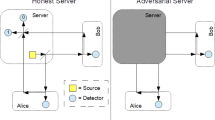
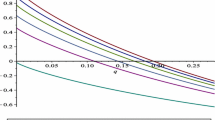
Abstract
Semi-quantum communication, a model introduced by Boyer et al. (Phys Rev Lett 99:140501, 2007), involves the use of fully quantum users and semi-quantum, or “classical” users. These restricted users are only allowed to interact with the quantum channel in a limited manner. Originally introduced to study the key-distribution problem, semi-quantum research has since expanded, and continues to grow, with new protocols, security proof methods, experimental implementations, and new cryptographic applications beyond key distribution. Research in the field of semi-quantum cryptography requires new insights into working with restricted protocols and, so, the tools and techniques derived in this field can translate to results in broader quantum information science. Furthermore, other questions such as the connection between quantum and classical processing, including how classical information processing can be used to counteract a quantum deficiency in a protocol, can shed light on important theoretical questions. This work surveys the history and current state of the art in semi-quantum research. We discuss the model and several protocols offering the reader insight into how protocols are constructed in this realm. We discuss security proof methods and how classical post-processing can be used to counteract users’ inability to perform certain quantum operations. Moving beyond key distribution, we survey current work in other semi-quantum cryptographic protocols and current trends. We also survey recent work done in attempting to construct practical semi-quantum systems including recent experimental results in this field. Finally, as this is still a growing field, we highlight, throughout this survey, several open problems that we feel are important to investigate in the hopes that this will spur even more research in this topic.







Similar content being viewed by others
References
Katz, Jonathan, Lindell, Yehuda: Introduction to Modern Cryptography. Chapman and Hall/CRC, Boca Raton (2014)
Stallings, William: Network Security Essentials: Applications and Standards. Pearson Education India, Bengaluru (2007)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, vol. 175. New York (1984)
Ekert, Artur K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661 (1991)
Shor, Peter W., Preskill, John: Simple proof of security of the bb84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441–444 (2000)
Renner, Renato, Gisin, Nicolas, Kraus, Barbara: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72, 012332 (2005)
Boyer, Michel, Kenigsberg, Dan, Mor, Tal: Quantum key distribution with classical Bob. Phys. Rev. Lett. 99, 140501 (2007)
Scarani, Valerio, Bechmann-Pasquinucci, Helle, Cerf, Nicolas J., Dušek, Miloslav, Lütkenhaus, Norbert, Peev, Momtchil: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301–1350 (2009)
Shenoy-Hejamadi, Akshata, Pathak, Anirban, Radhakrishna, Srikanth: Quantum cryptography: key distribution and beyond. Quanta 6(1), 1–47 (2017)
Razavi, Mohsen, Leverrier, Anthony, Ma, Xiongfeng, Qi, Bing, Yuan, Zhiliang: Quantum key distribution and beyond: introduction. J. Opt. Soc. Am. B 36(3), QKD1–QKD2 (2019)
Pirandola, S., Andersen, U.L., Banchi, L., Berta, M., Bunandar, D., Colbeck, R., Englund, D., Gehring, T., Lupo, C., Ottaviani, C., et al.: Advances in quantum cryptography. arXiv preprint arXiv:1906.01645 (2019)
Boyer, Michel, Gelles, Ran, Kenigsberg, Dan, Mor, Tal: Semiquantum key distribution. Phys. Rev. A 79, 032341 (2009)
Jian, Wang, Sheng, Zhang, Quan, Zhang, Chao-Jing, Tang: Semiquantum key distribution using entangled states. Chin. Phys. Lett. 28(10), 100301 (2011)
Sun, Z., Du, R., Long, D.: Semi-quantum key distribution protocol using bell state. arXiv preprint arXiv:1106.2910 (2011)
Zou, Xiangfu, Qiu, Daowen, Li, Lvzhou, Lihua, Wu, Li, Lvjun: Semiquantum-key distribution using less than four quantum states. Phys. Rev. A 79, 052312 (2009)
Krawec, Walter O.: Restricted attacks on semi-quantum key distribution protocols. Quantum Inf. Process. 13(11), 2417–2436 (2014)
Fung, Chi-Hang Fred, Lo, Hoi-Kwong: Security proof of a three-state quantum-key-distribution protocol without rotational symmetry. Phys. Rev. A 74, 042342 (2006)
Branciard, Cyril, Gisin, Nicolas, Lutkenhaus, Norbert, Scarani, Valerio: Zero-error attacks and detection statistics in the coherent one-way protocol for quantum cryptography. Quantum Inf. Comput. 7(7), 639–664 (2007)
Lucamarini, Marco, Di Giuseppe, Giovanni, Tamaki, Kiyoshi: Robust unconditionally secure quantum key distribution with two nonorthogonal and uninformative states. Phys. Rev. A 80(3), 032327 (2009)
Zhang, W., Qiu, D.: A single-state semi-quantum key distribution protocol and its security proof. arXiv preprint arXiv:1612.03087 (2016)
Hua, Lu, Cai, Qing-Yu.: Quantum key distribution with classical Alice. Int. J. Quantum Inf. 6(06), 1195–1202 (2008)
Sun, Zhi-Wei, Rui-Gang, Du, Long, Dong-Yang: Quantum key distribution with limited classical Bob. Int. J. Quantum Inf. 11(01), 1350005 (2013)
Lin, Po-Hua, Hwang, Tzonelih, Tsai, Chia-Wei: Double cnot attack on “quantum key distribution with limited classical Bob”. Int. J. Quantum Inf. 17(02), 1975001 (2019)
Krawec, W.O., Geiss, E.P.: Semi-quantum key distribution with limited measurement capabilities. In: 2018 International Symposium on Information Theory and its Applications (ISITA), pp. 462–466. IEEE (2018)
Gagliano, A., Krawec, W.O., Iqbal, H.: From classical to semi-quantum secure communication. In: 2019 IEEE International Symposium on Information Theory (ISIT), pp. 1707–1711. IEEE (2019)
Zou, Xiangfu, Qiu, Daowen, Zhang, Shengyu, Mateus, Paulo: Semiquantum key distribution without invoking the classical party’s measurement capability. Quantum Inf. Process. 14(8), 2981–2996 (2015)
Li, Qin, Chan, Wai Hong, Zhang, Shengyu: Semiquantum key distribution with secure delegated quantum computation. Sci. Rep. 6, 19898 (2016)
Kun-Fei, Yu., Yang, Chun-Wei, Liao, Ci-Hong, Hwang, Tzonelih: Authenticated semi-quantum key distribution protocol using Bell states. Quantum Inf. Process. 13(6), 1457–1465 (2014)
Li, Chuan-Ming, Kun-Fei, Yu., Kao, Shih-Hung, Hwang, Tzonelih: Authenticated semi-quantum key distributions without classical channel. Quantum Inf. Process. 15(7), 2881–2893 (2016)
Meslouhi, A., Hassouni, Yassine: Cryptanalysis on authenticated semi-quantum key distribution protocol using Bell states. Quantum Inf. Process. 16(1), 18 (2017)
Amer, Omar, Krawec, Walter O.: Semiquantum key distribution with high quantum noise tolerance. Phys. Rev. A 100(2), 022319 (2019)
Liu, W., Zhou, H.: A new semi-quantum key distribution protocol with high efficiency. In: 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), pp. 2424–2427. IEEE (2018)
Wang, Ming-Ming, Gong, Lin-Ming, Shao, Lian-He: Efficient semiquantum key distribution without entanglement. Quantum Inf. Process. 18(9), 260 (2019)
Lo, Hoi-Kwong, Chau, Hoi-Fung, Ardehali, M.: Efficient quantum key distribution scheme and a proof of its unconditional security. J. Cryptol. 18(2), 133–165 (2005)
Zhang, Ming-Hui, Li, Hui-Fang, Peng, Jin-Ye, Feng, Xiao-Yi: Fault-tolerant semiquantum key distribution over a collective-dephasing noise channel. Int. J. Theor. Phys. 56(8), 2659–2670 (2017)
Tsai, Chih-Lun, Hwang, Tzonelih: Semi-quantum key distribution robust against combined collective noise. Int. J. Theor. Phys. 57(11), 3410–3418 (2018)
Tsai, C.-W., Yang, C.-W.: Cryptanalysis and improvement of the semi-quantum key distribution robust against combined collective noise. Int. J. Theor. Phys. 58, 1–7 (2019)
Vlachou, Chrysoula, Krawec, Walter, Mateus, Paulo, Paunković, Nikola, Souto, André: Quantum key distribution with quantum walks. Quantum Inf. Process. 17(11), 288 (2018)
Iqbal, H., Krawec, W.O.: High-dimensional semi-quantum cryptography. arXiv preprint arXiv:1907.11340 (2019)
Bechmann-Pasquinucci, H., Tittel, Wolfgang: Quantum cryptography using larger alphabets. Phys. Rev. A 61(6), 062308 (2000)
Chau, H.F.: Quantum key distribution using qudits that each encode one bit of raw key. Phys. Rev. A 92(6), 062324 (2015)
Sasaki, Toshihiko, Yamamoto, Yoshihisa, Koashi, Masato: Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509(7501), 475 (2014)
Yin, Zhen-Qiang, Wang, Shuang, Chen, Wei, Han, Yun-Guang, Wang, Rong, Guo, Guang-Can, Han, Zheng-Fu: Improved security bound for the round-robin-differential-phase-shift quantum key distribution. Nat. Commun. 9(1), 457 (2018)
Wang, Rong, Yin, Zhen-Qiang, Cui, Chao-han, Wang, Shuang, Chen, Wei, Guo, Guang-Can, Han, Zheng-Fu: Security proof for single-photon round-robin differential-quadrature-phase-shift quantum key distribution. Phys. Rev. A 98(6), 062331 (2018)
Kempe, Julia: Quantum random walks: an introductory overview. Contemp. Phys. 44(4), 307–327 (2003)
Venegas-Andraca, Salvador Elías: Quantum walks: a comprehensive review. Quantum Inf. Process. 11(5), 1015–1106 (2012)
Maitra, Arpita, Paul, Goutam: Eavesdropping in semiquantum key distribution protocol. Inf. Process. Lett. 113(12), 418–422 (2013)
Devetak, Igor, Winter, Andreas: Distillation of secret key and entanglement from quantum states. Proc. R. Soc. A: Math., Phys. Eng. Sci. 461(2053), 207–235 (2005)
Miyadera, Takayuki: Relation between information and disturbance in quantum key distribution protocol with classical Alice. Int. J. Quantum Inf. 9(06), 1427–1435 (2011)
Fuchs, Christopher A., Gisin, Nicolas, Griffiths, Robert B., Niu, Chi-Sheng, Peres, Asher: Optimal eavesdropping in quantum cryptography. i. Information bound and optimal strategy. Phys. Rev. A 56(2), 1163 (1997)
Krawec, W.O.: Key-rate bound of a semi-quantum protocol using an entropic uncertainty relation. In: 2018 IEEE International Symposium on Information Theory (ISIT), pp. 2669–2673. IEEE (2018)
Krawec, W.O.: Security proof of a semi-quantum key distribution protocol. In: 2015 IEEE International Symposium on Information Theory (ISIT), pp. 686–690. IEEE (2015)
Alicki, Robert, Fannes, Mark: Continuity of quantum conditional information. J. Phys. A: Math. General 37(5), L55 (2004)
Audenaert, Koenraad M.R.: A sharp continuity estimate for the von Neumann entropy. J. Phys. A: Math. Theor. 40(28), 8127 (2007)
Winter, Andreas: Tight uniform continuity bounds for quantum entropies: conditional entropy, relative entropy distance and energy constraints. Commun. Math. Phys. 347(1), 291–313 (2016)
Berta, Mario, Christandl, Matthias, Colbeck, Roger, Renes, Joseph M., Renner, Renato: The uncertainty principle in the presence of quantum memory. Nat. Phys. 6(9), 659–662 (2010)
Coles, Patrick J., Berta, Mario, Tomamichel, Marco, Wehner, Stephanie: Entropic uncertainty relations and their applications. Rev. Mod. Phys. 89, 015002 (2017)
Bialynicki-Birula, I., Rudnicki, Ł.: Entropic uncertainty relations in quantum physics. In: Statistical Complexity, pp. 1–34. Springer, Berlin (2011)
Wehner, Stephanie, Winter, Andreas: Entropic uncertainty relations—a survey. New J. Phys. 12(2), 025009 (2010)
Krawec, Walter O.: Quantum key distribution with mismatched measurements over arbitrary channels. Quantum Inf. Comput. 17(3 and 4), 209–241 (2017)
Beaudry, Normand J., Lucamarini, Marco, Mancini, Stefano, Renner, Renato: Security of two-way quantum key distribution. Phys. Rev. A 88(6), 062302 (2013)
Lucamarini, Marco, Mancini, Stefano: Quantum key distribution using a two-way quantum channel. Theor. Comput. Sci. 560, 46–61 (2014)
Krawec, W.O.: Semi-Quantum Key Distribution: Protocols, Security Analysis, and New Models. PhD thesis, Stevens Institute of Technology (2015)
Krawec, Walter O.: Security of a semi-quantum protocol where reflections contribute to the secret key. Quantum Inf. Process. 15(5), 2067–2090 (2016)
Barnett, Stephen M., Huttner, Bruno, Phoenix, Simon J.D.: Eavesdropping strategies and rejected-data protocols in quantum cryptography. J. Mod. Opt. 40(12), 2501–2513 (1993)
Watanabe, Shun, Matsumoto, Ryutaroh, Uyematsu, Tomohiko: Tomography increases key rates of quantum-key-distribution protocols. Phys. Rev. A 78(4), 042316 (2008)
Matsumoto, Ryutaroh, Watanabe, Shun: Key rate available from mismatched measurements in the bb84 protocol and the uncertainty principle. IEICE Trans. Fundam. Electron., Commun. Comput. Sci. 91(10), 2870–2873 (2008)
Matsumoto, Ryutaroh, Watanabe, Shun: Narrow basis angle doubles secret key in the bb84 protocol. J. Phys. A: Math. Theor. 43(14), 145302 (2010)
Tamaki, Kiyoshi, Curty, Marcos, Kato, Go, Lo, Hoi-Kwong, Azuma, Koji: Loss-tolerant quantum cryptography with imperfect sources. Phys. Rev. A 90(5), 052314 (2014)
Krawec, W.O.: Asymptotic analysis of a three state quantum cryptographic protocol. In: IEEE International Symposium on Information Theory, ISIT 2016, Barcelona, July 10–15, 2016, pp. 2489–2493 (2016)
Zhang, Wei, Qiu, Daowen, Mateus, Paulo: Security of a single-state semi-quantum key distribution protocol. Quantum Inf. Process. 17(6), 135 (2018)
Xian-Zhou, Zhang, Wei-Gui, Gong, Yong-Gang, Tan, Zhen-Zhong, Ren, Xiao-Tian, Guo: Quantum key distribution series network protocol with m-classical Bobs. Chin. Phys. B 18(6), 2143 (2009)
Zhu, Kong-Ni, Zhou, Nan-Run, Wang, Yun-Qian, Wen, Xiao-Jun: Semi-quantum key distribution protocols with GHZ states. Int. J. Theor. Phys. 57(12), 3621–3631 (2018)
Zhou, N.-R., Zhu, K.-N., Zou, X.-F.: Multi-party semi-quantum key distribution protocol with four-particle cluster states. Annalen der Physik 531, 1800520 (2019)
Raussendorf, Robert, Briegel, Hans J.: A one-way quantum computer. Phys. Rev. Lett. 86(22), 5188 (2001)
Krawec, Walter O.: Mediated semiquantum key distribution. Phys. Rev. A 91(3), 032323 (2015)
Krawec, Walter O.: An improved asymptotic key rate bound for a mediated semi-quantum key distribution protocol. Quantum Inf. Comput. 16(9 and 10), 813–834 (2016)
Krawec, W.O.: Multi-mediated semi-quantum key distribution. In: 2019 IEEE Globecom Workshops (GC Wkshps) (2019, to appear)
Liu, Zhi-Rou, Hwang, Tzonelih: Mediated semi-quantum key distribution without invoking quantum measurement. Annalen der Physik 530(4), 1700206 (2018)
Lin, P.-H., Tsai, C.-W., Hwang, T.: Mediated semi-quantum key distribution using single photons. Annalen der Physik 531, 1800347 (2019)
Massa, F., Yadav, P., Moqanaki, A., Krawec, W.O., Mateus, P., Paunković, N., Souto, A., Walther, P.: Experimental quantum cryptography with classical users. arXiv preprint arXiv:1908.01780 (2019)
Shamir, Adi: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Beimel, A.: Secret-sharing schemes: a survey. In: International Conference on Coding and Cryptology, pp. 11–46. Springer, Berlin (2011)
Hillery, Mark, Bužek, Vladimír, Berthiaume, André: Quantum secret sharing. Phys. Rev. A 59(3), 1829 (1999)
Karlsson, Anders, Koashi, Masato, Imoto, Nobuyuki: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59(1), 162 (1999)
Gottesman, Daniel: Theory of quantum secret sharing. Phys. Rev. A 61(4), 042311 (2000)
Li, Qin, Chan, Wai Hong, Long, Dong-Yang: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Lin, Jason, Yang, Chun-Wei, Tsai, Chia-Wei, Hwang, Tzonelih: Intercept-resend attacks on semi-quantum secret sharing and the improvements. Int. J. Theor. Phys. 52(1), 156–162 (2013)
Wang, Jian, Zhang, Sheng, Zhang, Quan, Tang, Chao-Jing: Semiquantum secret sharing using two-particle entangled state. In. J. Quantum Inf. 10(05), 1250050 (2012)
Li, Lvzhou, Qiu, Daowen, Mateus, Paulo: Quantum secret sharing with classical Bobs. J. Phys. A: Math. Theor. 46(4), 045304 (2013)
Xie, Chen, Li, Lvzhou, Qiu, Daowen: A novel semi-quantum secret sharing scheme of specific bits. Int. J. Theor. Phys. 54(10), 3819–3824 (2015)
Yin, Aihan, Fangbo, Fu: Eavesdropping on semi-quantum secret sharing scheme of specific bits. Int. J. Theor. Phys. 55(9), 4027–4035 (2016)
Gao, Xiang, Zhang, Shibin, Chang, Yan: Cryptanalysis and improvement of the semi-quantum secret sharing protocol. Int. J. Theor. Phys. 56(8), 2512–2520 (2017)
Xiang, Yi, Liu, Jun, Bai, Ming-qiang, Yang, Xue, Mo, Zhi-wen: Limited resource semi-quantum secret sharing based on multi-level systems. Int. J. Theor. Phys. 58(9), 2883–2892 (2019)
Ye, Chong-Qiang, Ye, Tian-Yu.: Circular semi-quantum secret sharing using single particles. Commun. Theor. Phys. 70(6), 661 (2018)
Li, Zhulin, Li, Qin, Liu, Chengdong, Peng, Yu., Chan, Wai Hong, Li, Lvzhou: Limited resource semiquantum secret sharing. Quantum Inf. Process. 17(10), 285 (2018)
Chong-Qiang, Y., Tian-Yu, Y., De, H., Zhi-Gang, G.: Multiparty semi-quantum secret sharing with d-level single-particle states. Int. J. Theor. Phys. 58, 1–18 (2019)
Tsai, Chia-Wei, Yang, Chun-Wei, Lee, Narn-Yih: Semi-quantum secret sharing protocol using w-state. Mod. Phys. Lett. A 34(27), 1950213 (2019)
Kun-Fei, Yu., Jun, Gu, Hwang, Tzonelih, Gope, Prosanta: Multi-party semi-quantum key distribution-convertible multi-party semi-quantum secret sharing. Quantum Inf. Process. 16(8), 194 (2017)
Yin, Aihan, Wang, Zefan, Fangbo, Fu: A novel semi-quantum secret sharing scheme based on Bell states. Mod. Phys. Lett. B 31(13), 1750150 (2017)
Gao, Gan, Wang, Yue, Wang, Dong: Cryptanalysis of a semi-quantum secret sharing scheme based on Bell states. Mod. Phys. Lett. B 32(09), 1850117 (2018)
Gao, Gan, Wang, Yue, Wang, Dong: Multiparty semiquantum secret sharing based on rearranging orders of qubits. Mod. Phys. Lett. B 30(10), 1650130 (2016)
Yin, Ai Han, Tong, Yan: A novel semi-quantum secret sharing scheme using entangled states. Mod. Phys. Lett. B 32(22), 1850256 (2018)
He, Qijian, Yang, Wei, Chen, Bingren, Huang, Liusheng: Cryptanalysis and improvement of the novel semi-quantum secret sharing scheme using entangled states. Mod. Phys. Lett. B 33(04), 1950045 (2019)
Cao, G., Chen, C., Jiang, M.: A scalable and flexible multi-user semi-quantum secret sharing. In: Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering, pp. 28–32. ACM (2018)
Nie, Yi-you, Li, Yuan-hua, Wang, Zi-sheng: Semi-quantum information splitting using GHZ-type states. Quantum Inf. Process. 12(1), 437–448 (2013)
Long, Gui-Lu, Liu, Xiao-Shu: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65(3), 032302 (2002)
Boström, Kim, Felbinger, Timo: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89(18), 187902 (2002)
Deng, Fu-Guo, Liu, Xiao-Shu: Two-step quantum direct communication protocol using the Einstein–Podolsky–Rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Long, G.: Quantum secure direct communication: principles, current status, perspectives. In: 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), pp. 1–5 (2017)
Deng, Fu-Guo, Long, Gui Lu: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69(5), 052319 (2004)
Zou, XiangFu, Qiu, DaoWen: Three-step semiquantum secure direct communication protocol. Sci. China Phys., Mech. Astron. 57(9), 1696–1702 (2014)
Jun, Gu, Lin, Po-hua, Hwang, Tzonelih: Double c-not attack and counterattack on ‘three-step semi-quantum secure direct communication protocol’. Quantum Inf. Process. 17(7), 182 (2018)
Xie, Chen, Li, Lvzhou, Situ, Haozhen, He, Jianhao: Semi-quantum secure direct communication scheme based on Bell states. Int. J. Theor. Phys. 57(6), 1881–1887 (2018)
Zhang, Ming-Hui, Li, Hui-Fang, Xia, Zhao-Qiang, Feng, Xiao-Yi, Peng, Jin-Ye: Semiquantum secure direct communication using EPR pairs. Quantum Inf. Process. 16(5), 117 (2017)
Yan, LiLi, Sun, YuHua, Chang, Yan, Zhang, ShiBin, Wan, GuoGen, Sheng, ZhiWei: Semi-quantum protocol for deterministic secure quantum communication using Bell states. Quantum Inf. Process. 17(11), 315 (2018)
Sun, Yuhua, Yan, Lili, Chang, Yan, Zhang, Shibin, Shao, Tingting, Zhang, Yan: Two semi-quantum secure direct communication protocols based on bell states. Mod. Phys. Lett. A 34(01), 1950004 (2019)
Luo, Yi-Ping, Hwang, Tzonelih: Authenticated semi-quantum direct communication protocols using Bell states. Quantum Inf. Process. 15(2), 947–958 (2016)
Almousa, S., Barbeau, M.: Delay and reflection attacks in authenticated semi-quantum direct communications. In: 2016 IEEE Globecom Workshops (GC Wkshps), pp. 1–7. IEEE (2016)
Lu, H., Barbeau, M., Nayak, A.: Economic no-key semi-quantum direct communication protocol. In: 2017 IEEE Globecom Workshops (GC Wkshps), pp. 1–7. IEEE (2017)
Haoye, Lu, Barbeau, Michel, Nayak, Amiya: Keyless semi-quantum point-to-point communication protocol with low resource requirements. Sci. Rep. 9(1), 64 (2019)
Wang, M.-M., Liu, J.-L., Gong, L.-M.: Semiquantum secure direct communication with authentication based on single-photons. Int. J. Quantum Inf. 17, 1950024 (2019)
Tao, Z., Chang, Y., Zhang, S., Dai, J., Li, X.: Two semi-quantum direct communication protocols with mutual authentication based on Bell states. Int. J. Theor. Phys. 58, 1–8 (2019)
Zhang, Z.-J., Man, Z.-X.: Secure direct bidirectional communication protocol using the Einstein–Podolsky–Rosen pair block. arXiv preprint arXiv:quant-ph/0403215 (2004)
Nguyen, Ba An: Quantum dialogue. Phys. Lett. A 328(1), 6–10 (2004)
Shukla, Chitra, Thapliyal, Kishore, Pathak, Anirban: Semi-quantum communication: protocols for key agreement, controlled secure direct communication and dialogue. Quantum Inf. Process. 16(12), 295 (2017)
Ye, Tian-Yu., Ye, Chong-Qiang: Semi-quantum dialogue based on single photons. Int. J. Theor. Phys. 57(5), 1440–1454 (2018)
Liu, Lin, Xiao, Min, Song, Xiuli: Authenticated semiquantum dialogue with secure delegated quantum computation over a collective noise channel. Quantum Inf. Process. 17(12), 342 (2018)
Zhou, Nanrun, Zeng, Guihua, Xiong, Jin: Quantum key agreement protocol. Electron. Lett. 40(18), 1149–1150 (2004)
Chong, Song-Kong, Hwang, Tzonelih: Quantum key agreement protocol based on bb84. Opt. Commun. 283(6), 1192–1195 (2010)
Shukla, Chitra, Alam, Nasir, Pathak, Anirban: Protocols of quantum key agreement solely using bell states and Bell measurement. Quantum Inf. Process. 13(11), 2391–2405 (2014)
Liu, Wen-Jie, Chen, Zhen-Yu., Ji, Sai, Wang, Hai-Bin, Zhang, Jun: Multi-party semi-quantum key agreement with delegating quantum computation. Int. J. Theor. Phys. 56(10), 3164–3174 (2017)
Yan, L.-L., Zhang, S.-B., Chang, Y., Sheng, Z.-W., Yang, F.: Mutual semi-quantum key agreement protocol using Bell states. Mod. Phys. Lett. A 34, 1950294 (2019)
Yan, L., Zhang, S., Chang, Y., Sheng, Z., Sun, Y.: Semi-quantum key agreement and private comparison protocols using Bell states. Int. J. Theor. Phys. 58, 1–11 (2019)
Yao, A.C.: Protocols for secure computations. In: 23rd Annual Symposium on Foundations of Computer Science (sfcs 1982), pp. 160–164. IEEE (1982)
Lindell, Y.: Secure multiparty computation for privacy preserving data mining. In: Encyclopedia of Data Warehousing and Mining, pp. 1005–1009. IGI Global (2005)
Chen, Xiu-Bo, Gang, Xu, Niu, Xin-Xin, Wen, Qiao-Yan, Yang, Yi-Xian: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283(7), 1561–1565 (2010)
Liu, Wen, Wang, Yong-Bin, Jiang, Zheng-Tao: An efficient protocol for the quantum private comparison of equality with w state. Opt. Commun. 284(12), 3160–3163 (2011)
Liu, Wen, Wang, Yong-Bin, Jiang, Zheng-Tao, Cao, Yi-Zhen: A protocol for the quantum private comparison of equality with \(\chi \)-type state. Int. J. Theor. Phys. 51(1), 69–77 (2012)
Liu, Wenjie, Liu, Chao, Wang, Haibin, Jia, Tingting: Quantum private comparison: a review. IETE Tech. Rev. 30(5), 439–445 (2013)
Lo, Hoi-Kwong: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154 (1997)
Thapliyal, Kishore, Sharma, Rishi Dutt, Pathak, Anirban: Orthogonal-state-based and semi-quantum protocols for quantum private comparison in noisy environment. Int. J. Quantum Inf. 16(05), 1850047 (2018)
Chou, W.-H., Hwang, T., Gu, J.: Semi-quantum private comparison protocol under an almost-dishonest third party. arXiv preprint arXiv:1607.07961 (2016)
Yan-Feng, Lang: Semi-quantum private comparison using single photons. Int. J. Theor. Phys. 57(10), 3048–3055 (2018)
Lin, Po-Hua, Hwang, Tzonelih, Tsai, Chia-Wei: Efficient semi-quantum private comparison using single photons. Quantum Inf. Process. 18(7), 207 (2019)
Ye, Tian-Yu., Ye, Chong-Qiang: Measure-resend semi-quantum private comparison without entanglement. Int. J. Theor. Phys. 57(12), 3819–3834 (2018)
Wen, Xiao-Jun, Zhao, Xing-Qiang, Gong, Li-Hua, Zhou, Nan-Run: A semi-quantum authentication protocol for message and identity. Laser Phys. Lett. 16(7), 075206 (2019)
Zhou, Nan-Run, Zhu, Kong-Ni, Bi, Wei, Gong, Li-Hua: Semi-quantum identification. Quantum Inf. Process. 18(6), 197 (2019)
Xiao, Min, Zhang, Di-Fang: Practical quantum private query with classical participants. Chin. Phys. Lett. 36(3), 030301 (2019)
He, Jinjun, Li, Qin, Wu, Chunhui, Chan, Wai Hong, Zhang, Shengyu: Measurement-device-independent semiquantum key distribution. Int. J. Quantum Inf. 16(02), 1850012 (2018)
Yang, Yu-Guang, Yang, Rui, Lei, He, Shi, Wei-Min, Zhou, Yi-Hua: Quantum oblivious transfer with relaxed constraints on the receiver. Quantum Inf. Process. 14(8), 3031–3040 (2015)
Zhao, X.-Q., Chen, H.-Y., Wang, Y.-Q., Zhou, N.-R.: Semi-quantum bi-signature scheme based on w states. Int. J. Theor. Phys. 58, 1–13 (2019)
Damgård, Ivan B., Fehr, Serge, Salvail, Louis, Schaffner, Christian: Cryptography in the bounded-quantum-storage model. SIAM J. Comput. 37(6), 1865–1890 (2008)
Damgård, I.B., Fehr, S., Salvail, L., Schaffner, C.: Secure identification and qkd in the bounded-quantum-storage model. In: Annual International Cryptology Conference, pp. 342–359. Springer, Berlin (2007)
Wehner, Stephanie, Schaffner, Christian, Terhal, Barbara M.: Cryptography from noisy storage. Phys. Rev. Lett. 100(22), 220502 (2008)
Konig, Robert, Wehner, Stephanie, Wullschleger, Jürg: Unconditional security from noisy quantum storage. IEEE Trans. Inf. Theory 58(3), 1962–1984 (2012)
Tan, Yong-gang, Hua, Lu, Cai, Qing-yu: Comment on “quantum key distribution with classical Bob”. Phys. Rev. Lett. 102(9), 098901 (2009)
Boyer, Michel, Kenigsberg, Dan, Mor, Tal: Boyer, Kenigsberg, and Mor reply. Phys. Rev. Lett. 102(9), 098902 (2009)
Yang, Yu-Guang, Sun, Si-Jia, Zhao, Qian-Qian: Trojan–Horse attacks on quantum key distribution with classical Bob. Quantum Inf. Process. 14(2), 681–686 (2015)
Pirandola, Stefano, Mancini, Stefano, Lloyd, Seth, Braunstein, Samuel L.: Continuous-variable quantum cryptography using two-way quantum communication. Nat. Phys. 4(9), 726 (2008)
Ottaviani, Carlo, Pirandola, Stefano: General immunity and superadditivity of two-way gaussian quantum cryptography. Sci. Rep. 6, 22225 (2016)
Weedbrook, Christian, Ottaviani, Carlo, Pirandola, Stefano: Two-way quantum cryptography at different wavelengths. Phys. Rev. A 89(1), 012309 (2014)
Ottaviani, Carlo, Mancini, Stefano, Pirandola, Stefano: Two-way gaussian quantum cryptography against coherent attacks in direct reconciliation. Phys. Rev. A 92(6), 062323 (2015)
Zhuang, Quntao, Zhang, Zheshen, Lütkenhaus, Norbert, Shapiro, Jeffrey H.: Security-proof framework for two-way Gaussian quantum-key-distribution protocols. Phys. Rev. A 98(3), 032332 (2018)
Ghorai, Shouvik, Diamanti, Eleni, Leverrier, Anthony: Composable security of two-way continuous-variable quantum key distribution without active symmetrization. Phys. Rev. A 99(1), 012311 (2019)
Zhuang, Quntao, Zhang, Zheshen, Dove, Justin, Wong, Franco N.C., Shapiro, Jeffrey H.: Floodlight quantum key distribution: a practical route to gigabit-per-second secret-key rates. Phys. Rev. A 94, 012322 (2016)
Boyer, Michel, Katz, Matty, Liss, Rotem, Mor, Tal: Experimentally feasible protocol for semiquantum key distribution. Phys. Rev. A 96(6), 062335 (2017)
Krawec, W.O.: Practical security of semi-quantum key distribution. In: Quantum Information Science, Sensing, and Computation X, vol. 10660, p. 1066009. International Society for Optics and Photonics (2018)
Gurevich, P.: Experimental Quantum Key Distribution with Classical Alice. Technion-Israel Institute of Technology, Faculty of Computer Science (2012)
Boyer, Michel, Liss, Rotem, Mor, Tal: Attacks against a simplified experimentally feasible semiquantum key distribution protocol. Entropy 20(7), 536 (2018)
Tamaki, Kiyoshi, Koashi, Masato, Imoto, Nobuyuki: Security of the Bennett 1992 quantum-key distribution protocol against individual attack over a realistic channel. Phys. Rev. A 67(3), 032310 (2003)
Temporao, G.P.: Passive switching scheme for two-way quantum key distribution setups. Electron. Lett. 46(7), 512–513 (2010)
Funding
Funding was provided by the National Science Foundation, Directorate for Computer and Information Science and Engineering (Grant No. 1812070).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Iqbal, H., Krawec, W.O. Semi-quantum cryptography. Quantum Inf Process 19, 97 (2020). https://doi.org/10.1007/s11128-020-2595-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-2595-9