Abstract
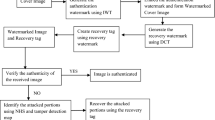
The ability against the collage attack of semi-fragile watermarking is improved by embedding the watermark of a block in other blocks, but the tamper detection performance is impaired under general tampering. A two-stage detection method is proposed to improve the tamper detection performance of semi-fragile watermarking. For each 8 × 8 block, six-bit watermark data generated by the significant DCT (Discrete Cosine Transformation) coefficients are divided into two parts with the same length: general tampering watermark (GTW) and collage attack watermark (CAW). The GTW and CAW data of a block are embedded in the quantized DCT coefficients of itself and other blocks, respectively. In the first-stage detection, the general tampered regions are localized by the GTW data. To identify whether the collage attack exists in the received image, the identification parameter is defined by both GTW and CAW data. The selection of the predefined threshold of the identification parameter is derived and verified by the statistical experiments. If the identification parameter is larger than the given threshold, the second stage detection is performed to detect the collaged regions. Experimental results demonstrate that the proposed two-stage detection method is able to identify tampering with high probability under general tampering, collage attack and hybrid attack.











Similar content being viewed by others
References
Che S, Ma B, Che Z (2007) Semi-fragile image watermarking algorithm based on visual features. In: Proc. of international conference on wavelet analysis and pattern recognition. Beijing, China, pp 382–387
Fridrich J, Goljan M, Du R (2001) Invertible authentication watermark for JPEG images. In: Proc. Of IEEE internal conference on information technology, pp 223–227
Fridrich J, Goljan M, Memon N (2002) Cryptanalysis of the Yeung-Mintzer fragile watermarking technique. J Electron Imaging 11:262–274
Han S, Chu C (2010) Content-based image authentication current status, issues, and challenges. Int J Inf Secur 9:19–32
Haouzia A, Noumeir R (2008) Methods for image authentication: a survey. Multimed Tools Appl 39:1–46
He H (2009) Digital Image secure authentication watermarking algorithms and their performance analysis of statistical detection. Ph.D Thesis, Southwest Jiaotong University
Huo YR, Chen F, He HJ, Yin ZK (2010) An alterable-capacity authentication watermarking algorithm with superior localization. In: Proc. of international conference on information theory and information security. Beijing, China, pp 608–611
Li C (2004) Digital fragile watermarking scheme for authentication of JPEG images. IEEE Proc Vis Image Signal Process 151:460–466
Lin CY, Chang SF (2000) Semi-Fragile Watermarking for Authenticating JPEG Visual Content. In: Proc. of SPIE, security and watermarking of multimedia contents II, vol 3971. San Jose, USA, pp 140–151
Liu H, Lin J, Huang J (2005) Image authentication using content based watermark. In: Proc. of IEEE international symposium on circuits and systems. Kobe, Japan, pp 4014–4017
Liu H, Yao X, Huang J (2010) Semi-Fragile Zernike Moment-Based Image Watermarking for Authentication. EURASIP J Adv Signal Process 2010:1–17
Phadikar A, Maity S, Mandal M (2012) Novel wavelet-based QIM data hiding technique for tamper detection and correction of digital images. J Vis Commun Image Represent 23:454–466
Qi X, Xin X (2011) A quantization-based semi-fragile watermarking scheme for image content authentication. J Vis Commun Image Represent 22:187–200
Rafiullah C, Asifullah K (2010) Digital image authentication and recovery: employing integer transform based information embedding and extraction. Inf Sci 180:4909–4928
Van Schyndel RG, Tirkel AZ, Osborne CF (1994) A digital watermark. In: Proc. of the IEEE international conference on image processing, vol 2. Austin Texas, USA, pp 86–90
Wolfgang RB, Delp EJ (1996) A watermark for digital images. In: Proceedings of the IEEE international conference on image processing, vol 3. Lausanne, Switzerland, pp 219–22
Yu M, He H, Zhang J (2007) A digital authentication watermarking scheme for JPEG images with superior localization and security. Sci China F Inf Sci 50:491–509
Zhang W, Frank Y (2011) Semi-fragile spatial watermarking based on local binary pattern operators. Opt Commun 284:3904–3912
Zhou X, Duan X, Wang D (2004) A semi-fragile watermarking scheme for image authentication. In: Proc. of the 10th international conference on multimedia modeling. Brisbane, Australia, pp. 374–377
Zhu B, Swanson M, Tewfix A (2004) When seeing isn’t believing. IEEE Signal Process 21:40–49
Acknowledgements
This work is supported in part by the National Natural Science Foundation of China (Grant No.60970122, 61170226), the Research Fund for the Doctoral Program of Higher Education (Grant No.20090184120021), the Fundamental Research Funds for the Central Universities (Grant No.SWJTU09CX039, SWJTU10CX09), Beijing Key Laboratory of Advanced Information Science & Network Technology and Railway Key Laboratory of Information Science & Engineering (Grant No. XDXX1007), and by the Science and Technique Foundation of Tibet Autonomous Region (2012).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Huo, Y., He, H. & Chen, F. A semi-fragile image watermarking algorithm with two-stage detection. Multimed Tools Appl 72, 123–149 (2014). https://doi.org/10.1007/s11042-012-1317-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-012-1317-4