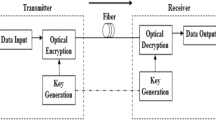
Abstract
The ever increasing growth of users and network capacity makes the security of passive optical networks (PON) an issue of great concern. In this paper, we present a novel work to enhance the physical layer security for wavelength division multiplexing orthogonal frequency division multiplexing PON. Elliptic curve with Diffie–Helman key exchange protocol is employed to derive a session key for Advanced Encryption Standard algorithm at optical line terminal and optical network units to provide secure communication. Encryption is applied on partial data of I/Q channel in order to reduce the computational time. Successful transmission of 16-Quadrature Amplitude Modulation encrypted OFDM signals at a distance of 100 km is demonstrated within the limits of peak to average power ratio value.










Similar content being viewed by others
References
Kani, J., Bourgart, F., Cui, A., Rafel, A., Rodrigues, S.: Next generation PON-part I: technology roadmap and general requirements. IEEE Commun. Mag. 47(11), 43–49 (2009)
Cvijetic, N.: OFDM for next-generation optical access networks. J. Lightwave Technol. 30(4), 384–398 (2012)
Effenberger, F., Mukai, H., Park, S., Pfeiffer, T.: Next-generation PON-part II: candidate systems for next-generation PON. IEEE Commun. Mag. 47(11), 50–57 (2009)
Zhang, J., Ansari, N.: On the capacity of WDM passive optical networks. IEEE Trans. Commun. 59(2), 552–559 (2011)
Chang, G., Chowdhury, A., Jia, Z., Chien, H., Huang, M., Yu, J., Ellinas, G.: Key technologies of WDM-PON for future converged optical broadband access networks. J. Opt. Commun. Netw. 1(4), C35–C50 (2009)
Lam, C.F.: Passive Optical Networks—Principles and Practice. Elsevier-Academic Press (2007)
Kanonakis, K., Tomkos, I., Pfeiffer, T., Prat, J., Kourtessis, P.: ACCORDANCE: a novel OFDMA-PON paradigm for ultra-high capacity converged wireline–wireless access networks. In: 12th IEEE-International Conference on Transparent Optical Networks, Munich, Germany, July 2010
Yu, J., Huang, M., Qian, D., Chen, L., Chang, G.: Centralized lightwave WDM-PON employing 16-QAM intensity modulated OFDM downstream and OOK modulated upstream signals. IEEE Photonics Technol. Lett. 20(18), 1545–1547 (2008)
Cvijetic, N., Cvijetic, M., Huang, M., Ip, E., Huang, Y., Wang, T.: Terabit optical access networks based on WDM-OFDMA-PON. J. Lightw. Technol. 30(4), 493–503 (2012)
Liu, B., Xin, X., Zhang, L., Yu, J., Zhang, Q., Yu, C.: A WDM-OFDM-PON architecture with centralized lightwave and PolSK-modulated multicast overlay. Opt. Express 18(3), 2137–2143 (2010)
Kartalopoulos, S.: Discriminating between faults and attacks in secure optical networks. In: IEEE Proceeding of Military Communications Conference, Orlando, FL, USA, Oct 2007
Kartalopoulos, S.: A primer on cryptography in communication. IEEE Commun. Mag. 44(4), 146–151 (2006)
Smart, Nigel P.: Cryptography Made Simple. Springer (2016)
Jiang, N., Zhang, C., Qiu, K.: Secure passive optical network based on chaos synchronization. Opt. Lett. 37(21), 4501–4503 (2012)
Kartalopoulos, S.: Optical network security: sensing eavesdropper intervention. In: IEEE Proceeding of Global Telecommunications Conference, San Francisco, CA, Nov 2006
Fok, M., Wang, Z., Deng, Y., Prucnal, P.: Optical layer security in fiber-optic networks. IEEE Trans. Inf. Forensics Secur. 6(3), 725–736 (2011)
Deng, L., Cheng, M., Wang, X., Li, H., Tanga, M., Fu, S.: Secure OFDM-PON system based on chaos and fractional Fourier transform techniques. J. Lightw. Technol. 32(15), 2629–2635 (2014)
Yang, X., Hu, X., Shen, Z., He, H., Hu, W., Bai, C.: Chaotic signal scrambling for physical layer security in OFDM-PON. In: 17th International Conference on Transparent Optical Networks (ICTON), Budapest, July 2015
Hu, X., Yang, X., Shen, Z., He, H., Hu, W.: Chaos-based partial transmit sequence technique for physical layer security in OFDM-PON. IEEE Photonics Technol. Lett. 27(23), 2429–2432 (2015)
Xu, M.: Cryptanalysis of an image encryption algorithm based on DNA sequence operation and hyper-chaotic system. 3D Res. 8, 15 (2017)
Caragata, D., Tabia, K., Luduena, M.: Cryptanalysis of a chaos-based encryption algorithm for distributed systems. In: 8th International Conference for Internet Technology and Secured Transactions, London, UK, Dec 2013
Akhavan, A., Samsudin, A., Akhshani, A.: Cryptanalysis of an improvement over an image encryption method based on total shuffling. Opt. Commun. 350, 77–82 (2015)
Xie, E.Y., Li, C., Yu, S., Lü, J.: On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process. 132, 150–154 (2017)
Diamanti, E., Lo, H.-K., Qi, B., Yuan, Z.: Practical challenges in quantum key distribution. npj Quantum Information. Article No. 16025 (2016)
Gill, H.S., Bhatia, K.S., Gill, S.S.: Analysis of secured optical orthogonal frequency division multiplexed system. J. Opt. Commun. 2191–6322 (2016)
Padmavathy, R., Bhagvati, C.: Discrete logarithm problem using index calculus method. Math. Comput. Model. 55(1–2), 161–169 (2012)
Weinstein, S., Luo, Y., Wang, T.: The COMSOC Guide to Passive Optical Networks—Enhancing the Last Mile Access. Wiley, New York (2012). ISBN: 978-0-470-16884-4
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gill, H.S., Gill, S.S. & Bhatia, K.S. A novel approach for physical layer security in future-generation passive optical networks. Photon Netw Commun 35, 141–150 (2018). https://doi.org/10.1007/s11107-017-0738-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11107-017-0738-4