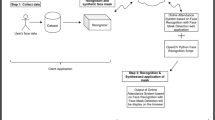
Abstract
The use of mobile computing devices like laptops, smartphones, tablets, etc. ease user access to work or connect remotely for performing a number of operations. Also, with the advent of these new technologies and devices, one of the major concerns emerges in the form of security for one’s personal data or information. Passwords are very critical to human safety as he or she could be a victim of unauthorized access, data misuse or even they may face some legal trouble because of unconventional activities. Robust passwords are recommended in this act to avoid various outbreaks. But, these passwords are not easy to remember in most of the cases. Therefore, an effort has been made in this paper to present a new graphical password-based method that verifies a user’s authenticity by using images as a password. In this regard, a two-way password verification system is adopted using non-regular low-density parity-check codes and an encryption methodology. The performance of the proposed work was evaluated for three different cases i.e. (a) To validate image for about thirteen of modifications (b) To validate image for different format conversion, and (c) Similarity measures for different face images taken from labeled faces in the wild (LFW) database. Results validated the performance of the proposed method when compared with other state-of-the-art approaches.






Similar content being viewed by others
Availability of data and material
Not applicable.
Code availability
Appended at the last.
References
Lin Y, Varodayan D, Girod B (2012) Image authentication using distributed source coding. IEEE Trans Image Process 21(1):273–283. https://doi.org/10.1109/TIP.2011.2157515
Tabatabaei SAH, Rehman OU, Zivic N, Ruland C (2015) Secure and robust two-phase image authentication. IEEE Trans Multimed 17(7):945–956. https://doi.org/10.1109/TMM.2015.2432672
Galbally J, Marcel S, Fierrez J (2014) Image quality assessment for fake biometric detection: application to iris, fingerprint and face recognition. IEEE Trans Image Process 23(2):710–724. https://doi.org/10.1109/TIP.2013.2292332
Li X, Sun X, Liu Q (2015) Image integrity authentication scheme based on fixed point theory. IEEE Trans Image Process 24(2):632–645. https://doi.org/10.1109/tip.2014.2372473
Bianchi A, Oakley I, Kim H (2016) PassBYOP: bring your own picture for securing graphical passwords. IEEE Trans Hum Mach Syst 46(3):380–389. https://doi.org/10.1109/THMS.2015.2487511
Guo G, Wen L, Yan S (2014) Face authentication with makeup changes. IEEE Trans Circuits Syst Video Technol 24(5):814–825. https://doi.org/10.1109/TCSVT.2013.2280076
Dubey RK, Goh J, Thing VLL (2016) Fingerprint liveness detection from single image using low-level features and shape analysis. IEEE Trans Inf Forensics Secur 11(7):1461–1475. https://doi.org/10.1109/TIFS.2016.2535899
Sharghi H, Sartipi K (2016) A user behavior-based approach to detect the insider threat in distributed diagnostic imaging systems. IEEE Int Symp Comput Based Med Syst. https://doi.org/10.1109/CBMS.2016.58
Bashar F, Khan A, Ahmed F, Kabir H (2014) Face recognition using similarity pattern of image directional edge response. Adv Electr Comput Eng 14(1):69–76. https://doi.org/10.4316/AECE.2014.01011
Ardizzone E, Bruno A, Mazzola G (2015) Copy-move forgery detection by matching triangles of key points. IEEE Trans Inf Forensics Secur 10(10):2084–2094. https://doi.org/10.1109/TIFS.2015.2445742
Cozzolino D, Poggi G, Verdoliva L (2015) Efficient dense-field copy–move forgery detection. IEEE Trans Inf Forensics Secur 10(11):2284–2297. https://doi.org/10.1109/TIFS.2015.2455334
Hamad S, Khalifa A, Elhadad A (2014) A blind high-capacity wavelet-based steganography technique for hiding images into other images. Adv Electr Comput Eng 14(2):35–42. https://doi.org/10.4316/AECE.2014.02006
Pande A, Chen S, Mohapatra P, Zambreno J (2014) Hardware architecture for video authentication using sensor pattern noise. IEEE Trans Circuits Syst Video Technol 24(1):157–167. https://doi.org/10.1109/TCSVT.2013.2276869
Battiato S, Farinella GM, Messina E, Puglisi G (2012) Robust image alignment for tampering detection. IEEE Trans Inf Forensics Secur 7(4):1105–1117. https://doi.org/10.1109/TIFS.2012.2194285
Zhao Y, Wang S, Zhang X, Yao H (2013) Robust hashing for image authentication using Zernike moments and local features. IEEE Trans Inf Forensics Secur 8(1):55–63. https://doi.org/10.1109/TIFS.2012.2223680
Korus P, Huang J (2016) Multi-scale fusion for improved localization of malicious tampering in digital images. IEEE Trans Image Process 25(3):1312–1326. https://doi.org/10.1109/TIP.2016.2518870
Lee J, Bauer L, Mazurek ML (2015) The effectiveness of security images in internet banking. IEEE Internet Comput 19(1):54–62. https://doi.org/10.1109/MIC.2014.108
Liveris AD, Xiong Z, Georghiades CN (2002) Compression of binary sources with side information at the decoder using LDPC codes. IEEE Commun Lett 6(10):440–442. https://doi.org/10.1109/LCOMM.2002.804244
Popescu AC, Farid H (2005) Exposing digital forgeries in color filter array interpolated images. IEEE Trans Signal Process 53(10):3948–3959. https://doi.org/10.1109/TSP.2005.855406
Yeh CH, Lee G, Lin CY (2015) Robust laser speckle authentication system through data mining techniques. IEEE Trans Ind Inf 11(2):505–512. https://doi.org/10.1109/TII.2015.2400411
Smith DF, Wiliem A, Lovell BC (2015) Face recognition on consumer devices: reflections on replay attacks. IEEE Trans Inf Forensics Secur 10(4):736–745. https://doi.org/10.1109/tifs.2015.2398819
Thavalengal Corcoran P (2016) User authentication on smart-phones: focusing on iris biometrics. IEEE Consum Electron Mag 5(2):87–93. https://doi.org/10.1109/MCE.2016.2522018
Bae NS, Memon N (2014) Online signature verification on mobile devices. IEEE Trans Inf Forensics Secur 9(6):933–947. https://doi.org/10.1109/TIFS.2014.2316472
Le N, Retraint F (2019) An improved algorithm for digital image authentication and forgery localization using demosaicing artifacts. IEEE Access 7:125038–125053. https://doi.org/10.1109/ACCESS.2019.2938467
Luan G, Li A, Zhang D, Wang D (2019) Asymmetric image encryption and authentication based on equal modulus decomposition in the Fresnel transform domain. IEEE Photon J 11(1):1–7. https://doi.org/10.1109/JPHOT.2018.2886295
Kumar SBJ, Nair A, Raj RVK (2017) Hybridization of RSA and AES algorithms for authentication and confidentiality of medical images. Int Conf Commun Signal Process. https://doi.org/10.1109/ICCSP.2017.8286536
Papadopoulos A, Nguyen T, Durmus E, Memon N (2017) IllusionPIN: shoulder-surfing resistant authentication using hybrid images. IEEE Trans Inf Forensics Secur 12(12):2875–2889. https://doi.org/10.1109/TIFS.2017.2725199
Yi F, Kim Y, Moon I (2018) Secure image-authentication schemes with hidden double random-phase encoding. IEEE Access 6:70113–70121. https://doi.org/10.1109/ACCESS.2018.2880730
Huang GB, Ramesh M, Berg T, Erik Learned-Miller (2007) Labeled faces in the wild: a database for studying face recognition in unconstrained environments. University of Massachusetts, Amherst, Technical Report 07-49
Chouhan SS, Kaul A, Singh UP (2019) Image segmentation using computational intelligence techniques: review. Arch Comput Methods Eng 26:533–596. https://doi.org/10.1007/s11831-018-9257-4
Chouhan SS, Kaul A, Singh UP (2018) Soft computing approaches for image segmentation: a survey. Multimed Tools Appl 77:28483–28537. https://doi.org/10.1007/s11042-018-6005-6
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The corresponding author on behalf of all the author states that there is no conflict of interest to disclose
Appendix: Code for the proposed method
Appendix: Code for the proposed method





























Rights and permissions
About this article
Cite this article
Singh, U.P., Chouhan, S.S. & Jain, S. Images as graphical password: verification and analysis using non-regular low-density parity check coding. Int. j. inf. tecnol. (2020). https://doi.org/10.1007/s41870-020-00477-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s41870-020-00477-x