Abstract
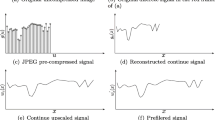
Resampling forgery generally refers to as the technique that utilizes interpolation algorithm to maliciously geometrically transform a digital image or a portion of an image. This paper investigates the problem of image resampling detection based on the linear parametric model. First, we expose the periodic artifact of one-dimensional 1-D) resampled signal. After dealing with the nuisance parameters, together with Bayes’ rule, the detector is designed based on the probability of residual noise extracted from resampled signal using linear parametric model. Subsequently, we mainly study the characteristic of a resampled image. Meanwhile, it is proposed to estimate the probability of pixels’ noise and establish a practical Likelihood Ratio Test (LRT). Comparison with the state-of-the-art tests, numerical experiments show the relevance of our proposed algorithm with detecting uncompressed/compressed resampled images.










Similar content being viewed by others
Notes
In fact, it is very difficult to assume the accurate distribution model of the original signal without any prior information. In this context, we arbitrarily assume the original signal approximately follows the Uniform distribution in the designed test, which is the limitation of our proposed algorithm.
In fact, it is very difficult to accurately define the distribution of the residual noise from a non-resampled image. Here, it is proposed to arbitrarily approximate its distribution using the Uniform distribution inspired by the reference [21].
The term post-camera is referred to as the operation after acquiring a digital image.
The fixed pattern can be described as α j = (0.5, 0.5, 0.5, 0.5, -0.25, -0.25, -0.25, -0.25) T, where α j denotes the weighted factors (see (15)).
References
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Serra G (2011) A sift-based forensic method for copy–move attack detection and transformation recovery. IEEE Trans Inf Forensics Secur 6(3):1099–1110
Bas P, Filler T, Pevný T. (2011) Break our steganographic system — the ins and outs of organizing boss. In: Filler T (ed) 13th International Workshop on Information Hiding
Chen M, Fridrich J, Goljan M, Lukás J (2008) Determining image origin and integrity using sensor noise. IEEE Trans Inf Forensics Secur 3(1):74–90
Christlein V, Riess C, Jordan J, Angelopoulou E (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans Inf Forensics Secur 7 (6):1841–1854
Cogranne R, Zitzmann C, Fillatre L, Retraint F, Nikiforov I, Cornu P (2011) A cover image model for reliable steganalysis. In: Information Hiding, pp 178–192. Springer
Dempster A P, Laird N M, Rubin D B et al (1977) Maximum likelihood from incomplete data via the em algorithm. J R Stat Soc 39(1):1–38
Farid H (2009) Exposing digital forgeries from jpeg ghosts. IEEE Trans Inf Forensics Secur 4(1):154–160
Farid H (2009) Image forgery detection. IEEE Signal Proc Mag 26(2):16–25
Feng X, Cox I J, Doërr G (2011) An energy-based method for the forensic detection of re-sampled images. In: 2011 IEEE International Conference on Multimedia and Expo (ICME), pp 1–6. IEEE
Feng X, Cox I J, Doerr G (2012) Normalized energy density-based forensic detection of resampled images. IEEE Trans Multimedia 14(3):536–545
Fridrich A J, Soukal B D, Lukáš A J (2003) Detection of copy-move forgery in digital images. In: Proceedings of Digital Forensic Research Workshop. Citeseer
Gallagher A, Chen T (2008) Image authentication by detecting traces of demosaicing. In: IEEE Computer Society Conference on Computer Vision and Pattern Recognition Workshops, 2008. CVPRW’08, pp 1–8. IEEE
Gallagher A C (2005) Detection of linear and cubic interpolation in jpeg compressed images. In: The 2nd Canadian Conference on Computer and Robot Vision, 2005. Proceedings, pp 65–72. IEEE
Kirchner M (2008) Fast and reliable resampling detection by spectral analysis of fixed linear predictor residue. In: Proceedings of the 10th ACM workshop on Multimedia and security, pp 11–20. ACM
Kirchner M (2010) Linear row and column predictors for the analysis of resized images. In: Proceedings of the 12th ACM workshop on Multimedia and security, pp 13–18. ACM
Lehman E R J (2005) Testing statistical hypotheses, 2nd Edn. Springer
Li J, Li X, Yang B, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inf Forensics Secur 10(3):507–518
Lukáš J, Fridrich J, Goljan M (2006) Detecting digital image forgeries using sensor pattern noise Electronic Imaging 2006, pp 60,720Y–60,720Y. International Society for Optics and Photonics
Mahdian B, Saic S (2008) Blind authentication using periodic properties of interpolation. IEEE Trans Inf Forensics Secur 3(3):529–538
Oppenheim A V, Schafer R W, Buck J R, et al. (1989) Discrete-time signal processing, vol 2. Prentice-hall, Englewood Cliffs
Popescu A C, Farid H (2005) Exposing digital forgeries by detecting traces of resampling. IEEE Trans Signal Process 53(2):758–767
Qiao T, Retraint F, Cogranne R (2013) Image authentication by statistical analysis. In: Signal Processing Conference (EUSIPCO), 2013 Proceedings of the 21th European, pp 1–5. IEEE, EURASIP
Qiao T, Retraint F, Cogranne R, Thai T H (2015) Source camera device identification based on raw images. In: 2015 IEEE International Conference on Image Processing (ICIP), pp 3812–3816. IEEE
Qiao T, Retraint F, Cogranne R, Zitzmann C (2015) Steganalysis of jsteg algorithm using hypothesis testing theory. EURASIP J Inf Secur 2015(1):1–16
Qiao T, Ziitmann C, Cogranne R, Retraint F (2014) Detection of jsteg algorithm using hypothesis testing theory and a statistical model with nuisance parameters. In: Proceedings of the 2nd ACM workshop on Information hiding and multimedia security, pp 3–13. ACM
Qiao T, Zitzmann C, Retraint F, Cogranne R (2014) Statistical detection of jsteg steganography using hypothesis testing theory. In: 2014 IEEE International Conference on Image Processing (ICIP), pp 5517–5521. IEEE
Qin C, Chang C C, Chen P Y (2012) Self-embedding fragile watermarking with restoration capability based on adaptive bit allocation mechanism. Signal Process 92(4):1137–1150
Qin C, Chen X, Ye D, Wang J, Sun X (2016) A novel image hashing scheme with perceptual robustness using block truncation coding. Inf Sci 361:84–99
Ryu S J, Lee H K (2014) Estimation of linear transformation by analyzing the periodicity of interpolation. Pattern Recogn Lett 36:89–99
Schaefer G, Stich M (2003) Ucid: an uncompressed color image database. In: Electronic Imaging 2004, pp 472–480. International Society for Optics and Photonics
Sencar H T, Memon N (2012) Digital image forensics: There is more to a picture than meets the eye. Springer
Stamm M C, Wu M, Liu K (2013) Information forensics: An overview of the first decade. IEEE Access 1(1):167–200
Thai T H, Cogranne R, Retraint F (2014) Camera model identification based on the heteroscedastic noise model. IEEE Trans Image Process 23(1):250–263
Wei W, Wang S, Zhang X, Tang Z (2010) Estimation of image rotation angle using interpolation-related spectral signatures with application to blind detection of image forgery. IEEE Trans Inf Forensics Secur 5(3):507–517
Xia Z, Wang X, Sun X, Liu Q, Xiong N (2016) Steganalysis of lsb matching using differences between nonadjacent pixels. Multimedia Tools and Applications 75 (4):1947–1962
Zitzmann C, Cogranne R, Retraint F, Nikiforov I, Fillatre L, Cornu P (2011) Statistical decision methods in hidden information detection. In: Information Hiding, pp 163–177. Springer
Acknowledgments
This work is funded by the State Key Program of Zhejiang Province Natural Science Foundation of China under Grant No. LZ15F020003 and the Natural Science Foundation of China (No. 61602295) and the Natural Science Foundation of Shanghai (No. 16ZR1413100). The Ph.D thesis of Tong Qiao is funded by the China Scholar Council (CSC) and the region Champagne-Ardenne, IDENT project.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Qiao, T., Zhu, A. & Retraint, F. Exposing image resampling forgery by using linear parametric model. Multimed Tools Appl 77, 1501–1523 (2018). https://doi.org/10.1007/s11042-016-4314-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-4314-1