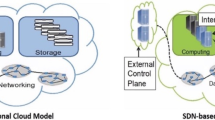
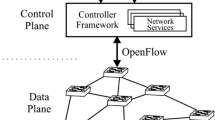
Abstract
Internal users are the main causes of anomalous and suspicious behaviors in a communication network. Even when traditional security middleboxes are present, internal attacks may lead the network to outages or to leakage of sensitive information. In this article, we propose BroFlow, an Intrusion Detection and Prevention System based on Bro traffic analyzer and on the global network view of the software-defined networks (SDN) which is provided by the OpenFlow. BroFlow main contributions are (i) dynamic and elastic resource provision of traffic-analyzing machines under demand; (ii) real-time detection of DoS attacks through simple algorithms implemented in a policy language for network events; (iii) immediate reaction to DoS attacks, dropping malicious flows close of their sources, and (iv) near-optimal placement of sensors through a proposed heuristic for strategically positioning sensors in the network infrastructure, which is shared by multi-tenants, with a minimum number of sensors. We developed a prototype of the proposed system, and we evaluated it in a virtual environment of the Future Internet Testbed with Security (FITS). An evaluation of the system under attack shows that BroFlow guarantees the forwarding of legitimate packets at the maximal link rate, reducing up to 90 % of the maximal network delay caused by the attack. BroFlow reaches 50 % of bandwidth gain when compared with conventional firewalls approaches, even when the attackers are legitimate tenants acting in collusion. In addition, the system reduces the sensors number, while keeping full coverage of network flows.











Similar content being viewed by others
References
Che X, Lopez J, Maag S, Morales G (2015) Testing trust properties using a formal distributed network monitoring approach. Ann Telecommun 70(3–4):95–105
Chen H, Clark JA, Tapiador JE, Shaikh SA, Chivers H, Nobles P (2009) A multi-objective optimisation approach to IDS sensor placement. In: Computational intelligence in security for information systems. Springer, pp 101–108
Coutinho E, de Carvalho Sousa F, Rego P, Gomes D, de Souza J (2015) Elasticity in cloud computing: a survey. Ann Telecommun 70(7–8):289–309
Fernandes NC, Moreira MDD, Moraes IM, Ferraz LHG, Couto RS, Carvalho HET, Campista MEM, Costa LHMK, Duarte OMB (2011) Virtual networks: isolation, performance, and trends. Ann Telecommun 66(5-6):339–355
Ferraz LHG, Mattos DMF, Duarte OCMB (2014) A two-phase multipathing scheme based on genetic algorithm for data center networking. In: IEEE global communications conference - GLOBECOM, pp 2270–2275
Giotis K, Argyropoulos C, Androulidakis G, Kalogeras D, Maglaris V (2014) Combining OpenFlow and sFlow for an effective and scalable anomaly detection and mitigation mechanism on SDN environments. Comput Netw 62:122–136
Hu H, Han W, Ahn GJ, Zhao Z (2014) FLOWGUARD: building robust firewalls for Software-Defined Networks. In: Proceedings of the 3rd workshop on hot topics in SDN. ACM, pp 97–102
Mattos DMF, Duarte OCMB (2014) XenFlow: Seamless migration primitive and Quality of Service for virtual networks. In: IEEE global communications conference - GLOBECOM
McKeown N, Anderson T, Balakrishnan H, Parulkar G, Peterson L, Rexford J, Shenker S, Turner J (2008) OpenFlow: enabling innovation in campus networks. SIGCOMM Comput Commun 38:69–74
Mehdi SA, Khalid J, Khayam SA (2011) Revisiting traffic anomaly detection using software defined networking. In: Recent advances in intrusion detection. Springer, pp 161–180
Moraes IM, Mattos DM, Ferraz LHG, Campista MEM, Rubinstein MG, Costa LHM, de Amorim MD, Velloso PB, Duarte OC, Pujolle G (2014) FITS: a flexible virtual network testbed architecture. Comput Netw 63:221–237
Nam J, Jamshed M, Choi B, Han D, Park K (2015) Scaling the performance of network intrusion detection with many-core processors. In: ACM/IEEE symposium on architectures for networking and communications systems (ANCS) , pp 191–192
Paxson V (1999) Bro: a system for detecting network intruders in real-time. Comput Netw 31(23–24):2435–2463
Piedrahita AFM, Rueda S, Mattos DM, Duarte OCM (2015) FlowFence: a denial of service defense system for software defined networking. In: Global information infrastructure and networking symposium -GIIS, p 6
Shanmugam PK, Subramanyam ND, Breen J, Roach C, Van der Merwe J (2014) DEIDtect: towards distributed elastic intrusion detection. In: Proceedings of the 2014 ACM SIGCOMM workshop on distributed cloud computing - DCC , pp 17–24
Siris VA, Papagalou F (2006) Application of anomaly detection algorithms for detecting SYN flooding attacks. Comput Commun 29:1433–1442
Sommer R, Paxson V (2010) Outside the closed world: on using machine learning for network intrusion detection. In: IEEE symposium on security and privacy, pp 305–316
Weaver N, Sommer R (2007) Stress testing cluster Bro. In: Proceedings of the DETER community workshop on cyber security experimentation and test. USENIX Association , pp 9–9
Xing T, Huang D, Xu L, Chung CJ, Khatkar P (2013) SnortFlow: a OpenFlow-based intrusion prevention system in cloud environment. In: 2nd GENI research and educational experiment workshop, pp 89–92
Yoon C, Park T, Lee S, Kang H, Shin S, Zhang Z (2015) Enabling security functions with SDN: a feasibility study. Computer Networks 1(1)
Acknowledgment
We also thank Lyno Henrique Gonçalves Ferraz, Antonio Lobato and Ulisses Figueredo for their significant contributions to obtain the results.
Author information
Authors and Affiliations
Corresponding author
Additional information
This work was supported by CNPq, CAPES, and FAPERJ.
Rights and permissions
About this article
Cite this article
Lopez, M.A., Ferrazani Mattos, D.M. & Duarte, O.C.M.B. An elastic intrusion detection system for software networks. Ann. Telecommun. 71, 595–605 (2016). https://doi.org/10.1007/s12243-016-0506-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-016-0506-y