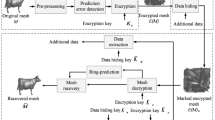
Abstract
Reversible data hiding in the encrypted domain (RDH-ED) reversibly encode and decode information to an encrypted cover medium without decrypting it. With the rapid development of multimedia applications, 3D models are considered as potential cover media for reversible data hiding due to their intrinsic capacity and potential applications in various areas such as military and medicine. In this paper, we propose a two-tier RDH-ED framework for 3D mesh models using the homomorphic Paillier cryptosystem. Two homomorphic properties of the underlying cryptosystem are utilized to propose a two-tier RDH-ED framework for end-to-end authentication and cloud data management. The proposed framework is successfully implemented on various simple and dense meshes. The performance evaluation of the proposed framework shows high embedding rates. Furthermore, it produces high-quality directly decrypted meshes from which information bits are extracted error-free and the original meshes are recovered losslessly.
Similar content being viewed by others
References
Cox, I.; Miller, M.; Bloom, J.; Fridrich, J.; Kalker, T.: Digital Watermarking and Steganography. Morgan Kaufmann, Burlington (2007)
Fridrich, J.: Steganography in Digital Media: Principles, Algorithms, and Applications. Cambridge University Press, Cambridge (2009)
Tian, J.: Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 13(8), 890–896 (2003)
Ni, Z.; Shi, Y.-Q.; Ansari, N.; Su, W.: Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 16(3), 354–362 (2006)
Avci, E.; Tuncer, T.; Avci, D.: A novel reversible data hiding algorithm based on probabilistic XOR secret sharing in wavelet transform domain. Arab. J. Sci. Eng. 41(8), 3153–3161 (2016)
Celik, M.U.; Sharma, G.; Tekalp, A.M.; Saber, E.: Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 14(2), 253–266 (2005)
Weng, S.; Zhao, Y.; Pan, J.-S.; Ni, R.: Reversible watermarking based on invariability and adjustment on pixel pairs. IEEE Signal Process. Lett. 15, 721–724 (2008)
Wang, X.; Li, X.; Yang, B.; Guo, Z.: Efficient generalized integer transform for reversible watermarking. IEEE Signal Process. Lett. 17(6), 567–570 (2010)
Qiu, Y.; Qian, Z.; Yu, L.: Adaptive reversible data hiding by extending the generalized integer transformation. IEEE Signal Process. Lett. 23(1), 130–134 (2016)
Coltuc, D.: Low distortion transform for reversible watermarking. IEEE Trans. Image Process. 21(1), 412–417 (2012)
Thodi, D.M.; Rodriguez, J.J.: Prediction-error based reversible watermarking. In: Image Processing, 2004. ICIP’04. 2004 International Conference on, pp. 1549-1552. IEEE (2004)
Thodi, D.M.; Rodríguez, J.J.: Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 16(3), 721–730 (2007)
Zhang, W.; Hu, X.; Li, X.; Yu, N.: Recursive histogram modification: establishing equivalency between reversible data hiding and lossless data compression. IEEE Trans. Image Process. 22(7), 2775–2785 (2013)
Hu, X.; Zhang, W.; Hu, X.; Yu, N.; Zhao, X.; Li, F.: Fast estimation of optimal marked-signal distribution for reversible data hiding. IEEE Trans. Inf. Forensics Secur. 8(5), 779–788 (2013)
Zhang, W.; Hu, X.; Li, X.; Nenghai, Y.: Optimal transition probability of reversible data hiding for general distortion metrics and its applications. IEEE Trans. Image Process. 24(1), 294–304 (2015)
Jiang, R.; Zhou, H.; Zhang, W.; Yu, N.-H.: Reversible data hiding in encrypted 3D mesh models. IEEE Trans. Multimedia 20(1), 55–67 (2017)
Ma, K.; Zhang, W.; Zhao, X.; Yu, N.; Li, F.: Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans. Inf. Forensics Secur. 8(3), 553–562 (2013)
Zhang, W.; Ma, K.; Yu, N.: Reversibility improved data hiding in encrypted images. Signal Process. 94, 118–127 (2014)
Cao, X.; Du, L.; Wei, X.; Meng, D.; Guo, X.: High capacity reversible data hiding in encrypted images by patch-level sparse representation. IEEE Trans. Cybern. 46(5), 1132–1143 (2016)
Zhang, X.: Reversible data hiding in encrypted image. IEEE Signal Process. Lett. 18(4), 255–258 (2011)
Liao, X.; Shu, C.: Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J. Vis. Commun. Image Represent. 28, 21–27 (2015)
Zhou, J.; Sun, W.; Dong, L.; Liu, X.; Au, O.C.; Tang, Y.Y.: Secure reversible image data hiding over encrypted domain via key modulation. IEEE Trans. Circuits Syst. Video Technol. 26(3), 441–452 (2016)
Zheng, S.; Li, D.; Hu, D.; Ye, D.; Wang, L.; Wang, J.: Lossless data hiding algorithm for encrypted images with high capacity. Multimedia Tools Appl. 75(21), 13765–13778 (2016)
Qian, Z.; Zhang, X.: Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans. Circuits Syst. Video Technol. 26(4), 636–646 (2016)
Chen, Y.-C.; Shiu, C.-W.; Horng, G.: Encrypted signal-based reversible data hiding with public key cryptosystem. J. Vis. Commun. Image Represent. 25(5), 1164–1170 (2014)
Wu, X.; Chen, B.; Weng, J.: Reversible data hiding for encrypted signals by homomorphic encryption and signal energy transfer. J. Vis. Commun. Image Represent. 41, 58–64 (2016)
Wu, H.-T.; Cheung, Y.-M.; Huang, J.: Reversible data hiding in Paillier cryptosystem. J. Vis. Commun. Image Represent. 40, 765–771 (2016)
Zhang, X.; Long, J.; Wang, Z.; Cheng, H.: Lossless and reversible data hiding in encrypted images with public-key cryptography. IEEE Trans. Circuits Syst. Video Technol. 26(9), 1622–1631 (2016)
Xiang, S.; Luo, X.: Efficient reversible data hiding in encrypted image with public key cryptosystem. EURASIP J. Adv. Signal Process. 2017(1), 59 (2017)
Chou, D.; Jhou, C.-Y.; Chu, S.-C.: Reversible watermark for 3D vertices based on data hiding in mesh formation. Int. J. Innov. Comput. Inf. Control 5(7), 1893–1901 (2009)
Wu, H.-t.; Dugelay, J.-L.: Reversible watermarking of 3D mesh models by prediction-error expansion. In: Multimedia Signal Processing, 2008 IEEE 10th Workshop on, pp. 797-802. IEEE (2008)
Wu, H.-T.; Cheung, Y.-m.: A reversible data hiding approach to mesh authentication. In: Proceedings of the 2005 IEEE/WIC/ACM International Conference on Web Intelligence, pp. 774–777. IEEE Computer Society (2005)
Luo, H.; Lu, Z.-m.; Pan, J.-s.: A reversible data hiding scheme for 3D point cloud model. In: Signal Processing and Information Technology, 2006 IEEE International Symposium on, pp. 863–867. IEEE (2006)
Luo, H.; Pan, J.-S.; Lu, Z.-M.; Huang, H.-C.: Reversible data hiding for 3D point cloud model. In: Intelligent Information Hiding and Multimedia Signal Processing, 2006. IIH-MSP’06. International Conference on, pp. 487–490. IEEE (2006)
Sun, Z.; Lu, Z.-M.; Li, Z.: Reversible data hiding for 3D meshes in the PVQ-compressed domain. In: Intelligent Information Hiding and Multimedia Signal Processing, 2006. IIH-MSP’06. International Conference on, pp. 593–596. IEEE (2006)
Lu, Z.-M.; Li, Z.: High capacity reversible data hiding for 3D meshes in the PVQ domain. In: Shi, Y.Q., Kim, H.J., Katzenbeisser, S. (eds.) Digital Watermarking. IWDW 2007. Lecture Notes in Computer Science, vol. 5041, pp. 233–243. Springer, Berlin, Heidelberg (2008)
Bianchi, T.; Piva, A.; Barni, M.: On the implementation of the discrete Fourier transform in the encrypted domain. IEEE Trans. Inf. Forensics Secur. 4(1), 86–97 (2009)
Deering, M.: Geometry compression. In: Proceedings of the 22nd Annual Conference on Computer Graphics and Interactive Techniques, pp. 13–20. ACM (1995)
Rivest, R.L.; Adleman, L.; Dertouzos, M.L.: On data banks and privacy homomorphisms. Found. Secure Comput. 4(11), 169–180 (1978)
Gentry, C.; Halevi, S.: Implementing gentry’s fully-homomorphic encryption scheme. In: Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 129–148. Springer (2011)
Paillier, P.: Public-key cryptosystems based on composite degree residuosity classes. In: International Conference on the Theory and Applications of Cryptographic Techniques, pp. 223–238. Springer (1999)
Damgård, I.; Jurik, M.: A generalisation, a simpli. cation and some applications of paillier’s probabilistic public-key system. In: International Workshop on Public Key Cryptography, pp. 119–136. Springer (2001)
ElGamal, T.: A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 31(4), 469–472 (1985)
Goldwasser, S.; Micali, S.: Probabilistic encryption. J. Comput. Syst. Sci. 28(2), 270–299 (1984)
Lavoué, G.; Gelasca, E.D.; Dupont, F.; Baskurt, A.; Ebrahimi, T.: Perceptually driven 3D distance metrics with application to watermarking. In: Applications of Digital Image Processing XXIX 2006, p. 63120L. International Society for Optics and Photonics
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shah, M., Zhang, W., Hu, H. et al. Homomorphic Encryption-Based Reversible Data Hiding for 3D Mesh Models. Arab J Sci Eng 43, 8145–8157 (2018). https://doi.org/10.1007/s13369-018-3354-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-018-3354-4