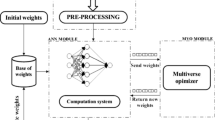
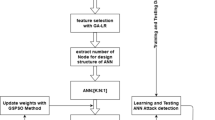
Abstract
Intrusion detection has been playing a crucial role for making a computer network secure for any transaction. An intrusion detection system (IDS) detects various types of malicious network traffic and computer usage, which sometimes may not be detected by a conventional firewall. Recently, many IDS have been developed based on machine learning techniques. Specifically, advanced detection approaches created by combining or integrating evolutionary algorithms and neural networks have shown better detection performance than general machine learning approaches. The present study reports two new hybrid intrusion detection methods; one is based on gravitational search (GS), and other one is a combination of GS and particle swarm optimization (GSPSO). These two techniques have been successfully implemented to train artificial neural network (ANN) and the resulting models: GS-ANN and GSPSO-ANN are successfully applied for intrusion detection process. The applicability of these proposed approaches is also compared with other conventional methods such as decision tree, ANN based on gradient descent (GD-ANN), ANN based on genetic algorithm (GA-ANN) and ANN based on PSO (PSO-ANN) by testing with NSL-KDD dataset. Moreover, the results obtained by GS-ANN and GSPSO-ANN are found to be statistically significant based on the popular Wilcoxon’s rank sum test as compared to other conventional techniques. The obtained test results reported that the proposed GS-ANN and GSPSO-ANN could achieve a maximum detection accuracy of 94.9 and 98.13 % respectively. The proposed models (GS-ANN and GSPSO-ANN) could also achieve good performance when tested with highly imbalanced datasets.


Similar content being viewed by others
References
Ahmad I, Hussain M, Alghamdi A, Alelaiwi A (2014) Enhancing SVM performance in intrusion detection using optimal feature subset selection based on genetic principal components. Neural Comput Appl 24(7–8):1671–1682
Alshammari R, Zincir-Heywood AN (2007) A flow based approach for SSH traffic detection. IEEE Int Conf Syst Man Cybern 2007:296–301
Aydin MA, Zaim AH, Ceylan KG (2009) A hybrid intrusion detection system design for computer network security. Comput Electr Eng 35:517–526
Bao F, Chen I-R, Chang M, Cho J-H (2012) Hierarchical trust management for wireless sensor networks and its applications to trust-based routing and intrusion detection. IEEE Trans Netw Serv Manag 9(2):169–183
Beghdad R (2008) Critical study of neural networks in detecting intrusions. Comput Secur 27(5–6):168–175
Catania CA, Garino CG (2012) Automatic network intrusion detection: current techniques and open issues. Comput Electr Eng 38:1062–1072
Chen YH, Abraham A, Yang B (2007) Hybrid flexible neural-tree-based intrusion detection systems. Int J Intell Syst 22(4):337–352
Dainotti A, Pescapé A, Rossi PS, Palmieri F, Ventre G (2008) Internet traffic modeling by means of hidden Markov models. Comput Netw 52(14):2645–2662
Dash T, Nayak SK, Behera HS (2015a) Hybrid gravitational search and particle swarm based fuzzy MLP for medical data classification. In: Computational intelligence in data mining, vol 1. Springer, India, pp 35–43
Dash T, Nayak T, Swain RR (2015b) Controlling wall following robot navigation based on gravitational search and feed forward neural network. In: Proceedings of the 2nd international conference on perception and machine intelligence, ACM, pp 196–200
Eberhart R, Kennedym J (1995) A new optimization using particle swarm theory. In: Sixth international symposium on micro machine and human science, MHS’95, IEEE, pp 39–43
Fiore U, Palmieri F, Castiglione A, De Santis A (2013) Network anomaly detection with the restricted Boltzmann machine. Neurocomputing 122:13–23
Garcia S, Molina D, Lozano M, Herrera F (2009) A study on the use of non-parametric tests for analyzing the evolutionary algorithms’ behaviour: a case study on the CEC’2005 special session on real parameter optimization. J Heuristics 15:617–644
Gómez J, Gil C, Baños R, Márquez AL, Montoya FG, Montoya MG (2013) A Pareto-based multi-objective evolutionary algorithm for automatic rule generation in network intrusion detection systems. Soft Comput 17(2):255–263
Gu Y, McCallum A, Towsley D (2005) Detecting anomalies in network traffic using maximum entropy estimation, In: Proceedings of the 5th ACM SIGCOMM conference on internet measurement, IMC’05. USENIX Association, Berkeley, CA, USA, p 32
Horng S-J, Su M-Y, Chen Y-H, Kao T-W, Chen R-J, Lai J-L, Perkasa CD (2011) A novel intrusion detection system based on hierarchical clustering and support vector machines. Expert Syst Appl 38:306–313
Hu J, Yu X, Qiu D (2009) A simple and efficient hidden Markov model scheme for host-based anomaly intrusion detection. IEEE Netw 23:42–47
KDD Cup (1999) Intrusion detection data set. http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html
Kim G, Lee S, Kim S (2014) A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst Appl 41(4):1690–1700
Kuang F, Zhang S, Jin Z, Xu W (2015) A novel SVM by combining kernel principal component analysis and improved chaotic particle swarm optimization for intrusion detection. Soft Comput 19:1187–1199
Kumar PAR, Selvakumar S (2011) Distributed denial of service attack detection using an ensemble of neural classifier. Comput Commun 34:1328–1341
Lazarevic A, Kumar V, Srivastava J (2005) Intrusion detection: a survey. In: Managing cyber threats. Massive Computing, vol 5. Springer, New York, pp 19–78
Lee W, Nimbalkar RA, Yee KK, Patil SB, Desai PH, Tran TT, Stolfo SJ (2000) A data mining and CIDF based approach for detecting novel and distributed intrusions. In: Recent advances in intrusion detection, Springer, Berlin, pp 49–65
Levin I (2000) KDD-99 classifier learning contest LLSoft’s results overview. SIGKDD Explor 1(2):67–75
Linda O, Vollmer T, Manic M (2009) Neural network based intrusion detection system for critical infrastructures. In: Proceedings of international joint conference on neural networks, Atlanta, Georgia, USA, 14–19 June 2009, pp 1827–1834
Mabu S, Chen C, Lu N, Shimada K, Hirasawa K (2011) An intrusion-detection model based on fuzzy class-association-rule mining using genetic network programming. IEEE Trans Syst Man Cyber Part C 41(1):130–139
Mahoney MV, Chan PK (2002) Learning nonstationary models of normal network traffic for detecting novel attacks. In: Proceedings of the eighth ACM SIGKDD international conference on Knowledge discovery and data mining. KDD\(\acute{0}\)2. ACM, New York, NY, USA, pp 376-385
Manikopoulos C, Papavassiliou S (2002) Network intrusion and fault detection: a statistical anomaly approach. IEEE Commun Mag 40(10):76–82
Marín-Blázquez JG, Pérez GM (2009) Intrusion detection using a linguistic hedged fuzzy-XCS classifier system. Soft Comput 13(3):273–290
McHugh J (2000) Testing intrusion detection systems: a critique of the 1998 and 1999 darpa intrusion detection system evaluations as performed by lincoln laboratory. ACM Trans Inf Syst Secur 3(4):262–294
Mirjalili S, Hashim SZM, Sardroudi HM (2012) Training feedforward neural networks using hybrid particle swarm optimization and gravitational search algorithm. Appl Math Comput 218:11125–11137
Palmieri F, Fiore U, Castiglione A (2014) A distributed approach to network anomaly detection based on independent component analysis. Concurr Comput 26(5):1113–1129
Palmieri F, Fiore U (2010) Network anomaly detection through nonlinear analysis. Comput Secur 29(7):737–755
Patcha A, Park JM (2007) An overview of anomaly detection techniques: existing solutions and latest technological trends. Comput Netw 51(12):3448–3470
Pfahringer B (2000) Winning the KDD99 classification cup: bagged boosting. SIGKDD Explor 1(2):65–66
Ramasubramanian P, Kannan A (2006) A genetic-algorithm based neural network short-term forecasting framework for database intrusion prediction system. Soft Comput 10(8):699–714
Rashedi E, Nezamabadi-pour H, Saryazdi S (2009) GSA: a gravitational search algorithm. Inf Sci 179:2232–2248
Rastegari S, Hingston P, Lam CP (2015) Evolving statistical rulesets for network intrusion detection. Appl Soft Comput 33:348–359
Shakshuki EM, Kang N, Sheltami TR (2013) EAACKA secure intrusion-detection system for MANETs. IEEE Trans Ind Electron 60(3):1089–1098
Shin S, Kwon T, Jo G-Y, Park Y, Rhy H (2010) An experimental study of hierarchical intrusion detection for wireless industrial sensor networks. IEEE Trans Ind Inf 6(4):744–757
Sindhu SSS, Geetha S, Marikannan M, Kannan A (2009) A neuro-genetic based short-term forecasting framework for network intrusion prediction system. Int J Autom Comput 6(4):406–414
Tavallaee M, Bagheri E, Lu W, Ghorbani A (2009) A detailed analysis of the KDD CUP’99 dataset. In: Proceedings of the IEEE symposium on computational intelligence for security and defense applications, pp 53–58
Toosi AN, Kahani M (2007) A new approach to intrusion detection based on an evolutionary soft computing model using neuro-fuzzy classifiers. Comput Commun 30:2201–2212
Vollmer T, Alves-Foss J, Manic M (2011) Autonomous rule creation for intrusion detection. In: IEEE symposium on computational intelligence in cyber security (CICS), pp 1–8
Wang G, Hao J, Ma J, Huang L (2010) A new approach to intrusion detection using artificial neural networks and fuzzy clustering. Expert Syst Appl 37:6225–6232
Wu SX, Banzhaf W (2008) The use of computational intelligence in intrusion detection systems: a review. Technical report #2008-05, Memorial University of Newfoundland
Wu S, Yen E (2009) Data mining-based intrusion detectors. Expert Syst Appl 36(3):5605–5612
Ye N, Emran SM, Chen Q, Vilbert S (2002) Multivariate statistical analysis of audit trails for host-based intrusion detection. IEEE Trans Comput 51(7):810820
Yu Z, Tsai JJP, Weigert T (2007) An automatically tuning intrusion detection system. IEEE Trans Syst Man Cybern Part B 37(2):373–384
Zbilut JP, Webber CL (2006) Recurrence quantification analysis. In: Akay M (ed) Wiley encyclopedia of biomedical engineering. Wiley, Hoboken
Acknowledgments
The author expresses his sincere gratitude to Dr. Prabhat K. Sahu (NIST Berhampur) and Dr. Sukanta Mondal (BITS-Pilani, Goa) for their fruitful suggestions during the work. The author thankfully acknowledges NIST Berhampur and BITS-Pilani, Goa for providing required support. The author thanks anonymous reviewers and the editor for their valuable comments and suggestions to improve the quality of the paper.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The author declares that there is no conflict of interest regarding publication of this work.
Additional information
Communicated by V. Loia.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Appendix
Appendix
1.1 Complexity analysis of proposed model
As the proposed ANN models are three-layered architecture, i.e., (input–hidden–output), the computation will be carried out in two phases; (i) forward computation is from input to hidden layer which occurs in O(NM) times, (ii) the next computation is from hidden to output layer which takes O(M) times. So total is \(T(N,M) = O(NM) + O(M)\approx O(NM)\). For proposed GS-ANN and GSPSO-ANN, O(NM) computations will be carried out for each agent in the system. Hence, the overall algorithmic time complexity of the proposed models is O(NM) multiplied with population size (\(N_\mathrm{pop}\)). Therefore, algorithmic time complexity of the model is \(O(N_\mathrm{pop}\times NM)\).
Rights and permissions
About this article
Cite this article
Dash, T. A study on intrusion detection using neural networks trained with evolutionary algorithms. Soft Comput 21, 2687–2700 (2017). https://doi.org/10.1007/s00500-015-1967-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-015-1967-z