Abstract
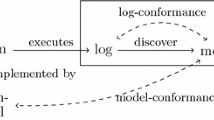
Process mining is a set of techniques in the field of process management that have primarily been used to analyse business processes, for example for the optimisation of enterprise resources. In this research, the feasibility of using process mining techniques for the analysis of event data from machine logs is investigated. A novel methodology, based on process mining, for profiling abnormal machine behaviour is proposed. Firstly, a process model is constructed from the event logs of the healthy machines. This model can subsequently be used as a benchmark to compare process models of other machines by means of conformance checking. This comparison results in a set of conformance scores related to the structure of the model and other more complex aspects such as the differences in duration of particular traces, the time spent in individual events, and the relative path frequency. The identified differences can subsequently be used as a basis for root cause analysis. The proposed approach is evaluated on a real-world industrial data set from the renewable energy domain, more specifically event logs of a fleet of inverters from several solar plants.






Similar content being viewed by others
References
van der Aalst W, Adriansyah A, van Dongen B (2012) Replaying history on process models for conformance checking and performance analysis. WIREs Data Mining and Knowledge Discovery 2(2):182–192. https://doi.org/10.1002/widm.1045
Van der Aalst W, Weijters T, Maruster L (2004) Workflow mining: discovering process models from event logs. IEEE Trans Knowl Data Eng 16(9):1128–1142
van der Aalst WM (2014) Process mining in the large: a tutorial. Springer International Publishing, Cham, pp 33–76. https://doi.org/10.1007/978-3-319-05461-2_2
Bolt A, de Leoni M, van der Aalst WMP (2016) A visual approach to spot statistically-significant differences in event logs based on process metrics. In: Nurcan S, Soffer P, Bajec M, Eder J (eds) Advanced information systems engineering. Springer International Publishing, Cham, pp 151–166
Calderón-Ruiz G, Sepúlveda M (2013) Automatic discovery of failures in business processes using process mining techniques. In: Anais principais do IX simpósio brasileiro de sistemas de informação, SBC, pp 439–450
Dagnely P, Tsiporkova E, Tourwé T, Ruette T, De Brabandere K, Assiandi F (2015) A semantic model of events for integrating photovoltaic monitoring data. In: 2015 IEEE 13Th international conference on industrial informatics (INDIN), pp 24–30. https://doi.org/10.1109/INDIN.2015.7281705
van Dongen BF, de Medeiros AKA, Verbeek HMW, Weijters AJMM, van der Aalst WMP (2005) The prom framework: a new era in process mining tool support. In: Proceedings of the 26th international conference on applications and theory of petri nets, ICATPN?05. Springer, Berlin, pp 444–454. https://doi.org/10.1007/11494744_25
Gupta N, Anand K, Sureka A (2015) Pariket: Mining business process logs for root cause analysis of anomalous incidents. In: Chu W, Kikuchi S, Bhalla S (eds) Databases in networked information systems. Springer International Publishing, Cham, pp 244–263
Leemans SJ, Fahland D, van der Aalst WM (2014) Discovering block-structured process models from incomplete event logs. In: International conference on applications and theory of petri nets and concurrency, Springer, pp 91–110
Leemans SJJ, Fahland D, van der Aalst WMP (2014) Process and deviation exploration with inductive visual miner. In: BPM (Demos), CEUR workshop proceedings, vol 1295, CEUR-WS.org, pp 46
Rozinat A, van der Aalst WMP (2008) Conformance checking of processes based on monitoring real behavior. Inf Syst 33(1):64–95. https://doi.org/10.1016/j.is.2007.07.001
Suriadi S, Ouyang C, van der Aalst WMP, ter Hofstede AHM (2013) Root cause analysis with enriched process logs. In: La Rosa M, Soffer P (eds) Business process management workshops. Springer, Berlin, pp 174–186
van der Aalst W, de Medeiros A (2005) Process mining and security: detecting anomalous process executions and checking process conformance. Electronic Notes in Theoretical Computer Science 121:3–21. https://doi.org/10.1016/j.entcs.2004.10.013. http://www.sciencedirect.com/science/article/pii/S1571066105000228. Proceedings of the 2nd International Workshop on Security Issues with Petri Nets and other Computational Models (WISP 2004)
Weijters A, van Der Aalst WM, De Medeiros AA (2006) Process mining with the heuristics miner-algorithm. Technische Universiteit Eindhoven Tech Rep WP 166:1–34
Wilson P, Dell L, Anderson G (1993) Root cause analysis: a tool for total quality management workbook. ASQC Quality Press. https://books.google.be/books?id=36SO86CQ2CYC
Acknowledgements
The authors would like to thank 3E (http://www.3e.eu) for granting access to the data and providing domain expert feedback on the results and Pierre Dagnely for the initial preprocessing of the data.
Funding
This work was funded in part by the Region of Bruxelles-Capitale - Innoviris and in part by the Flemish Government (AI Research Program).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Maeyens, J., Vorstermans, A. & Verbeke, M. Process mining on machine event logs for profiling abnormal behaviour and root cause analysis. Ann. Telecommun. 75, 563–572 (2020). https://doi.org/10.1007/s12243-020-00809-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-020-00809-9