnet.2006.10.002
Al-Karaki J, Almalkawi I, Manel Z, Julian M (2010) Wireless multimedia sensor networks: current trends and future directions. Sensors 10(7):6662–6717. doi:10.3390/s100706662
AlNuaimi M, Farag S, Khaled S (2011) A survey of wireless multimedia sensor networks challenges and solutions. International Conference on Innovations in Information Technology (IIT): 191–196. doi:10.1109/INNOVATIONS.2011.5893815
Bahia Z, Manel C, Nadjib B (2012) Energy-efficient protocol based sleep-scheduling for wireless sensor networks. IEEE internatinal conference on complex system (ICCS): 1–6. doi:10.1109/ICoCS.2012.6458592
Bambang H, Song H (2010) Wireless multimedia sensor networks applications and security challenges. IEEE international conference on broadband, wireless computing, communication and applications: 842–846.doi:10.1109/BWCCA.2010.182
Batalin M, Sukhatme G (2004) Coverage, exploration and deployment by a mobile robot and communication network. Telecommun Syst 26(2–4):181–196. doi:10.1023/B:TELS.0000029038.31947.d1
Boukerche A, Ren Y,Mokdad L (2010) Applying symmetric and asymmetric key algorithms for the security in wireless networks: proof of correctness. Proceedings of the 6th ACM workshop on QoS and security for wireless and mobile networks: 33–40. doi:10.1145/1868630.1868637
Carlo B, William F, Luigi R (2013) Optimal hibernation policies for energy efficient stateful operation in high-end wireless sensor nodes. World of wireless, mobile and multimedia networks (WoWMoM), 14thIEEE internatinal symposium and workshops on:1–3. doi:10.1109/WoWMoM.2013.6583420
Cheng L, Pu W, Hsiao-Hwa C, Guizani A (2008) Cluster Based On-demand Multi-Channel MAC Protocol for Wireless Multimedia Sensor Networks. IEEE International Conference on Communications (ICC): 2371–2376. doi: 10.1109/ICC.2008.451
Chilamkurti N, Zeadally S,Vasilakos A, Sharma V (2009) Cross-layer support for energy efficient routing in wireless sensor networks. Journal of Sensors:1–9. doi:10.1155/2009/134165
Cobo L, Alejandro Q, Samuel P (2010) Ant-based routing for wireless multimedia sensor networks using multiple QoS metrics. Comput Netw 54(17):2991–3010. doi:10.1016/j.comnet.2010.05.014
Dionisis K, Michail T, Ilias P, Anthony T, Stavros K (2011) Energy efficient and perceived QoS aware video routing over wireless multimedia sensor networks. Multimedia Ad Hoc Sens Netw 9(4):591–607. doi:10.1016/j.adhoc.2010.09.001
Eirini K, Joannis G, Joannis T, Fotini-Niovi P (2007) UWB technology to enhance the performance of wireless multimedia sensor networks. 12thIEEE sumposium on ISCC: 57–62. doi:10.1109/ISCC.2007.4381637
ElbasiE, Ozdemir S (2012) Secure data aggregation in wireless multimedia sensor networks via watermarking. 6th International Conference on Application of Information and Communication Technologies (AICT): 1–6. doi:10.1109/ICAICT.2012.6398501
Ganeriwal S, Kansal A, Srivastava M (2004) Self aware actuation for fault repair in sensor networks. IEEE Int Conf Robot Autom Proc 5:5244–5249. doi:10.1109/ROBOT.2004.1302550
Ganic E, Eskicioglu M (2004) Robust DWT-SVD doman image watermarking: embedding data in all frequencies. Proceedings of the ACM Multimedia and Security workshop: 167–174. doi:10.1145/1022431.1022461
Grieco A, Boggia G, Sicari S, Colombo P (2009) Secure wireless multimedia sensor networks: a survey. Mobile ubiquitous computing, systems, services and technologies, UBICOMM, IEEE: 194–201. doi:10.1109/UBICOMM.2009.27
Guerrero-Zapata M, Ruken Z, Jos’e M, Barcel O, Kemal B, Bulent T (2010) The future of security in wireless multimedia sensor networks. Telecommun Syst Springer 45:77–91. doi:10.1007/s11235-009-9235-0
Hamid M, Muhammad A, Choong H (2008) Design of a QoS-aware routing mechanism for wireless multimedia sensor networks. IEEE global telecommunications conference: 1–6. doi:10.1109/GLOCOM.2008.ECP.159
Han K, Luo J, Liu Y, Vasilakos A (2013) Algorithm design for data communications in duty-cycled wireless sensor networks: A survey. IEEE Communications Magazine 51(7): 107–113 doi:10.1109/MCOM.2013.6553686
Harjito B, Han S, Potdar V, Chang E, Xie M (2010) Secure communication in wireless multimedia sensor networks using watermarking. 4th IEEE International Conference on Digital Ecosystems and Technologies: 640–645. doi:10.1109/DEST.2010.5610580
Harjito B, Potdar V, Singh J (2012) Watermarking technique for wireless sensor networks: a state of the art. Eighth International Conference on Semantics, Knowledge and Grids (SKG): 832–840. doi:10.1145/2381716.2381873
Harjito B, Potdar V, Singh J (2012) Watermarking technique for copyright protection of wireless sensor network data using LFSR and Kolmogorov complexity. Proceedings of the 10th International Conference on Advances in Mobile Computing & Multimedia: 208–217. doi:10.1145/2428955.2428995
He D, Chen C, Chan S, Bu J, Vasilakos A (2012) A distributed trust evaluation model and its application scenarios for medical sensor networks. IEEE Trans Inf Technol Biomed 16(6):1164–1175. doi:10.1109/TITB.2012.2199996
He D, Chen C, Chan S, Bu J, Vasilakos A (2012) ReTrust: attack-resistant and lightweight trust management for medical sensor networks. IEEE Trans Inf Technol Biomed 16(4):623–632. doi:10.1109/TITB.2012.2194788
Hempe LM, Wang H, Dongming P, Wei W (2010) Index-based selective audio encryption for wireless multimedia sensor networks. IEEE Trans Multimedia 12(3):215–223. doi:10.1109/TMM.2010.2041102
Jian Y, Madria K (2006) SecRout: a secure routing protocol for sensor networks. 20th International conference on advanced information networking and applications (AINA) 1: 1–5. doi:10.1109/AINA.2006.297
Josang A (1999) Trust-Based decision making for electronic transactions. Proceedings of the fourth nordic workshop onsecure computer systems (NORDSEC’99), Stockholm University, Sweden: 1–21
Josang A, Ismail R, Boyd C (2007) A survey of trust and reputation systems for online service provision. Decis Support Syst 43(2):618–644
Kai L, Xiaohu G, Xiaofei W, Chunsheng Z, Heung-Gyoon R (2012) Research on secure data collection in wireless multimedia sensor networks. computer communications 35(15) :1902–1909. doi:10.1016/j.comcom.2012.03.010
Khalifeh A, Yousefi’zadeh H (2008) An Optimal UEP scheme of audio transmission over MIMO wireless links. Wireless Communications and Networking Conference (WCNC), IEEE: 3191–3196. doi:10.1109/WCNC.2008.557
Koushanfar F, Potkonjak M, Xiao Y (2007) Watermarking technique for sensor networks: foundations and applications. Book chapter, in Security in Sensor Networks, CRC Press, US
Kundur D, William L, Unoma O, Takis Z (2008) Security and privacy for distributed multimedia sensor networks. Proceedings of the IEEE 96: 112–130. doi:10.1109/JPROC.2007.909914
Lei Y, Chungui L (2011) Robust lifetime optimization of wireless multimedia sensor networks with correlated sources. Commun Comput Inf Sci 158:410–416. doi:10.1007/978-3-642-22694-6_58
Lei S, Yan Z, Laurence Y, Yu W, Manfred H, Naixue X (2009) TPGF: geographic routing in wireless multimedia sensor networks. Telecommun Syst, Springer: 79–95. doi:10.1007/s11235-009-9227-0
Li M, Li Z, Vasilakos A (2013) A survey on topology control in wireless sensor networks: taxonomy, comparative study, and open issues. Proc IEEE 101(12):2538–2557. doi:10.1109/JPROC.2013.2257631
Liu F, Jia Z, Li Y (2012) A Novel Partial Dynamic Reconfiguration Image Sensor Node for Wireless Multimedia Sensor Networks. IEEE 14th International Conference on High Performance Computing and Communication: 1368–1374. doi:10.1109/HPCC.2012.201
Masood H, Haider U, Rehman S, Khosa I (2010) Secure Communication in WMSN. Int Conf Inf Netw Autom (ICINA) 1:37–42. doi:10.1109/ICINA.2010.5636438
Mohammad Y, Donald A (2009) Priority-based rate control for service differentiation and congestion control in wireless multimedia sensor networks. Comput Netw 53:1798–1811. doi:10.1016/j.comnet.2009.02.011
Muhammad T, Ronan F (2010) Optimal Utility Lifetime and Delay-Robustness Tradeoff in Wireless Multimedia Sensor Networks. IEEE International Conference on Communications (ICC): 1–5. doi: 10.1109/ICC.2010.5502640
Nagarathna K, Kiran B, Mallapur D, Hiremath S (2012) Trust based secured routing in wireless multimedia sensor networks. Fourth international conference on computational intelligence, communication systems and networks (CICSyN), IEEE: 53–58. doi:10.1109/CICSyN.2012.20
Navrati S, Abhishek R, Jitae S (2008) Dynamic duty cycle and adaptive contention window based QoS-MAC protocol for wireless multimedia sensor networks. Comput Netw 52:2532–2542. doi:10.1016/j.comnet.2008.05.009
Okorafor N, Kundur D (2006) OPSENET: A security-enabled routing scheme for a system of optical sensor networks. Broadband Communications, Networks and Systems, BROADNETS: 1–10. doi:10.1109/BROADNETS.2006.4374297
Özgür A, Ian A (2005) Event-to-Sink reliable transport in wireless sensor networks. IEEE/ACM Trans Netw (TON) 13(5):1003–1016. doi:10.1109/TNET.2005.857076
Pathan A, Hyung-Woo L, Choong H (2006) Security in wireless sensor networks: issues and challenges. The 8th international conference on advanced communication technology (ICACT) 2: 1043–1048 doi:10.1109/ICACT.2006.206151
Pinar B, Kerem I, Sebnem B, Emre H (2012) Image quality estimation in wireless multimedia sensor networks: an experimental study. Broadband Commun Netw Syst 66:226–241. doi:10.1007/978-3-642-30376-0_15
Poonam B (2014) DAG based approach for fault tolerance in wireless multimedia sensor network. 2nd international e-conference on emerging trends in technology, international journal of advanced technology & engineering research (IJATER): 78–80
Ravi M, Vithya G (2012) QoS with security in wireless multimedia sensor networks. Int J Comput Netw Wirel Commun (IJCNWC) 2(3):390–396
Ruizhen L, Tieniu T (2002) An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans Multimedia 4(1):121–128. doi:10.1109/6046.985560
Samina E, Bechir H (2012) A survey on energy-efficient routing techniques with QoS assurances for wireless multimedia sensor networks. IEEE Commun Surv Tutor 14:265–278. doi:10.1109/SURV.2011.020211.00058
Sanjay M, Jian Y (29009) SeRWA: A secure routing protocol against wormhole attacks in sensor networks. Ad Hoc Networks 7(6): 1051–1063. doi:10.1016/j.adhoc.2008.09.005
Sarisaray P, Gur G, Baydere S, Harmanc E (2007) Performance comparison of error compensation techniques with multipath transmission in wireless multimedia sensor networks. 15th International symposium on modeling, analysis and simulation of computer and telecommunication systems, IEEE: 73–86. doi:10.1109/MASCOTS.2007.50
Sharif A, Potdar V, Chang E (2009) Wireless multimedia sensor network technology: a survey. IEEE 7thInternational Conference on: 606–613. doi:10.1109/INDIN.2009.5195872
Sheng Z, Yang S, Yu Y, Vasilakos A et al (2013) A survey on the IETF protocol suite for the internet of things: standards, challenges, and opportunities. IEEE Wirel Commun 20(6):91–98. doi:10.1109/MWC.2013.6704479
Shin J, Ruland C (2013) A survey of image hashing technique for data authentication in WMSNs. IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob): 253–258. doi:10.1109/WiMOB.2013.6673369
Shinya K, Akimitsu K, Takahiro H, Shojiro N (2010) Energy-efficient data gathering using sleep scheduling and spatial interpolation in wireless sensor networks. 13th IEEE international conference on network-based information systems: 62–69. doi:10.1109/NBiS.2010.58
Shobha P, Manohara P (2010) multipath data transfer in wireless multimedia sensor network. International conference on broadband wireless computing communication and applications, IEEE: 379–383. doi:10.1109/BWCCA.2010.100
Song S, Hwang K, Kwok Y (2006) Risk-Resilient heuristics and genetic algorithms for security-assured grid job scheduling. IEEE Transactions on Computers 55(6): 243–253. doi:10.1109/TC.2006.89
Taye M, Lei S, Manfred H, Min C, Takahiro H, Shojiro N (2010) Secured two phase geographic forwarding protocol in wireless multimedia sensor networks. Global telecommunications conference (GLOBECOM), IEEE: 1–6. doi:10.1109/GLOCOM.2010.5683532
Tian D, Georganas N (2002) A coverage-preserving node scheduling scheme for large wireless sensor networks. 2nd Proceedings of the 1st ACM international workshop on Wireless sensor networks and applications: 32–41. doi:10.1145/570738.570744
Tsitsipis D, Nikolakopoulos G, Koubias S (2011) A dual scheme for secured multimedia wirelesssensor network.19th Mediterranean Conference on control & Automation (MED): 1160–1165. doi:10.1109/MED.2011.5983142
Van Dam T, Langendoen K (2003) An adaptive energy-efficient MAC protocol for wireless sensor networks. Proceedings of the 1st international conference on Embedded networked sensor systems: 171–180. doi:10.1145/958491.958512
Vasilakos A, Zhang Y, Spyropoulos T (2012) Delay tolerant networks: protocols and applications. CRC Press, US
Venkatasubramanian K, Banerjee A, Gupta S (2010) PSKA: usable and secure key agreement scheme for body area networks. IEEE Trans Inf Technol Biomed 14(1):60–68. doi:10.1109/TITB.2009.2037617
Vu K, Zheng R (2011) Robust coverage under uncertainty in wireless sensor networks. INFOCOM IEEE Proceedings: 2015–2023. doi: 10.1109/INFCOM.2011.5935008
Wang G, Cao G, la Porta T (2003) A bidding protocol for deploying mobile sensors. IEEE Trans Mob Comput 6(5):315–324. doi:10.1109/TMC.2007.1022
Wang G, Cao G, la Porta T (2006) Movement-assisted sensor deployment. IEEE Trans Mob Comput 5(6):640–652. doi:10.1109/TMC.2006.80
Wang H, Yin B (2013) Communication-resource-aware adaptive watermarking for multimedia authentication in wireless multimedia sensor networks. J Supercomput 64(3):883–897. doi:10.1007/s11227-010-0500-5
Wang H, Yin B (2013) A perceptual hashing-based robust image authentication scheme for wireless multimedia sensor networks. International Journal of Distributed Sensor Networks: 1–9. doi:10.1155/2013/791814
Xiang L, Luo J, Vasilakos A (2011) Compressed data aggregation for energy efficient wireless sensor networks. 8th Annual IEEE communications society conference on sensor, mesh and ad hoc communications and networks: 46–54. doi:10.1109/SAHCN.2011.5984932
Xiaojiang D, Yang X, Hsiao-Hwa C, Qishi W (2006) Secure cell relay routing protocol for sensor networks. Wiley Online Libr 6(3):375–391. doi:10.1002/wcm.402
Xie T, Qin X (2008) Security-Aware Resource Allocation for Real-Time Parallel Jobs on Homogeneous and Heterogeneous Clusters. IEEE transactions on parallel and distributed systems 19(5): 688–697. doi:10.1109/TPDS.2007.70776
Xiong Z, Fan X, Liu S, Zhong Z (2011) Low complexity image compression for wireless multimedia sensor networks. IEEE International Conference on Information Science and Technology: 665–670. doi:10.1109/ICIST.2011.5765335
Yan S, Hong L, Sajal D (2012) A trust-based framework for fault-tolerant data aggregation in wireless multimedia sensor networks. IEEE Trans Dependable Secure Comput 9(6):785–797. doi:10.1109/TDSC.2012.68
Yan Z, Zhang P, Vasilakos A (2014) A survey on trust management for Internet of Things. Journal of network and computer applications 42:120–134. doi:10.1016/j.jnca.2014.01.014
Yang Y, Chen Y, Yi W (2010) Cross-layer FEC for reliable transfer of variable-length coded data in WMSN. International Conference on Wireless Sensor Network, IEEE: 380–384. doi:10.1049/cp.2010.1083
Yao Y, Cao Q, Vasilakos A (2013) EDAL: An energy-efficient, delay-aware, and lifetime-balancing data collection protocol for wireless sensor networks. IEEE 10th international conference on mobile ad-hoc and sensor systems: 182–190. doi:10.1109/MASS.2013.44
Ye W, Heidemann J, Estrin D (2002) An energy-efficient MAC protocol for wireless sensor networks. 21th Annual Joint Conference of the IEEE Computer and Communications Societies 3: 1567–1576. doi:10.1109/INFCOM.2002.1019408
Yigitel A, Ozlem I, Cem E (2011) Design and implementation of a QoS-aware MAC protocol for wireless multimedia sensor networks. Comput Commun 34(16):1991–2001. doi:10.1016/j.comcom.2011.06.006
Zeng Y, Xiang K, Li D, Vasilakos A (2013) Directional routing and scheduling for green vehicular delay tolerant networks. Wirel Netw 19(2):161–173. doi:10.1007/s11276-012-0457-9
Zhang H, Hou J (2005) Maintaining sensing coverage and connectivity in large sensor networks. Ad Hoc Sensor Wirel Netw 1:89–124. doi:10.1201/9780203323687.ch28
Zhang Z, Wang H, Vasilakos A, Fang H (2012) ECG-Cryptography and authentication in body area networks. IEEE Trans Inf Technol Biomed 16(6):1070–1078. doi:10.1109/TITB.2012.2206115
Zhe-yuan X, Xiao-ping F, Shao-qiang L, Zhi Z (2010) Distributed image coding in wireless multimedia sensor networks: a survey. Third international workshop on advanced computational intelligence (IWACI): 618–622. doi:10.1109/IWACI.2010.5585161
Zhou L, Chao H, Vasilakos A (2011) joint forensics-scheduling strategy for delay-sensitive multimedia applications over heterogeneous networks. IEEE J Sel Areas Commun 29(7):1358–1367. doi:10.1109/JSAC.2011.110803
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ghadi, M., Laouamer, L. & Moulahi, T. Securing data exchange in wireless multimedia sensor networks: perspectives and challenges. Multimed Tools Appl 75, 3425–3451 (2016). https://doi.org/10.1007/s11042-014-2443-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-014-2443-y