Abstract
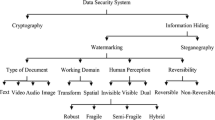
Multimedia technology usages is increasing day by day and to provide authorized data and protecting the secret information from unauthorized use is highly difficult and involves a complex process. By using the watermarking technique, only authorized user can use the data. Digital watermarking is a widely used technology for the protection of digital data. Digital watermarking deals with the embedding of secret data into actual information. Digital watermarking techniques are classified into three major categories, and they were based on domain, type of document (text, image, music or video) and human perception. Performance of the watermarked images is analysed using Peak signal to noise ratio, mean square error and bit error rate. Watermarking of images has been researched profoundly for its specialized and modern achievability in all media applications such as copyrights protection, medical reports (MRI scan and X-ray), annotation and privacy control. This paper reviews the watermarking technique and its merits and demerits.









Similar content being viewed by others
References
Allaf AH, Kbir MA (2018) A review of digital watermarking applications for medical image exchange security. In: The proceedings of the third international conference on smart city applications, pp 472–480
Arya RK, Singh S, Saharan R (2015) A secure non-blind block based digital image watermarking technique using DWT and DCT. In: IEEE international conference on advances in computing, communications and informatics (ICACCI), pp 2042–2048
Barni M, Bartolini F, Piva A (2001) Improved wavelet based watermarking through pixel-wise masking. IEEE Trans Image Process 10(5):783–791
Bell AE (1999) The dynamic digital disk. IEEE Spectr 36(10):28–35
Chamlawi R, Khan A, Idris A (2007) Wavelet based image authentication and recovery. J Comput Sci Technol 22(6):795–804
Chang CC, Fan YH, Tai WL (2008) Four-scanning attack on hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 41(2):654–661
Chen CC, Fan KC, Wang SW (2003) A wavelet-based public key image authentication watermarking. In: IEEE annual international Carnahan conference on security technology, pp 321–324
Chen TH, Horng G, Wang SH (2003b) A robust wavelet-based watermarking scheme using quantization and human visual system model. Pak J Inf Technol 2(3):213–230
Chen M, Chen Z, Zeng X, Xiong Z (2009) Reversible image watermarking based on full context prediction. In: IEEE international conference on image processing, pp 4253–4256
Coltuc D (2011) Improved embedding for prediction-based reversible watermarking. IEEE Trans Inf Forensics Secur 6(3):873–882
Cox J, Miller ML, Bloom JA, Fridrich J, Kalker T (2007) Digital watermarking and steganography. Elsevier, Amsterdam
Dili RB, Mwangi E (2007) An image watermarking method based on the singular value decomposition and the wavelet transform. IEEE AFRICON, pp 1–5
Dumitrescu S, Wu X, Wang Z (2002) Detection of LSB steganography via sample pair analysis. In: International workshop on information hiding, pp 355–372
El Bakrawy LM, Ghali NI, ella Hassanien A, Kim TH (2011) A rough k-means fragile watermarking approach for image authentication. In: IEEE federated conference on computer science and information systems (FedCSIS), pp 19–23
Feng JB, Lin IC, Tsai CS, Chu YP (2006) Reversible watermarking: current status and key issues. IJ Netw Secur 2(3):161–170
Ganic E, Eskicioglu AM (2004) Robust DWT-SVD domain image watermarking: embedding data in all frequencies. In: ACM proceedings of the workshop on multimedia and security, pp 166–174
Gonge SS, Ghatol A (2016) Composition of DCT-SVD image watermarking and advanced encryption standard technique for still image. In: The international symposium on intelligent systems technologies and applications, pp 85–97
Hsieh MS, Tseng DC, Huang YH (2001) Hiding digital watermarks using multiresolution wavelet transform. IEEE Trans Ind Electron 48(5):875–882
Hsu CT, Wu JL (1998) Multi-resolution watermarking for digital images. IEEE Trans Circ Syst II Analog Dig Signal Process 45(8):1097–1101
Hung KL, Chang CC, Chen TS (2001) Secure discrete-cosine-transform-based technique for recoverable tamper proofing. Opt Eng 40(9):1950–1958
Hyung-Shin K, Baek Y, Heung-Kyu L, Young-Ho S (2002) Robust image watermark using Radon transform and bispectrum invariants. In: International workshop on information hiding, pp 145–159
Jialing H, Xiaohui Z, Chunyan Q (2016) A digital image watermarking method based on host image analysis and genetic algorithm. J Ambient Intell Hum Comput 7(1):37–45
Johnson NF (1999) An introduction to watermark recovery from images. In: Proceedings of SANS intrusion detection and response conference, pp 1–6
Kahaner D, Moler C, Nash S (1989) Numerical methods and software. Prentice Hall, Englewood Cliffs
Kino M, Wada S (2004) Wavelet based perceptual watermarking with bit data embedded in still color images. Electron Commun Jpn Part III Fund Electron Sci 87(1):1–9
Ko LT, Chen JE, Shieh YS, Hsin HC, Sung TY (2012) Nested quantization index modulation for reversible watermarking and its application to healthcare information management systems. In: Computational and mathematical methods in medicine, pp 1–9
Koch E, Zhao J (1995) Towards robust and hidden image copyright labeling. IEEE Workshop Nonlinear Signal Image Process 1:123–132
Komatsu N, Tominaga H (1988) Authentication system using concealed images in telematics. Mem Sch Sci Eng Waseda Univ 52:45–60
Kundur D, Hatzinakos D (1997) A robust digital image watermarking method using wavelet-based fusion. IEEE Proc Int Conf Image Process 1:544–547
Kundur D, Hatzinakos D (1999) Digital watermarking for telltale tamper proofing and authentication. Proc IEEE 87(7):1167–1180
Lai CC, Huang HC, Tsai CC (2008). Image watermarking scheme using singular value decomposition and micro-genetic algorithm. In: IEEE international conference on intelligent information hiding and multimedia signal processing, pp 469–472
Lee S, Jang D, Yoo CD (2005) An SVD-based watermarking method for image content authentication with improved security. In Proceedings (ICASSP’05), IEEE international conference on acoustics, speech, and signal processing, vol 2, pp 525–528
Li KF, Chen TS, Wu SC (2001) Image tamper detection and recovery system based on discrete wavelet transformation. IEEE Pac Rim Conf Commun Comput Signal Process 1:164–167
Li Q, Yuan C, Zhong YZ (2007) Adaptive DWT-SVD domain image watermarking using human visual model. IEEE Int Conf Adv Commun Technol 3:1947–1951
Lin CY, Wu M, Bloom JA, Cox IJ, Miller ML, Lui YM (2001) Rotation, scale and translation resilient watermarking for image. IEEE Trans Image Process 10(5):767–782
Lin CH, Su TS, Hsieh WS (2007) Semi-fragile watermarking scheme for authentication of JPEG images. Tamkang J Sci Eng 10(1):57–66
Lin C, Pan JS, Lu ZM (2008) A double domain based robust digital image watermarking scheme. In: International conference on technologies for E-learning and digital entertainment, pp 656–663
Lingling Z, Wei R, Yuling C, Min L (2019) LMDGW: a novel matrix based dynamic graph watermark. J Ambient Intell Hum Comput 10(1):295–304
Liu H, Steinebach M (2006) Semi-fragile watermarking for image authentication with high tampering localization capability. In: IEEE 2nd international conference on automated production of cross media content for multi-channel distribution, pp 143–152
Lu CS, Liao HY (2001) Multipurpose watermarking for image authentication and protection. IEEE Trans Image Process 10(10):1579–1592
Macq BM, Quisquater JJ (1995) Cryptology for digital TV broadcasting. Proc IEEE 83(6):944–957
Meerwald P (2001) Quantization watermarking in the JPEG2000 coding pipeline. In: Communications and multimedia security issues of the New Century, pp 69–79
Potdar VM, Han S, Chang E (2005) A survey of digital image watermarking techniques. In: IEEE international conference on industrial informatics, pp 709–716
Radhakrishnan R, Memon N (2002) On the security of the digest function in the SARI image authentication system. IEEE Trans Circ Syst Video Technol 12(11):1030–1033
Ratha NK, Connell JH, Bolle RM (2000) Secure data hiding in wavelet compressed fingerprint images. In: ACM proceedings of the workshops on multimedia, pp 127–130
Raval MS, Rege PP (2003) Discrete wavelet transform based multiple watermarking scheme. IEEE Conf Converg Technol Asia Pac Region 3:935–938
Rhoads GB (1995) Identification/authentication coding method and apparatus. World Intellectual Property Organization
SDMI (1999) SDMI portable device specification, Part 1 (version 1.0)
Seo YH, Choi SY, Park SH, Kim DW (2004) A digital watermarking algorithm using correlation of the tree structure of DWT coefficients. IEICE Trans Fund Electron Commun Comput Sci 87(6):1347–1354
Shieh CS, Huang HC, Wang FH, Pan JS (2004) Genetic watermarking based on transform-domain techniques. Pattern Recogn 37(3):555–565
Singh AK, Sharma N, Dave M, Mohan A (2012) A novel technique for digital image watermarking in spatial domain. In: IEEE international conference on parallel, distributed and grid computing, pp 497–501
Soualmi A, Alti A, Laouamer L (2018) A new blind medical image watermarking based on weber descriptors and Arnold chaotic map. Arab J Sci Eng 43(12):7893–7905
Suthaharan S (2004) Fragile image watermarking using a gradient image for improved localization and security. Pattern Recogn Lett Elsevier Sci 25(16):1893–1903
Suthaharan S, Kim SW, Lee HK, Sathananthan S (2000) Perceptually tuned robust watermarking scheme for digital images. Pattern Recogn Lett 21(2):145–149
Tao P, Eskicioglu AM (2004) A robust multiple watermarking scheme in the discrete wavelet transform domain. Int Multimed Manag Syst 5601:133–144
Tsai MJ, Yu KY, Chen YZ (2000) Joint wavelet and spatial transformation for digital watermarking. IEEE Trans Consum Electron 46(1):241–245
Van Schyndel RG, Tirkel AZ, Osborne CF (1994) A digital watermark. IEEE Proc Int Conf Image Process 2:86–90
Waldemar P, Ramstad TA (1997) Hybrid KLT-SVD image compression. IEEE Int Conf Acoust Speech Signal Process 4:2713–2716
Wang CT, Chen TS, He SH (2003) Detecting and restoring the tampered images based on iteration-free fractal compression. J Syst Softw 67(2):131–140
Yang H, Sun X, Sun G (2010) A semi-fragile watermarking algorithm using adaptive least significant bit substitution. Inf Technol J 9(1):20–26
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mohanarathinam, A., Kamalraj, S., Prasanna Venkatesan, G.K.D. et al. Digital watermarking techniques for image security: a review. J Ambient Intell Human Comput 11, 3221–3229 (2020). https://doi.org/10.1007/s12652-019-01500-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01500-1