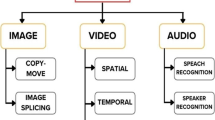
Abstract
Digital audio forensics is used for a variety of applications ranging from authenticating audio files to link an audio recording to the acquisition device (e.g., microphone), and also linking to the acoustic environment in which the audio recording was made, and identifying traces of coding or transcoding. This survey paper provides an overview of the current state-of-the-art (SOA) in digital audio forensics and highlights some open research problems and future challenges in this active area of research. The paper categorizes the audio file analysis into container and content-based analysis in order to detect the authenticity of the file. Existing SOA, in audio forensics, is discussed based on both container and content-based analysis. The importance of this research topic has encouraged many researchers to contribute in this area; yet, further scopes are available to help researchers and readers expand the body of knowledge. The ultimate goal of this paper is to introduce all information on audio forensics and encourage researchers to solve the unanswered questions. Our survey paper would contribute to this critical research area, which has addressed many serious cases in the past, and help solve many more cases in the future by using advanced techniques with more accurate results.























Similar content being viewed by others
References
Alexander A, Forth O, Tunstall D (2012) Music and noise fingerprinting and reference cancellation applied to forensic audio enhancement. In: Audio engineering society conference: 46th international conference: audio forensics
Balasubramaniyan VA, Poonawalla A, Ahamad M, Hunter MT, Traynor P (2010) PinDr0p: using single-ended audio features to determine call provenance. In Proceedings of the 17th ACM conference on computer and communications security, pp 109–120
Bang KH, Park Y-C, Youn D-H (2006) A dual audio transcoding algorithm for digital multimedia broadcasting services. In: Audio Engineering Society Convention 120
Bianchi T, Rosa AD, Fontani M, Rocciolo G, Piva A (2014) Detection and localization of double compression in MP3 audio tracks. EURASIP J Inf Secur 2014:10
Boll S (1979) Suppression of acoustic noise in speech using spectral subtraction. Acoustics, Speech and Signal Processing, IEEE Transactions on 27:113–120
Brixen EB (2007) Techniques for the authentication of digital audio recordings. In: Audio Engineering Society Convention 122
Buchholz R, Kraetzer C, Dittmann J (2009) Microphone classification using Fourier coefficients. In: Information hiding, pp 235–246
Chaudhary UA, Malik H (2010) Automatic recording environment identification using acoustic features. In: Audio Engineering Society Convention 129
Chen N, Xiao H-D, Wan W (2011) Audio hash function based on non-negative matrix factorisation of mel-frequency cepstral coefficients. Information Security, IET 5:19–25
Cuccovillo L, Mann S, Tagliasacchi M, Aichroth P (2013) Audio tampering detection via microphone classification. In: Multimedia Signal Processing (MMSP), 2013 I.E. 15th International Workshop on, pp 177–182
D’Alessandro B, Shi YQ (2009) MP3 bit rate quality detection through frequency spectrum analysis. In: Proceedings of the 11th ACM workshop on multimedia and security, pp 57–62
Ding H, Havelock DI (2010) Drift-compensated adaptive filtering for improving speech intelligibility in cases with asynchronous inputs. EURASIP J Adv Signal Process 2010:12
Garcia-Romero D, Espy-Wilson CY (2010) Automatic acquisition device identification from speech recordings. In: Acoustics Speech and Signal Processing (ICASSP), 2010 I.E. International Conference on, pp 1806–1809
Gerazov B, Kokolanski Z, Arsov G, Dimcev V (2012) Tracking of electrical network frequency for the purpose of forensic audio authentication. In: Optimization of Electrical and Electronic Equipment (OPTIM), 2012 13th International Conference on, 2012, pp 1164–1169
Grigoras C (2007) Applications of ENF criterion in forensic audio, video, computer and telecommunication analysis. Forensic Sci Int 167:136–145
Grigoras C (2009) Applications of ENF analysis in forensic authentication of digital audio and video recordings. J Audio Eng Soc 57:643–661
Grigoras C (2010) Statistical tools for multimedia forensics. In: Audio engineering society conference: 39th international conference: audio forensics: practices and challenges
Gupta S, Cho S, Kuo C-C (2012) Current developments and future trends in audio authentication. MultiMedia, IEEE 19:50–59
Hatje U, Musialik CM (2005) Frequency-domain processors for efficient removal of noise and unwanted audio events. In: Audio Engineering Society Conference: 26th International Conference: Audio Forensics in the Digital Age
Hermansky H (1990) Perceptual linear predictive (PLP) analysis of speech. The Journal of the Acoustical Society of America 87:1738–1752
Hicsonmez S, Sencar HT, Avcibas I (2011) Audio codec identification through payload sampling. In: Information Forensics and Security (WIFS), 2011 I.E. international workshop on, pp 1–6
Ikram S, Malik H (2010) Digital audio forensics using background noise. In: Multimedia and Expo (ICME), 2010 I.E. International Conference on, pp 106–110
Jenner F, Kwasinski A (2012) Highly accurate non-intrusive speech forensics for codec identifications from observed decoded signals. In: Acoustics, Speech and Signal Processing (ICASSP), 2012 I.E. international conference on, pp 1737–1740
Ju F-S, Fang C-M (2006) Time-frequency domain fast audio transcoding. In: Multimedia, 2006. ISM’06. Eighth IEEE international symposium on, pp 750–753
Koenig BE (1990) Authentication of forensic audio recordings. J Audio Eng Soc 38:3–33
Koenig BE, Lacey DS (2009) Forensic authentication of digital audio recordings. J Audio Eng Soc 57:662–695
Koenig BE, Lacey DS (2012) Forensic authenticity analyses of the header data in re-encoded WMA files from small Olympus audio recorders. J Audio Eng Soc 60:255–265
Koenig BE, Lacey DS, Killion SA (2007) Forensic enhancement of digital audio recordings. J Audio Eng Soc 55:352–371
Korycki R (2014a) Authenticity examination of compressed audio recordings using detection of multiple compression and encoders’ identification. Forensic Sci Int 238:33–46
Korycki R (2014b) Detection of montage in lossy compressed digital audio recordings. Archives of Acoustics 39:65–72
Kraetzer C, Oermann A, Dittmann J, Lang A (2007) Digital audio forensics: a first practical evaluation on microphone and environment classification. In: Proceedings of the 9th workshop on Multimedia & security, pp 63–74
C. Kraetzer, K. Qian, M. Schott, and J. Dittmann (2011) A context model for microphone forensics and its application in evaluations. In: IS&T/SPIE Electronic Imaging, pp 78800P–78800P-15
Kurniawan F, Rahim MSM, Khalil MS, Khan MK (2016) Statistical-based audio forensic on identical microphones. International Journal of Electrical and Computer Engineering (IJECE) 6:2211–2218
Lim JS, Oppenheim AV (1979) Enhancement and bandwidth compression of noisy speech. Proc IEEE 67:1586–1604
Liu Q, Sung AH, Qiao M (2010) Detection of double MP3 compression. Cogn Comput 2:291–296
Luo D, Yang R, Huang J (2015) Identification of AMR decompressed audio. Digital Signal Processing 37:85–91
Lv Z, Hu Y, Li C-T, Liu B-B (2013) Audio forensic authentication based on MOCC between ENF and reference signals. In: Signal and Information Processing (ChinaSIP), 2013 I.E. China Summit & International Conference on, pp 427–431
Maher R (2009) Audio forensic examination. Signal Processing Magazine, IEEE 26:84–94
Maher RC (2010) Overview of audio forensics. In: Intelligent multimedia analysis for security applications. Springer, vol. 282, pp. 127–144
Malik H (2013) Acoustic environment identification and its applications to audio forensics. Information Forensics and Security, IEEE Transactions on 8:1827–1837
Malik H, Farid H (2010) Audio forensics from acoustic reverberation. In: Acoustics Speech and Signal Processing (ICASSP), 2010 I.E. International Conference on, pp 1710–1713
Malik H, Zhao H (2012) Recording environment identification using acoustic reverberation. In: Acoustics, Speech and Signal Processing (ICASSP), 2012 I.E. International Conference on, pp 1833–1836
Mansour MF (2009) Strategies for bit allocation reuse in audio transcoding. In: ICASSP, pp 157–160
Mansour MF (2012) A transcoding system for audio standards. IEEE transactions on multimedia 14:1381–1389
McAulay R, Malpass M (1980) Speech enhancement using a soft-decision noise suppression filter. Acoustics, Speech and Signal Processing, IEEE Transactions on 28:137–145
Moon C-B, Kim H, Kim BM (2014) Audio recorder identification using reduced noise features. In: Ubiquitous information technologies and applications, Springer, pp 35–42
Muhammad G, Alotaibi YA, Alsulaiman M, Huda MN (2010) Environment recognition using selected MPEG-7 audio features and Mel-Frequency Cepstral Coefficients. In: Digital Telecommunications (ICDT), 2010 Fifth International Conference on, pp 11–16
Nikias CL (1993) Higher-order spectral analysis. In: Engineering in Medicine and Biology Society, 1993. Proceedings of the 15th Annual International Conference of the IEEE. pp 319–319
Olanrewaju R, Khalifa O (2012) Digital audio watermarking; techniques and applications, In: Computer and Communication Engineering (ICCCE), 2012 International Conference on,pp 830–835
Owen T (1996) AES recommended practice for forensic purposes-managing recorded audio materials intended for examination. J Audio Eng Soc 44(4):275
Paliwal K, Wójcicki K, Schwerin B (2010) Single-channel speech enhancement using spectral subtraction in the short-time modulation domain. Speech Comm 52:450–475
Qiao M, Sung AH, Liu Q (2010) Revealing real quality of double compressed MP3 audio. In: Proceedings of the international conference on multimedia, pp 1011–1014
Qiao M, Sung AH, Liu Q (2013) Improved detection of MP3 double compression using content-independent features. In: Signal Processing, Communication and Computing (ICSPCC), 2013 I.E. international conference on, pp 1–4
Rabiner LR, Schafer RW (1978) Digital processing of speech signals, vol 100. Prentice-hall, Englewood Cliffs
Ratnam R, Jones DL, Wheeler BC, O’Brien WD Jr, Lansing CR, Feng AS (2003) Blind estimation of reverberation time. The Journal of the Acoustical Society of America 114:2877–2892
Rodríguez DPN, Apolinário JA, Biscainho LWP (2010) Audio authenticity: detecting ENF discontinuity with high precision phase analysis. Information Forensics and Security, IEEE Transactions on 5:534–543
Shanmugasundaram K, Kharrazi M, Memon N (2004) Nabs: a system for detecting resource abuses via characterization of flow content type. In: Computer security applications conference, 2004. 20th Annual, pp 316–325
Sharma D, Naylor PA, Gaubitch ND, Brookes M (2012) Non intrusive codec identification algorithm. In: Acoustics, Speech and Signal Processing (ICASSP), 2012 I.E. international conference on, pp 4477–4480
Soulodre GA (2010) About this dereverberation business: A method for extracting reverberation from audio signals. In: Audio Engineering Society Convention 129
Takagi K, Miyaji S, Sakazawa S, Takishima Y (2006) Conversion of MP3 to AAC in the compressed domain. In: Multimedia Signal Processing, 2006 I.E. 8th Workshop on, pp 132–135
Tsoukalas DE, Mourjopoulos JN, Kokkinakis G (1997) Speech enhancement based on audible noise suppression. Speech and Audio Processing, IEEE Transactions on 5:497–514
Weiss M, Aschkenasy E, Parsons T (1975) Study and development of the INTEL technique for improving speech intelligibility. DTIC Document
Yang R, Qu Z, Huang J (2008) Detecting digital audio forgeries by checking frame offsets. In Proceedings of the 10th ACM workshop on multimedia and security, pp 21–26
Yang R, Shi Y-Q, Huang J (2009) Defeating fake-quality MP3. In: Proceedings of the 11th ACM workshop on multimedia and security, pp 117–124
Yang R, Shi YQ, Huang J (2010) Detecting double compression of audio signal. In: IS&T/SPIE electronic imaging, pp 75410 K–75410 K-10
Yang R, Qu Z, Huang J (2012) Exposing MP3 audio forgeries using frame offsets. ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM) 8:35
Yiu K-K, Mak M-W, Kung S-Y (2003) Environment adaptation for robust speaker verification. In: INTERSPEECH
Zhang Y, Zhao Y (2013) Modulation domain blind speech separation in noisy environments. Speech Comm 55:1081–1099
Zhao H, Malik H (2012) Audio forensics using acoustic environment traces. In: Statistical Signal Processing Workshop (SSP), 2012 IEEE, 2012, pp 373–376
Zhao H, Malik H (2013) Audio recording location identification using acoustic environment signature. Information Forensics and Security, IEEE Transactions on 8:1746–1759
Zhao H, Chen Y, Wang R, Malik H (2014) Audio source authentication and splicing detection using acoustic environmental signature. In: Proceedings of the 2nd ACM workshop on Information hiding and multimedia security, pp 159–164
Zhou J, Garcia-Romero D, Espy-Wilson CY (2011) Automatic speech codec identification with applications to tampering detection of speech recordings. In proceedings of Interspeech, Florence, Italy, August, 2011, pp. 2533–2536
Acknowledgement
“This Project was funded by the National Plan for Science, Technology and Innovation (MAARIFAH), King Abdulaziz City for Science and Technology, Kingdom of Saudi Arabia, Award Number (12-INF2634-02)”.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zakariah, M., Khan, M.K. & Malik, H. Digital multimedia audio forensics: past, present and future. Multimed Tools Appl 77, 1009–1040 (2018). https://doi.org/10.1007/s11042-016-4277-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-4277-2