Abstract
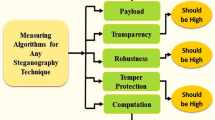
Steganography is the technique for hiding information within a carrier file so that it is imperceptible for unauthorized parties. In this study, it is intended to combine many techniques to gather a new method for colour image steganography to obtain enhanced efficiency, attain increased payload capacity, posses integrity check and security with cryptography at the same time. Proposed work supports many different formats as payload. In the proposed method, the codeword is firstly formed with secret data and its CRC-32 checksum, then the codeword is compressed by Gzip just before encrypting it by AES, and it is finally added to encrypted header information for further process and then embedded into the cover image. Embedding the encrypted data and header information process utilizes Fisher-Yates Shuffle algorithm for selecting next pixel location. To hide one byte, different LSB (least significant bits) of all colour channels of the selected pixel is exploited. In order to evaluate the proposed method, comparative performance tests are carried out against different spatial image steganographic techniques using some of the well-known image quality metrics. For security analysis, histogram, enhanced LSB and Chi-square analyses are carried out. The results indicate that with the proposed method has an improved payload capacity, security and integrity check for common problems of simple LSB method. Moreover, it has been shown that the proposed method increases the visual quality of the stego image when compared to other studied methods, and makes the secret message difficult to be discovered.











Similar content being viewed by others
References
Trivedi M C Sharma S and Yadav V K 2016 Analysis of several image steganography techniques in spatial domain: a survey. In; Second International Conference on Information and Communication Technology for Competitive Strategies (ICTCS ‘16). ACM. Article 84
Petitcolas F A P Anderson R J and Kuhn M G 1999 Information hiding-a survey. Proc. IEEE. 87(7): 1062–1078
Mazurczyk W and Caviglione L 2015 Steganography in modern smartphones and mitigation techniques. IEEE Commun. Surv. Tutor. 17(1): 334–357
Singla D and Juneja M 2014 An analysis of edge based image steganography techniques in spatial domain. In: Recent Advances in Engineering and Computer Sciences (RAECS) 1–5
Akhtar N 2016 An LSB substitution with bit inversion steganography method. In: Proceedings of 3rd International Conference on Advanced Computing, Networking and Informatics 43: 515–521
Chen Y, Han Z, Li S, Lu C and Yao X H 2010 An adaptive steganography algorithm based on block sensitivity vectors using HVS features.In: 3rd International Congress in Image and Signal Processing. 1151–1155
Chan C-K and Cheng L-M 2004 Hiding data in images by simple LSB substitution. Pattern Recognit. 37: 469–474
Wu D-A and Tsai W-H 2003 A steganographic method for images by pixel-value differencing. Pattern Recognit. Lett. 24(9–10):1613–1626
Wu H-C, Wu N I, Tsai C S and Hwang M S 2005 Image steganographic scheme based on pixel-value differencing and LSB replacement methods. IEE Proceedings Vision, Image and Signal Processing 152: 611–615
Anand J V and Dharaneetharan G D 2011 New approach in steganography by integrating different LSB algorithms and applying randomization concept to enhance security. Proceedings of the 2011 In: International Conference on Communication, Computing 474–476
Kukapalli V R, Rao T B and Reddy B S 2014 Image Steganograpghy by Enhanced Pixel Indicator Method Using Most Significant Bit (MSB) Compare. International Journal of Computer Trends and Technology 15(3): 97-101
Dighe D and Gand Kapale N D 2013 Random Insertion Using Data Parity Steganography Technique. Int. J. Eng. Sci. Innov Technol (IJESIT) 2(2): 364–368
Bashardoost M, Sulong G B and Gerami P 2013 Enhanced LSB image steganography method by using knight tour algorithm, vigenere encryption and LZW Compression. Int. J. Comput. Sci. Iss. (IJCSI) 10(2) 1: 221–227
Dadgostar H A and Fsari F 2016 Image steganography based on interval-valued intuitionistic fuzzy edge detection and modified LSB. Journal of Information Security and Applications (JISA). 30: 94–104
Fridrich J, Goljan M and Du R 2001 Detecting LSB steganography in colour and gray-scale images. IEEE Trans. Multimed. 8(4): 22–28
Peterson W W and Brown D T 1961 Cyclic Codes for Error Detection. Proc. IRE 49 (1): 228–235
Wikipedia Cyclic redundancy check. https://en.wikipedia.org/wiki/Cyclic_redundancy_check. Accessed on Jan 2018
Gailly J-L and Adler M Gzip Home Page. http://www.gzip.org/. Accessed on Jan 2018
Sahmoud S, Elmasry W and Abudalfa S 2013 Enhancement the security of AES against modern attacks by using Variable key block cipher. Int. Arab J. e-Technol. (IAJeT). 3(1): 17–26
Daemen J and Rijmen V 2001 Rijndael: the advanced encryption standard. Dr. Dobb’s J. 26(03): 137–139
Lou D-C and Sung C-H 2004 A steganographic scheme for secure communications based on the chaos and Euler Theorem. IEEE Trans. Multimed. 6(3): 501–509
Luo W, Huang F and Huang J 2010 Edge adaptive image steganography based on LSB matching revisited. IEEE Trans. Inf. Forensics Secur 5(2): 201–214
Wang S, Yang B and Niu X 2010 A secure steganography method based on genetic algorithm. J. Inf. Hiding Multimed. Signal Process 1(1): 28–35
Fisher R A and Yates F 1948 Statistical tables for biological, agricultural and medical research. London: Oliver & Boyd, pp. 26–27
Sasivarnan C, Jagan A, Kaur J, Jyoti D and Rao D S 2011 Image quality assessment techniques in spatial domain. Int. J. Comput. Sci. Technol (IJCST) 2(3): 177–184
Stanley C A Pairs of Values and the Chi-Squared Attack https://orion.math.iastate.edu/dept/thesisarchive/MSCC/CStanleyMSSS05.pdf. Accessed on Jan 2018.
Cheddad A, Condell J, Curran K and McKevitt P 2010 Digital image steganography: Survey and analysis of current methods. Signal Process. 90(3): 727–752
Li B, He J, Huang J and Shi Y Q 2011 A Survey on Image Steganography and Steganalysis. J. Inf. Hiding Multimed. Signal Process. 2(2):142–172
Jain M and Lenka S K 2016 A review of digital image steganography using LSB and LSB array. Int. J. Appl. Eng. Res. 11(3):1820–1824
Al-Hawi T, Al-Qutayri M and Barada H 2003 A testbed for evaluating security and robustness of steganography techniques. In: IEEE 46th Midwest Symposium in Circuits and Systems. 3: 1583–1586
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Cem kasapbaşi, M., Elmasry, W. New LSB-based colour image steganography method to enhance the efficiency in payload capacity, security and integrity check. Sādhanā 43, 68 (2018). https://doi.org/10.1007/s12046-018-0848-4
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12046-018-0848-4