Abstract
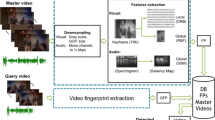
In this paper, a novel robust Video Fingerprinting-Watermarking Hybrid Scheme (VFWHS) is proposed by applying fingerprinting technique to zero-watermarking algorithm for enhancing the performance of video Digital Rights Management (DRM). In the VFWHS, the content-based feature of the original video is extracted by an improved 3D-DCT fingerprinting algorithm and stored in a video fingerprint database for retrieval, while the watermark-based feature of the watermark image is extracted by a 2D-DCT fingerprinting algorithm for copyright identification. According to the visual secret sharing scheme, a master share is generated from the content-based feature while an ownership share is generated from the master share and the watermark-based feature. The ownership share is then stored in an ownership database. When a video is queried, its content-based features are generated, and a process of similarity measurement is executed to obtain the matched feature with the relevant ownership share. The copyright ownership can be identified by stacking the master share generated from the queried video with the relevant ownership share. Our experimental results demonstrate that the VFWHS can obtain the relevant ownership share precisely for reliable copyright identification in the mass content processing which cannot be achieved by the zero-watermarking algorithms, and provide explicit copyright identification to avoid possible copyright dissension which cannot be achieved by the fingerprinting algorithms.

Similar content being viewed by others
References
Chan CS, Chang CC, Vo HP (2012) A user-friendly image sharing scheme using JPEG-LS median edge predictor. JIHMSP 3(4):340–351
Cortes C, Vapnik V (1995) Support-vector networks. Mach Learn 20(3):273–297
Coskun B, Sankur B, Memon N (2006) Spatio–temporal transform based video hashing. IEEE Trans Multimed 8(6):1190–1208
Esmaeili MM, Fatourechi M, Ward RK (2011) A robust and fast video copy detection system using content-based fingerprinting. IEEE Trans Inf Foren Sec 6(1):213–226
Gao G, Jiang G (2013) A lossless copyright authentication scheme based on Bessel-fourier moment and extreme learning machine in curvature-feature domain. J Syst Softw 86(1):222–232
Gao G, Jiang G (2013) Bessel-fourier moment-based robust image zero-watermarking. Multimed Tools Appl. doi:10.1007/s11042-013-1701-8
Guo C, Chang CC (2013) A construction for secret sharing scheme with general access structure. JIHMSP 4(1):1–8
Huang GB, Zhu QY, Siew CK (2006) Extreme learning machine: theory and applications. Neurocomputing 70(1):489–501
Joly A, Buisson O, Frelicot C (2007) Content-based copy retrieval using distortion-based probabilistic similarity search. IEEE Trans Multimed 9(2):293–306
Lee MC, Chan RKW, Adjeroh DA (1997) Quantization of 3D-DCT coefficients and scan order for video compression. J Vis Commun Image Represent 8(4):405–422
Lee SJ, Jung SH (2001) A survey of watermarking techniques applied to multimedia. In Proc. of Int. Symp. Industrial electronics (ISIE), pp 272–277
Lee S, Yoo CD (2008) Robust video fingerprinting for content-based video identification. IEEE Trans Circ Syst Evid 18(7):983–988
Lian S, Nikolaidis N, Sencar HT (2010) Content-based video copy detection - a survey. In: Sencar HT, Velastin S, Nikolaidis N, Lian S (eds) Intelligent multimedia analysis for security applications. Springer-Verlag Berlin and Heidelberg GmbH & Co. K, pp 253–273
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60(2):91–110
Naor M, Shamir A (1995) Visual cryptography. In: advances in cryptology-EUROCRYPT’94, pp 1–12
Potdar VM, Han S, Chang E (2005) A survey of digital image watermarking techniques. In: Int. Conf. on industrial informatics (INDIN), pp 709–716
Rawat S, Raman B (2012) A blind watermarking algorithm based on fractional fourier transform and visual cryptography. Signal Process 92(6):1480–1491
Singh TR, Singh KM, Roy S (2013) Video watermarking scheme based on visual cryptography and scene change detection. AEU Int J Electron Commun 67(8):645–651
Sun J, Wang J, Zhang J, Nie X, Liu J (2012) Video hashing algorithm with weighted matching based on visual saliency. IEEE Signal Proc Let 19(6):328–331
Sun Z, Zhu Y, Liu X, Zhang L (2013) A robust video fingerprinting algorithm based on centroid of spatio-temporal gradient orientations. KSII Trans Internet Inf 7(11):2754–2768
Tsai HH, Tseng HC, Lai YS (2010) Robust lossless image watermarking based on α-trimmed mean algorithm and support vector machine. J Syst Softw 83(6):1015–1028
Wang MS, Chen WC (2009) A hybrid DWT-SVD copyright protection scheme based on k-means clustering and visual cryptography. Comput Stand Int 31(4):757–762
Wang ZH, Pizzolatti MS, Chang CC (2014) Efficient and meaningful multi-secret image sharing based on block imitation. JIHMSP 5(1):55–69
Acknowledgment
The authors would like to thanks Mr. Dennis D. Zhu for the kind support and valuable comments on this paper. This work is supported by the 973 Program of China under Grant 2012CB315904; and Shenzhen Engineering Laboratory for Broadband Wireless Network Security.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, X., Zhu, Y., Sun, Z. et al. A novel robust video fingerprinting-watermarking hybrid scheme based on visual secret sharing. Multimed Tools Appl 74, 9157–9174 (2015). https://doi.org/10.1007/s11042-014-2073-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-014-2073-4