Abstract
In this paper, a fuzzy logic based digital image watermarking technique is proposed. The contrast and edge values of the host image are analyzed by the fuzzy inference system (FIS) against fuzzy rules and then the FIS evaluates the output which is proposed as the watermarking strength (α) of the image. By varying the contrast and edge values of the host image, the fuzzy logic adjusts the watermarking strength to keep the system performance unchanged which helps to improve imperceptibility of the watermarked image. DWT is performed to divide the cover image and watermark image into sub-bands and the maximum entropy region among the sub-bands is calculated for selecting the embedding location because it is less affected by the image processing attacks. Hence, it makes the scheme more robust than other fuzzy based methods. In the extraction phase, the watermark is recovered from the sub-band where it was embedded. The effectiveness of the algorithm is measured in terms of performance parameters like peak signal to noise ratio and normalized correlation. Experimental results indicate that the fuzzy logic adjusts the watermarking strength to keep the performance parameters unchanged irrespective of the contrast and edge values of the host image.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In this modern age, digital contents are suffering from lack of security due to easier access to the internet and the availability of intelligent software. This kind of act threats the transmission of digital data over the communication channels [1]. Hence, some data hiding techniques are introduced to reduce this. They can be divided into two classes: steganography and digital watermarking. [2] Digital image watermarking is a process of hiding information without compromising the host image. Digital watermarking is more effective and secure than the steganography in terms of data ownership.
Two important properties of digital image watermarking are imperceptibility and robustness. Imperceptibility can be defined in terms of visual degradation of the host image [3]. If the host image is less visually degraded, the algorithm is more imperceptible. Again, robustness can be defined in terms of image processing attacks. If the host image can tolerate the image processing attacks and the watermark image is approximately reconstructed from the watermarked image, the algorithm is said to be robust. All efficient watermarking schemes need to increase these properties.
According to the necessity of host image for the watermark extraction process, digital image watermarking can be divided into blind, semi-blind and non-blind schemes. Blind schemes do not require host image but semi-blind and non-blind schemes require host image or secret keys to detect watermark image [4]. Digital image watermarking can also be classified on the basis of the embedding domain into two classes. They are spatial domain techniques and transform domain techniques. Spatial domain techniques directly modify the image pixel bits and these modifications are used in watermark reconstruction [5]. The scheme proposed by Abraham et al. [5] uses two different masks in embedding for improving the performance parameters of the scheme. It works efficiently as the watermark bits are scattered over a broad region.
Transform domain-based methods contain transformations like DWT, DCT or DFT. Watermark is then embedded by changing the domain coefficients [6]. Singh et al. [6] proposed a method based on 3 level DWT and student t-distribution. This method gives the benefits of student t-distributions compared to the normal and logistic distributions that are applied to the DWT coefficients. Lande et al. [7] proposed an adaptive method using human visual system (HVS) based fuzzy logic for masking and the model was implemented practically. The main turning point of the method is the use of fuzzy logic to determine the gain factor on the basis of HVS.
The method proposed by Jamali et al. [8] manipulates fuzzy logic for calculating embedding strength in DCT domain. This approach shows good PSNR and NC values due to the adaptive use of fuzzy mapping. Coumou et al. [9] proposed a scheme using fuzzy logic for determining the invisible embedding features. But this method has the limitation of optimization of the fuzzy system and robustness.
The scheme proposed by Arun Kumar et al. [10] utilizes a genetic algorithm for determining the locations of watermark embedding and fuzzy logic for optimization. It shows good performance in HH sub-band compared to the other sub-bands. Huang et al. [11] introduced a method using bacterial foraging instead of genetic algorithm along with fuzzy logic. It shows improved performance when compared with the schemes using the genetic algorithm as the method utilizes the continuous tuning of weighting elements.
Agarwal et al. [12] proposed a method utilizing hybridized fuzzy logic and back-propagation neural network for embedding the binary watermark. The performance is good for using block threshold values of HVS properties and fuzzy optimization techniques. Jagadeesh et al. [13] use fuzzy logic for HVS properties along with DCT for blind watermarking. It shows better results in terms of PSNR and NC compared to similar types of algorithms. The method proposed by Sridevi et al. [14] determines embedding strength based on fuzzy rules and also incorporates the features of DCT and SVD. Although the performance of the system is satisfactory, it has the limitation of multiple level DWT divisions and pointing out the perfect embedding location.
In the proposed method, HVS properties like the contrast and edge values are used by the fuzzy inference system to effectively calculate the embedding strength (α) and then the maximum entropy is calculated to determine the suitable embedding location. The scopes and objectives of the proposed work are information hiding, ownership authentication and copyright protection in the fields of image processing. The rest of the paper is organized as follows: Sect. 2 describes the importance of contrast and edge sensitivity. Then, watermark embedding algorithm of the proposed method is discussed in details in Sect. 3. The watermark extraction process of the proposed method is explained in Sect. 4. Performance parameters are included in Sect. 5. Then Sect. 6 includes the results and findings. Finally, Sect. 7 concludes the analysis of the results for the proposed method.
2 Importance of contrast and edge sensitivity
The sensitivity of human eye to an image depends on different properties. These are Brightness sensitivity, Frequency sensitivity, Edge Sensitivity and Contrast Sensitivity [1]. In our proposed scheme we use contrast and edge sensitivity as fuzzy inputs and their importance in watermarking are discussed below:
A. Contrast sensitivity
High contrast areas are less detectable by the human visual system. Hence the increasing contrast areas are more suitable for embedding. The contrast sensitivity can be expressed by the following formula:
where Cj is the contrast value of the image in the jth pixel and cond(X) gives the rounded value to 1 if value ≠ 0, else 0 [13].
B. Edge sensitivity
Human eyes do not recognize the non-uniform changes in the image. Thus embedding in higher edges of the image is more advantageous than in the lower edges [8].
3 Proposed watermark embedding algorithm
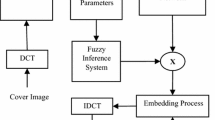
The proposed watermark embedding block diagram is shown in Fig. 1. Firstly, the contrast and edge value of the host image are given as input to the fuzzy inference system (FIS). The output of the FIS is the embedding strength. Host and watermark images are decomposed into sub-bands using DWT and then the entropy of each sub-band is calculated. Finally, the watermark is embedded in the highest entropy region and inverse discrete wavelet transform (IDWT) is performed. The entire procedure is discussed in the following steps:
-
Step 1 Host image and the watermark image are decomposed into four sub-bands using DWT.
-
Step 2 The entropy of each sub-band is calculated to determine the maximum entropy location. This location is selected for watermark embedding. Maximum entropy area is the location with a maximum degree of information variation and embedding in this region do not change the original information very much. The entropy of an image sub-band is calculated by the following formula [15]:
$${\text{L}} = \sum {{\text{R}}_{\text{i}} \,\log \left( {{\text{R}}_{\text{i}} } \right)}$$(2)where L is the entropy of the sub-band and Ri is the intensity of pixel i.
-
Step 3 For calculating the embedding strength, first the contrast and edge values of the host image are calculated using the following functions:
$${\text{Ic}} = {\text{f}}\left( {\text{Im} } \right)$$(3)$${\text{Ie}} = {\text{g}}\left( {\text{Im} } \right)$$(4)where Im is the host image. Ic and Ie are the contrast and edge values which are the functions of Im. The contrast and edge values are varied for evaluating system performance later.
-
Step 4 Contrast and edge values determined in the previous step, work as input to the fuzzy system. A Mamdani type FIS with centroid defuzzification is used in the process as shown in Fig. 2. It gives proposed watermarking strength (α) as output based on the inputs. So, the embedding strength can be expressed by the following function:
$$\upalpha = {\text{f}}\,({\text{Ic}}\,\&\, {\text{Ie}})$$(5)
The membership functions used in the system are shown in Figs. 3 and 4. The general rules for contrast and edge sensitivity are:
-
1.
If contrast is high or low, embedding strength is high.
-
2.
If contrast is medium, embedding strength is low.
-
3.
If edge is high, embedding strength is high.
-
4.
If edge is low, embedding strength is low.
-
5.
If edge is medium, embedding strength is medium.
Depending on the general rules, the contrast and edge sensitivities have very low, low, medium, high and very high levels. As both properties have 5 levels, there are total 25 (5 × 5) decision rules based on which the embedding strength varies. The decision rules are based on logical AND operation. Variation of embedding strength with the inputs is shown in Fig. 5. It can be observed that when contrast is very small and edge is very low, α is medium. Again, when contrast is very big and edge is very high, α is large. Thus, the embedding strength varies from 0 to 1 according to the inputs. The overall 3D-rule viewer surface of the FIS is shown in Fig. 6.
-
Step 5 Watermark is embedded in the maximum entropy sub-band of the host image with the maximum entropy sub-band of the watermark image according to the embedding strength output of FIS.
-
Step 6 Perform IDWT to get the watermarked image.
4 Proposed watermark extraction algorithm
The block diagram of the proposed watermark extraction algorithm is shown in Fig. 7. Firstly, watermarked image is decomposed by DWT. Then the watermark pixels are reconstructed from the embedding sub-band and IDWT is applied. The entire process is discussed in the following steps:
-
Step 1 Apply DWT to the watermarked image. The image will be decomposed into four sub-bands.
-
Step 2 Locate the sub-band in which the watermark was embedded. Subtract the original sub-band from it and divide it with the embedding strength to determine the watermark pixels. It can be expressed by the following formula:
$$Rw = \frac{We - Wo}{\alpha }$$(6)where We is the located sub-band in which the watermark was embedded, Wo is the original sub-band prior to watermarking and Rw is the recovered watermark pixel.
-
Step 3 Apply IDWT to the recovered sub-band which contains the recovered pixels to reconstruct the watermark image.
5 Performance parameters
Performance of the watermarking scheme is determined on the basis of following parameters:
A. PSNR
Peak signal to noise ratio (PSNR) of an image can be defined by the following formula [13]:
where h(i, j) is the host image, H(i, j) is the watermarked image and M × M is the size of the host image respectively.
B. NC
Normalized correlation (NC) of an image is defined by the following mathematical formula [12]:
where L(i, j) is the extracted watermark image and G(i, j) is the original watermark image respectively.
6 Results
Three images named “Lena”, “Peppers” and “Cameraman”, are used as host image and “CUET logo” is used as the watermark image. All the images are shown in Fig. 8.
The watermarked images are shown in Fig. 9.
Performance of the proposed scheme and comparison with other methods can be discussed as follows:
-
1.
Without contrast and edge sensitivity:
For evaluating the performance of the proposed algorithm without contrast and edge sensitivity, we use a higher value of embedding strength of 0.9. The performance of the proposed scheme can be shown in Table 1.
-
2.
With contrast and edge sensitivity:
The corresponding edge value is changed after changing the contrast value of every host images. The fuzzy interference system takes contrast and edge values as inputs and gives watermarking strength (α) as output. Tables 2, 3 and 4 show the adjustment of watermarking strength with different contrasts and edges for every host images. The corresponding PSNR and NC values simulated for various watermarking strengths are also shown. It can be seen from these results that the PSNR and NC values remain approximately consistent for every host images.
The fuzzy logic adjusts α according to the inputs and keeps the value of PSNR and NC values approximately consistent to an average of 50.1844 dB and 0.9949 for Lena image. For Peppers image these values are 49.9420 dB and 0.9949. For Cameraman image these values are 39.0701 dB and 0.9832. It can be observed that with contrast and edge sensitivity the PSNR values for all the host images are higher compared to the absence of contrast and edge sensitivity. Hence, the imperceptibility is improved.
-
3.
Comparison of the proposed method with other methods
Table 5 shows the PSNR and NC values using Lena and Peppers as host image for different methods without any attack on the image. Comparing them it can be observed that the proposed scheme gives better PSNR value than the other methods which is the indication of good imperceptibility.
Tables 6, 7, 8 and 9 compare different watermarking methods for various image processing attacks. It can be seen that the proposed method gives better NC values than the other methods which is the indicator of good robustness. It should be noted that results for noise attack in Refs. [12] and [14] are for Gaussian noise and in Ref. [13] and proposed method are for salt and pepper noise.
Figures 10 and 11 shows the comparison of the proposed method with other existing methods in terms of the average PSNR and average NC values. It can be observed that the proposed method has better PSNR and NC values which are the direct result of using fuzzy logic and maximum entropy region. Therefore, the proposed method can be considered as more imperceptible and robust than other schemes.
Table 10 shows the performance of the proposed method for the cameraman image. It shows a slightly decreased performance compared to the other host images. The recovered watermark images after various attacks are shown in Fig. 12.
7 Conclusion
In this paper, a fuzzy rule-based watermarking algorithm is discussed which eliminates the varying performance of the algorithm with varying contrasts and edges. The fuzzy logic effectively determines the watermarking strength based on contrast and edge sensitivity. Performance of the system is better than the conventional fuzzy based watermarking algorithms as it shows a higher degree of robustness and imperceptibility. Use of maximum entropy region also gives the advantage to hide the information based on entropy which is unpredictable in the extraction phase of an unknown receiver. Based on these advantages, this method can be a potential solution for the drawbacks of existing fuzzy based watermarking algorithms and can be applied in the related fields. In Future, more fuzzy rules on other properties of HVS can be added for smooth and precise operation of the algorithm. Besides, other fuzzy logic based systems apart from Mamdani type can also be investigated. The sophisticated physical implementation equipments which will handle the embedding and extraction process can also be experimented in future.
References
Jagadeesh B, Praveen Kumar D (2014) Fuzzy-neuro based robust digital image watermarking technique. Int J Adv Res Comput Commun Eng 3(7):7380–7385
Gaata M, Puech W, Sadkhn S (2011) Digital watermarking method based on fuzzy image segmentation technique. In: Proceedings of 2011 IEEE international symposium on signal processing and information technology (ISSPIT), pp 218–223, https://doi.org/10.1109/isspit.2011.6151563
Latif A (2013) An adaptive digital image watermarking scheme using fuzzy logic and Tabu search. J Inf Hiding Multimed Signal Process 4(4):250–271
Kaur K, ErS Kaur (2016) Advanced fuzzy logic based image watermarking technique for medical images. Int J Adv Res Ideas Innov Technol 3(1):1–7
Abraham J, Paul V (2017) An imperceptible spatial domain color image watermarking scheme. J King Saud Univ Comput Inf Sci 31(1):1–10
Singh S, Singh HV, Mohan A (2015) Secure and robust watermarking using wavelet transform and student t-distribution. In: Proceedings of 4th international conference on eco-friendly computing and communication systems (ICECCS 2015). Procedia Computer Science (Elsevier), pp 442–447. https://doi.org/10.1016/j.procs.2015.10.071
Lande PU, Talbar SN, Shinde GN (2010) Robust image adaptive watermarking using fuzzy logic an FPGA approach. Int J Signal Process Image Process Pattern Recognit 3(4):43–54
Jamali M, Rafiee S, Soroushmehr SMR, Karimi N, Shirani S, Najarian K, Samavi S (2017) Adaptive blind image watermarking using fuzzy inference system based on human visual perception. Cornell University Library, Ithaca
Coumou DJ, Mathew A, A fuzzy logic approach to digital image watermarking. https://www.researchgate.net/profile/David_Coumou/publication/249670322_A_FUZZY_LOGIC_APPROACH_TO_DIGITAL_IMAGE_WATERMARKING/links/542435cf0cf238c6ea6e9aa9.pdf. Accessed 9 Sept 2014
Kumar A, NarayanaRao TV (2016) Digital image watermarking using fuzzy logic and genetic algorithm. Int J Comput Trends Technol 41(2):101–105
Huang H-C, Chen Y-H, Abraham A (2010) Optimized watermarking using swarm-based bacterial foraging. J Inf Hiding Multimed Signal Process 1(1):51–58
Agarwal Charu, Mishra Anurag, Sharma Arpita (2015) A novel gray-scale image watermarking using hybrid fuzzy-BPN architecture. Egypt Inform J 16:83–102
Jagadeesh B, Rajesh Kumar P, Chenna Reddy P (2015) Fuzzy inference system based robust digital image watermarking technique using discrete cosine transform. In: Proceedings of international conference on information and communication technologies (ICICT 2014). Procedia Computer Science (Elsevier), pp 1618–1625
Sridevi T, Sameena Fatima S (2013) Digital image watermarking using fuzzy logic approach based on DWT and SVD. Int J Comput Appl 74(13):16–20
Strong AW (1995) Maximum entropy imaging of COMPTEL data. In: Bassani L, Di Cocco G (eds) Imaging in high energy astronomy. Springer, Dordrecht. https://link.springer.com/chapter/10.1007/978-94-011-0407-4_12
Sakr N, Zhao J, Groza V (2005) A dynamic fuzzy logic approach to adaptive HVS-based watermarking. In: Proceedings of IEEE international workshop on haptic audio visual environments and their applications, pp 121–126. https://doi.org/10.1109/have.2005.1545664
Imran M, Ghafoor A, Riaz MM Adaptive watermarking technique based on human visual system and fuzzy inference system. In: Proceedings of IEEE international symposium on circuits and systems (ISCAS 2013), pp 2816–2819. https://doi.org/10.1109/iscas.2013.6572464
Funding
This work was financially supported by Chittagong University of Engineering & Technology.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest regarding the publication of this paper. The images are used with no conflict of copyright statements.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Dhar, J.P., Islam, M.S. & Ullah, M.A. A fuzzy logic based contrast and edge sensitive digital image watermarking technique. SN Appl. Sci. 1, 716 (2019). https://doi.org/10.1007/s42452-019-0731-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42452-019-0731-x